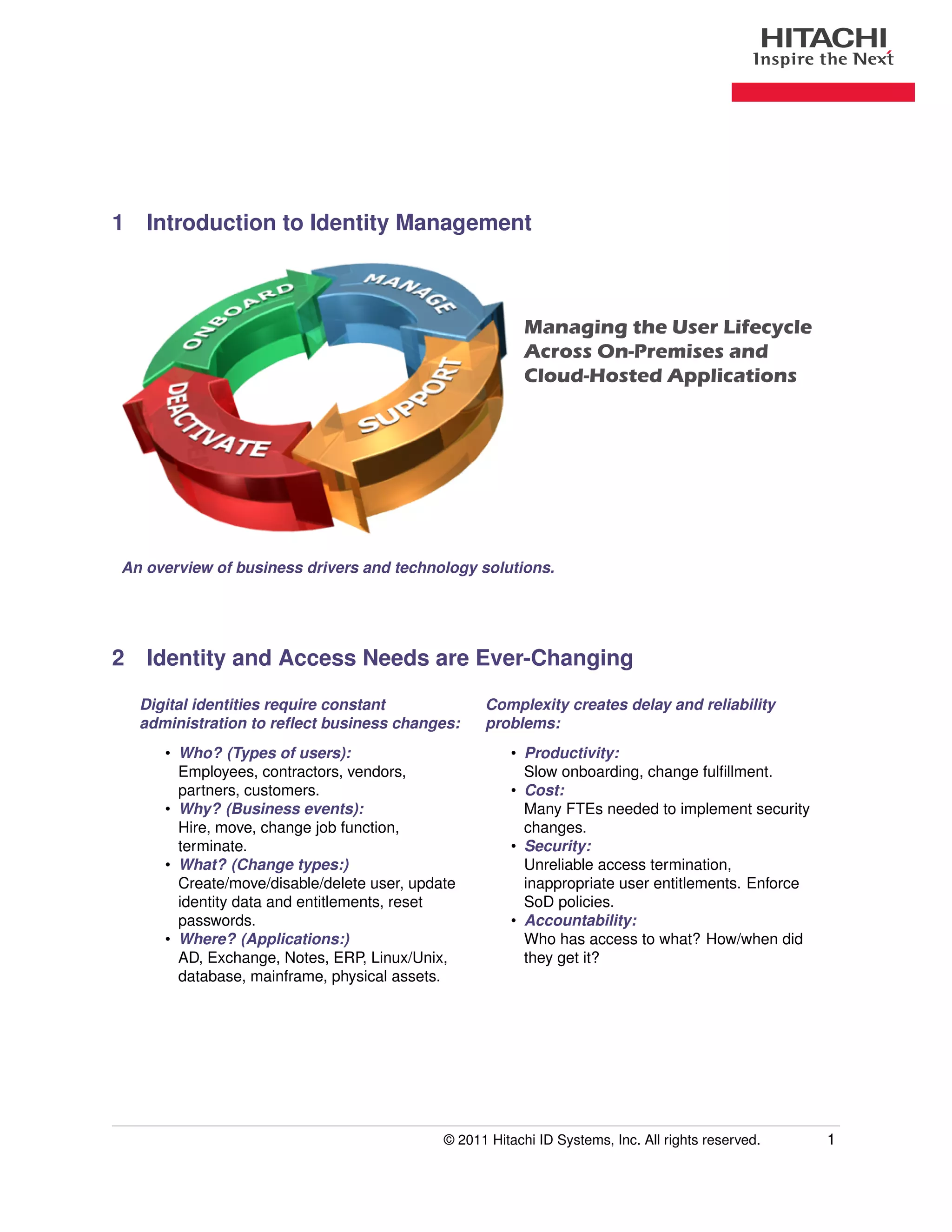
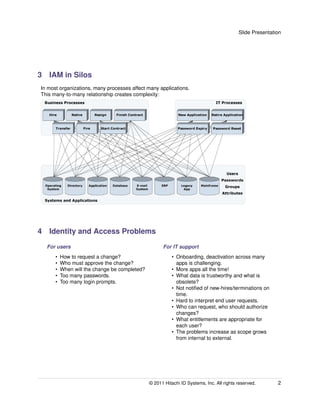
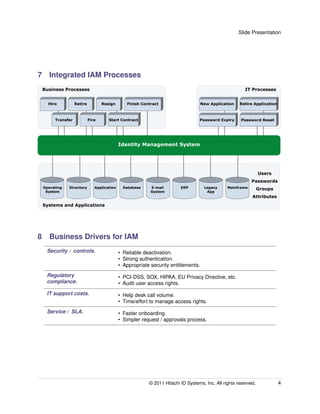
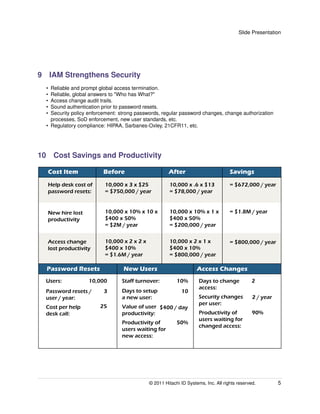
An integrated identity and access management (IAM) solution can help address challenges organizations face in managing digital identities and user access across multiple on-premises and cloud-based applications. As business needs change, user identities and access rights must be constantly updated, but managing these changes across numerous siloed systems leads to delays, reliability issues, and security risks. An IAM system extracts identity functions from separate application silos into a centralized infrastructure to streamline user onboarding, access changes, offboarding and improve security, compliance and productivity. Key benefits include reliable deprovisioning, strong authentication, appropriate entitlements, reduced help desk costs, faster access provisioning and strengthened audit capabilities.