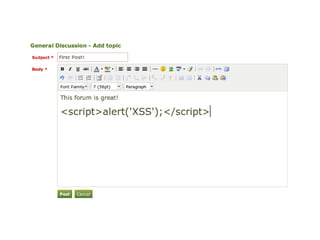
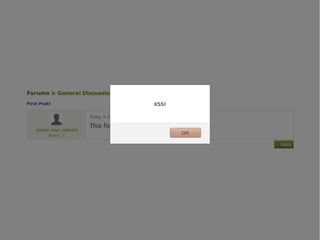
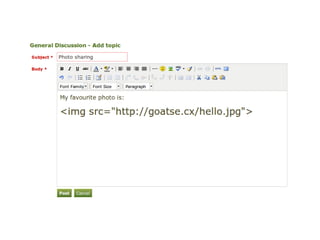
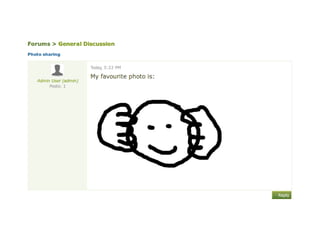
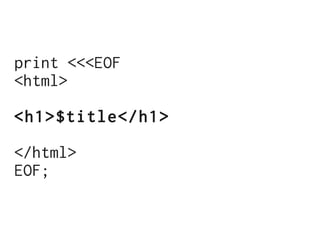
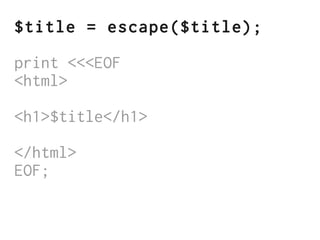
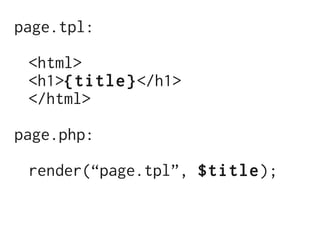
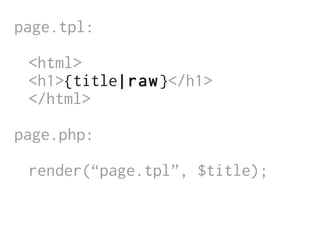
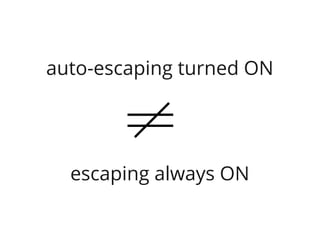
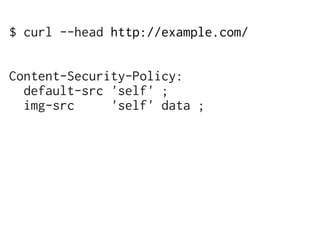
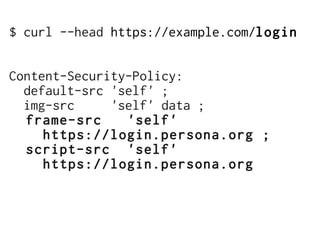
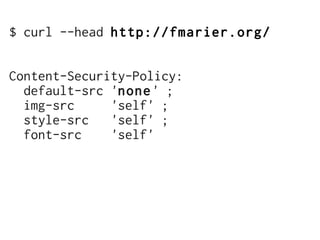
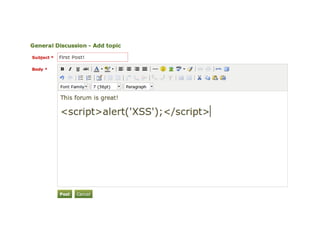
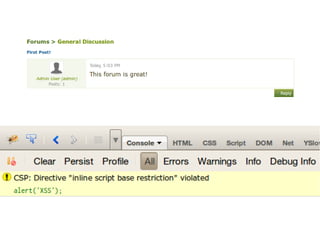
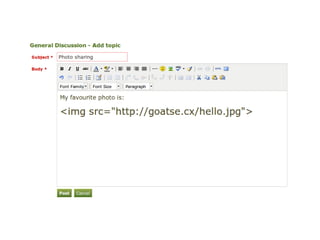
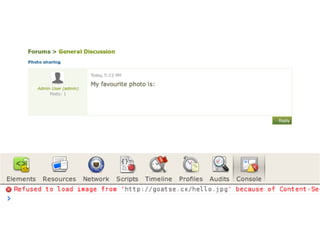
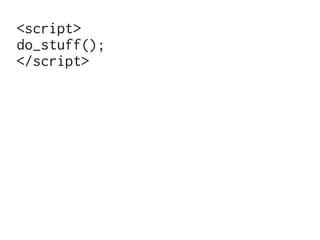
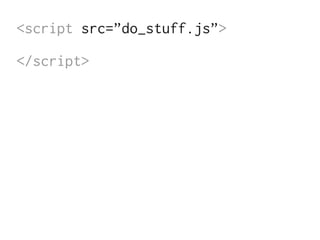
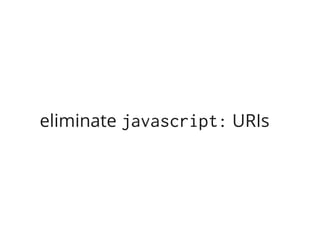
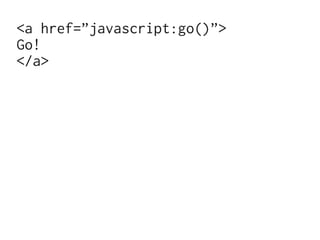
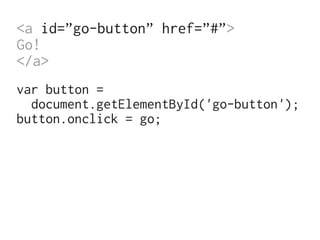
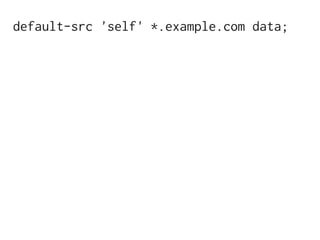
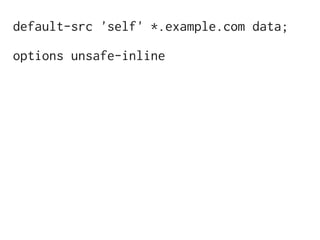
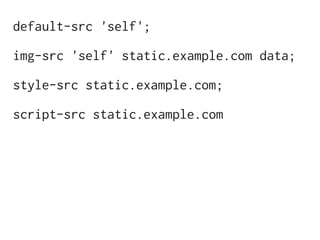
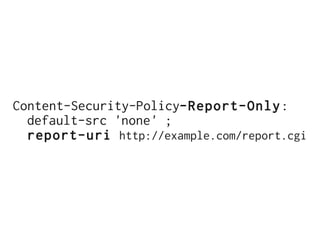
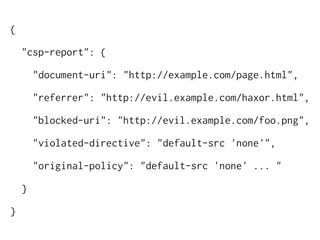
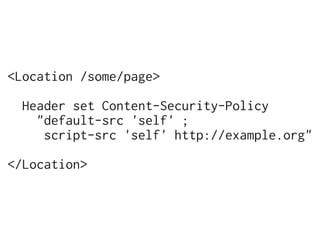
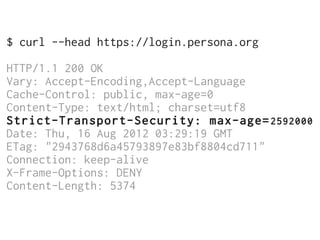
The document discusses Cross-Site Scripting (XSS) attacks and introduces Content Security Policy (CSP) as a preventive measure. It explains how to implement CSP by configuring web server headers and highlights steps to eliminate risky practices such as inline scripts. Additionally, it emphasizes that while CSP enhances security, it is not a substitute for basic XSS hygiene.