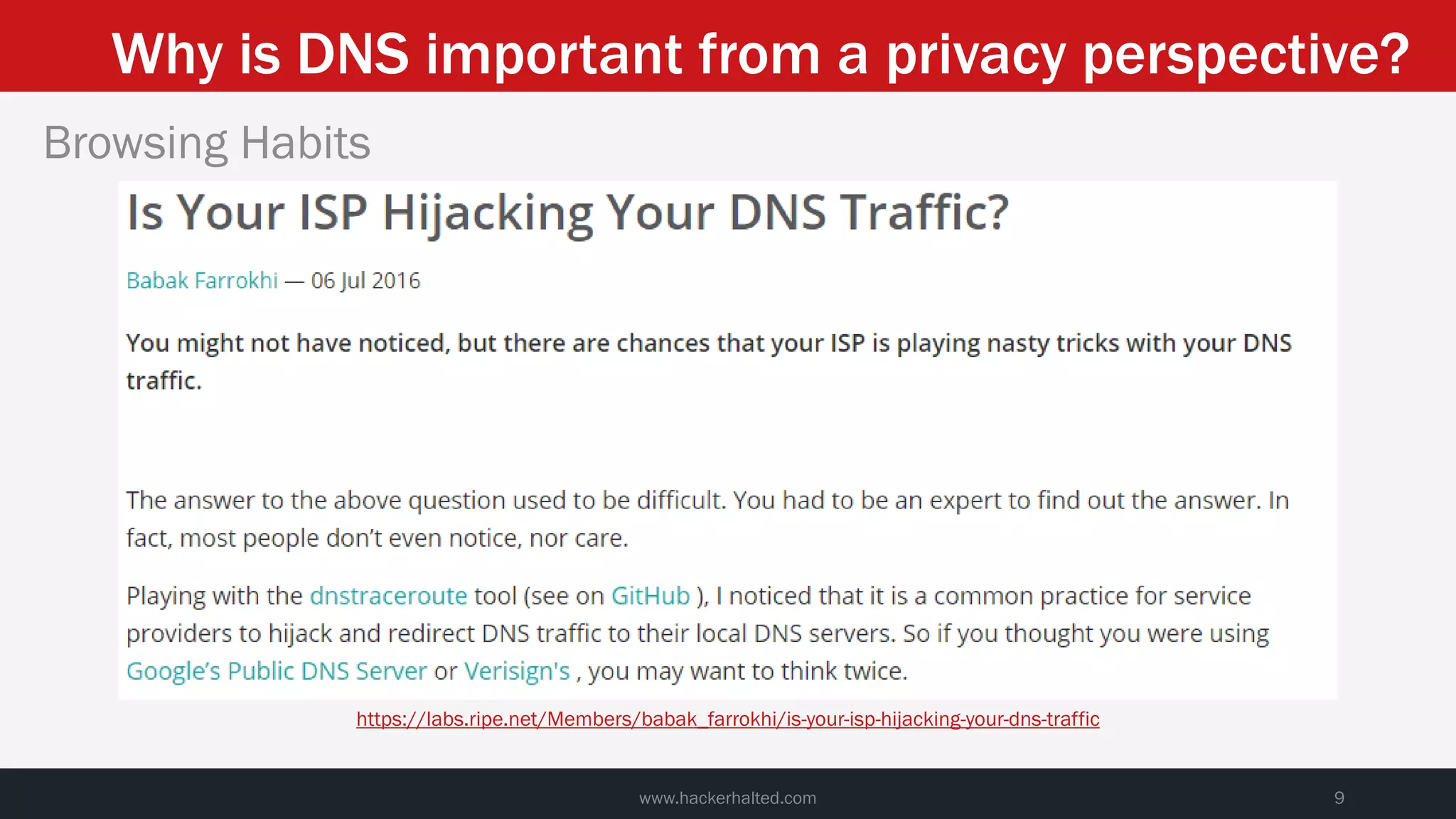
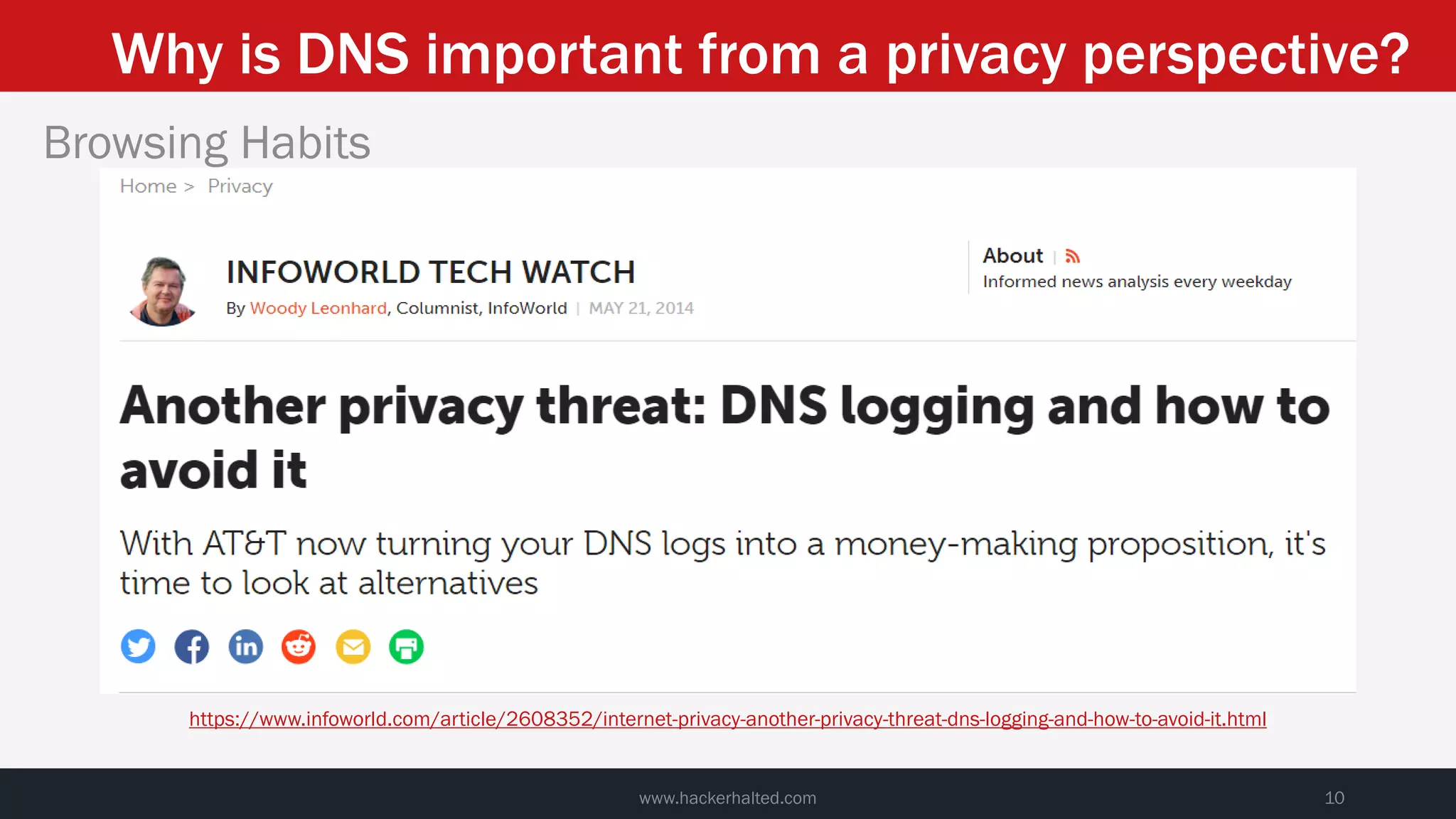
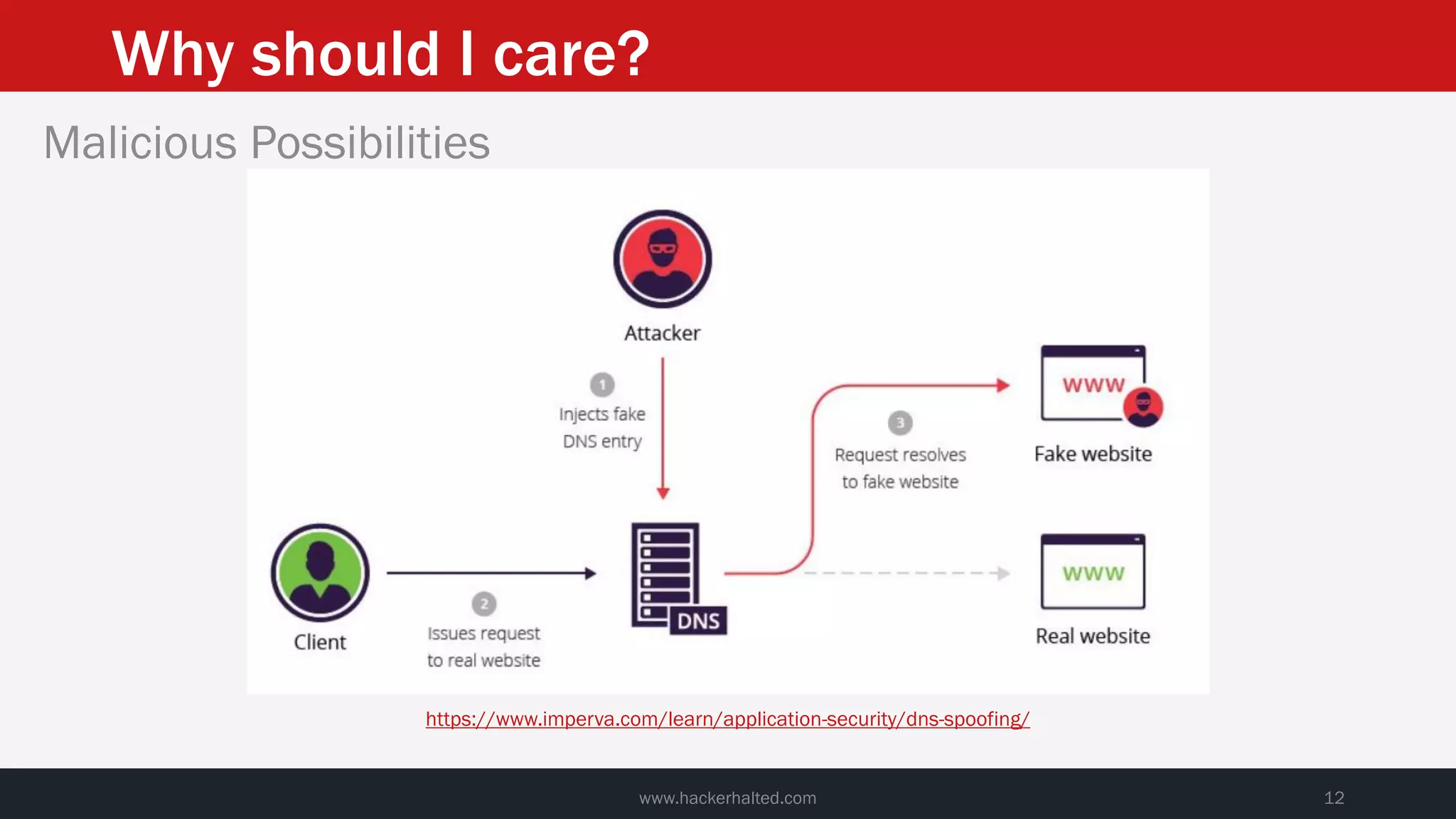
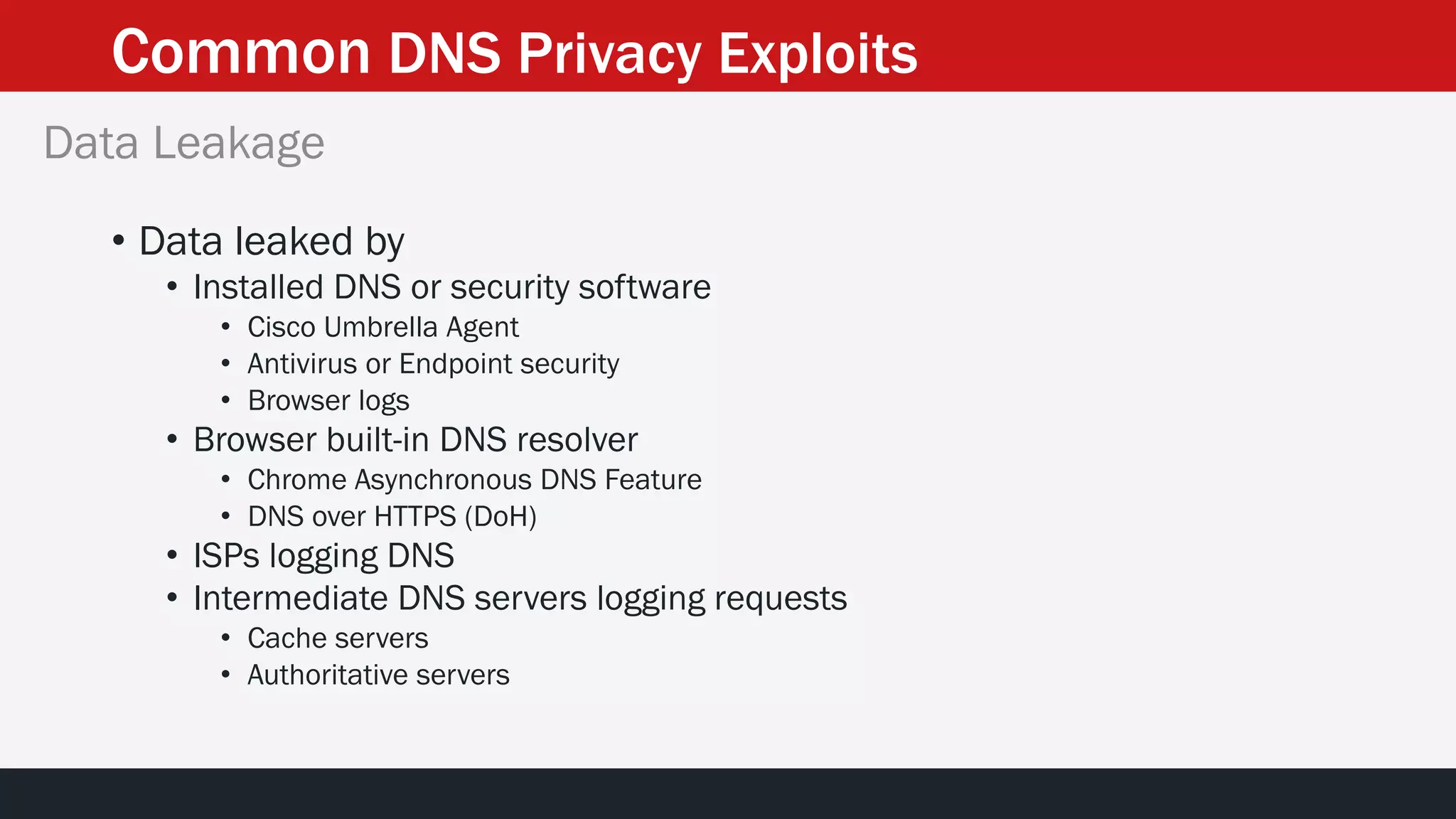
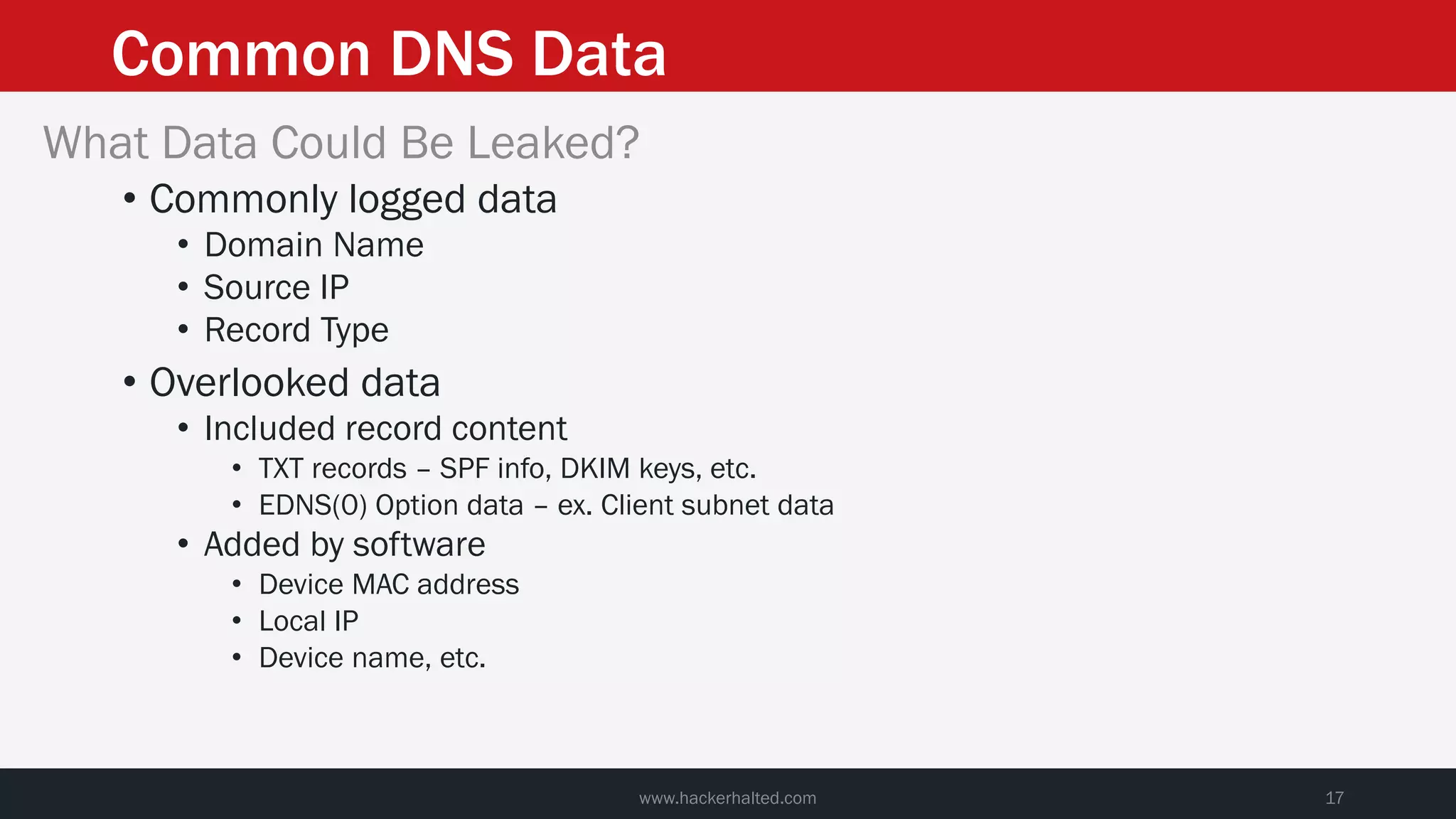
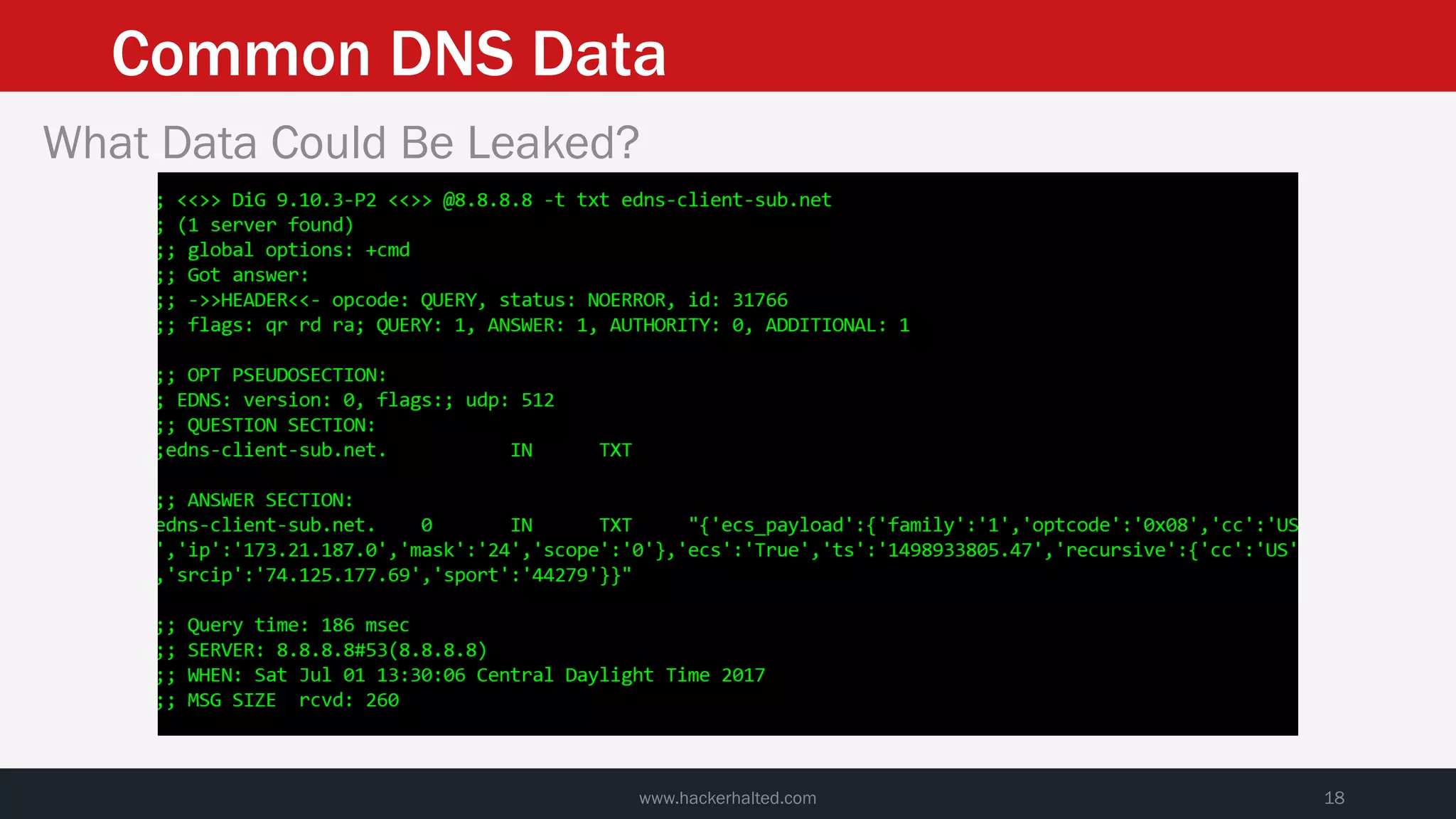
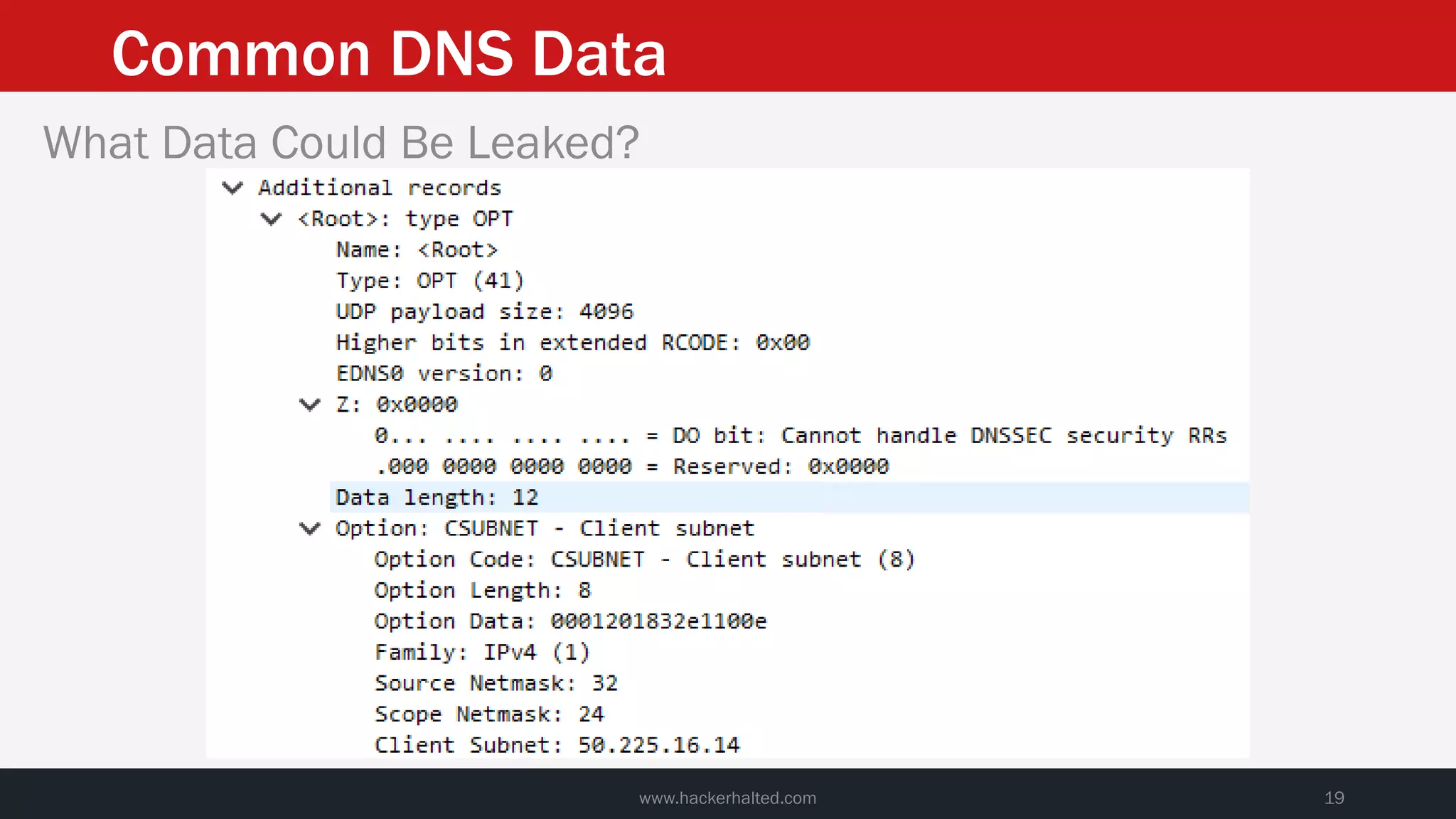
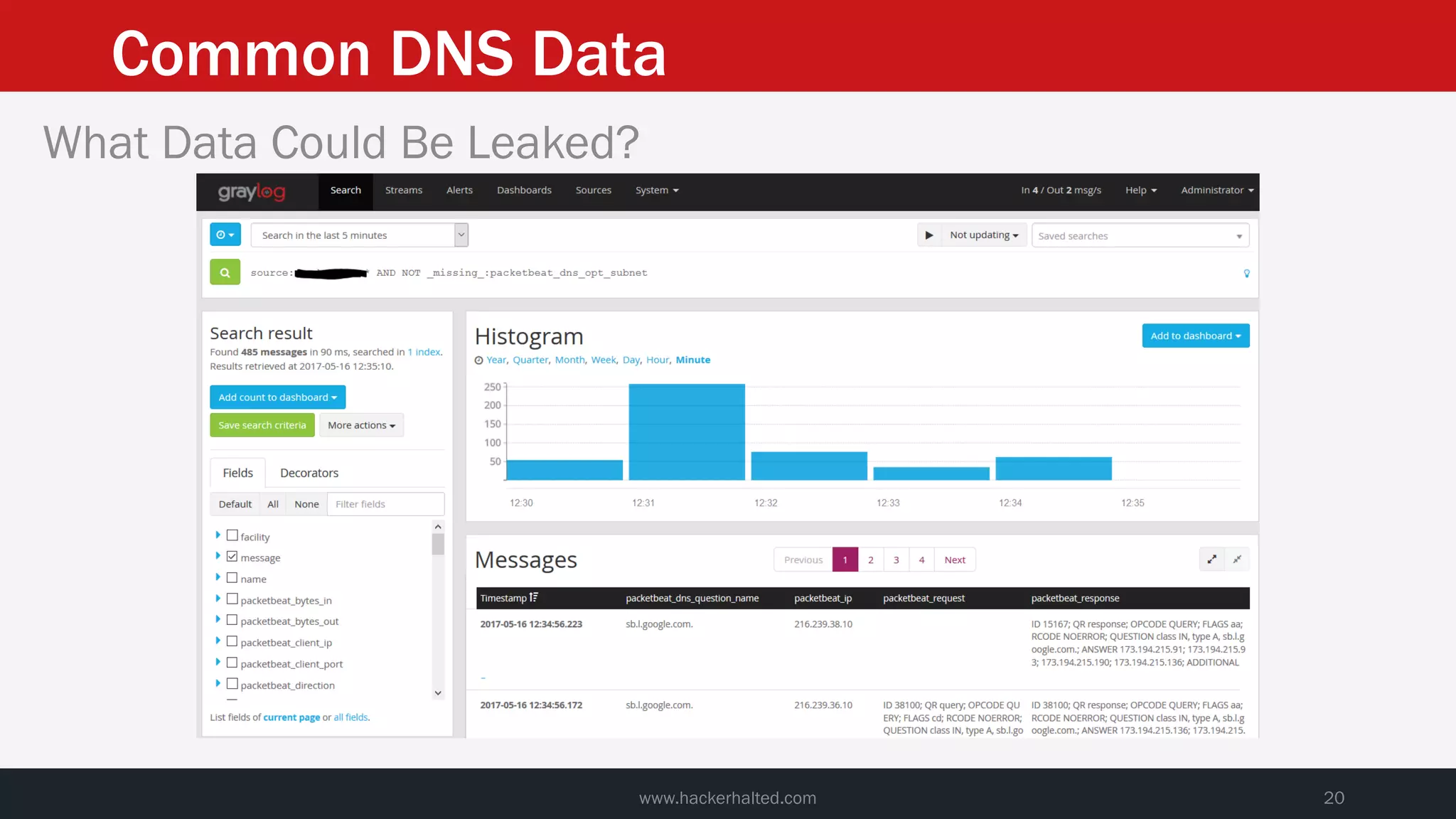
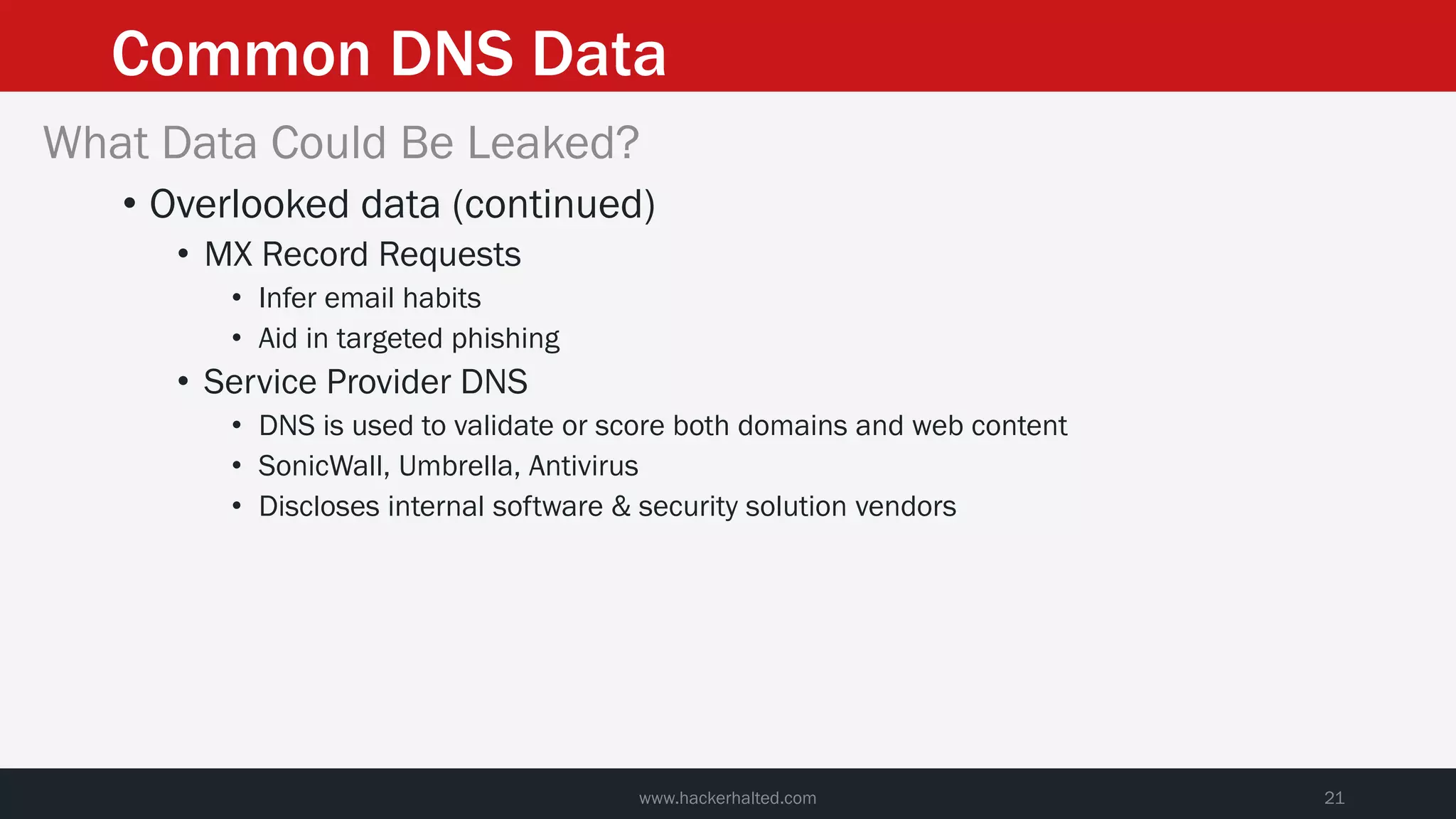
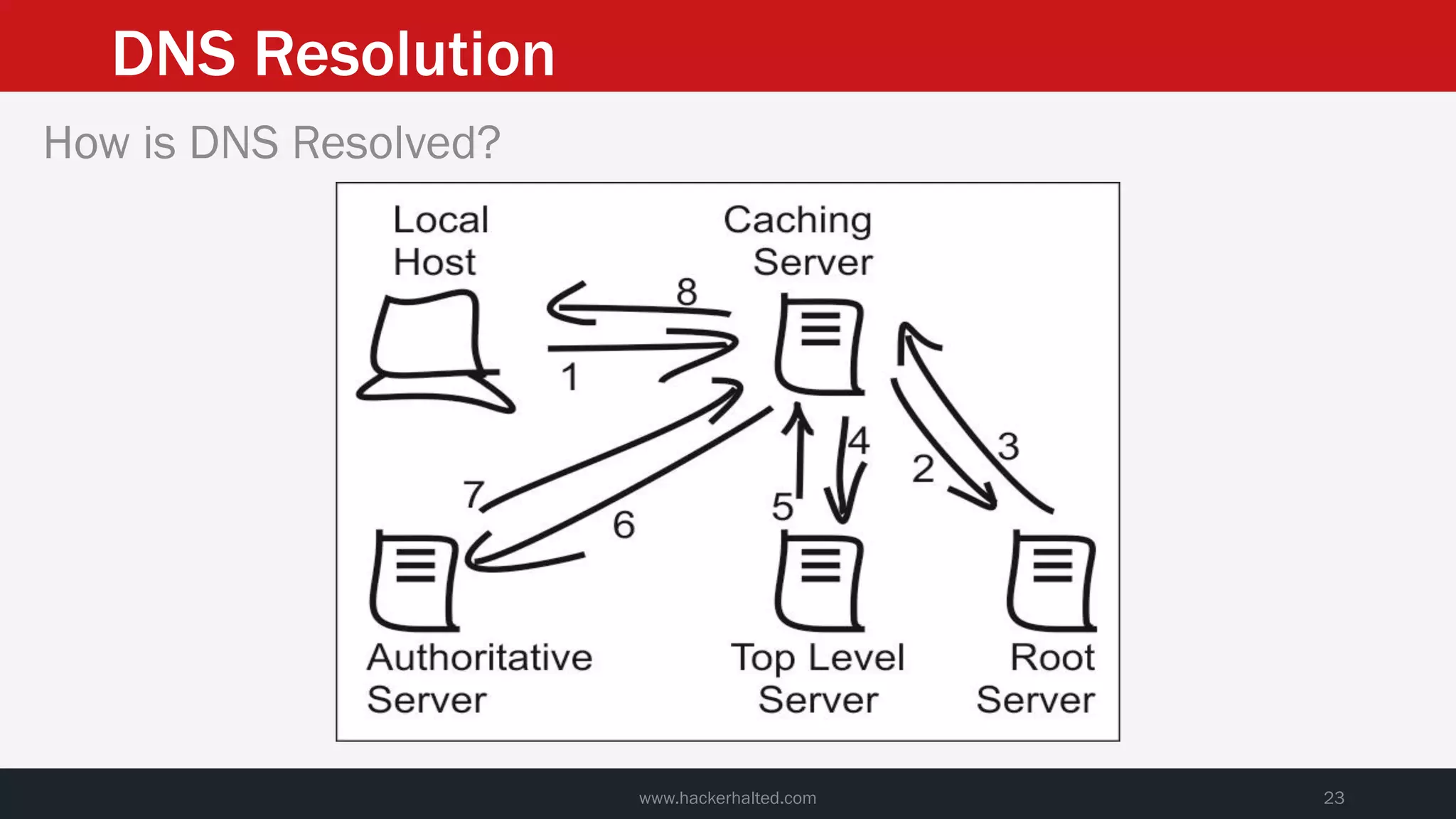
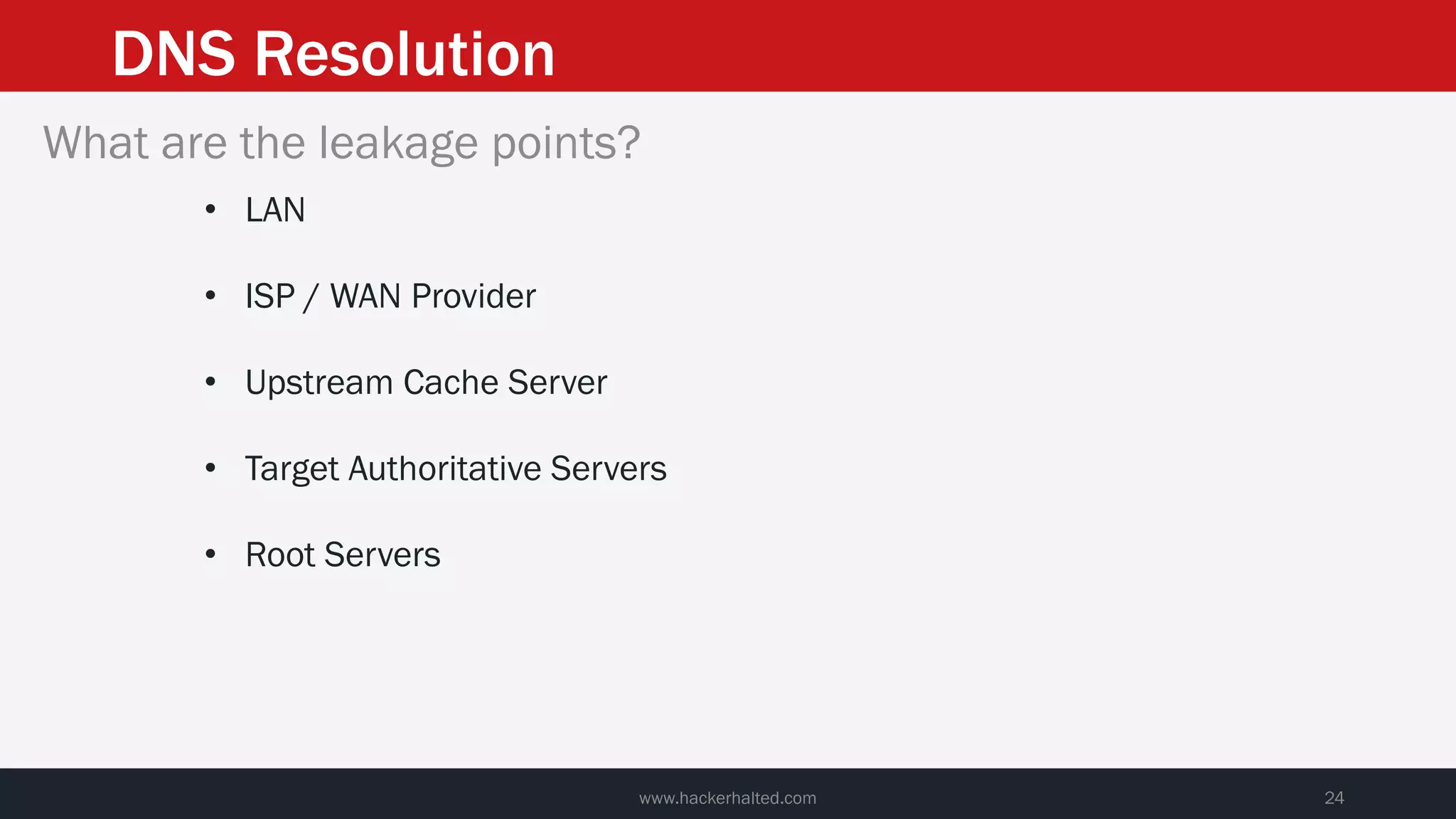
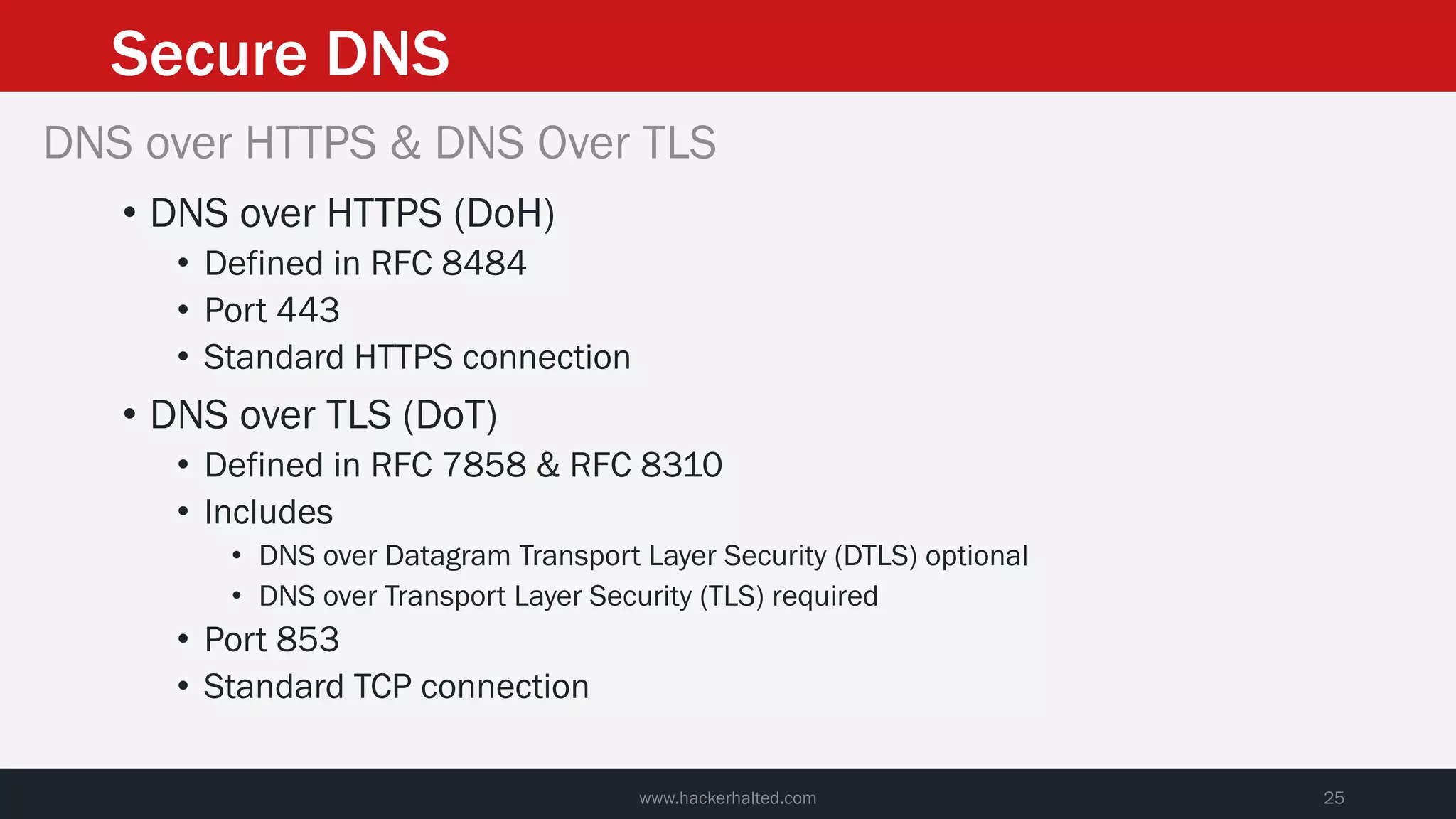
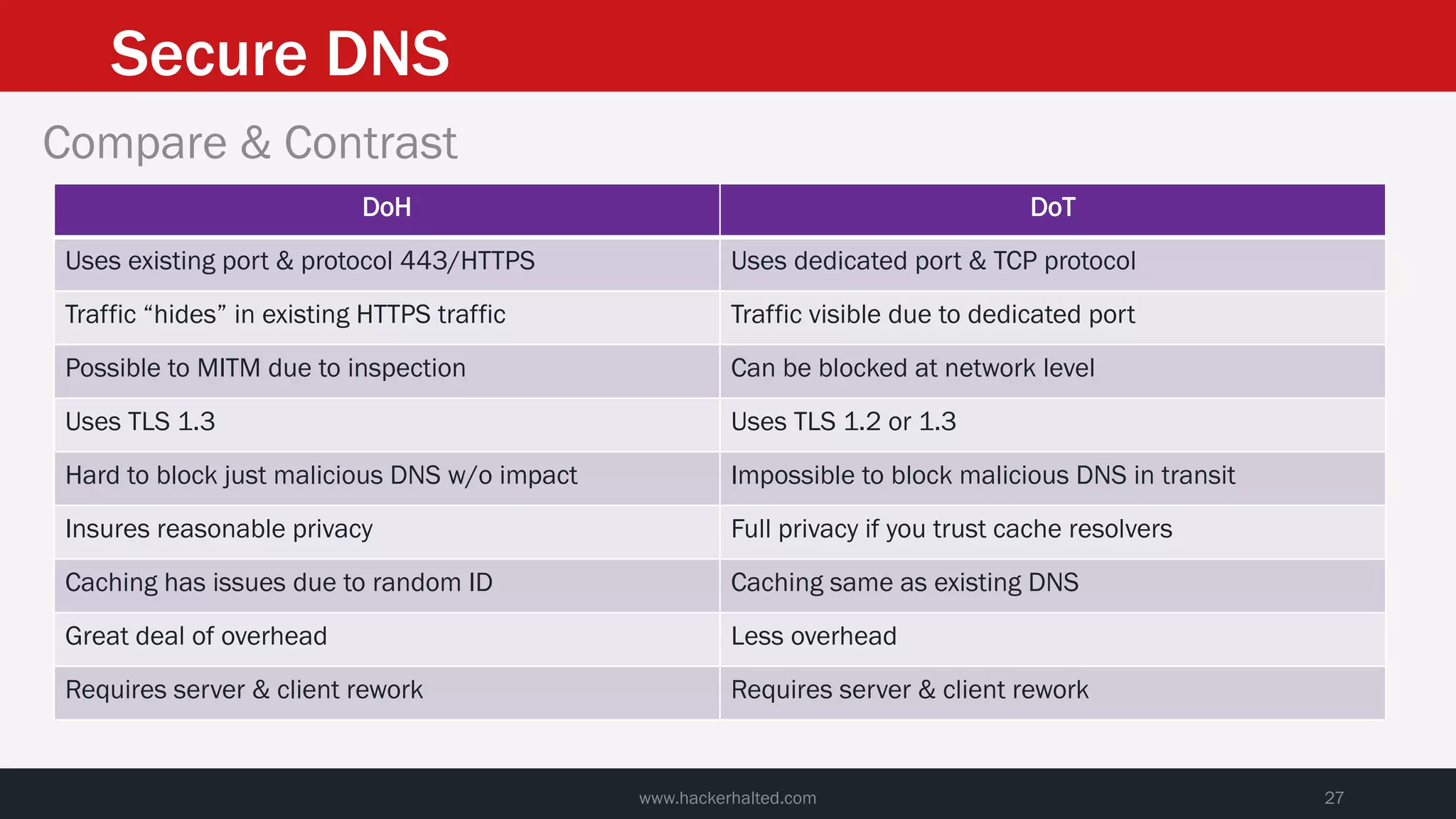
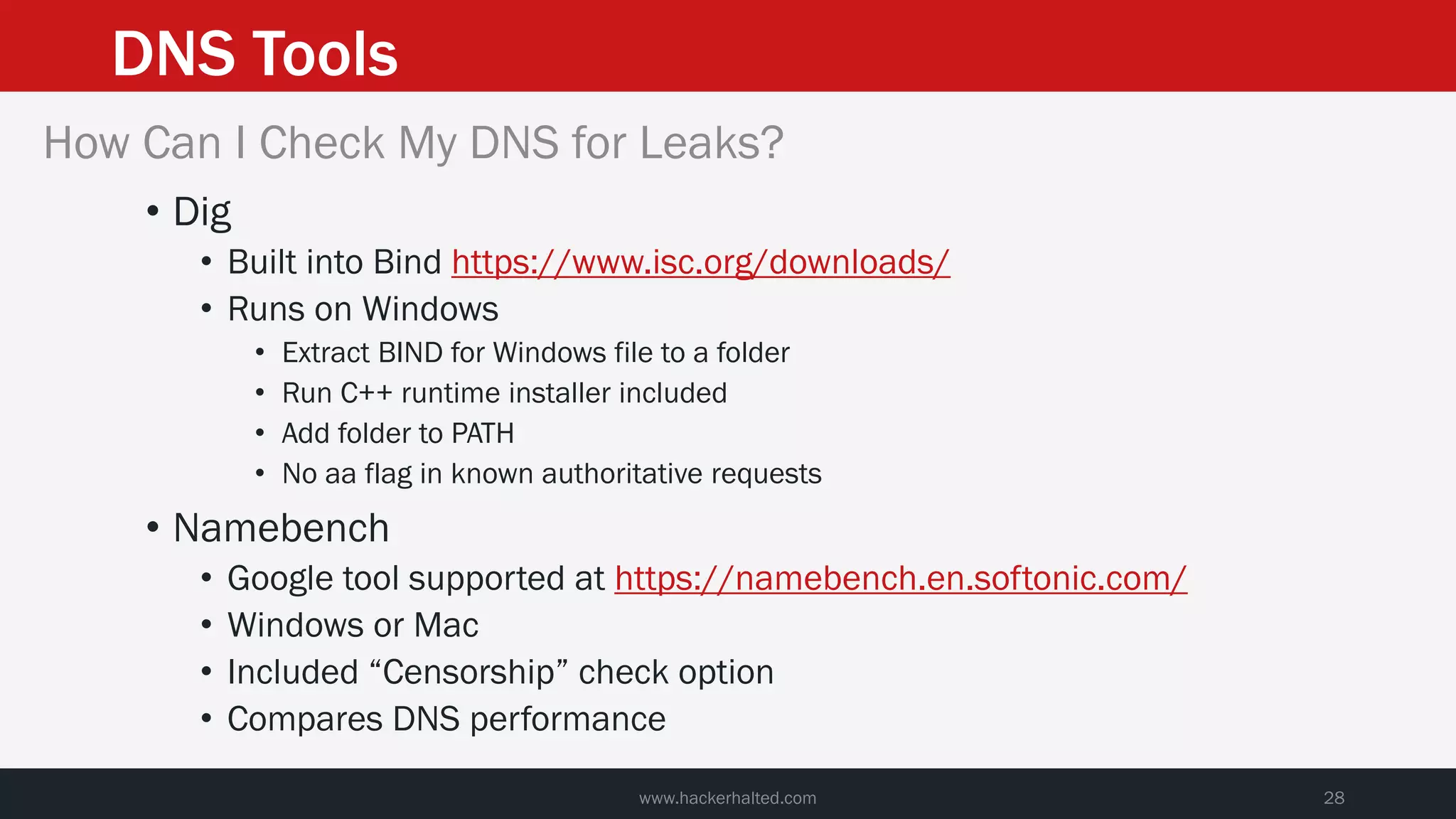
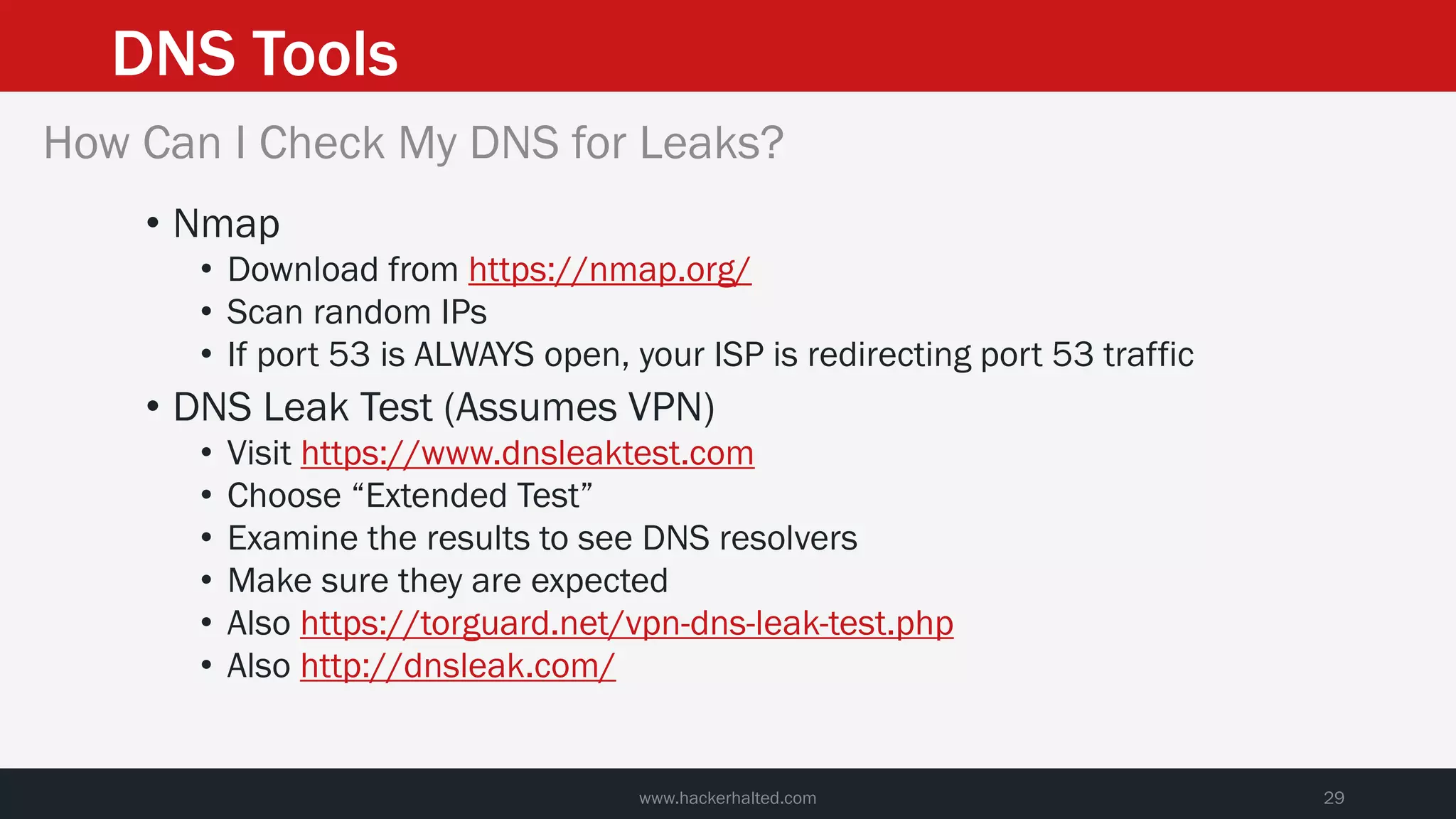
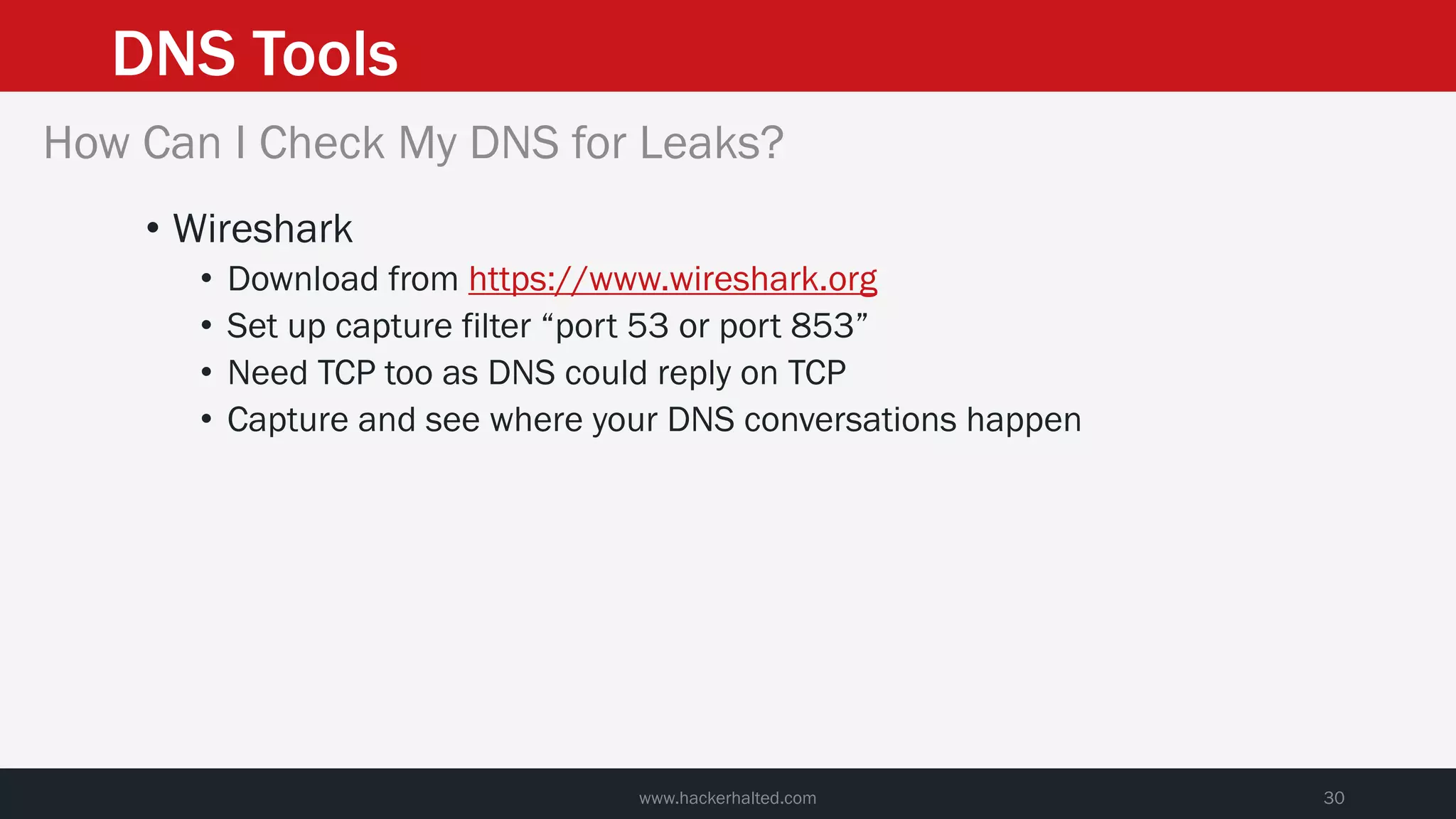
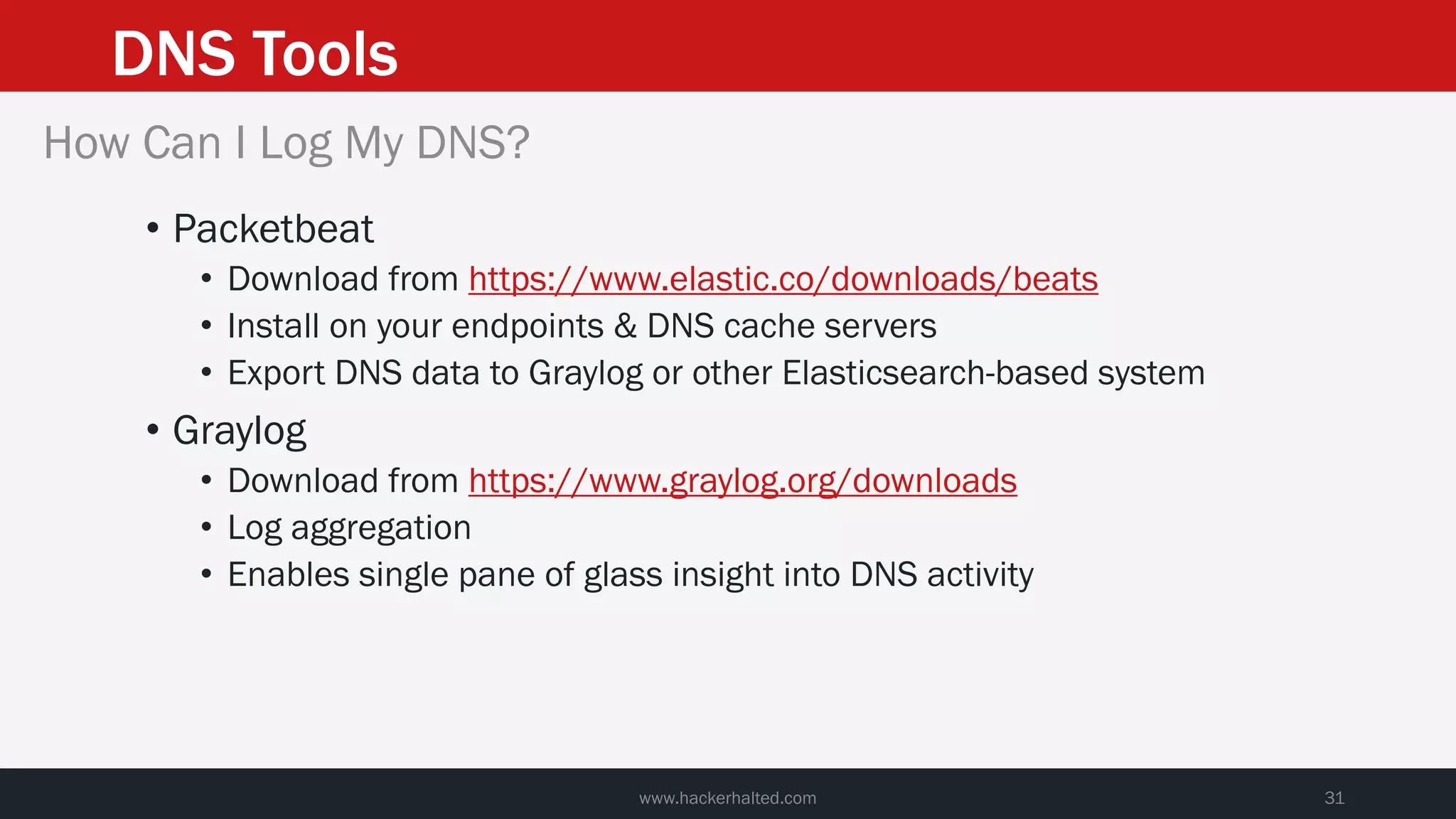
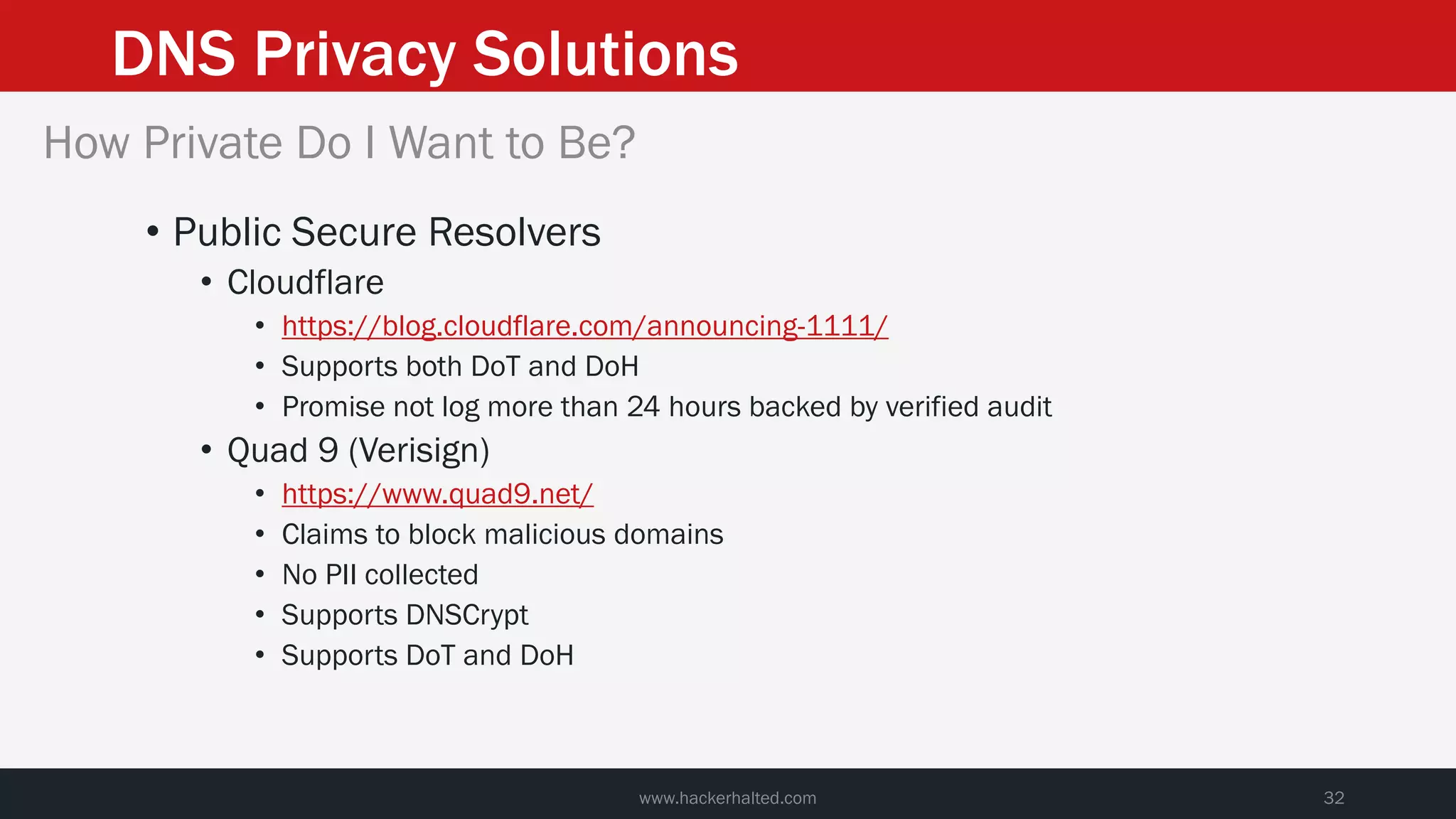
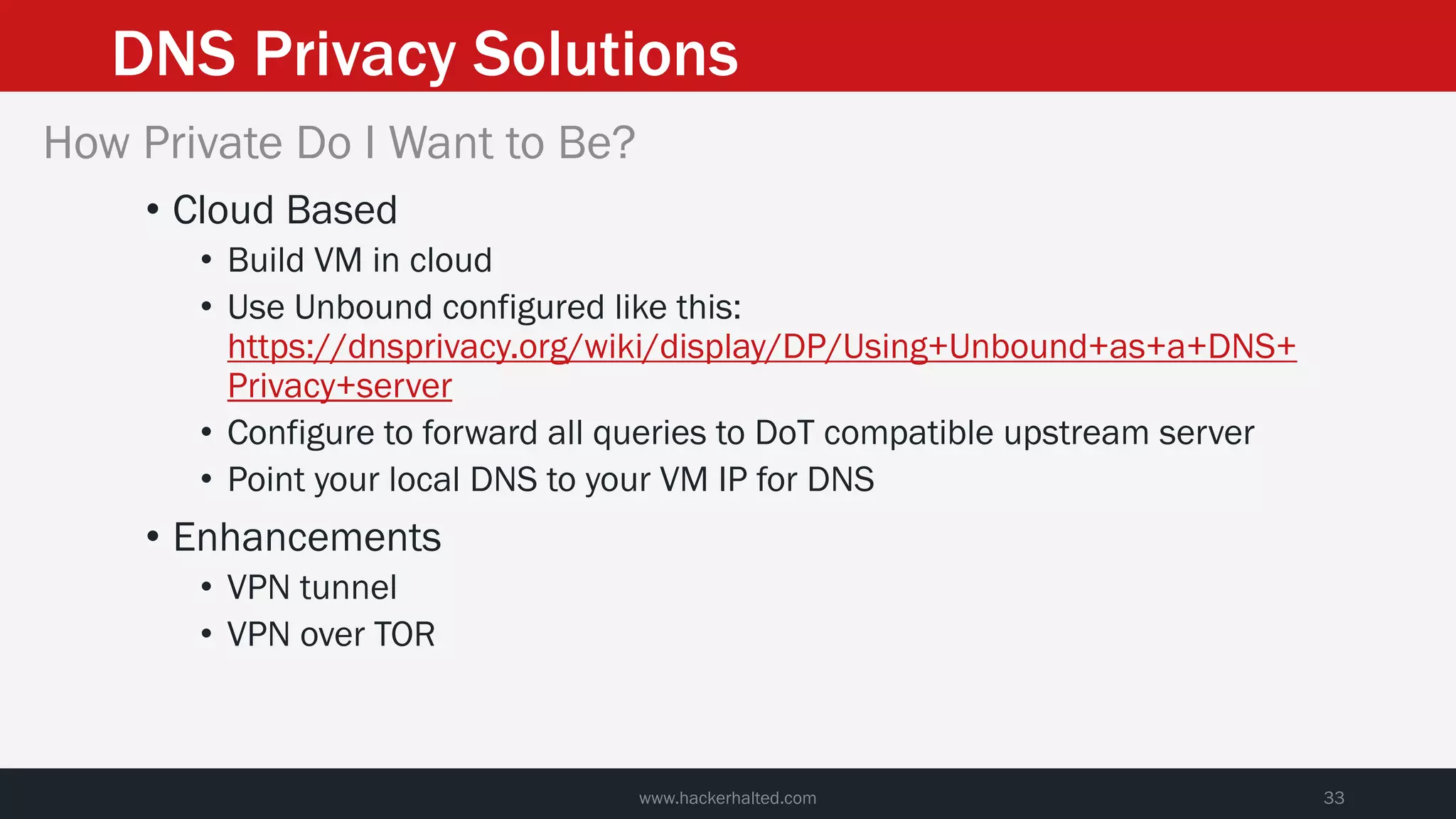
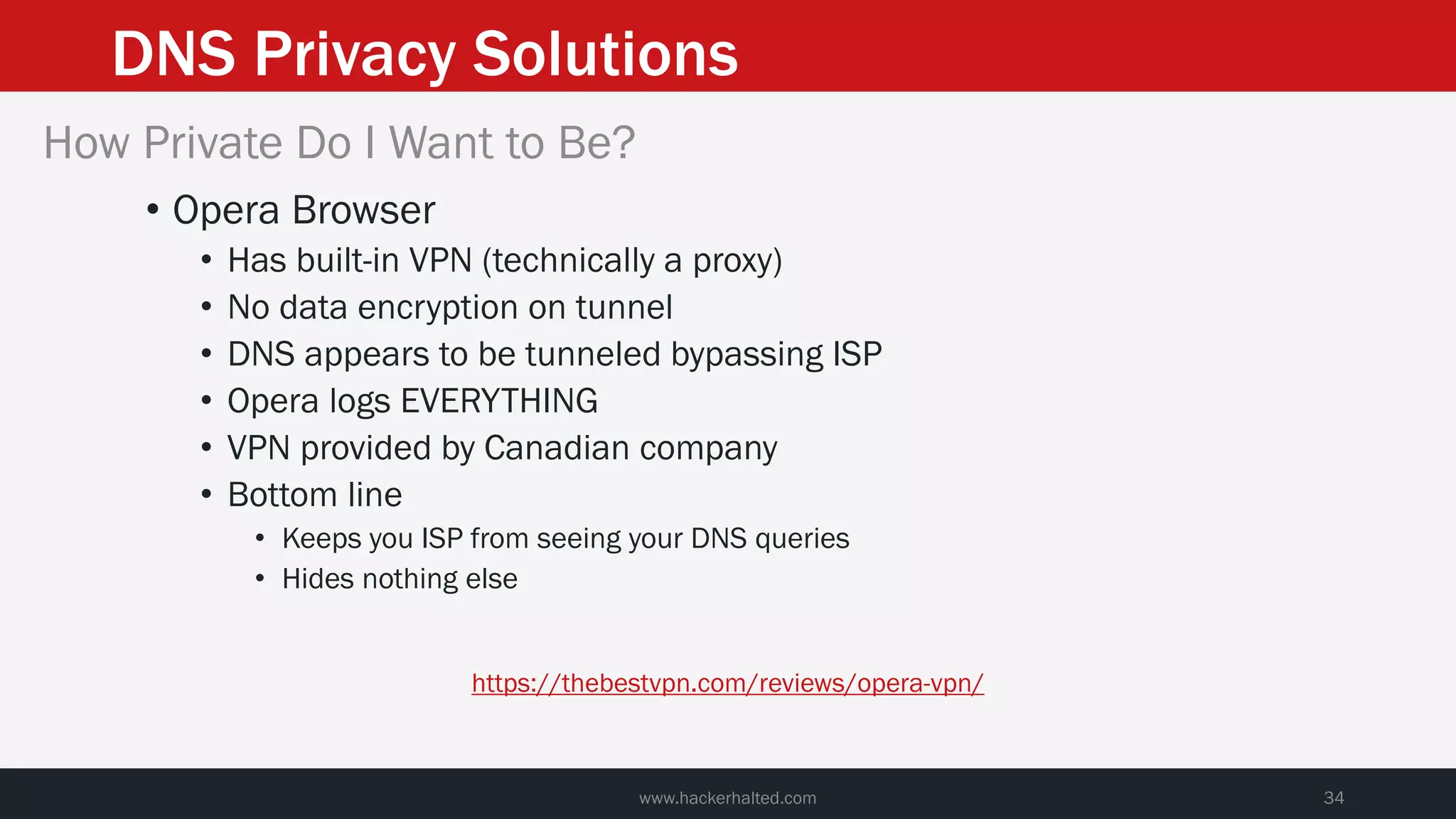
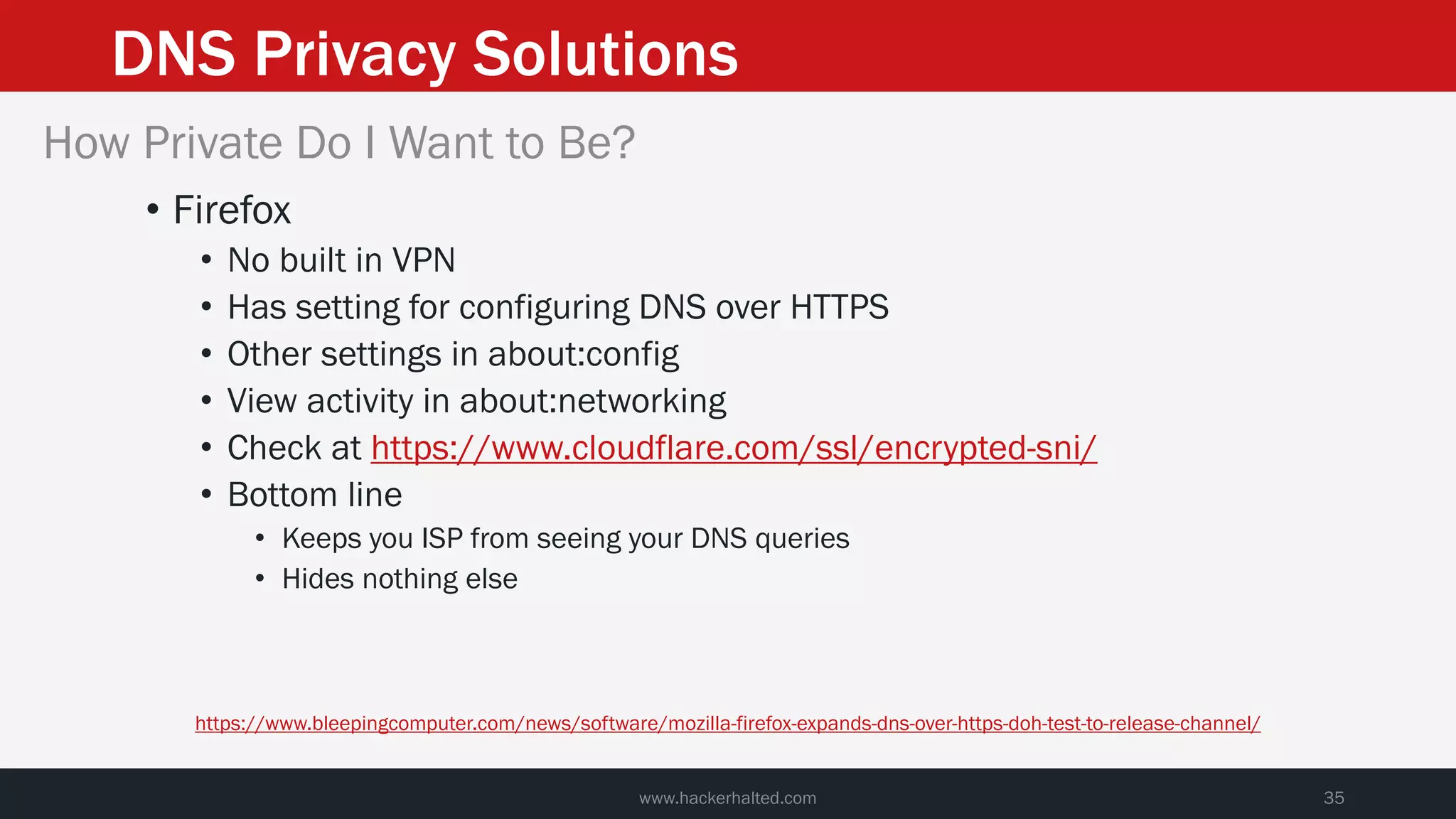
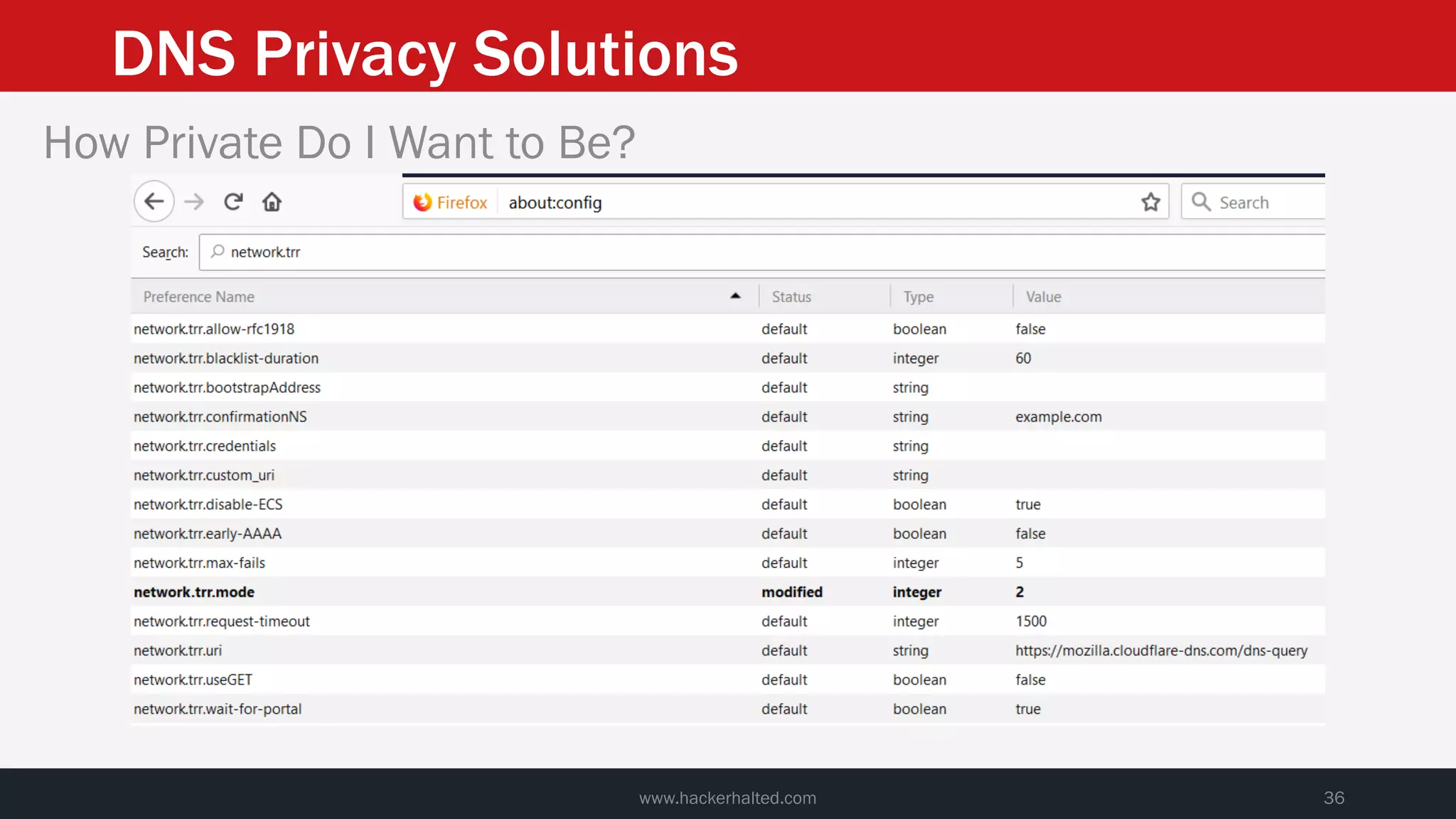
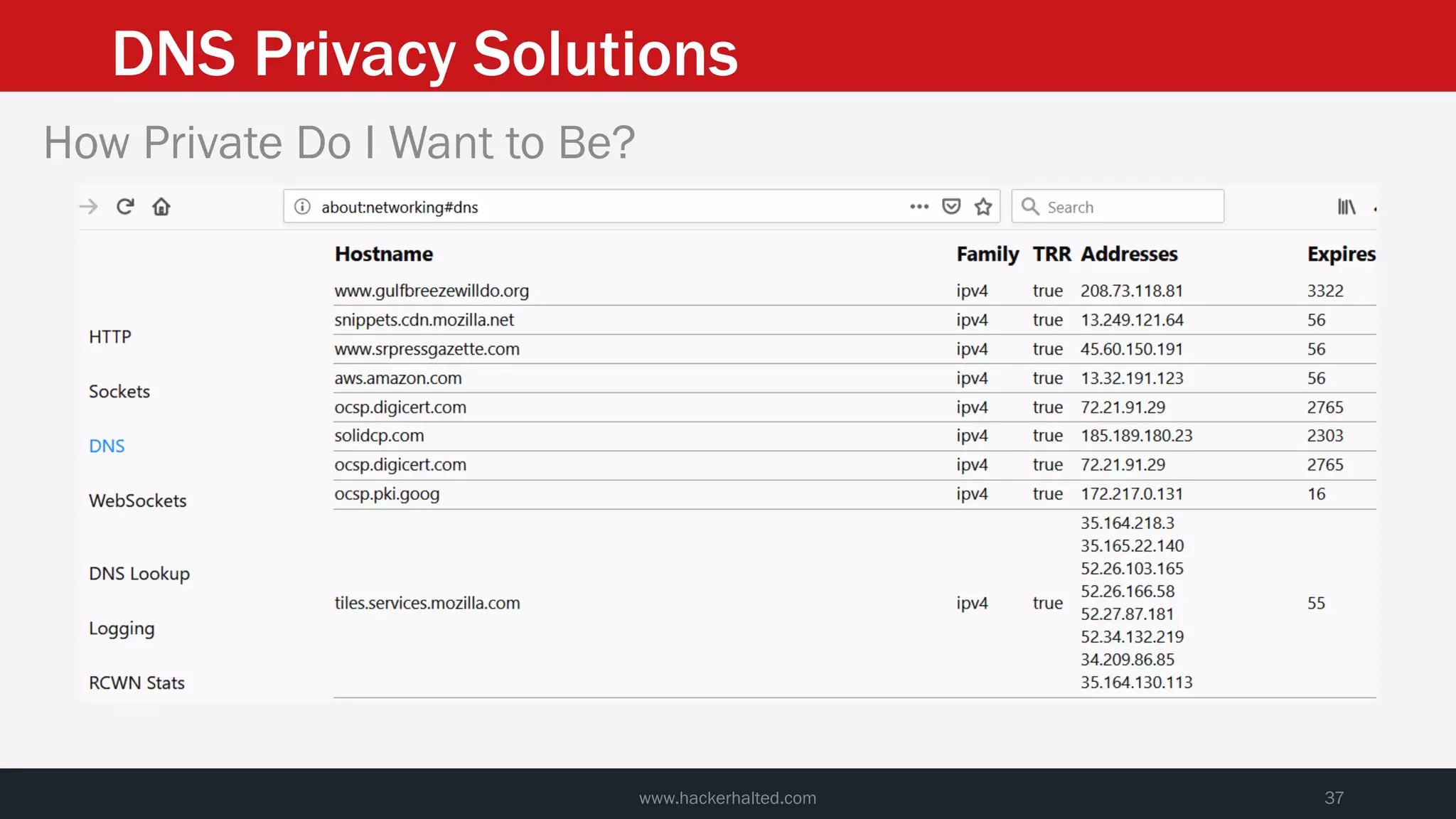
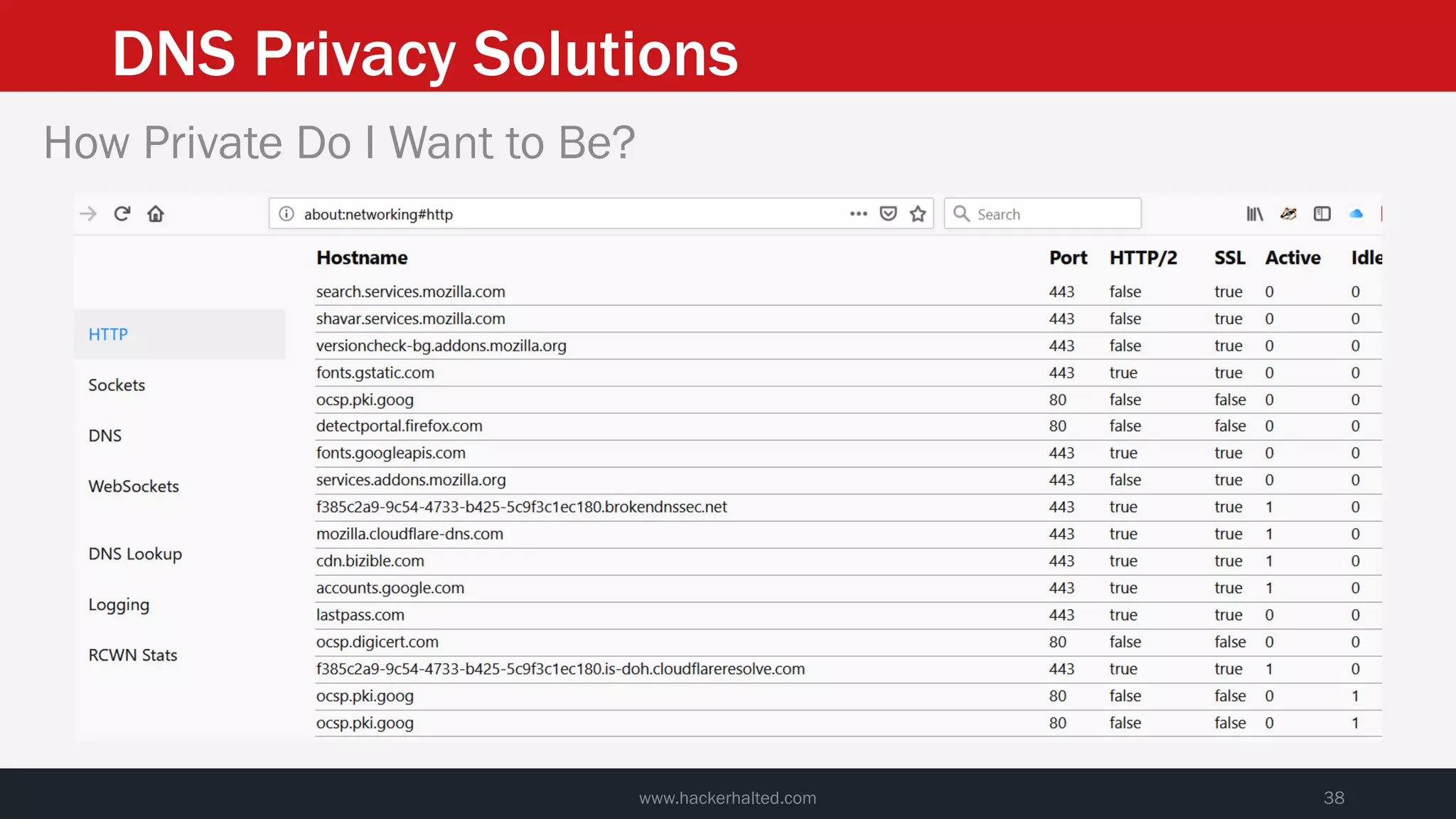
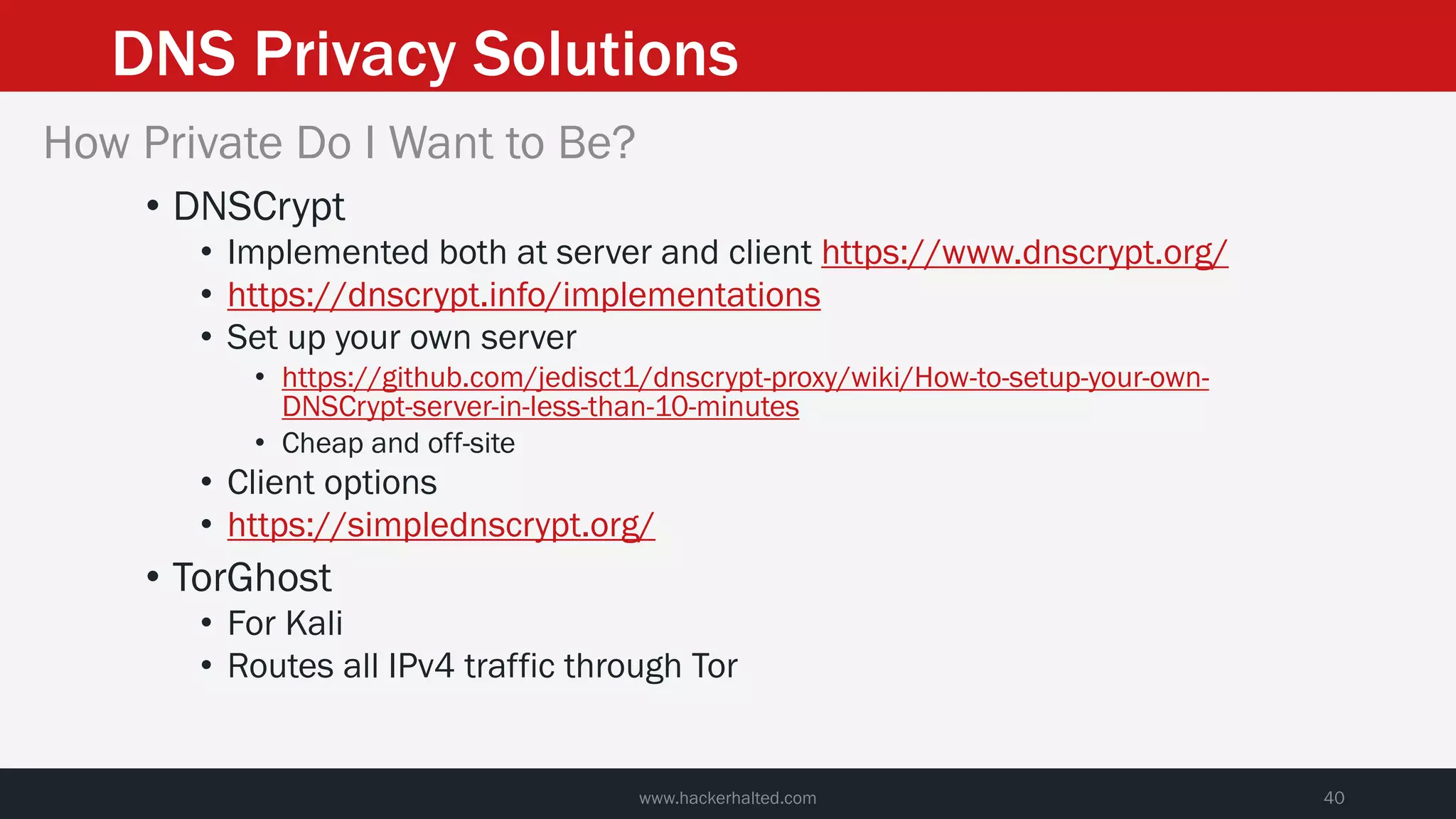
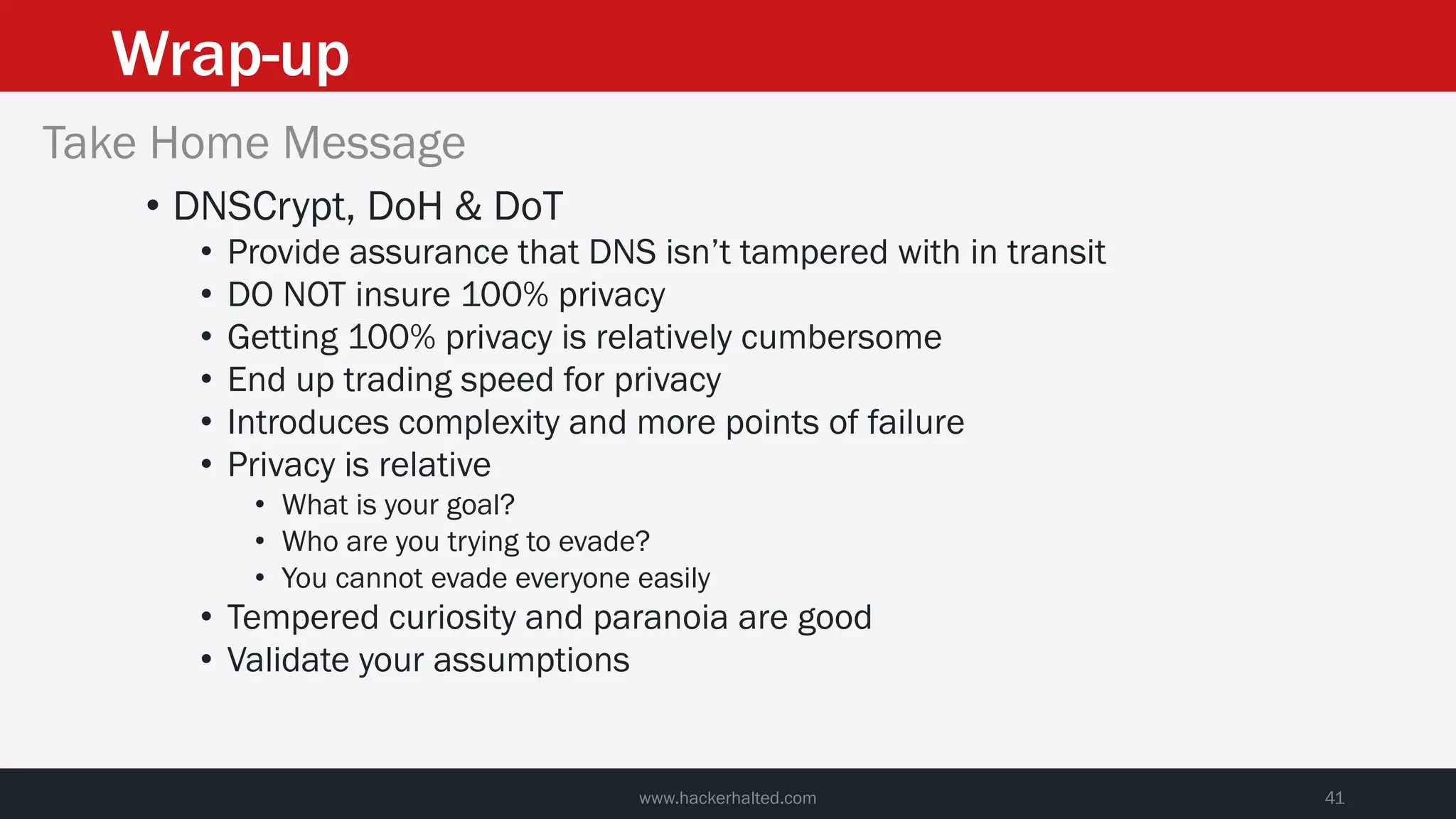
This document discusses strategies for reducing DNS data leakage and protecting online privacy. It begins with an introduction and overview of topics to be covered, including why DNS data is important from a privacy perspective, common DNS privacy exploits, insecure DNS resolution processes, and solutions for anonymizing DNS data like DNS over HTTPS and DNS over TLS. The document provides details on how DNS data can be tracked and leaked, as well as tools and techniques for analyzing DNS traffic and protecting privacy, including public secure resolvers, browser-based protections, VPNs, and running one's own recursive resolver. It concludes with taking privacy to varying degrees and balancing privacy with usability.