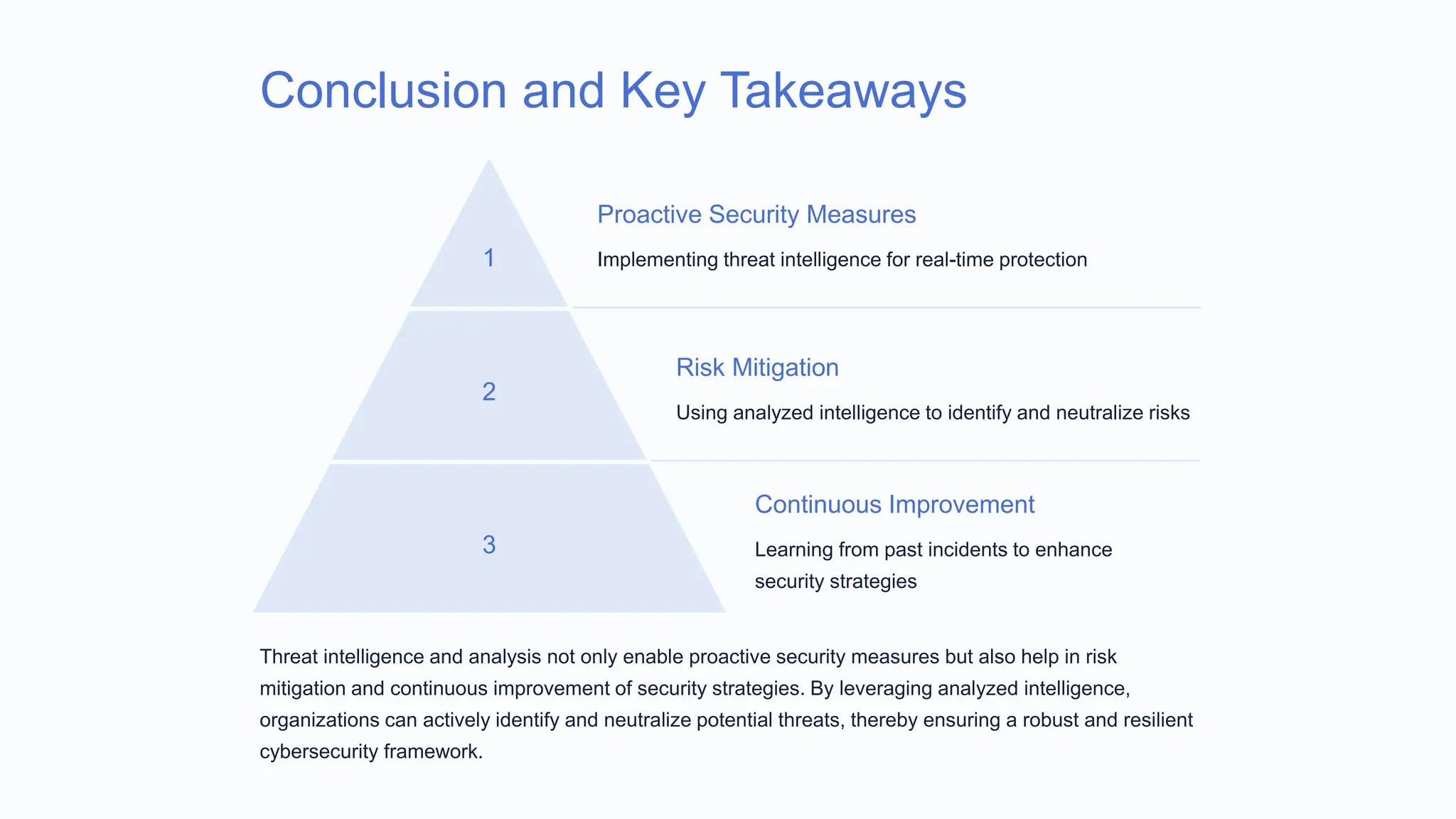
Threat intelligence and analysis are essential for identifying and mitigating security threats through proactive measures, contributing to enhanced cybersecurity postures. Methods of gathering this intelligence include open-source intelligence, cyber threat feeds, and dark web monitoring, while analysis techniques involve pattern recognition and machine learning. Challenges in implementing these programs include data standardization, skill shortages, and resource constraints.