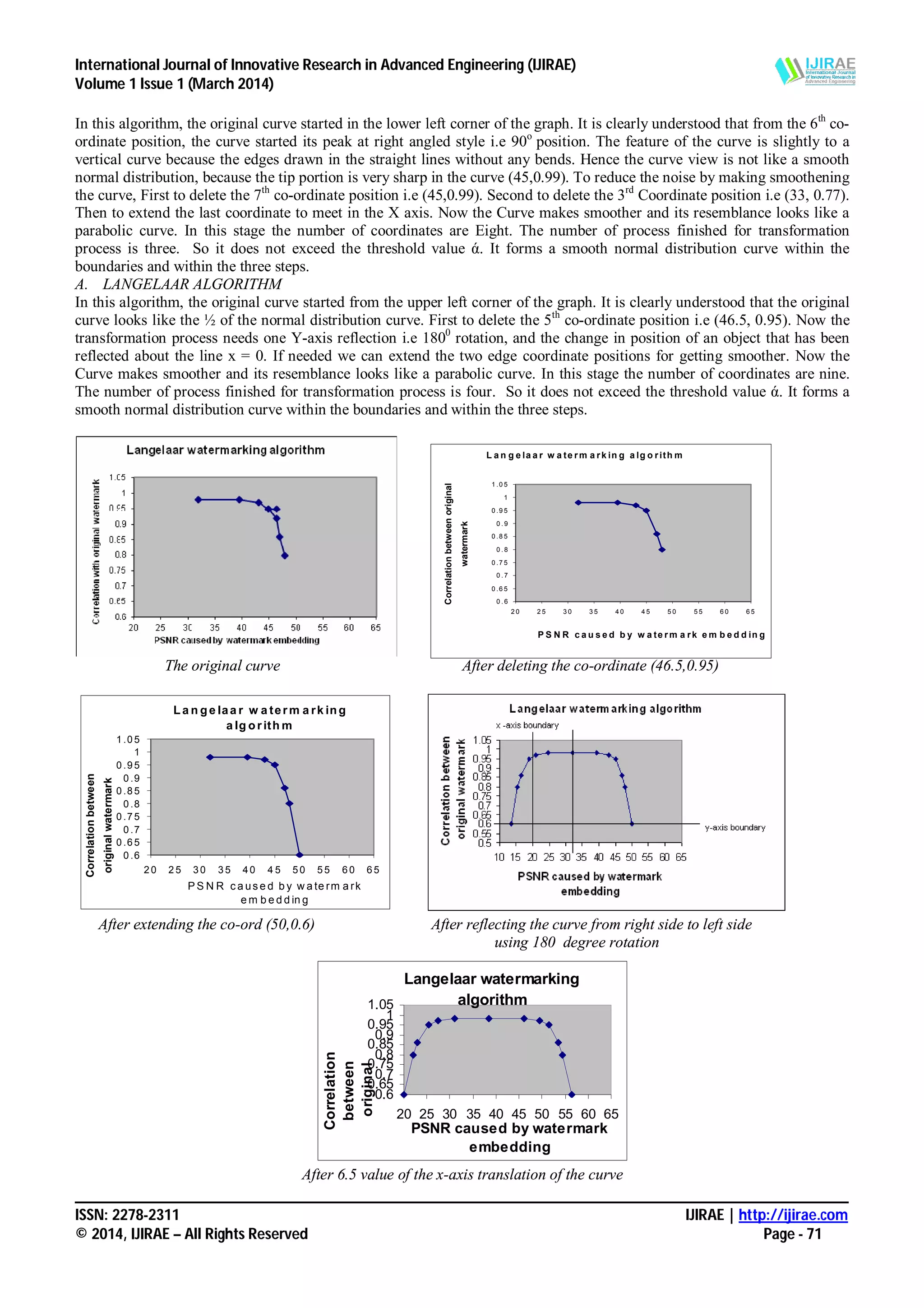
This document presents a comparative analysis of spatial and fractal watermarking algorithms, highlighting their roles in data security and ownership protection. It details various techniques, including Kutter, Bruyndonckx, and Langelaar algorithms in spatial watermarking, and Bas, Puate, and Davern in fractal watermarking, along with their mechanisms and effectiveness. The conclusion emphasizes that the Bruyn algorithm exhibits the best performance when compared to others in handling noise and maintaining watermark integrity.