The document outlines a laboratory exercise on computer network security, specifically demonstrating a cyber attack using open-source tools to exploit vulnerabilities in a target machine running Windows XP. It details steps like reconnaissance, gaining access, privilege escalation, and maintaining access through the use of tools like Nmap, Nessus, and Metasploit. Ethical hacking is emphasized, focusing on identifying vulnerabilities for corrective measures without destructive actions.
![Securitatea Retelelor de Calculatoare Lucrare de laborator Adrian Furtun ă M.Sc. C|EH [email_address]](https://image.slidesharecdn.com/mastersecuritatearetelelorlaborator-1263986080971-phpapp01/85/Laboratory-exercise-Network-security-Penetration-testing-1-320.jpg)





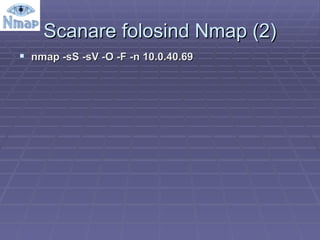
![Scanare folosind Nmap (1) http:// insecure.org nmap –h [fragmente] HOST DISCOVERY: -sP: Ping Scan - go no further than determining if host is online -PN: Treat all hosts as online -- skip host discovery -PS/PA/PU/PY[portlist]: TCP SYN/ACK, UDP or SCTP discovery to given ports -n/-R: Never do DNS resolution/Always resolve [default: sometimes] SCAN TECHNIQUES: -sS/sT/sA/sW/sM: TCP SYN/Connect()/ACK/Window/Maimon scans -sU: UDP Scan -sN/sF/sX: TCP Null, FIN, and Xmas scans PORT SPECIFICATION AND SCAN ORDER: -p <port ranges>: Only scan specified ports -F: Fast mode - Scan fewer ports than the default scan SERVICE/VERSION DETECTION: -sV: Probe open ports to determine service/version info SCRIPT SCAN: -sC: equivalent to --script=default --script=<Lua scripts>: <Lua scripts> is a comma separated list of directories, script-files or script-categories OS DETECTION: -O: Enable OS detection OUTPUT: -oN/-oX/-oS/-oG <file>: Output scan in normal, XML, s|<rIpt kIddi3, and Grepable format, respectively, to the given filename.](https://image.slidesharecdn.com/mastersecuritatearetelelorlaborator-1263986080971-phpapp01/85/Laboratory-exercise-Network-security-Penetration-testing-7-320.jpg)




![Obtinerea accesului – Metasploit (2) http:// www.metasploit.org Exploatam vulnerabilitatea ms08-067 (Conficker/Kido/Downadup) http://www.microsoft.com/technet/security/Bulletin/MS08-067.mspx Start Metasploit Web Exploits -> Search [ms08-067] Set TARGET - Windows XP SP2 English Set PAYLOAD - windows/meterpreter/bind_tcp (sau reverse_tcp) Set OPTIONS - RHOST (adresa IP a victimei) Exploit](https://image.slidesharecdn.com/mastersecuritatearetelelorlaborator-1263986080971-phpapp01/85/Laboratory-exercise-Network-security-Penetration-testing-13-320.jpg)

![Obtinerea accesului – Metasploit (4) http:// www.metasploit.org Stdapi: System Commands Command Description ------- ----------- clearev Clear the event log execute Execute a command kill Terminate a process ps List running processes reboot Reboots the remote computer shell Drop into a system command shell sysinfo Gets information about the remote system, such as OS Stdapi: User interface Commands Command Description ------- ----------- keyscan_dump Dump they keystroke buffer keyscan_start Start capturing keystrokes keyscan_stop Stop capturing keystrokes Meterpreter help [fragmente] Stdapi: File system Commands Command Description ------- ----------- cat Read the contents of a file to the screen cd Change directory del Delete the specified file download Download a file or directory edit Edit a file getlwd Print local working directory getwd Print working directory lcd Change local working directory lpwd Print local working directory ls List files mkdir Make directory pwd Print working directory rm Delete the specified file rmdir Remove directory upload Upload a file or directory](https://image.slidesharecdn.com/mastersecuritatearetelelorlaborator-1263986080971-phpapp01/85/Laboratory-exercise-Network-security-Penetration-testing-15-320.jpg)

![The End Va multumesc! Adrian Furtunã M.Sc. C|EH [email_address] ? I N T R E B A R I ?](https://image.slidesharecdn.com/mastersecuritatearetelelorlaborator-1263986080971-phpapp01/85/Laboratory-exercise-Network-security-Penetration-testing-17-320.jpg)