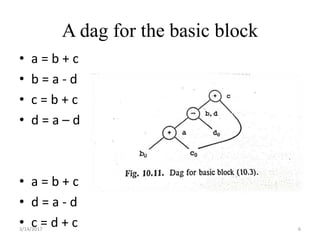
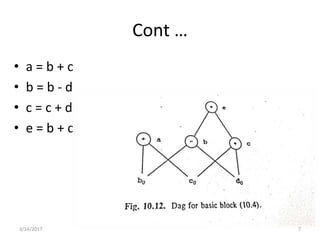
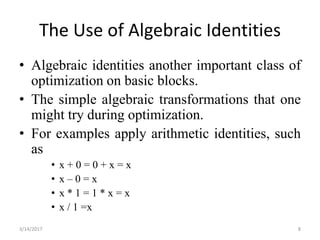
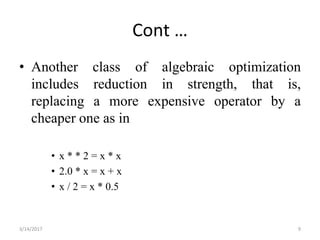
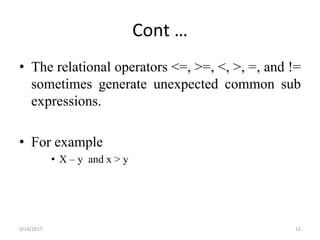
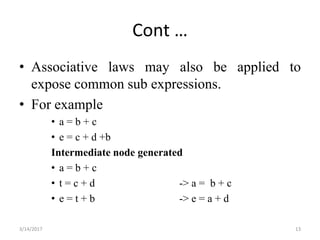
The document discusses various optimization techniques that can be applied to basic blocks in code including:
- Common subexpression elimination and dead code elimination to remove redundant computations.
- Algebraic transformations like applying arithmetic identities to simplify expressions and reduce strength of operations.
- Representing the basic block as a directed acyclic graph (DAG) to help identify common subexpressions and apply transformations using properties like commutativity.