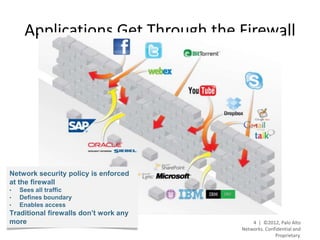
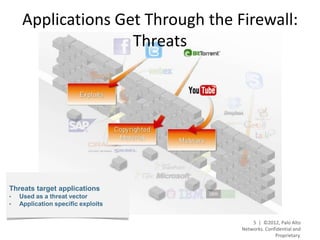
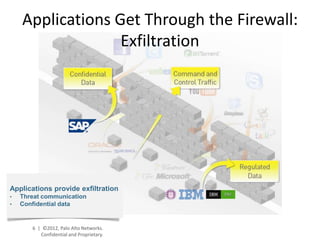
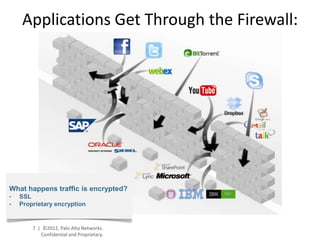
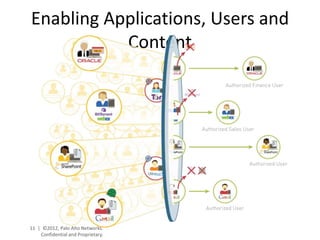
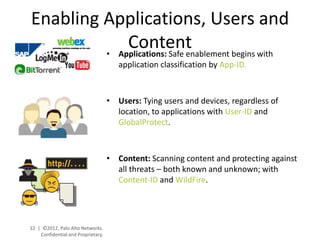
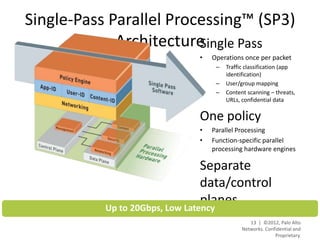
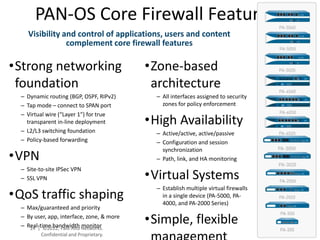
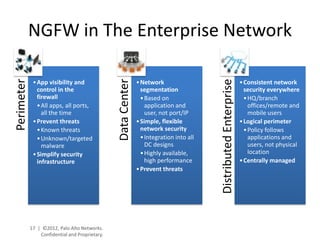
- Palo Alto Networks provides a next-generation firewall platform that can identify applications, users, and content to enable safe application usage while protecting against both known and unknown threats. This is achieved through technologies like App-ID, User-ID, Content-ID, WildFire, and SP3 architecture.
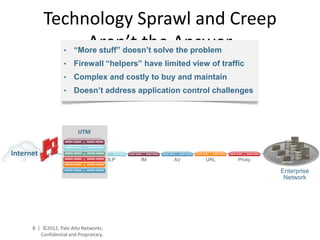
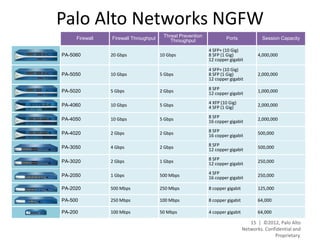
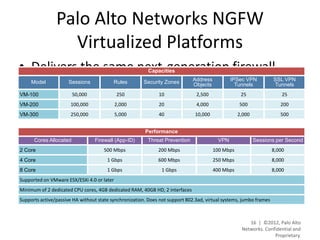
- The platform offers high performance, visibility, control, and threat prevention across applications, users, and content to replace traditional firewalls and security tools in a single device. This allows for a simplified security posture.
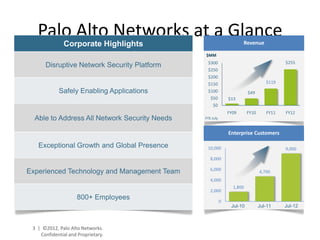
- Palo Alto Networks has seen strong revenue growth and increased its global customer base significantly in recent years, showing the success of its disruptive next-generation firewall approach.