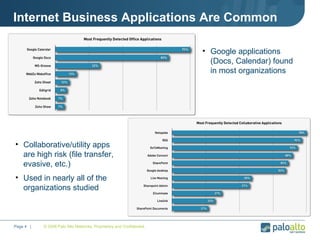
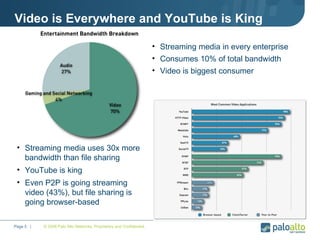
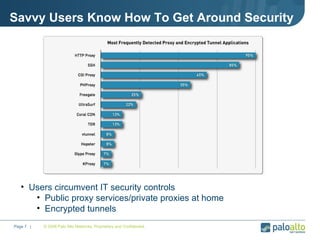
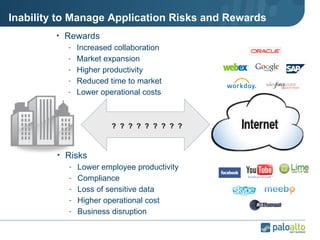
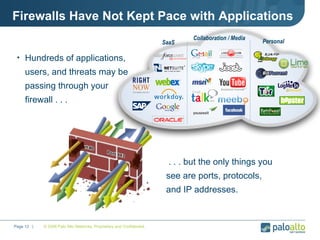
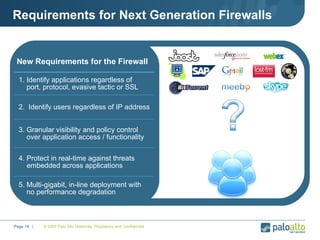
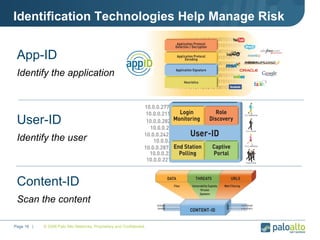
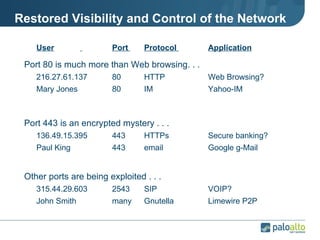
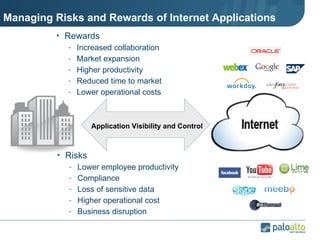
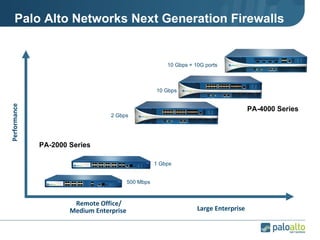
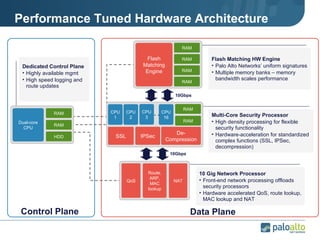
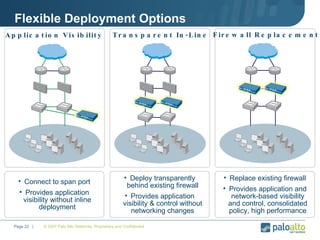
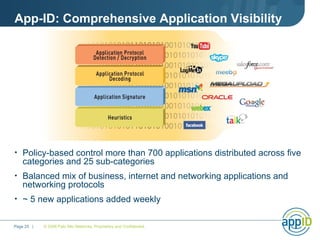
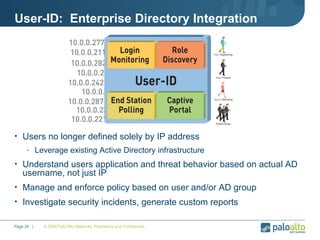
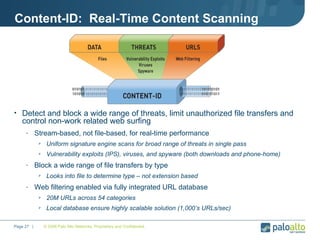
The document discusses the results of analyzing network traffic across 60 enterprises. It found that HTTP has become the universal protocol and video consumes the most bandwidth. Most common threats exploit popular applications. Next generation firewalls are needed that can identify applications, users, and threats to better manage risks and allow business benefits of internet applications.