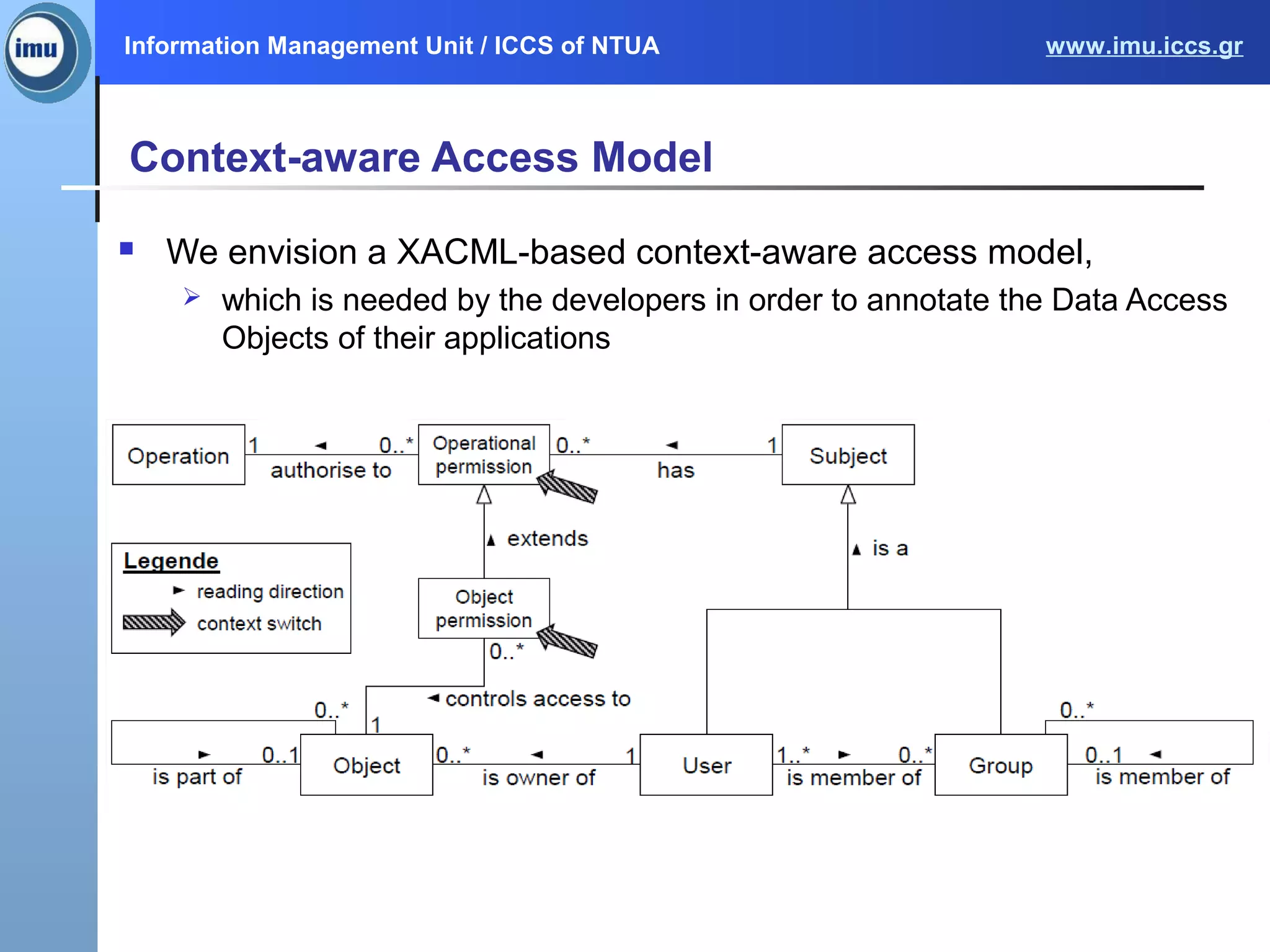
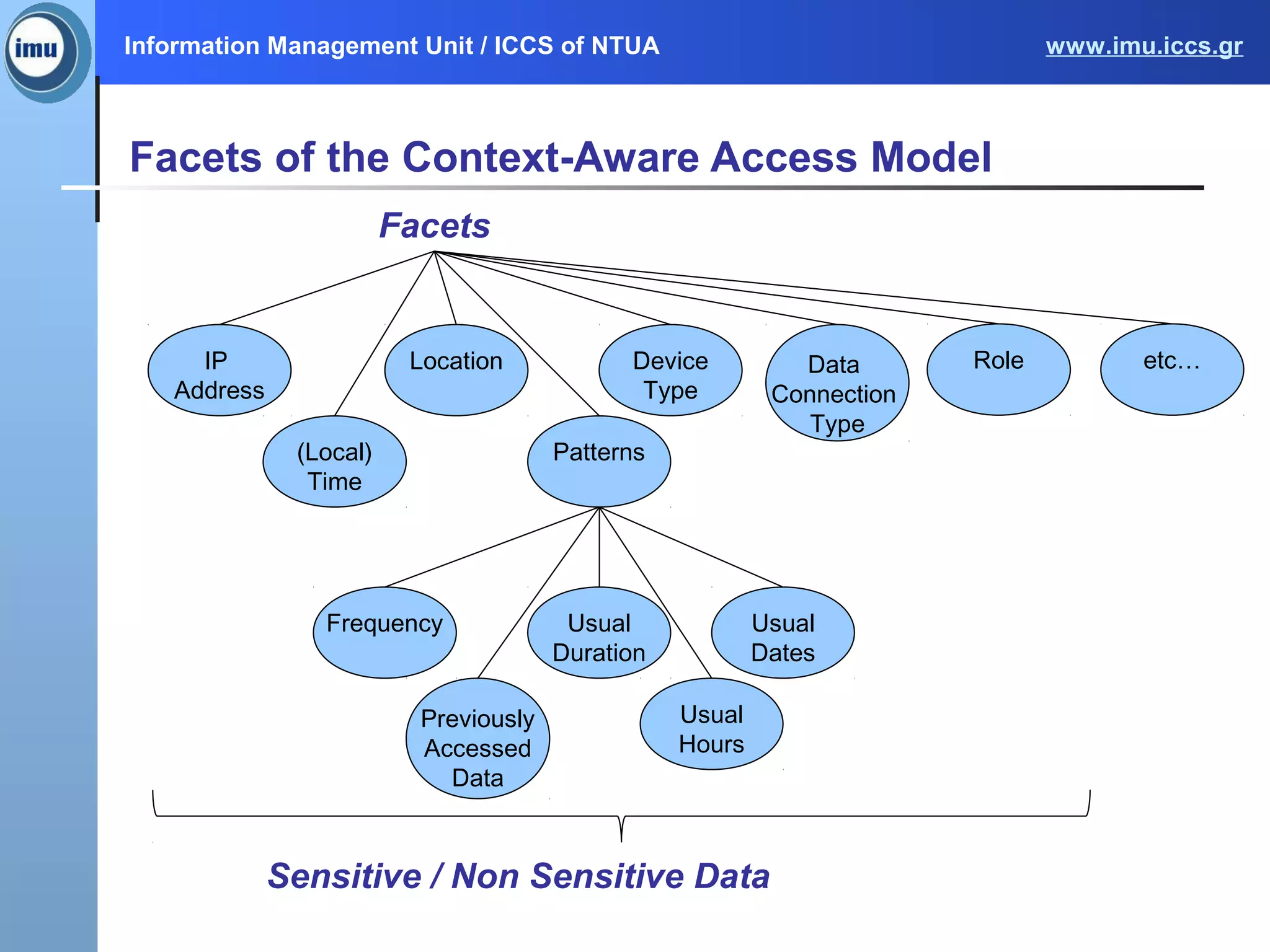
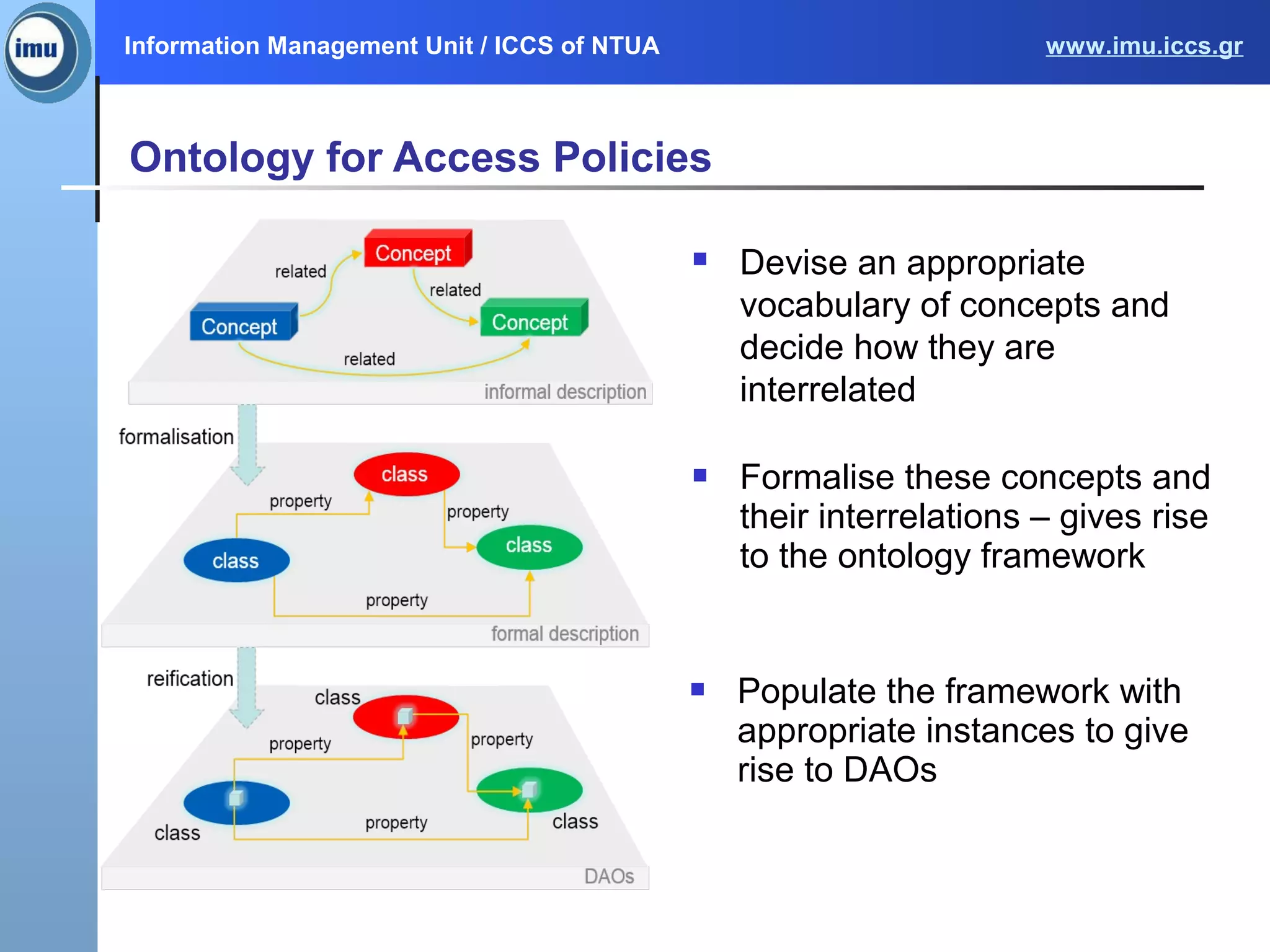
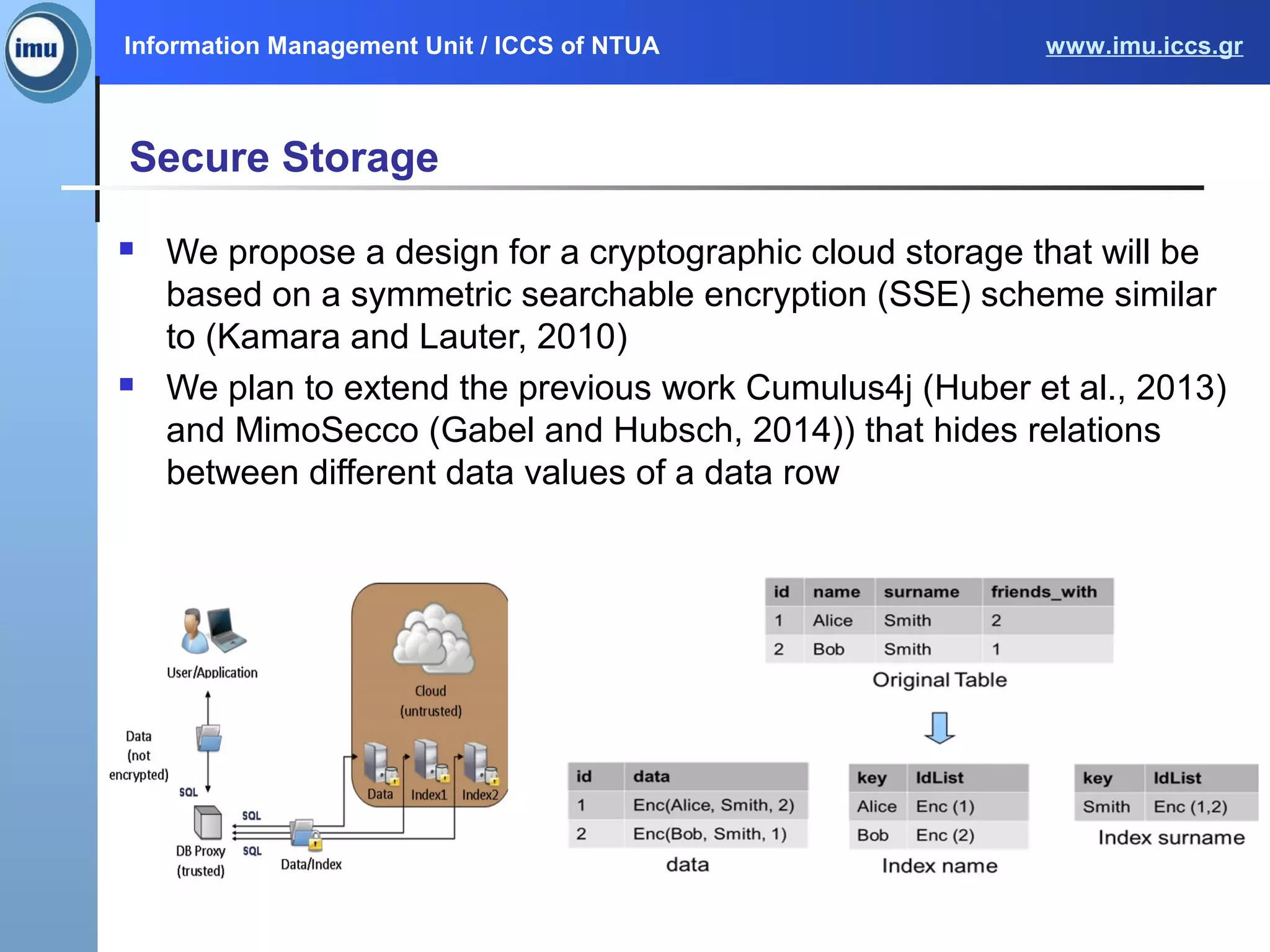
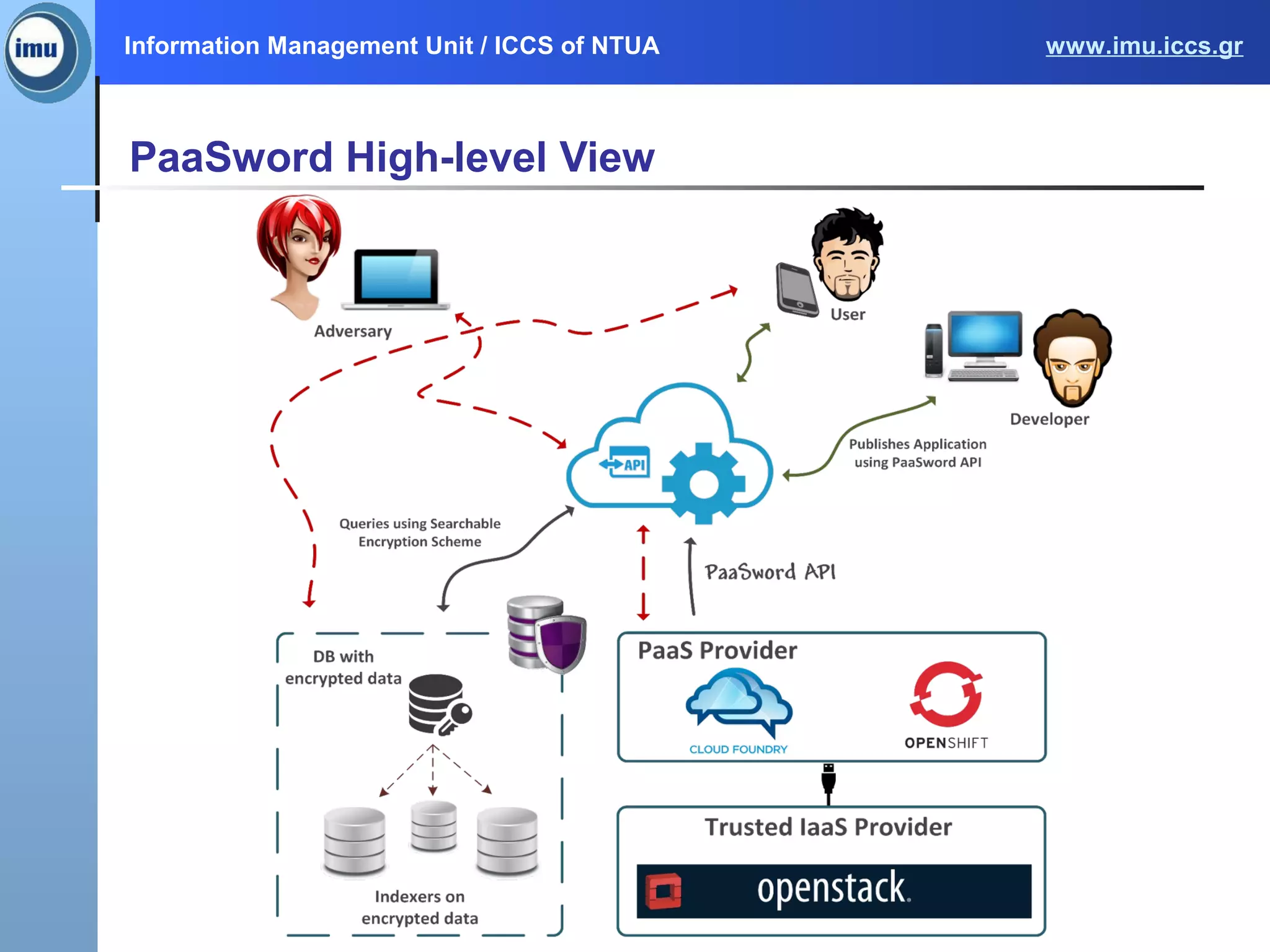
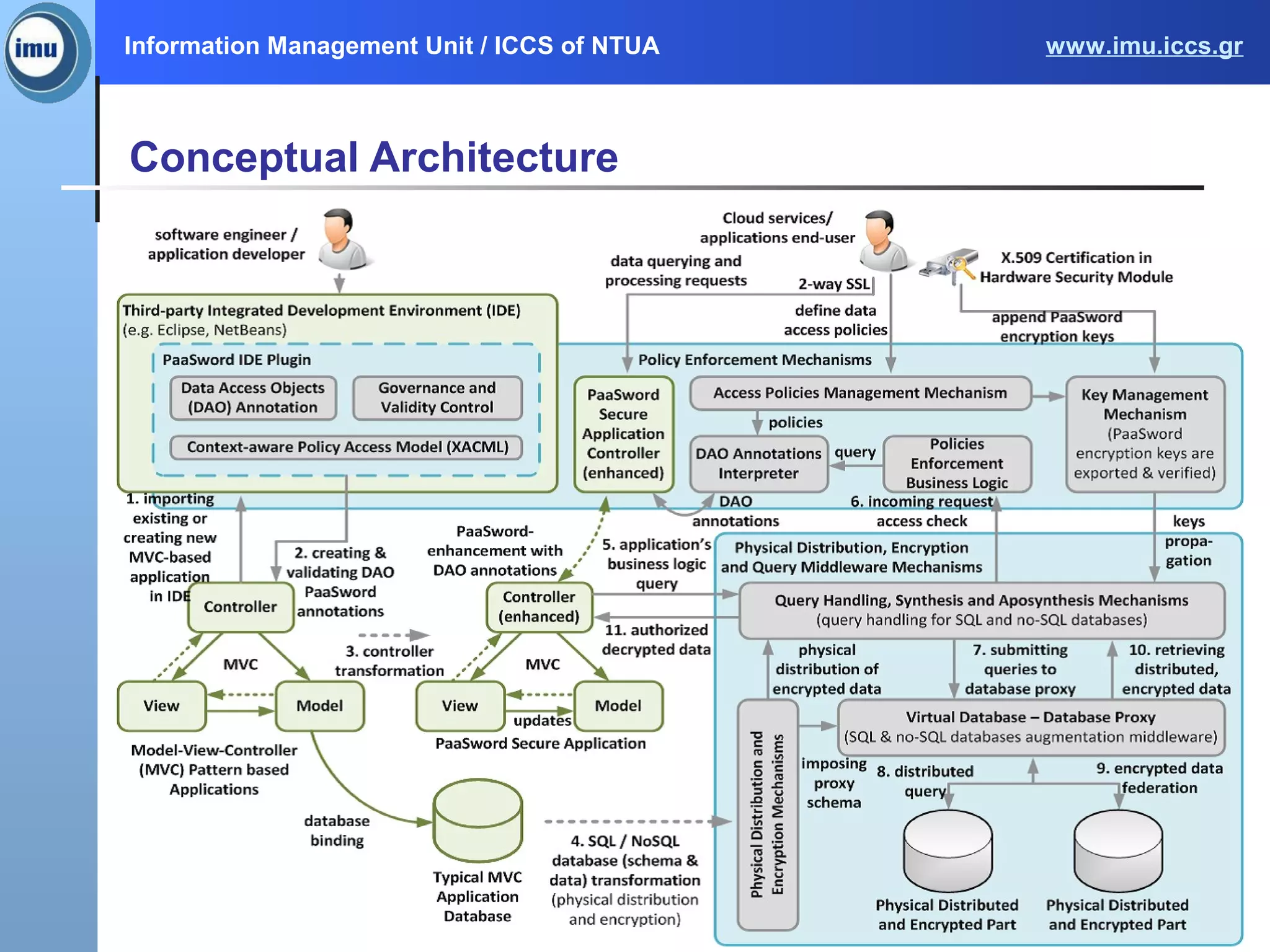
The document presents the Paasword framework, a holistic approach to data privacy and security for cloud services, addressing significant challenges like data leakage and account hijacking. It discusses the need for robust access control models and secure data storage solutions, alongside the proposal for a context-aware access model to enhance security measures. Future work includes implementing and validating the framework through various pilot projects aimed at protecting sensitive information across multiple cloud environments.