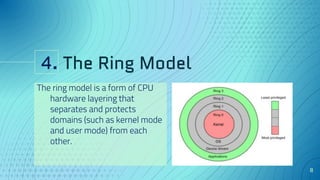
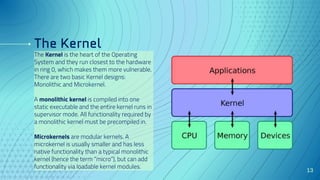
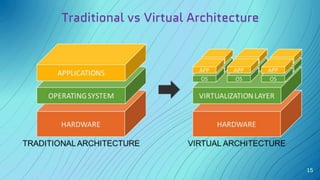
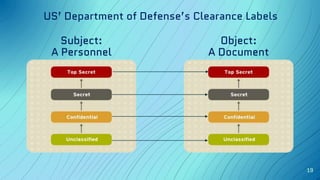
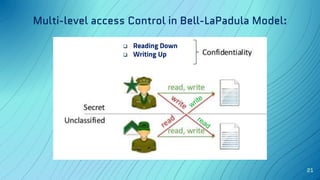
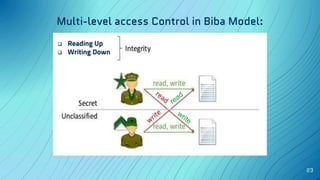
The document discusses the concept of security architecture and design, emphasizing its role in creating secure computer systems through hardware, software, and logical models. It outlines the benefits of strong security architecture for businesses, including reducing breaches and ensuring compliance with data security standards. Additionally, it explains design techniques such as layering, abstraction, and the evaluation models used to assess system security.