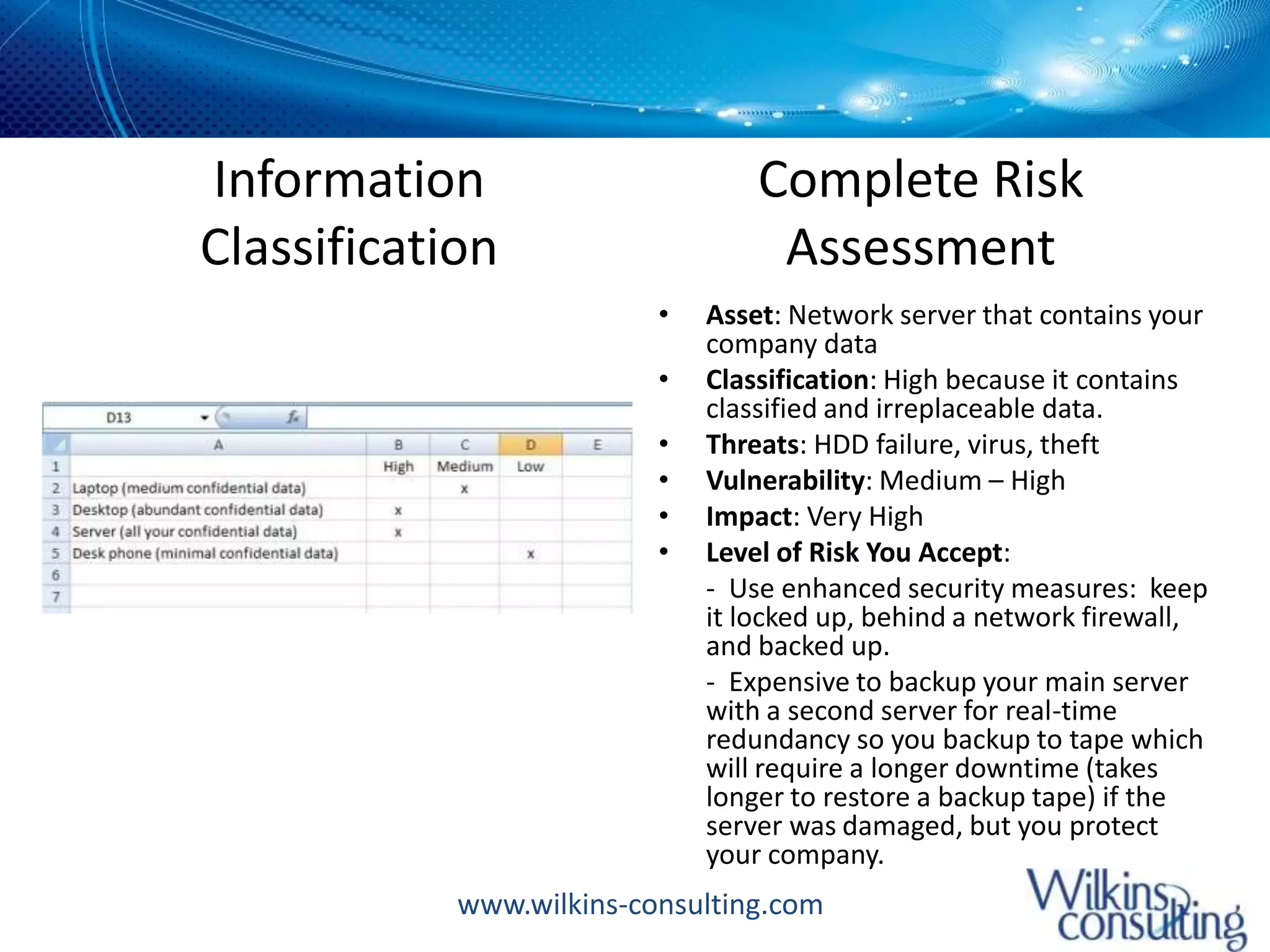
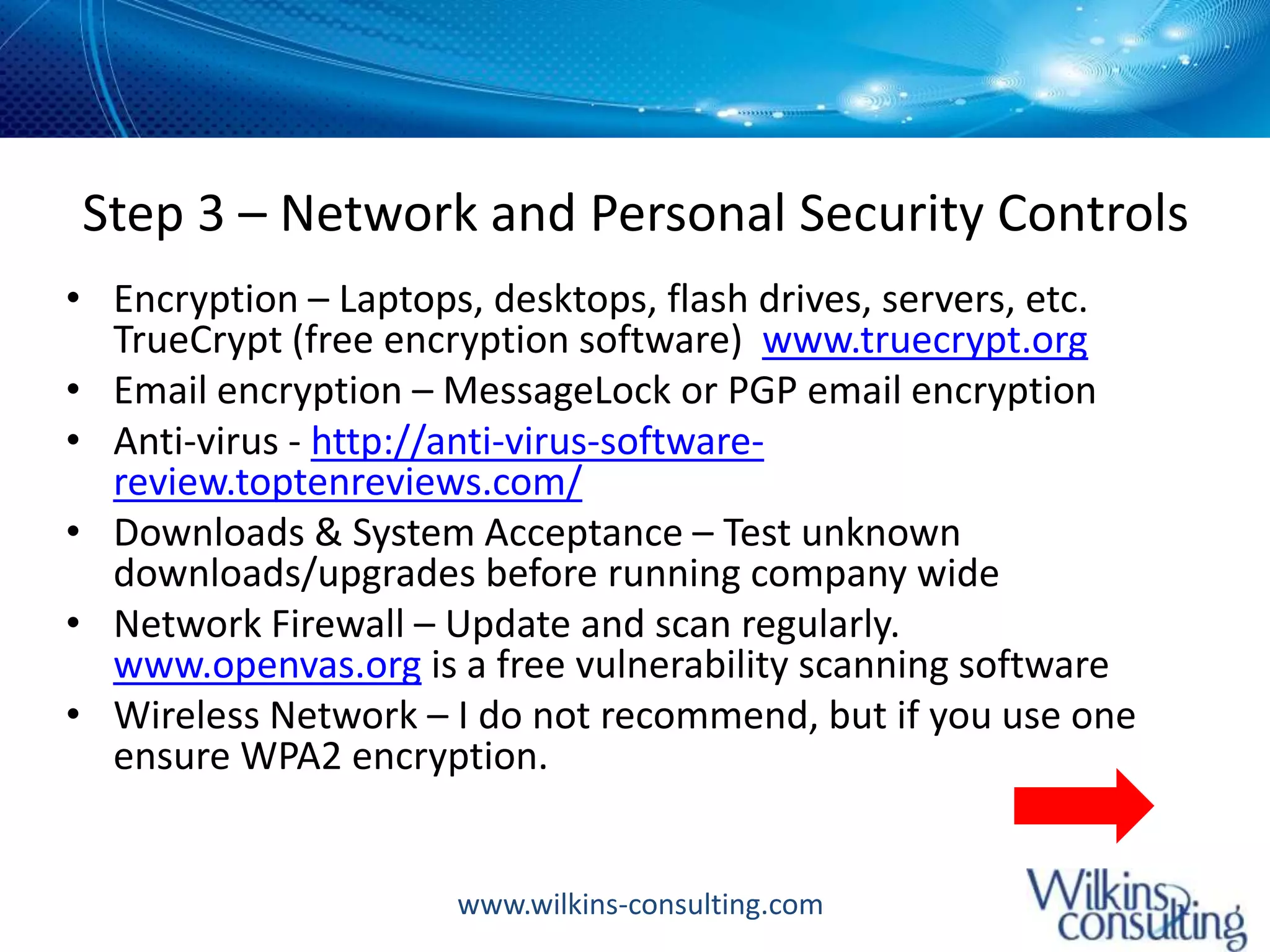
The document outlines a 5-step data security plan for small businesses based on ISO 27001 principles, highlighting the serious threat of data breaches which can lead to financial ruin. It emphasizes the importance of asset identification, access controls, physical security, document controls, and general security measures to protect sensitive information. The document also suggests implementing background checks, regular audits, and emergency response plans to enhance overall security.