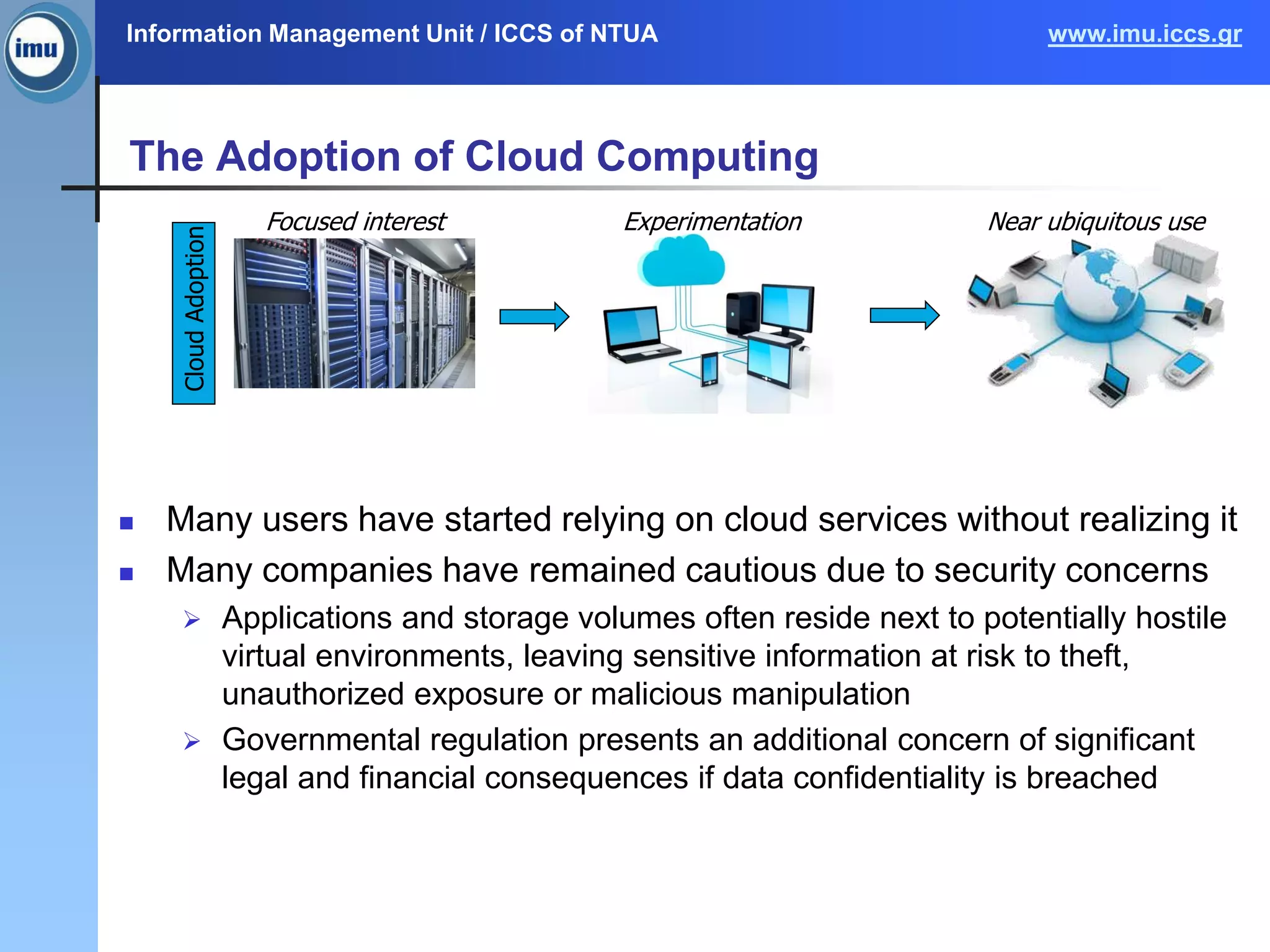
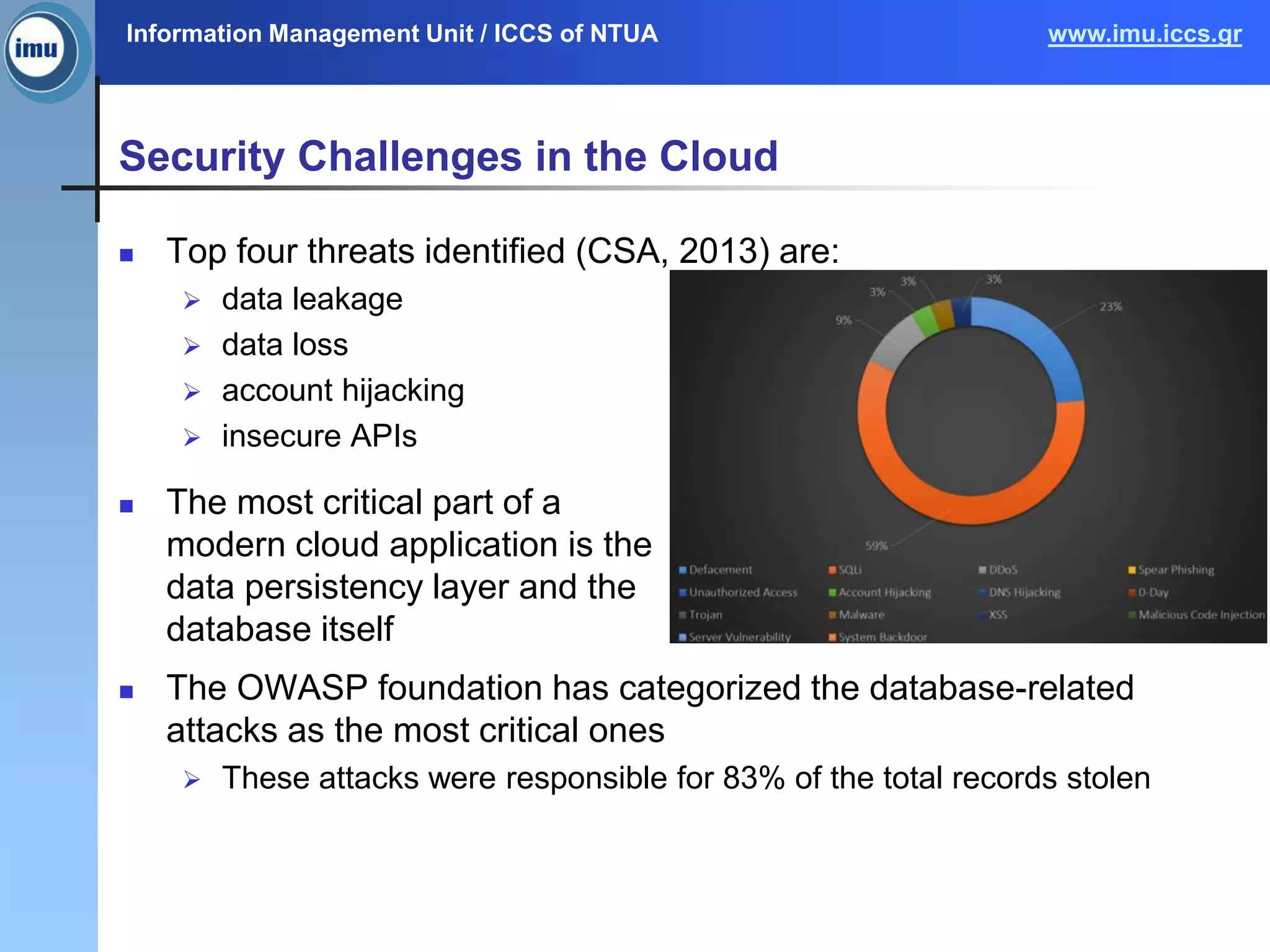
The document discusses a survey on context security policies in cloud computing, addressing various security challenges such as data leakage, loss, and account hijacking. It explores policy modeling techniques, comparing traditional access control models with context-aware approaches, and highlights the limitations of existing models. Future work aims to develop and validate context and policy models for improved security in cloud applications.









![Information Management Unit / ICCS of NTUA www.imu.iccs.gr
Policy Modeling
Semantically-rich Policy Description
employs ontologies in order to assign meaning to actors, actions
and resources
ability to reason about policy compliance generically
identification of inter-policy relations such as inconsistent policies, and
overlapping policies
portability, visibility, and reusability of policies
facilitates policy governance
KAoS [Uszok et al., 2004], Rei [Kagal et al., 2003], [Hu et al.,
2011]](https://image.slidesharecdn.com/cloudspd15context-awaresecuritymodelsyiannissimos-151216165255/75/A-Survey-on-Context-Security-Policies-in-the-Cloud-16-2048.jpg)