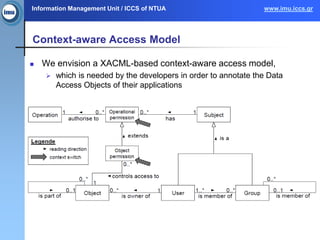
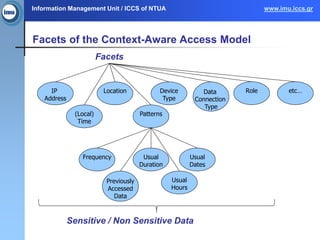
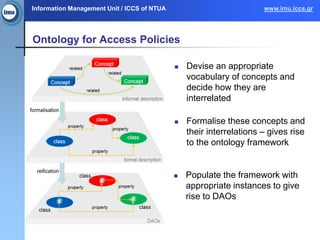
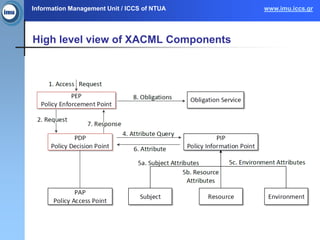
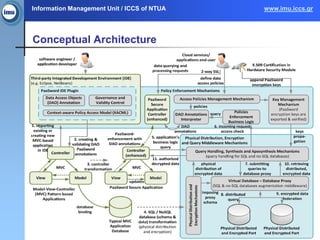
The document presents the paasword framework, a holistic approach to enhancing data privacy and security for cloud services, addressing challenges such as data leakage, loss, account hijacking, and insecure APIs. It discusses existing access control models, highlights security threats in cloud environments, and proposes a context-aware access model to improve policy enforcement and management. The framework aims to ensure secure data outsourcing and will be validated through various pilot projects focused on encrypted data management and personal information protection.