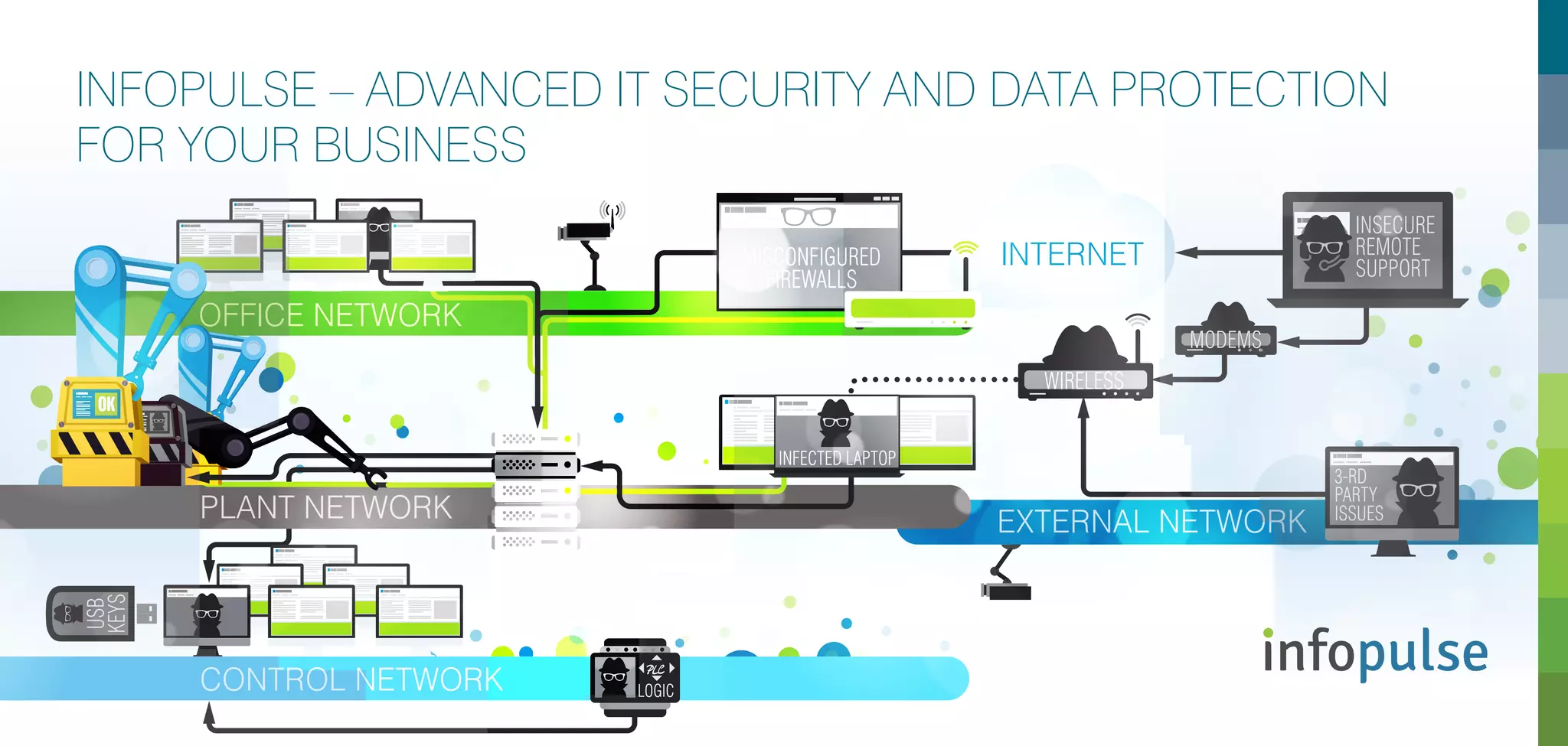
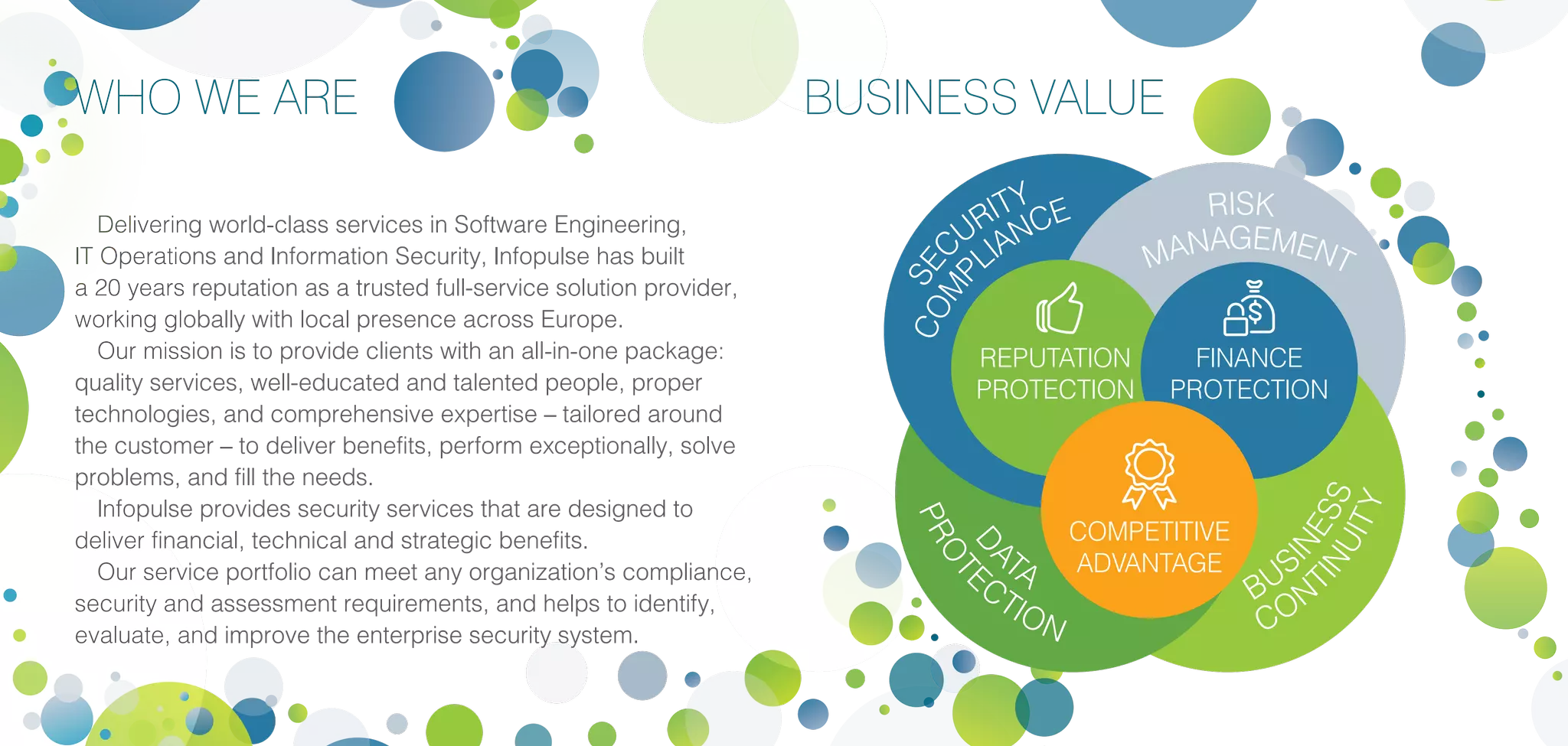
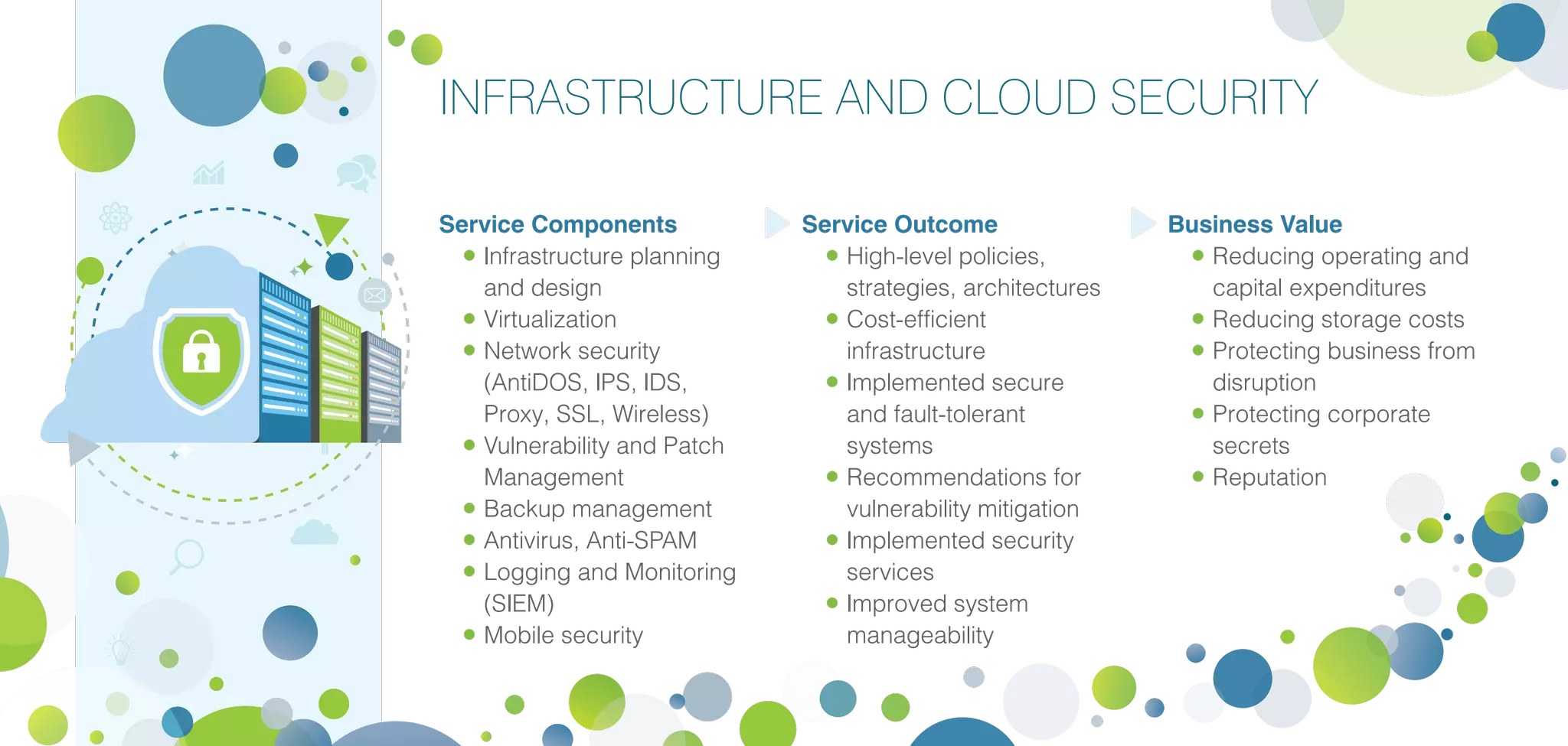
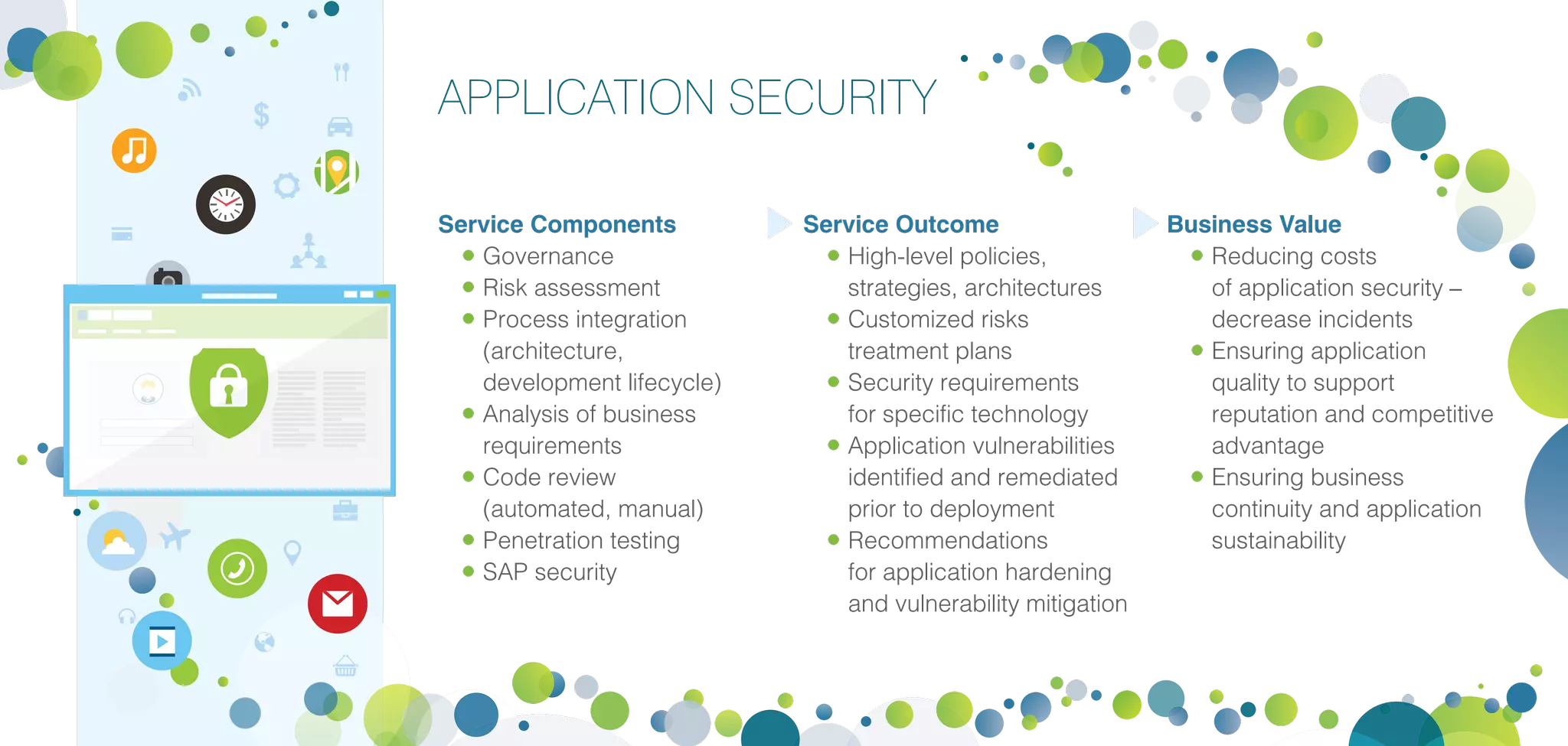
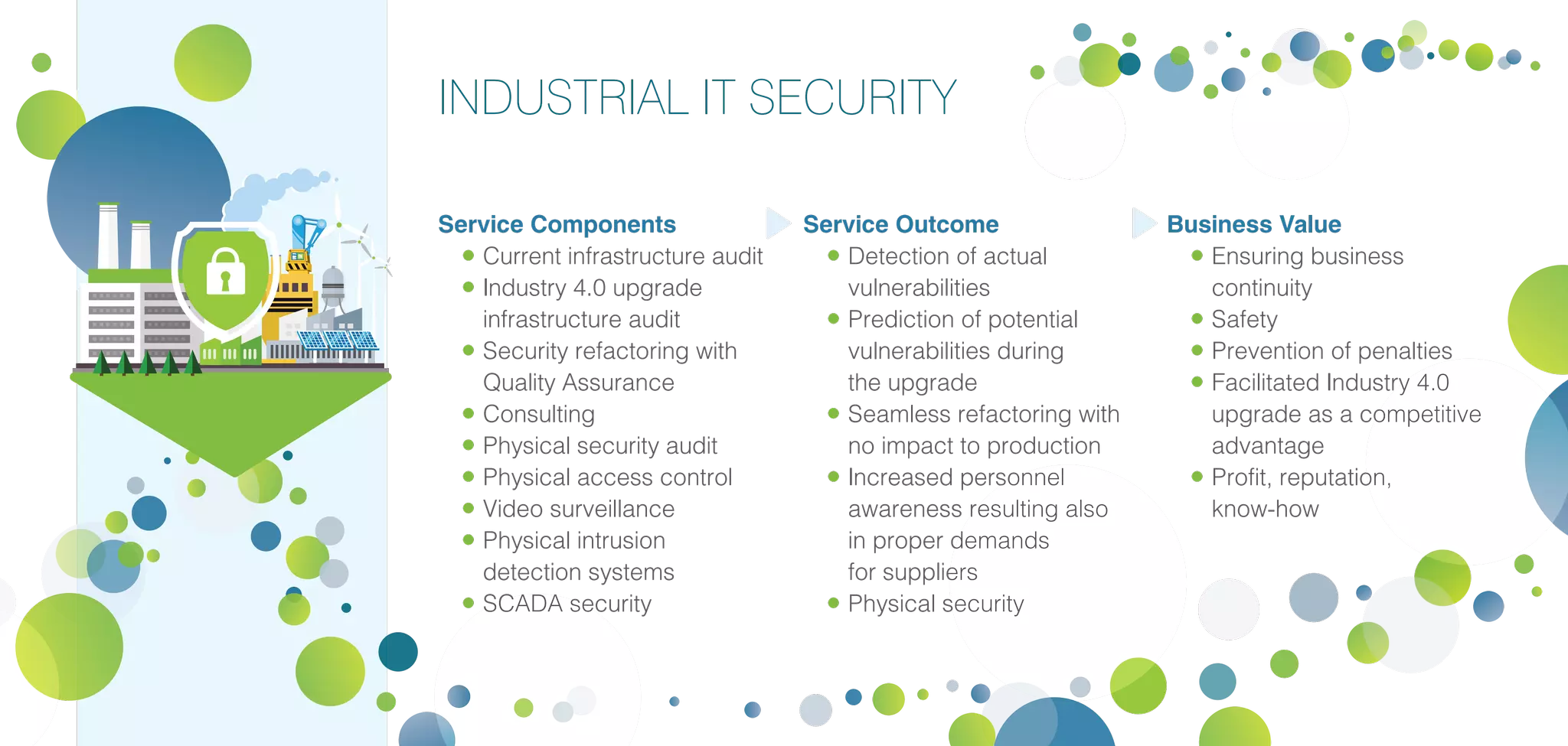
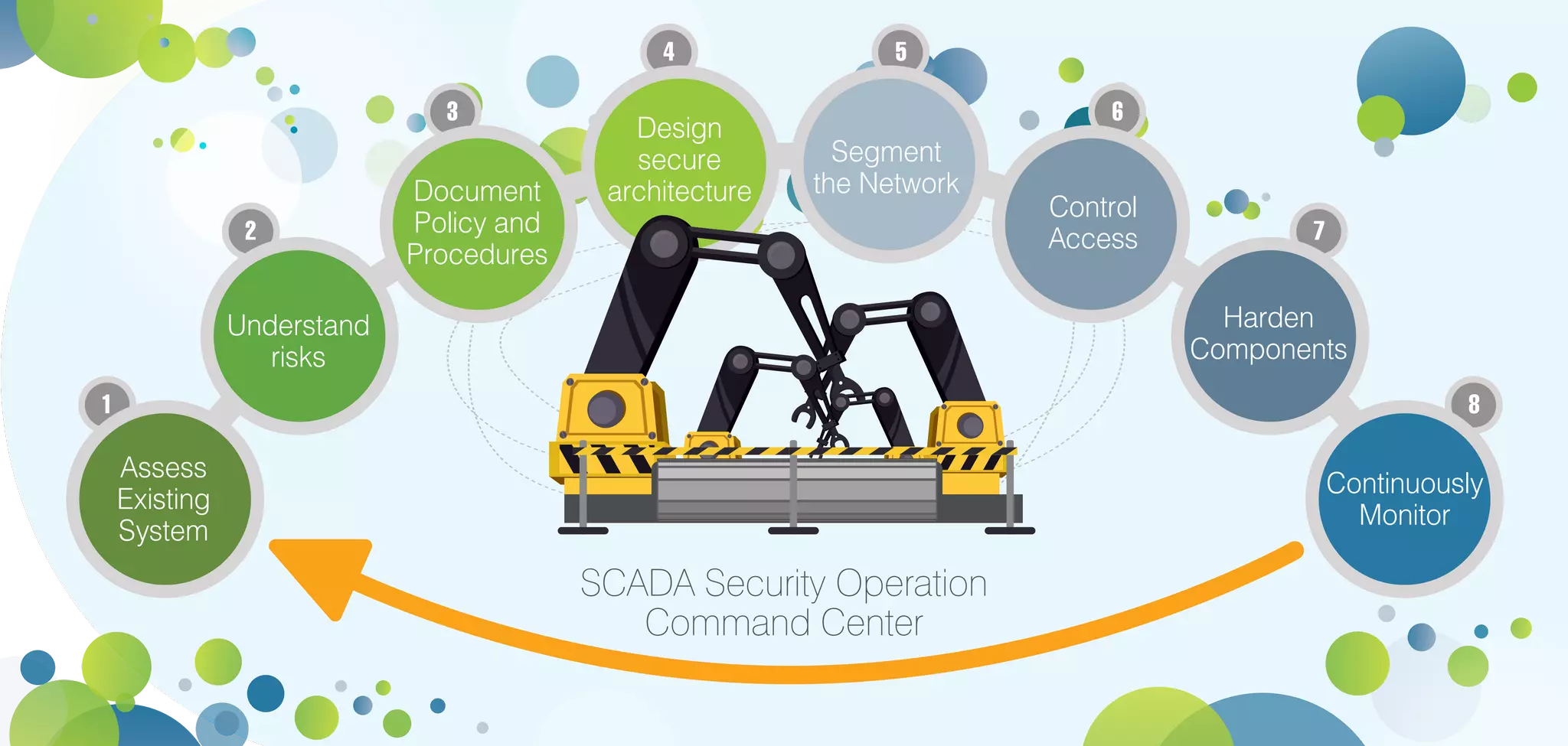
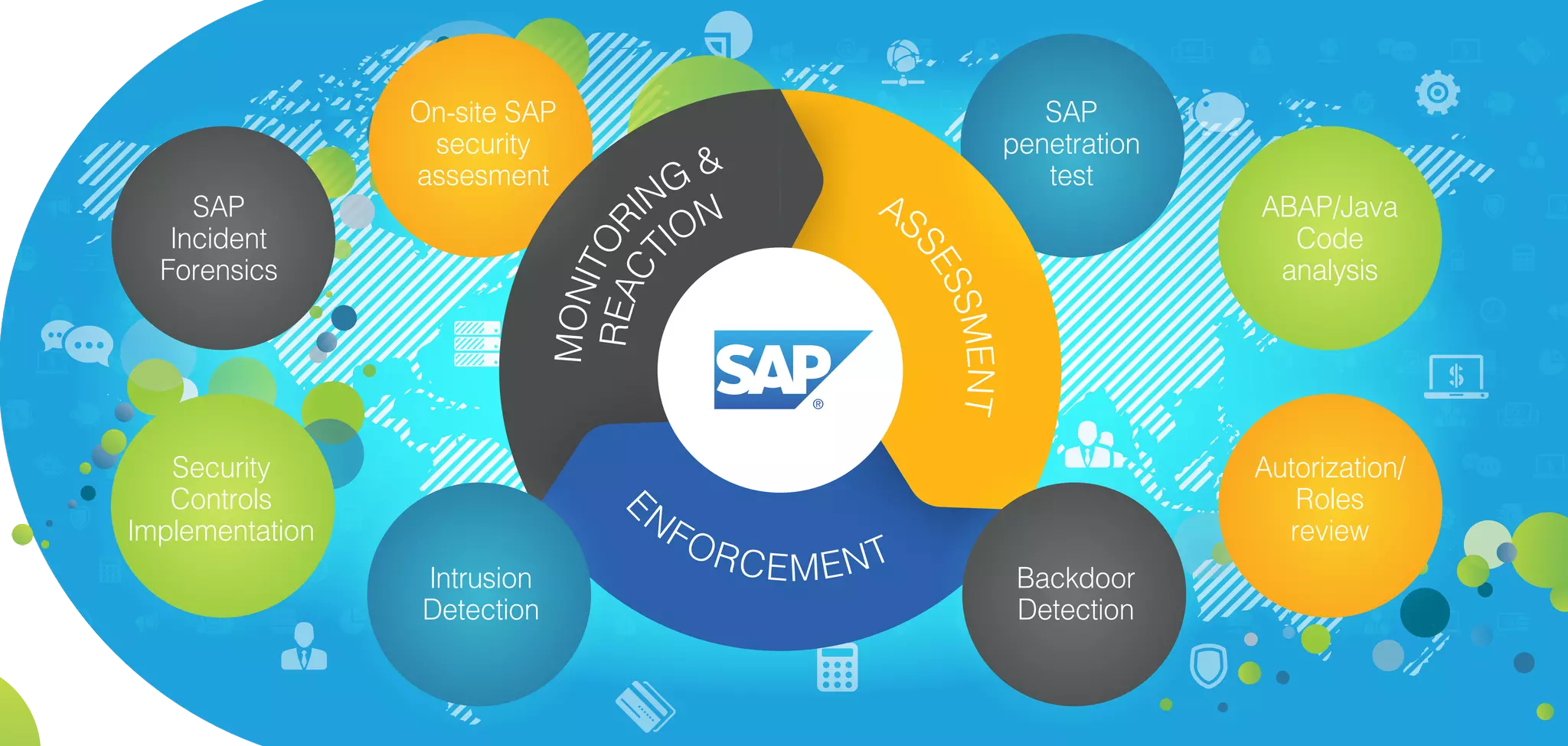
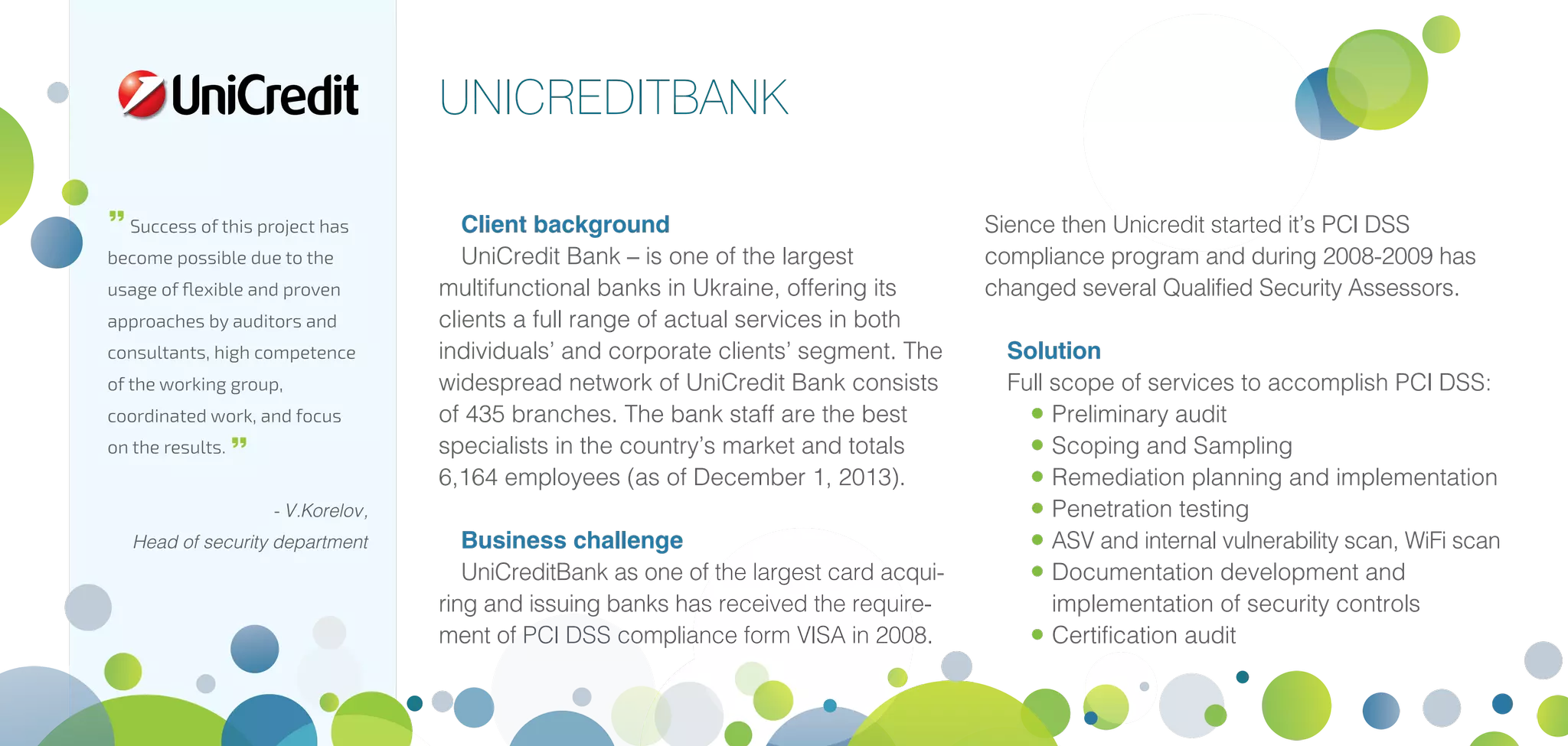
Infopulse offers advanced IT security and data protection services, leveraging 20 years of experience to enhance enterprise security frameworks across various sectors. Their comprehensive service portfolio includes risk management, compliance audits, and tailored solutions for endpoints, application, and infrastructure security, aiming to bolster organizations against evolving cyber threats. Infopulse's approach includes thorough assessments, implementation of robust security measures, and continuous monitoring, ensuring businesses maintain operational integrity and protect sensitive data.