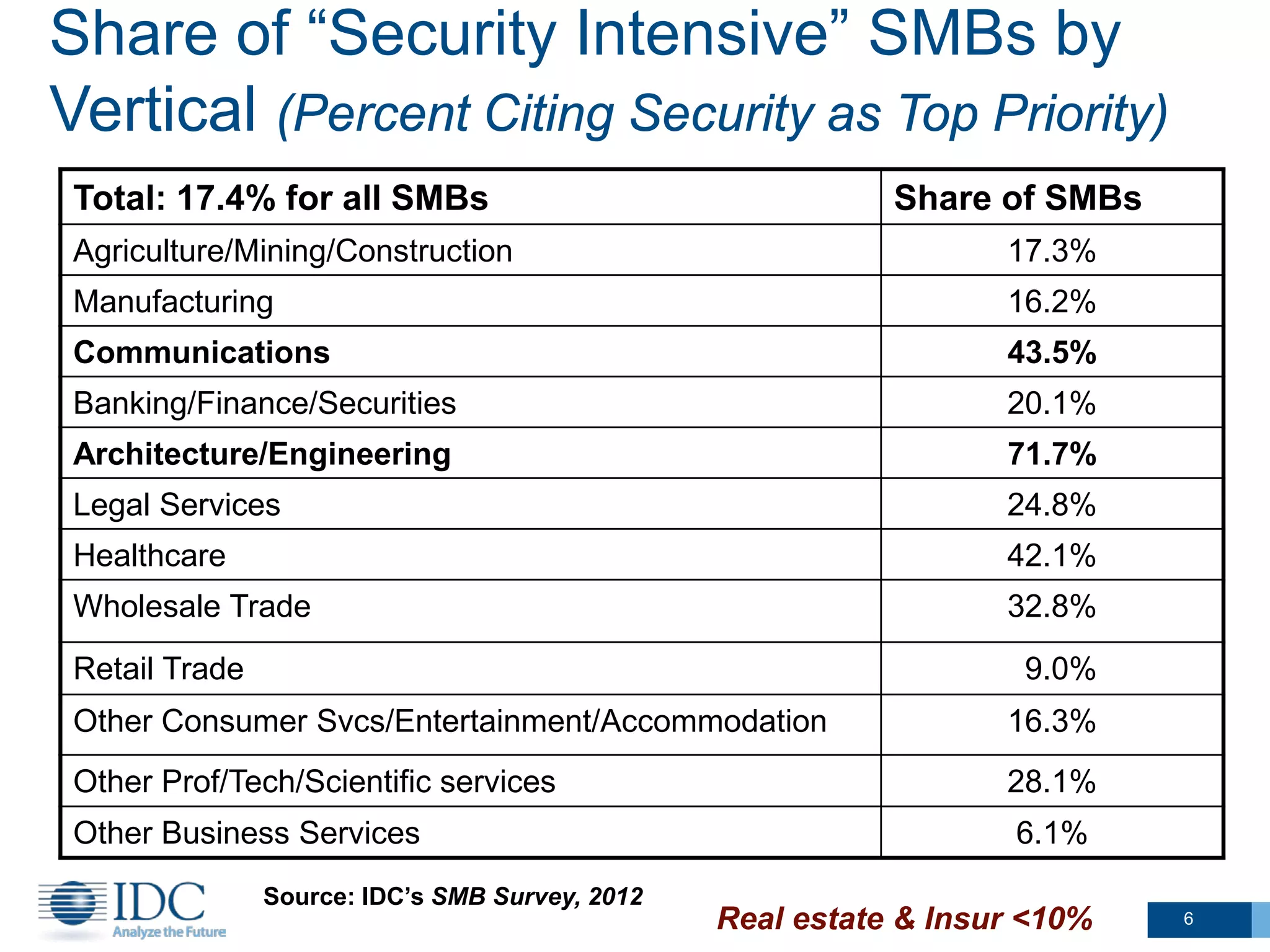
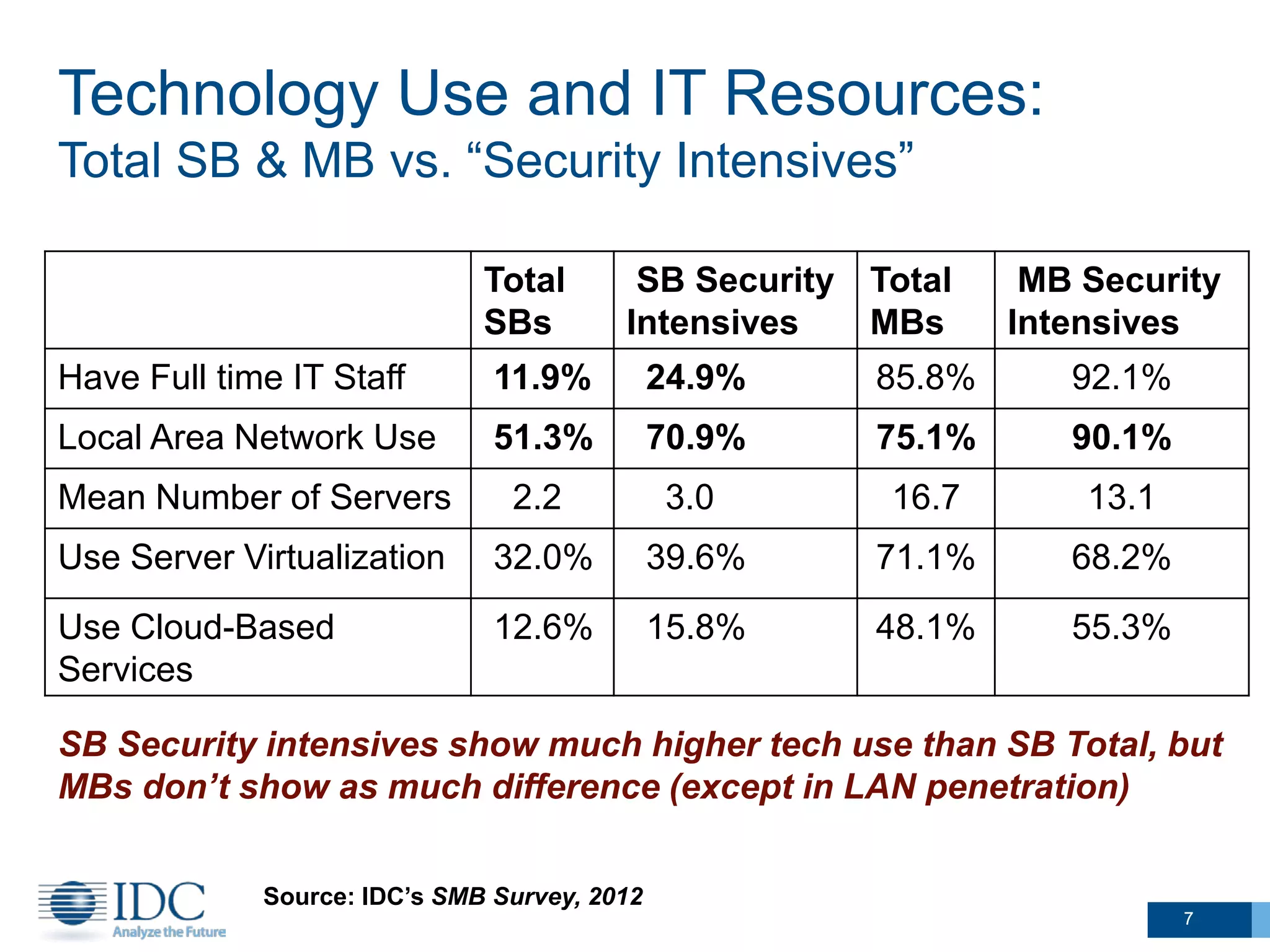
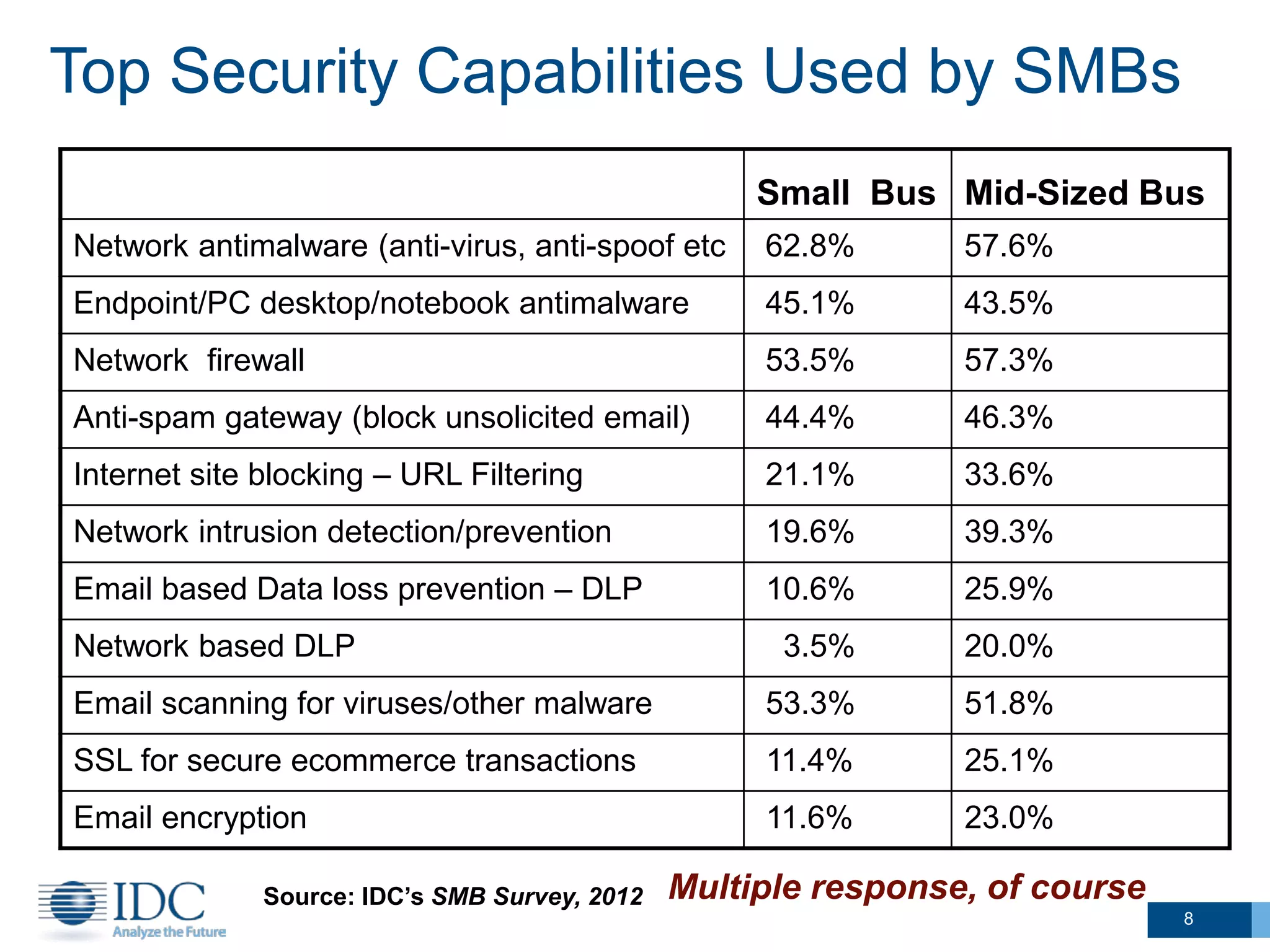
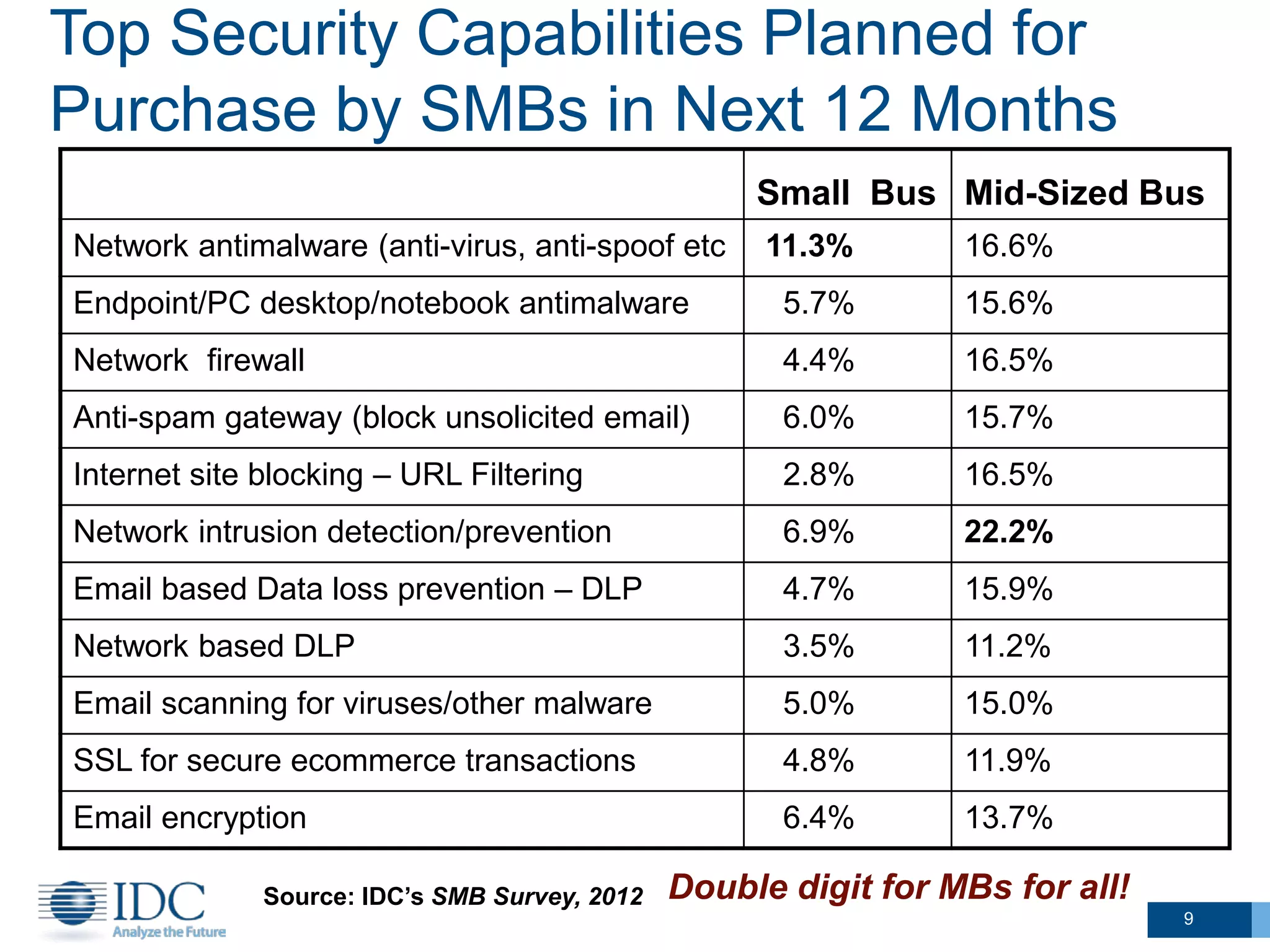
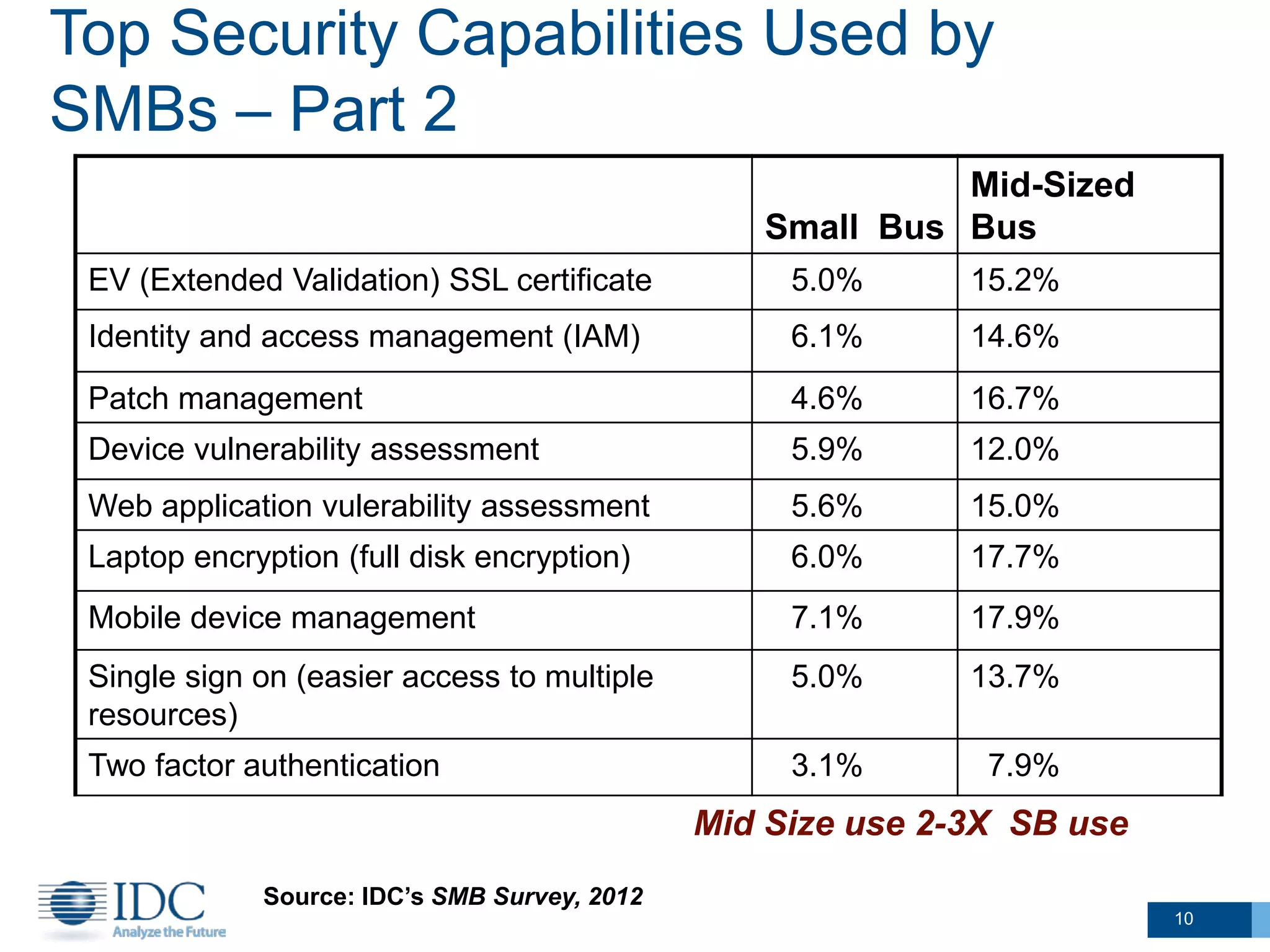
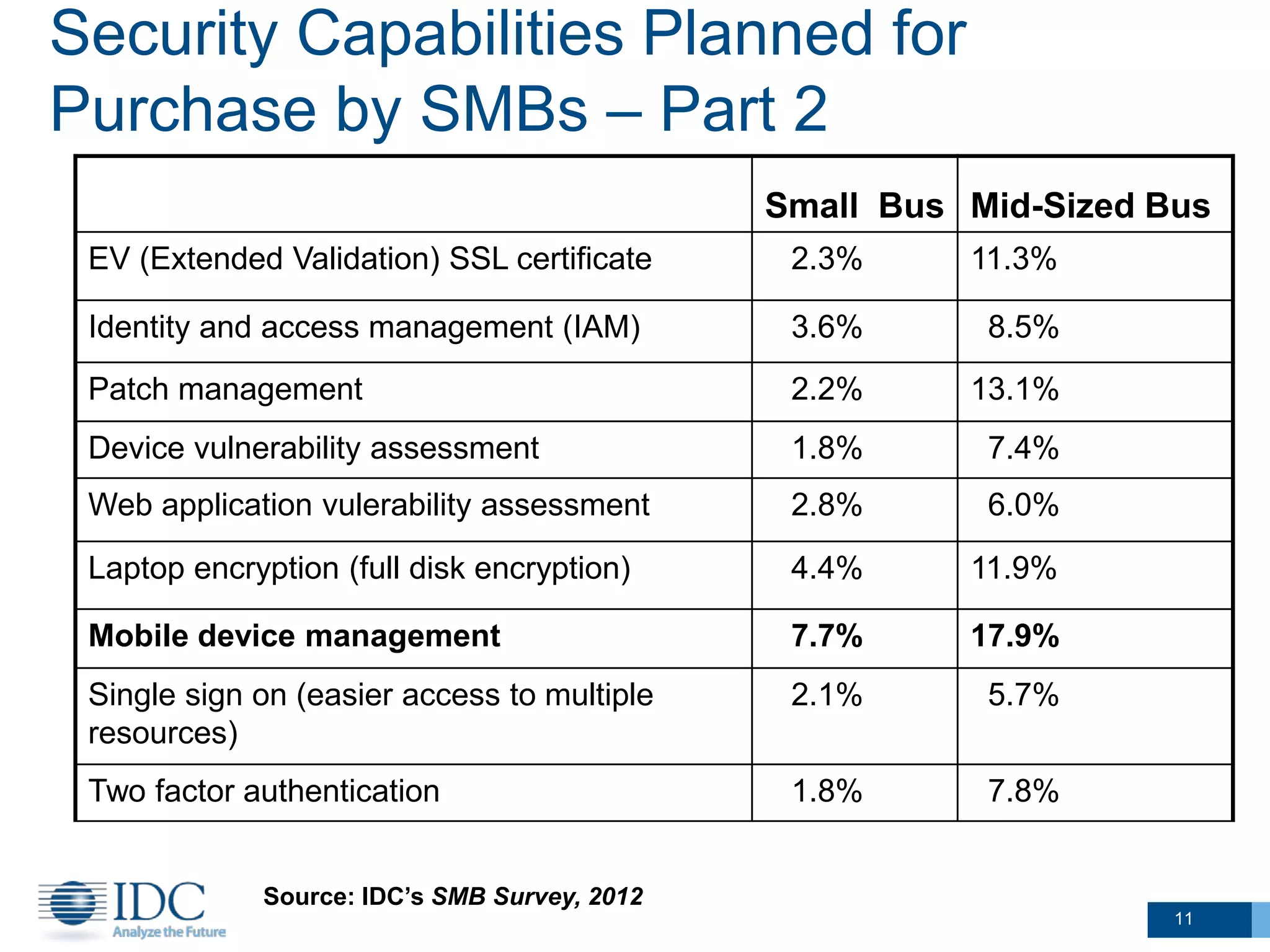
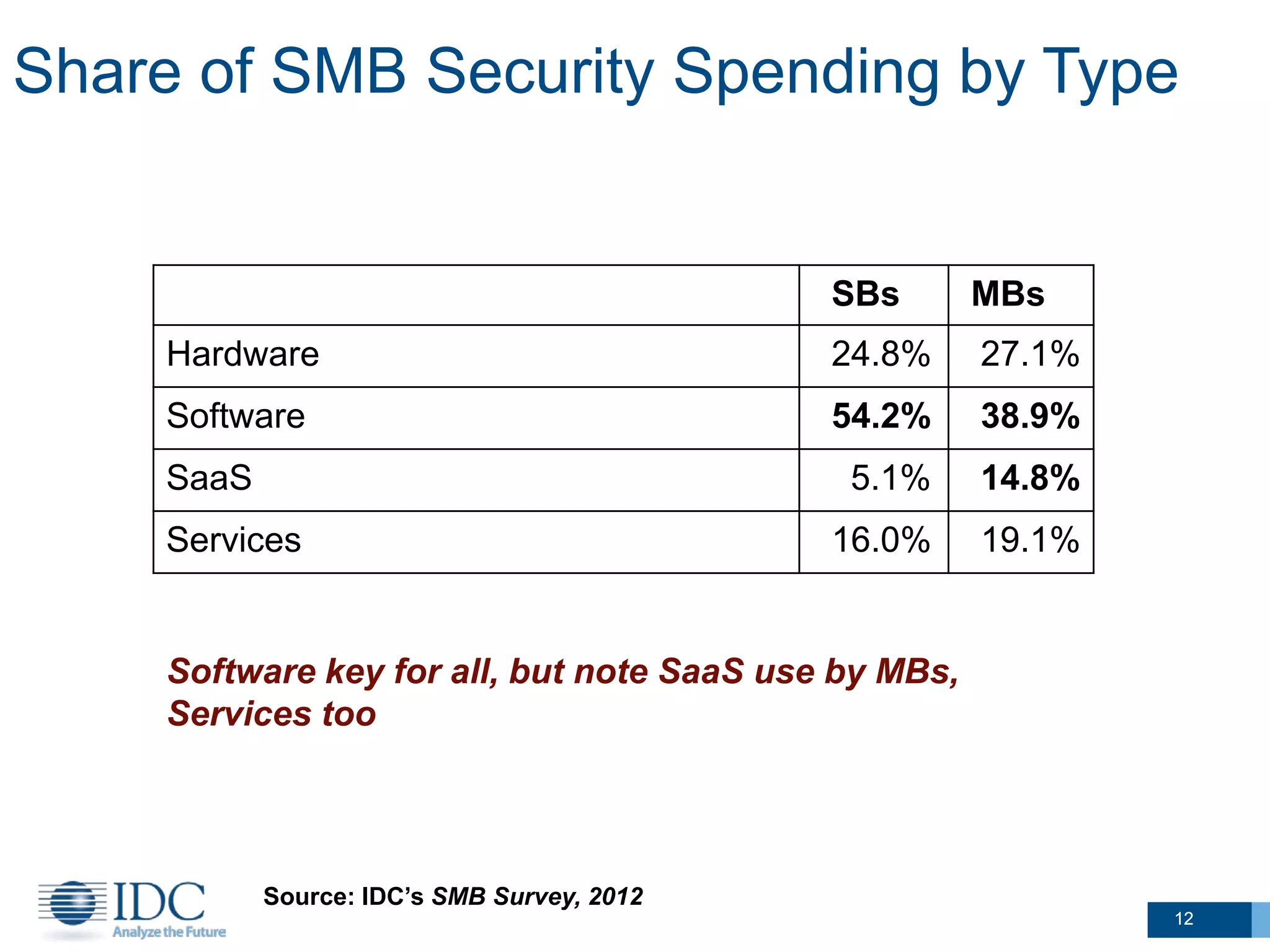
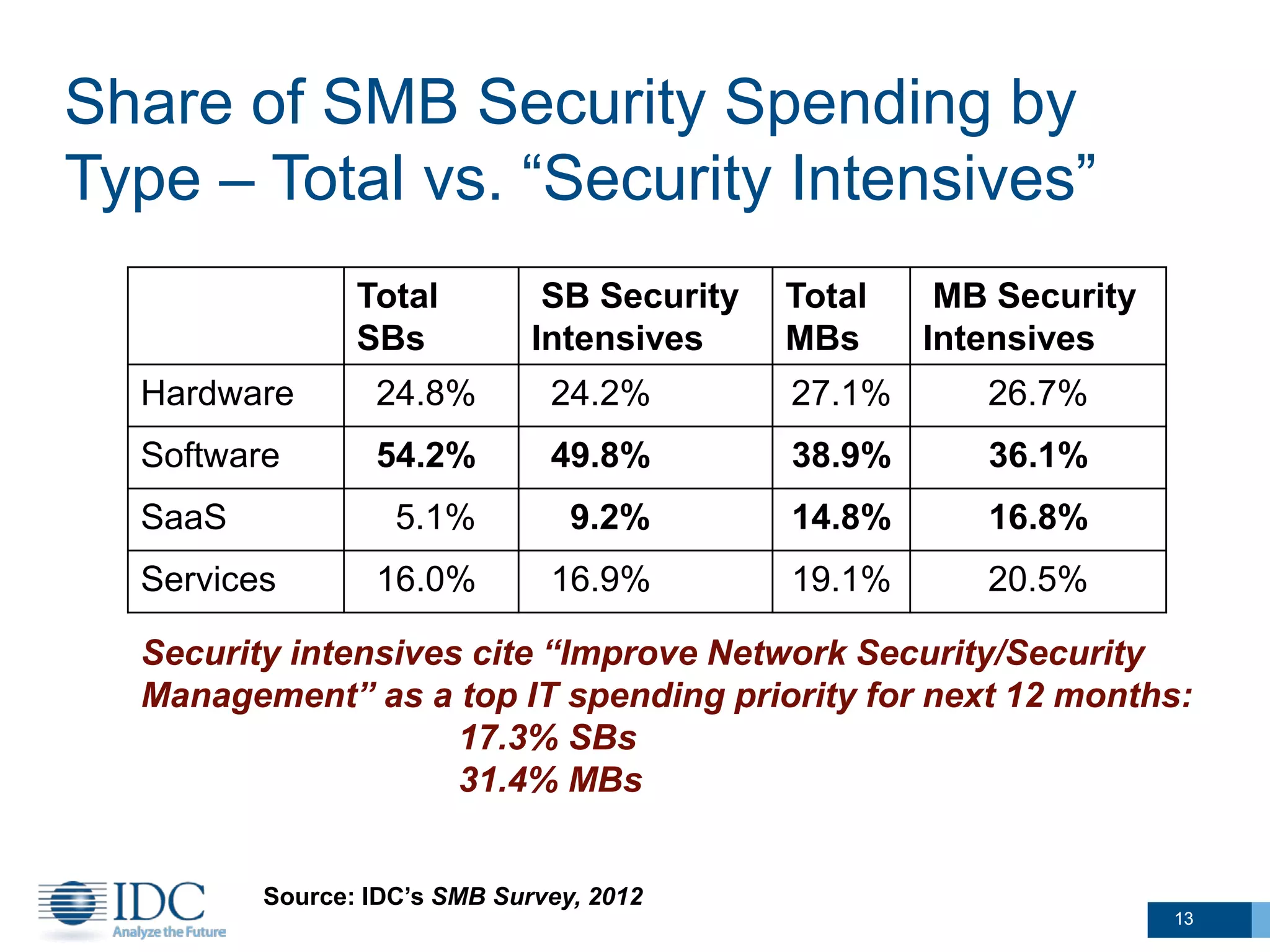
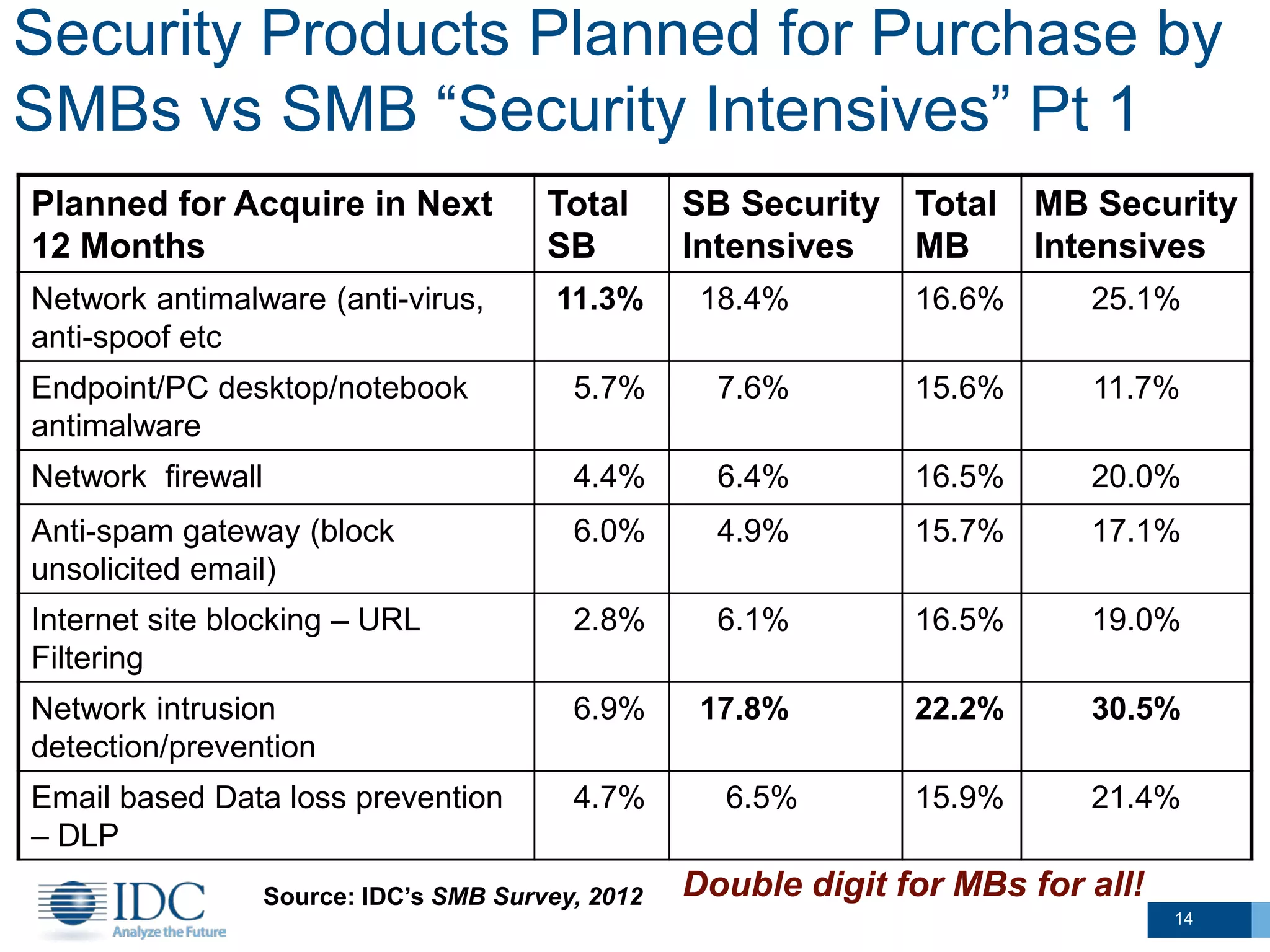
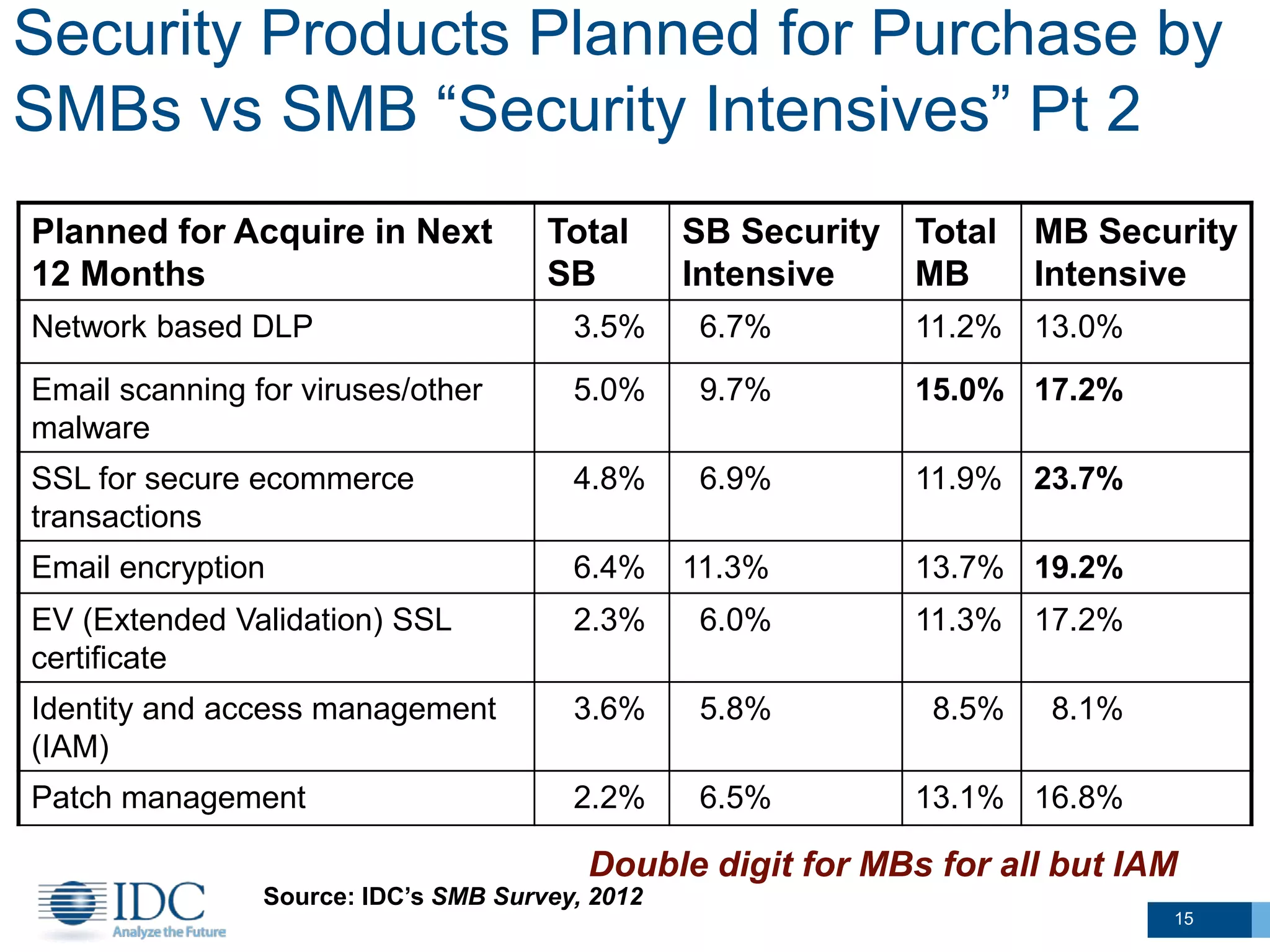
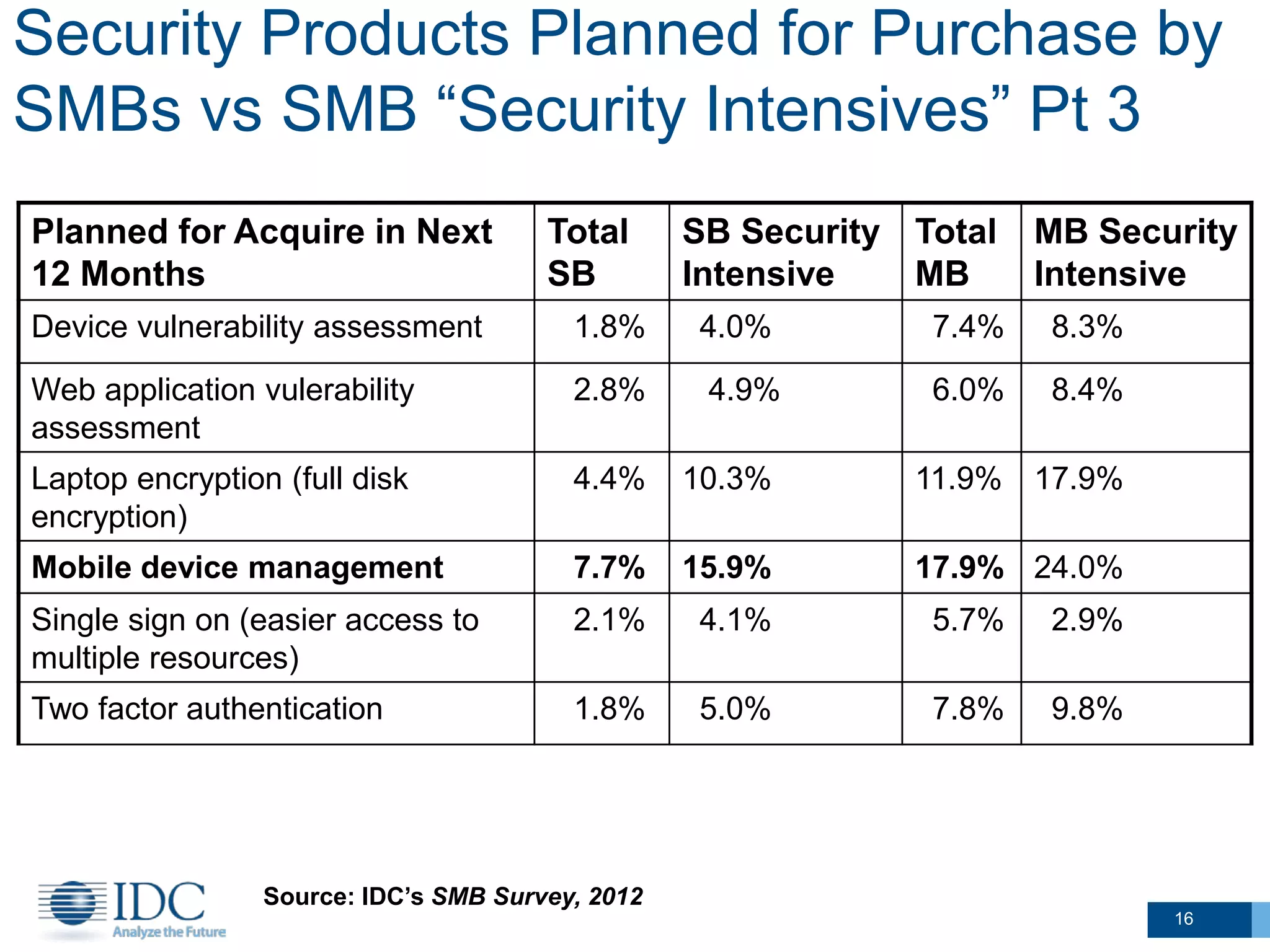
This document summarizes survey results about SMB security technology use and plans. It finds that while most SMBs prioritize basic security like antivirus, a group of "security intensive" SMBs in fields like engineering and healthcare devote more resources to security. These intensives are more likely to have IT staff, networks, and cloud services. They currently use and plan to adopt more advanced security technologies at higher rates than average SMBs, especially mid-sized businesses. The document concludes SMBs recognize the importance of security but need guidance on effective solutions as risks grow with mobility and online activities.