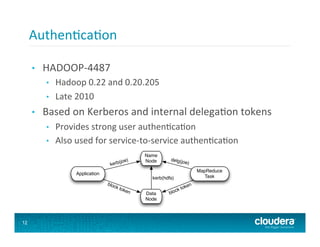
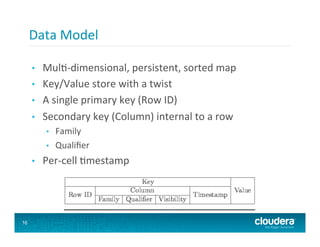
The document discusses the evolution of security features in big data systems, particularly focusing on Hadoop. Key topics include file permissions, authorization, and authentication mechanisms, as well as the importance of preventing unauthorized access and securing data in multi-tenant environments. It also covers security implementations in technologies like Apache Accumulo and Apache HBase, emphasizing encryption for data at rest and the need for granular access controls.