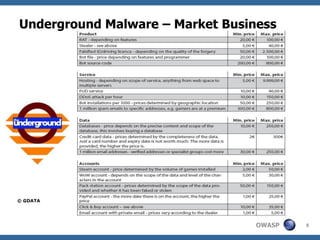
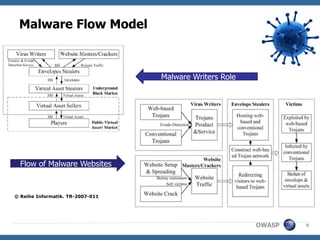
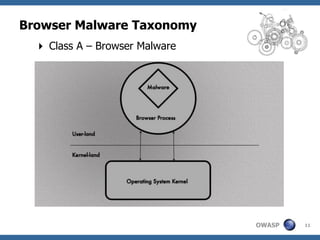
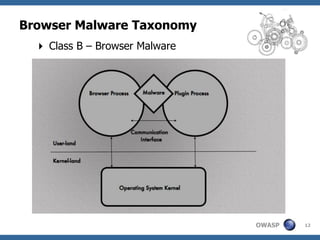
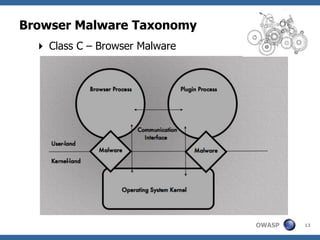
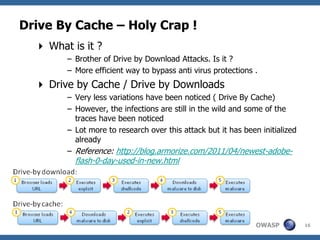
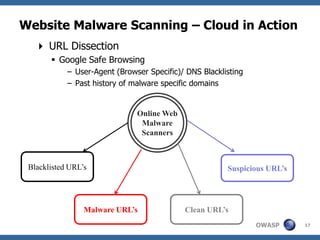
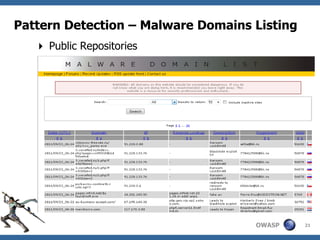
This document summarizes a presentation on hunting web malware as a "good hacker" or malware hunter. It discusses browser malware taxonomy, strategies attackers use to infect websites like iframe injections and compromised servers, and methodology for analyzing website traffic dumps to extract malware. It includes two case studies: one on taking down the BlackHole Exploit Pack and another on conducting a SQL injection attack against a SpyEye botnet command and control server. The presentation emphasizes the penetration testing skills and understanding of malware and exploits needed to rigorously hunt for web malware.
![The Good Hacker – Dismantling
Web Malware
Aditya K Sood and Richard J Enbody
SecNiche Security Labs
Michigan State University
OWASP adi_ks [at] secniche.org | enbody [at] cse.msu.edu
AppSec USA 2011
Minneapolis, Minnesota
Copyright © The OWASP Foundation
September 22-23, Permission is granted to copy, distribute and/or modify this document
2010 under the terms of the OWASP License.
The OWASP Foundation
http://www.owasp.org](https://image.slidesharecdn.com/adityaksowaspappsec2011mnus-111002215257-phpapp02/75/OWASP-AppSec-USA-2011-Dismantling-Web-Malware-1-2048.jpg)











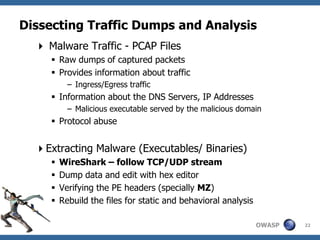
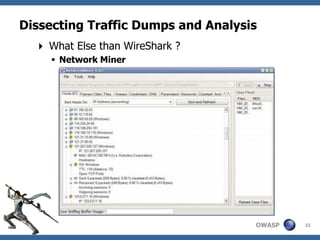
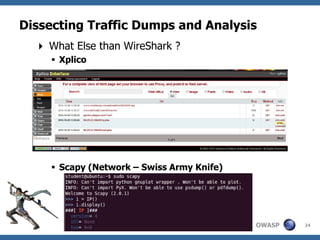
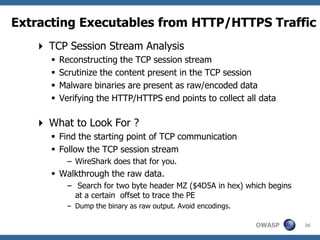
![Dissecting Traffic Dumps and Analysis
Walking through the Process (Generic)
Step 1 - Applying filters in WireShark ( to remove unwanted
traffic)
» http://media.packetlife.net/media/library/13/Wireshark_Dis
play_Filters.pdf
Step 2 - Create the requisite PCAP files
» Use rdpcap() / sniff(offline=“”) (Scapy) to walkthrough
PCAP files
» Pdfdump/Psdump to make graphical output
Step 3 - Perform data operations (Scapy)
» Example: Writing first 5 bytes file_handle(pkt.load[5:])
» Other required data operations
Step 4 – Automated mining of PCAP files
» Use Network Miner and Xplico
OWASP 25](https://image.slidesharecdn.com/adityaksowaspappsec2011mnus-111002215257-phpapp02/85/OWASP-AppSec-USA-2011-Dismantling-Web-Malware-25-320.jpg)
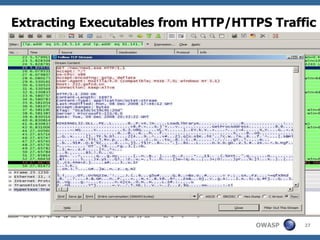




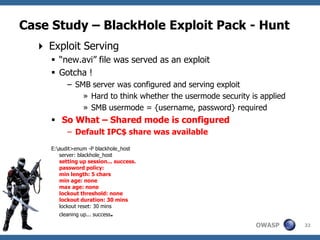
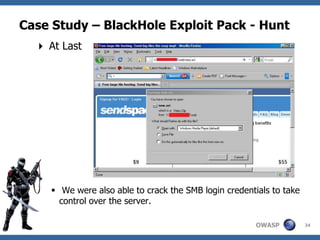
![Case Study – BlackHole Exploit Pack - Hunt
Verifying the Facts
The server was not browseable
Fuzzing the UNC path as follows
• blackhole_hosthomenew.avi
• blackhole_hostusrnew.avi
• blackhole_hosthomesmbnew.avi [ Gotcha]
• blackhole_hostusrsmbnew.avi
SMB server must be configured with following metrics
[global]
security = share
[smb]
comment = smb
path = /home/smb
public = yes
browseable = no
writeable = no
guest ok = yes
OWASP 33](https://image.slidesharecdn.com/adityaksowaspappsec2011mnus-111002215257-phpapp02/85/OWASP-AppSec-USA-2011-Dismantling-Web-Malware-33-320.jpg)