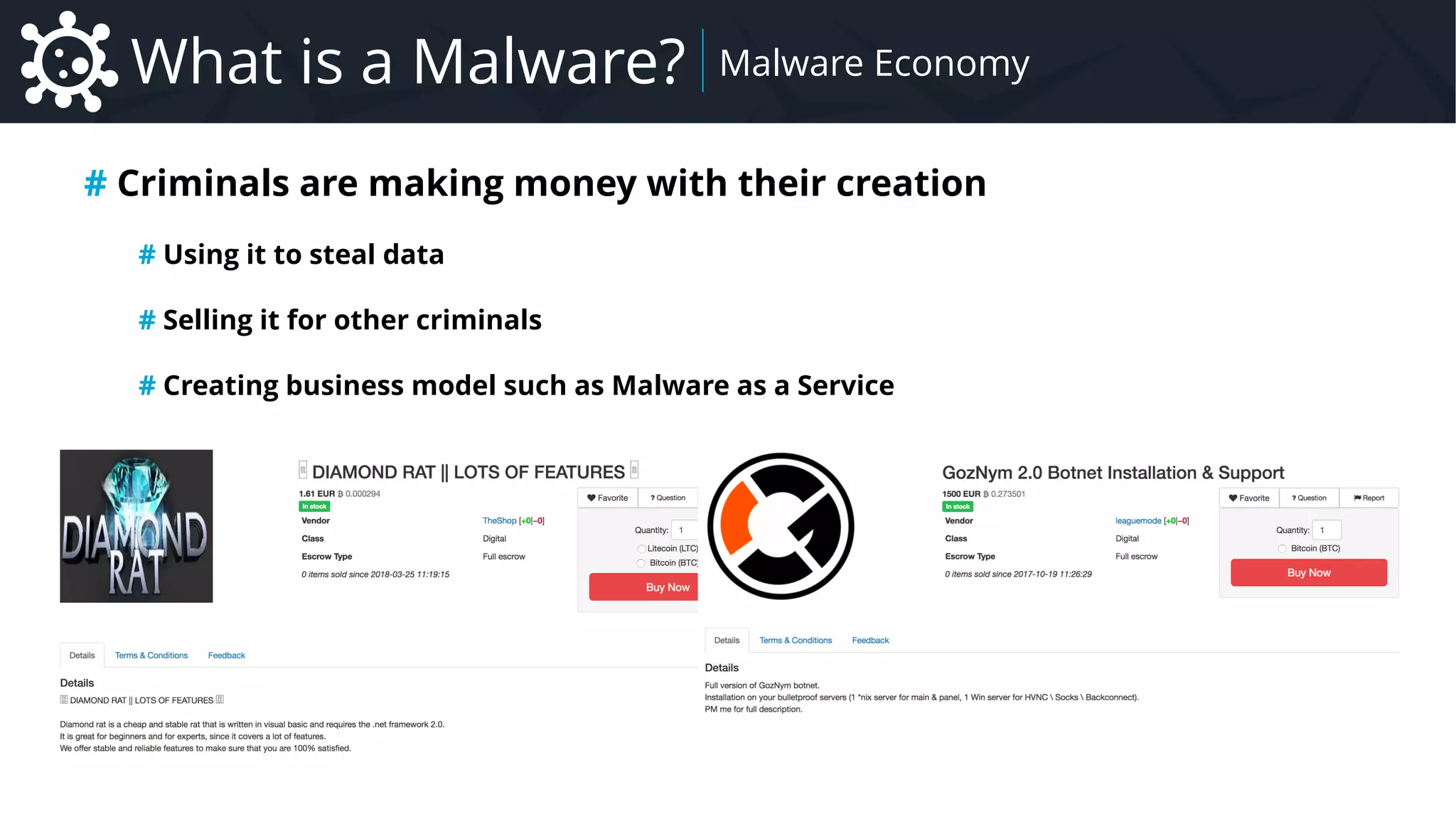
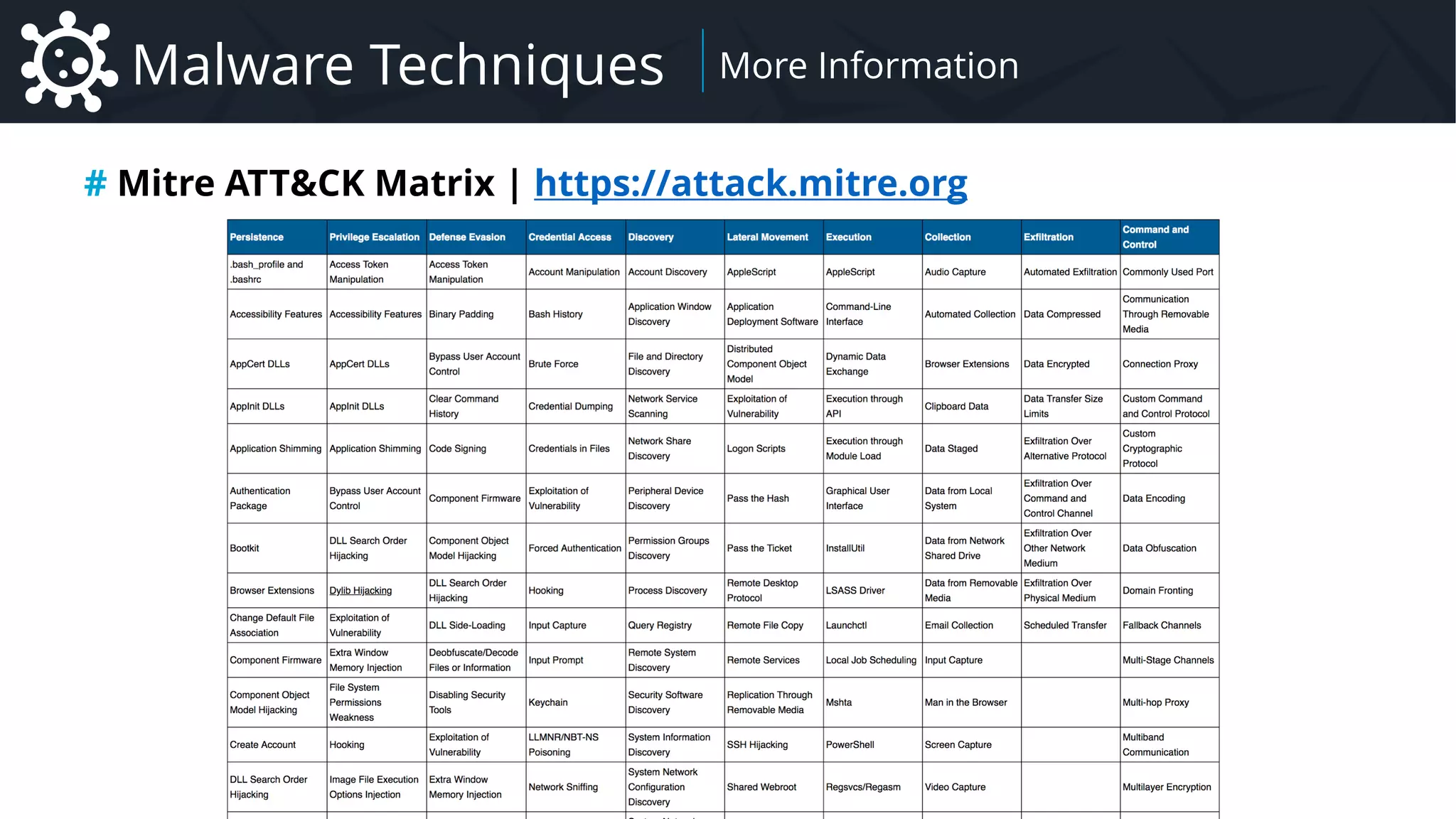
The document provides a comprehensive overview of malware, focusing particularly on remote administration tools (RATs), their definitions, economic impact, techniques of infection, persistence, privilege escalation, evasion methods, and analysis strategies. It outlines various malware families, attribution methods, and the business models surrounding malware distribution and usage. Additionally, it delves into the specifics of RAT functionalities, networking protocols, command-and-control mechanisms, and payload configurations.





















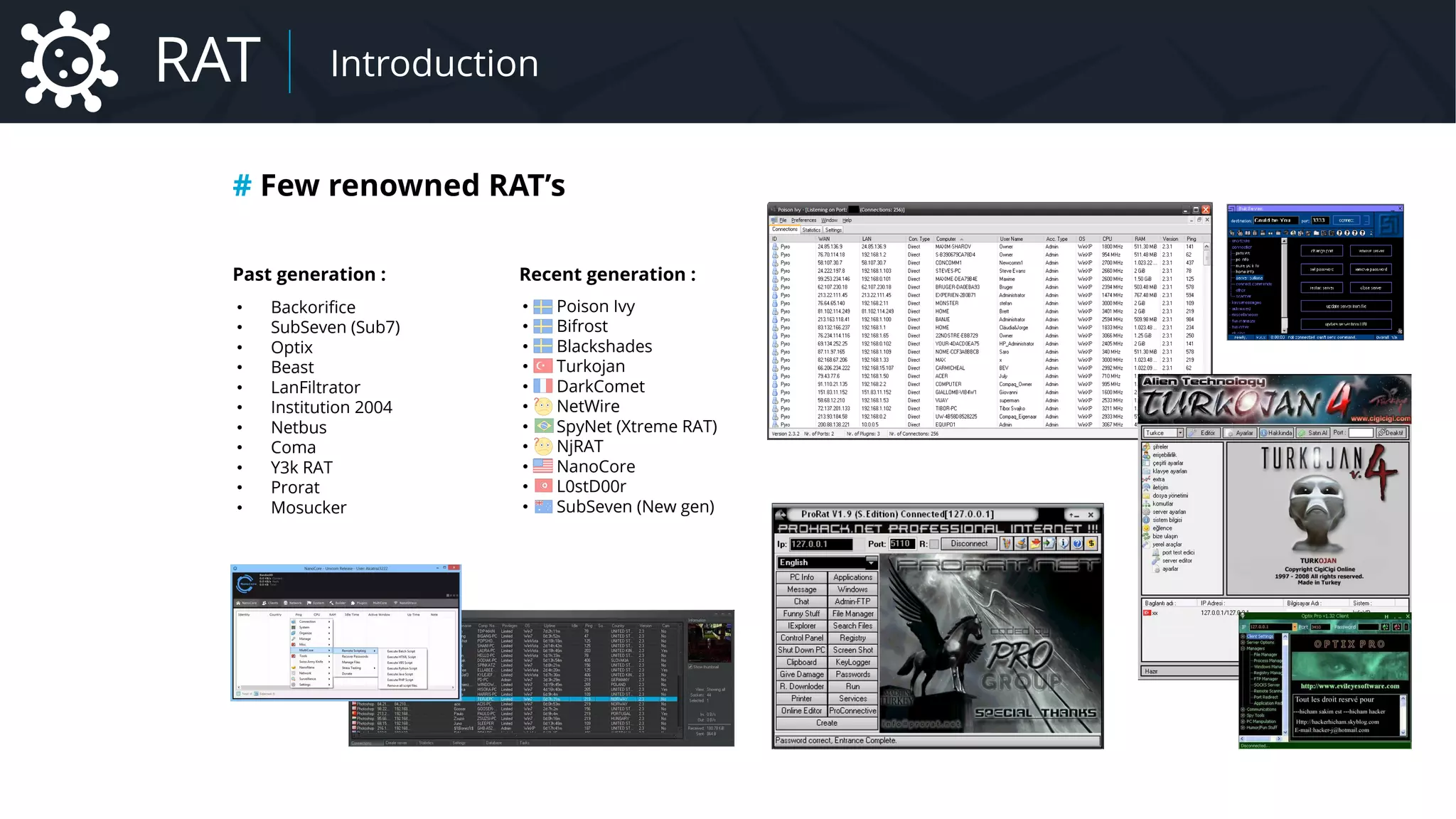


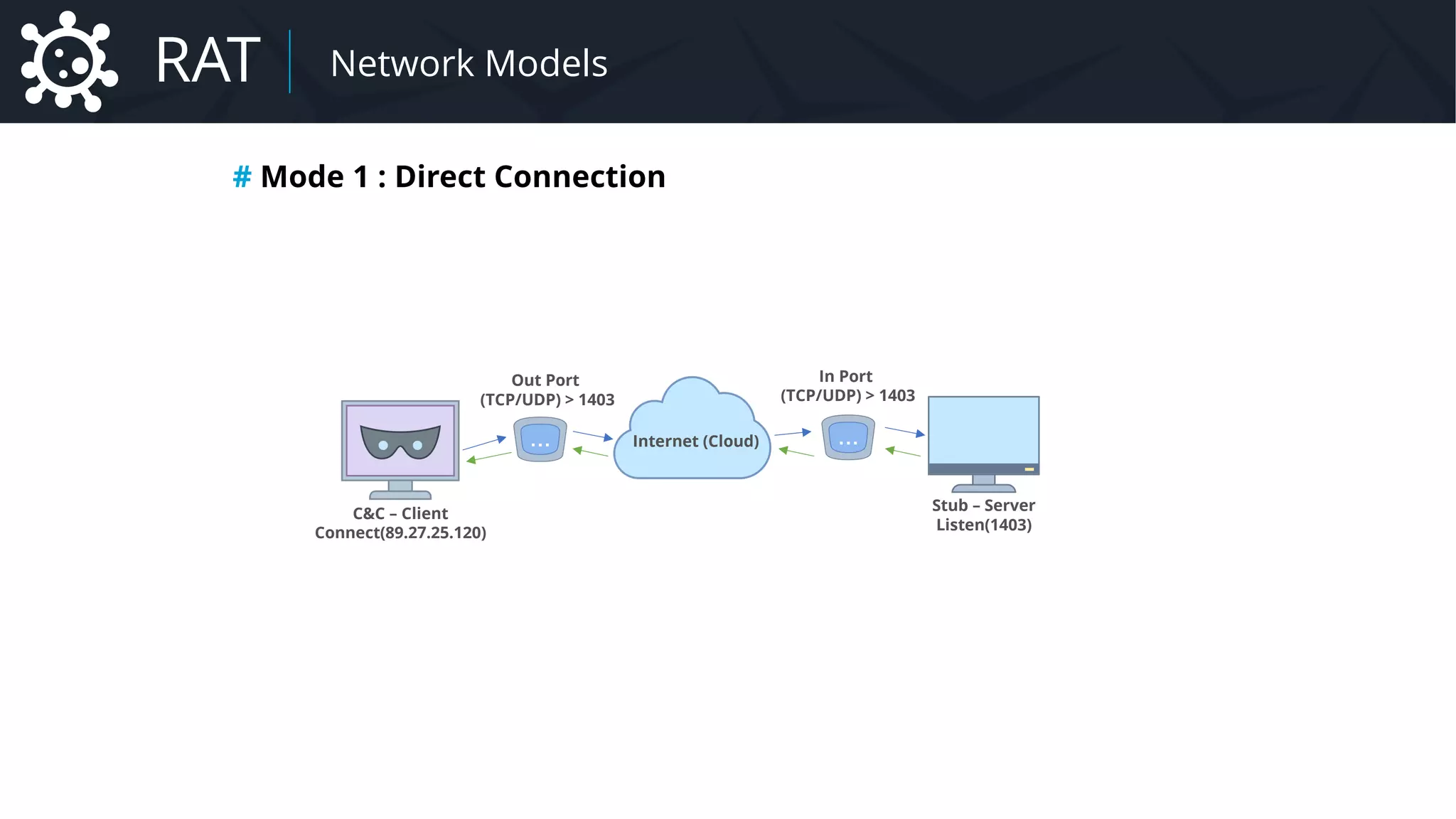
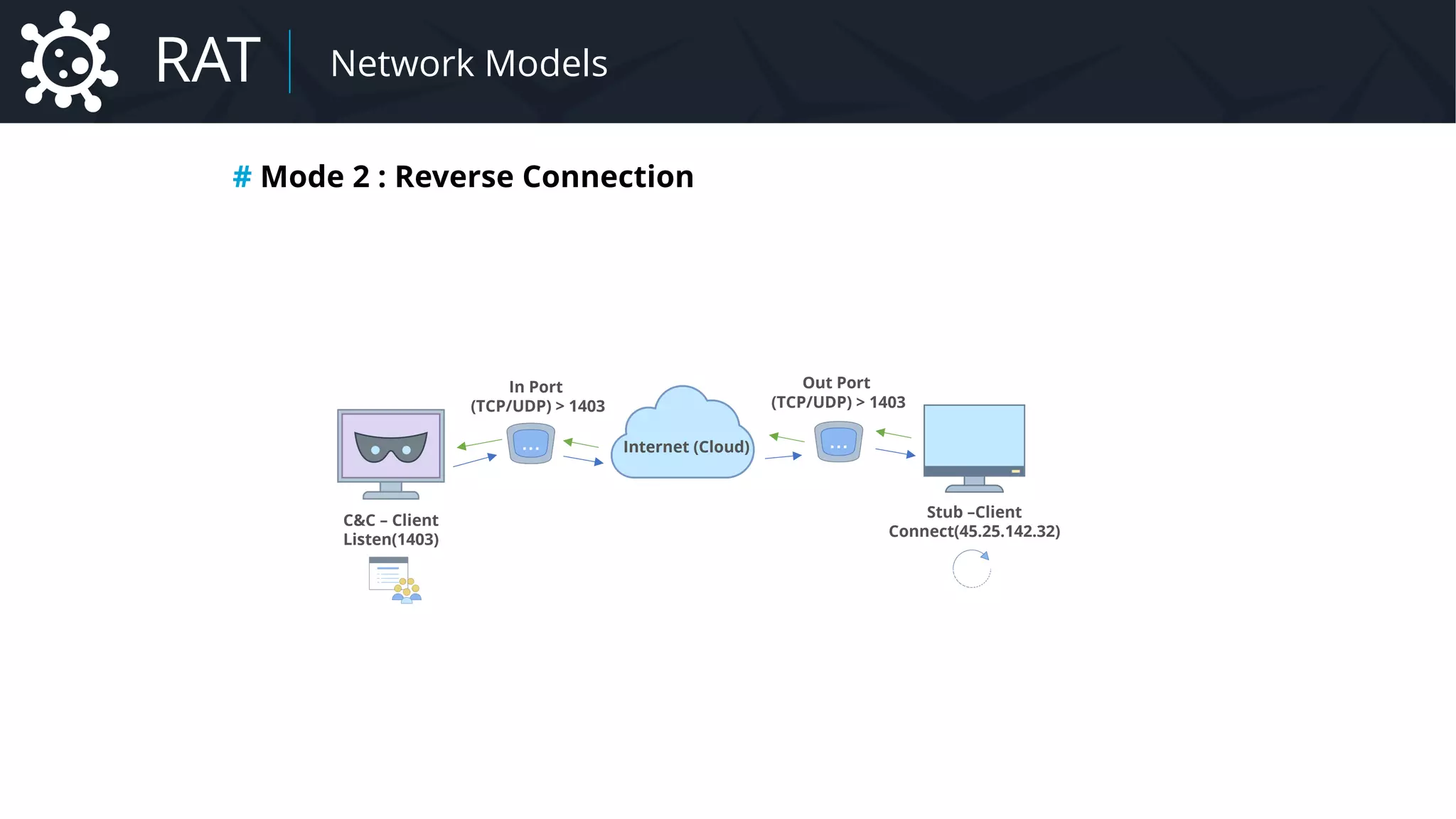
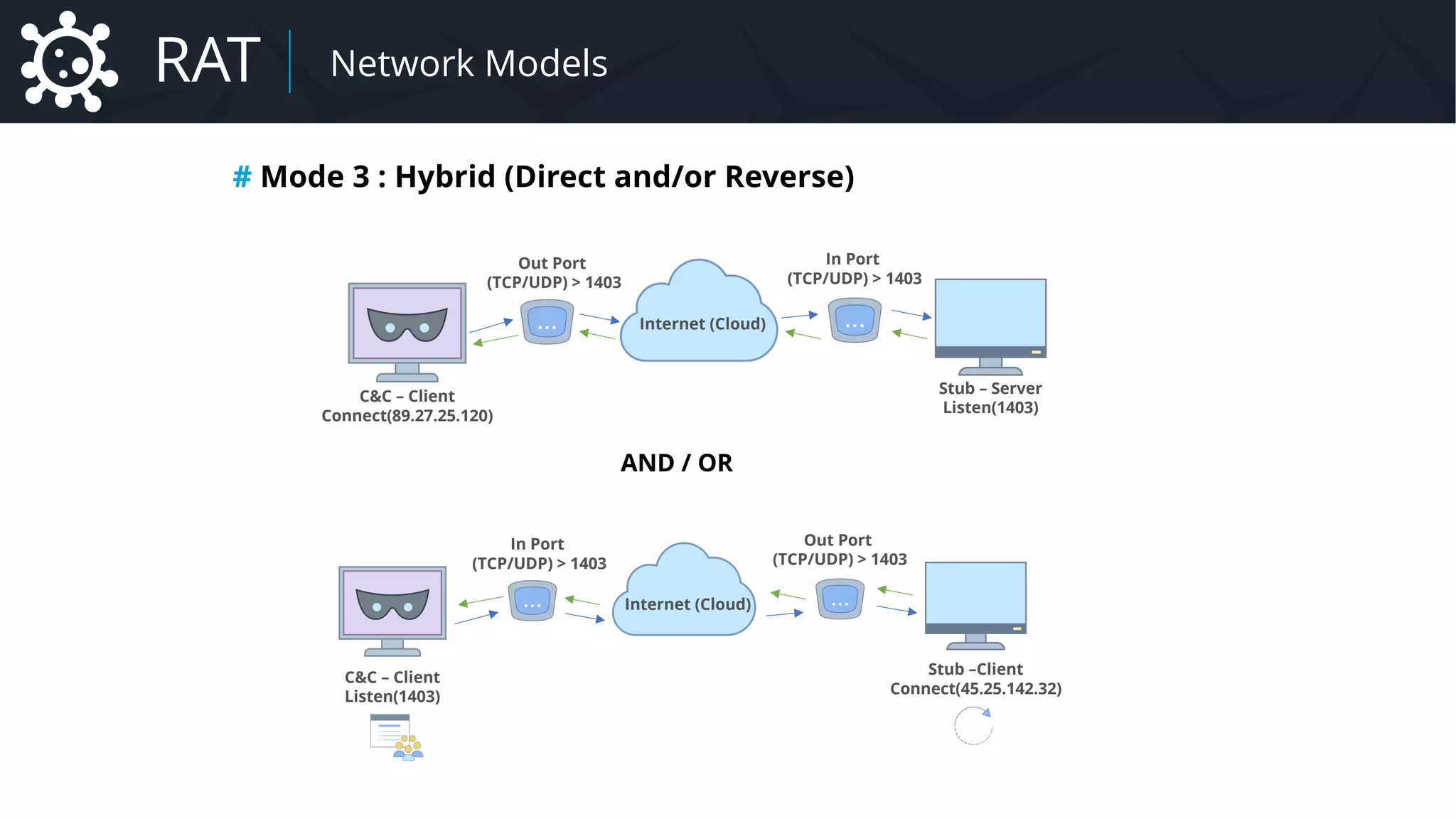



![Malware Network Protocol
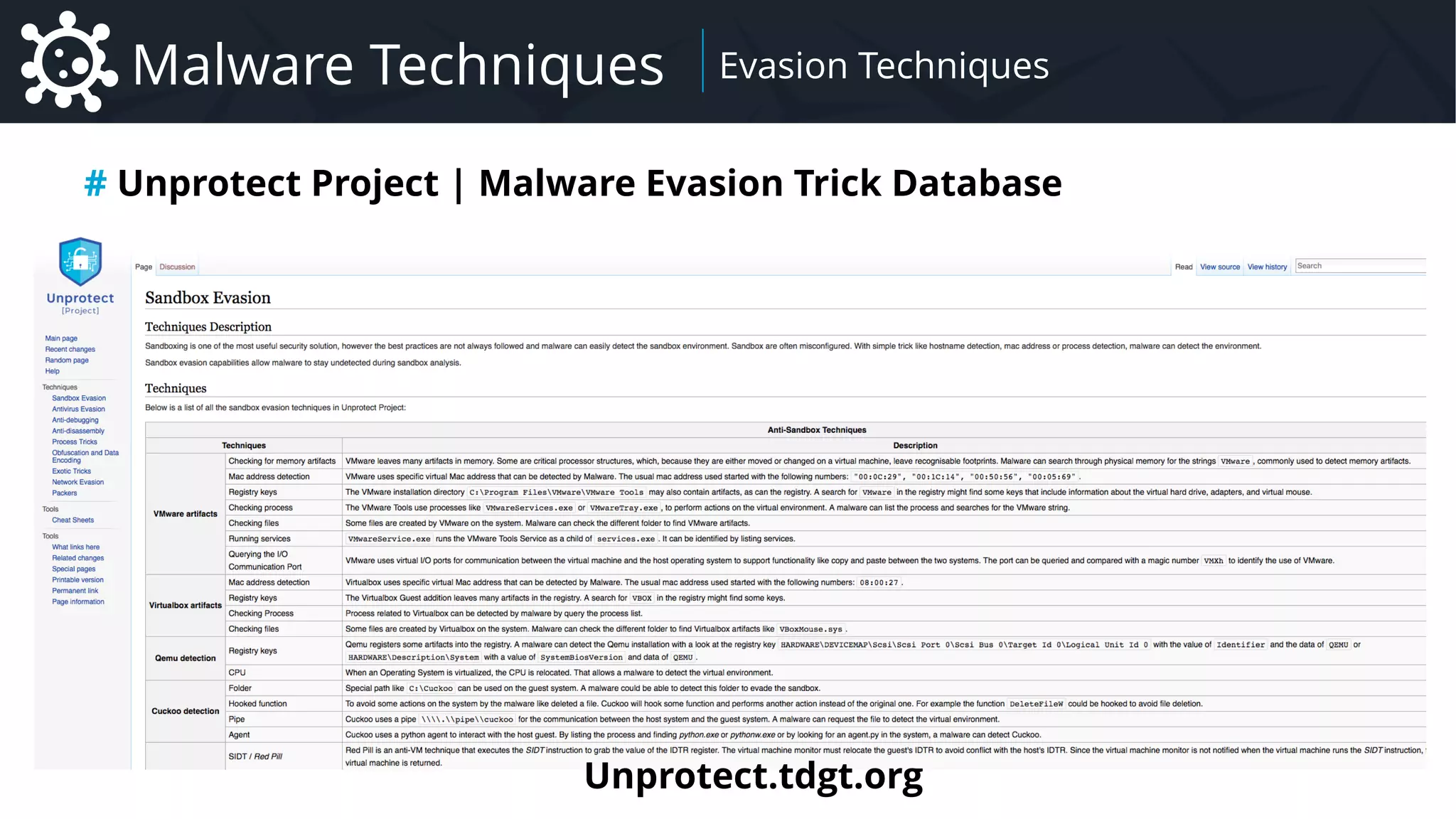
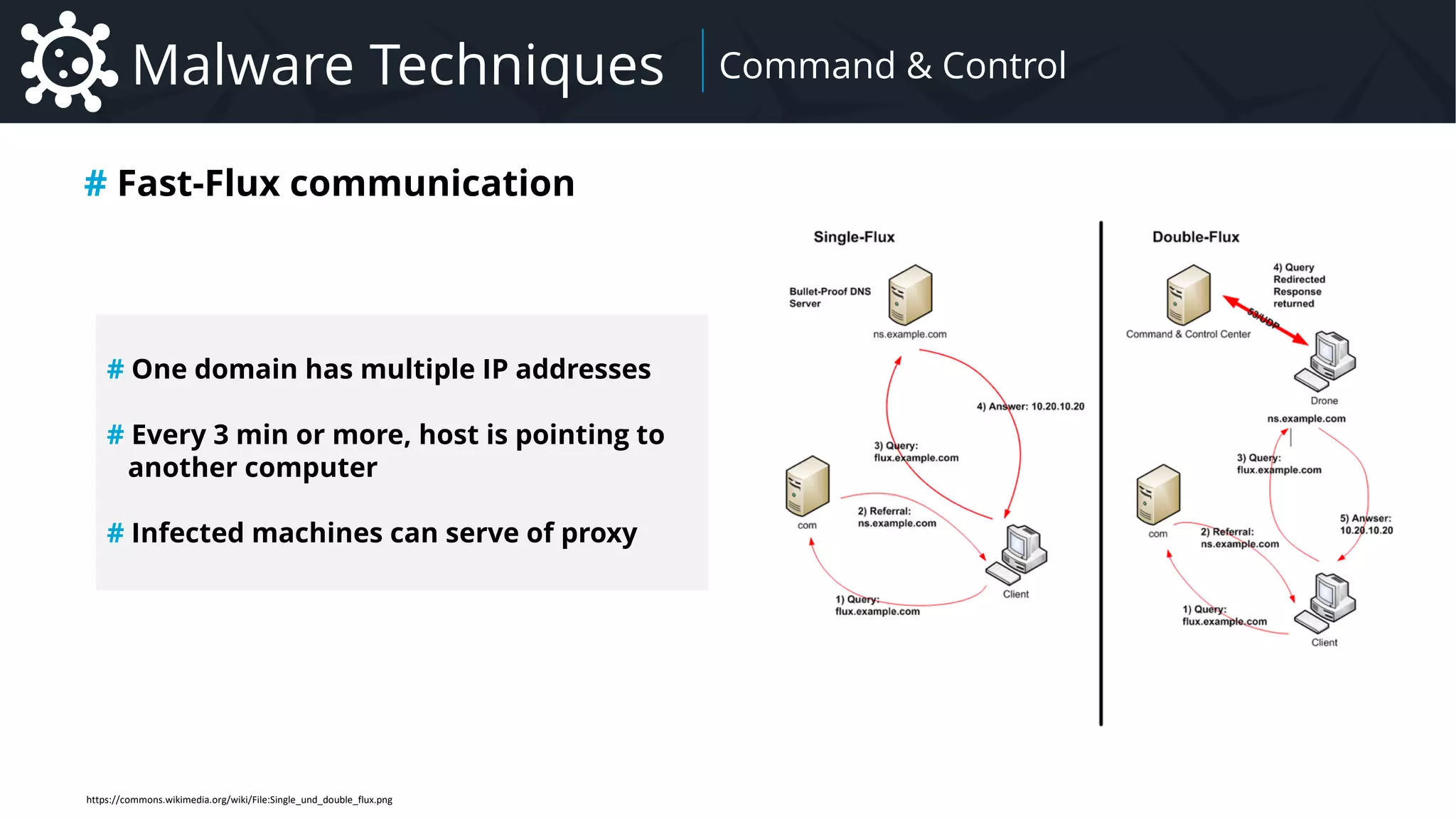
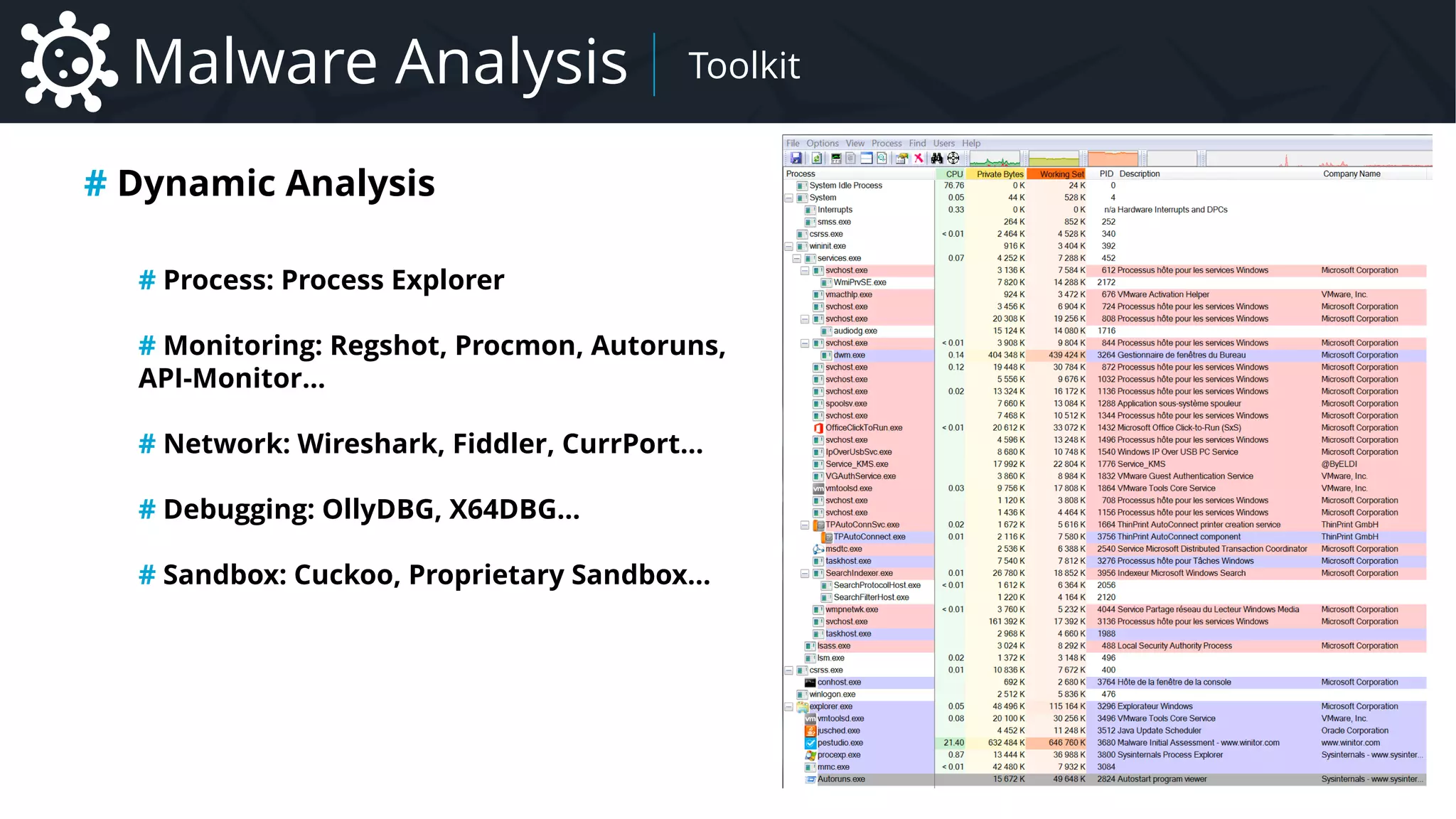
# Nature of transmitted data
CSV
kill:14032,1254,12687
JSON
{
“action”:”kill”,
“data”:[
14032,
1254,
12687
]
}
BYTES (Struct)
4c000000011402000000
0000c0000000000000469
b000800200000005284ce
b6f7c8d3015284ceb6f7c
8d3014b5333d55ba3d301
00fa01…
RAT Network Protocol](https://image.slidesharecdn.com/malware-42-roccia-lesueur-180424062501/75/42-Malware-Understand-the-Threat-and-How-to-Respond-51-2048.jpg)
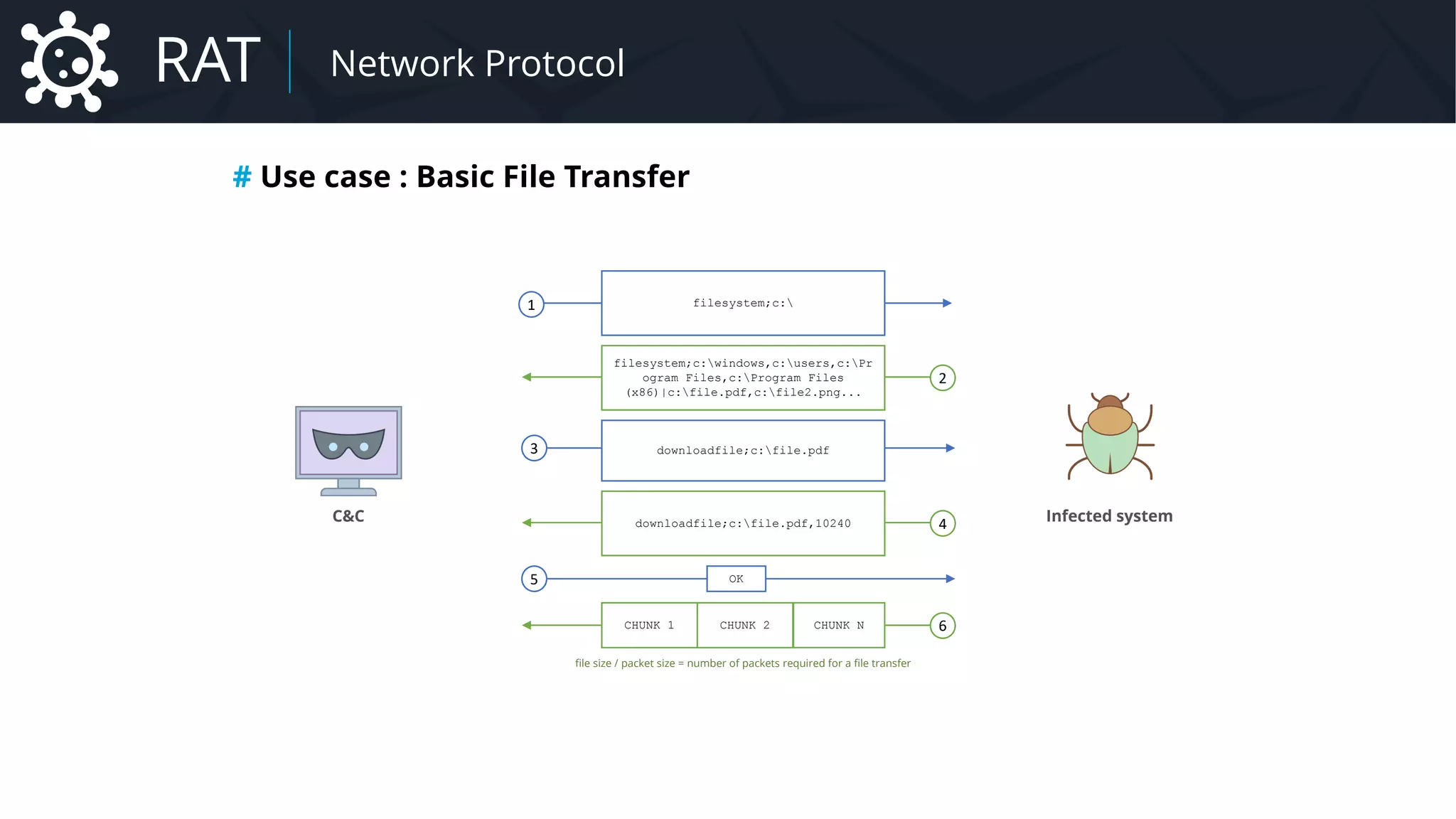






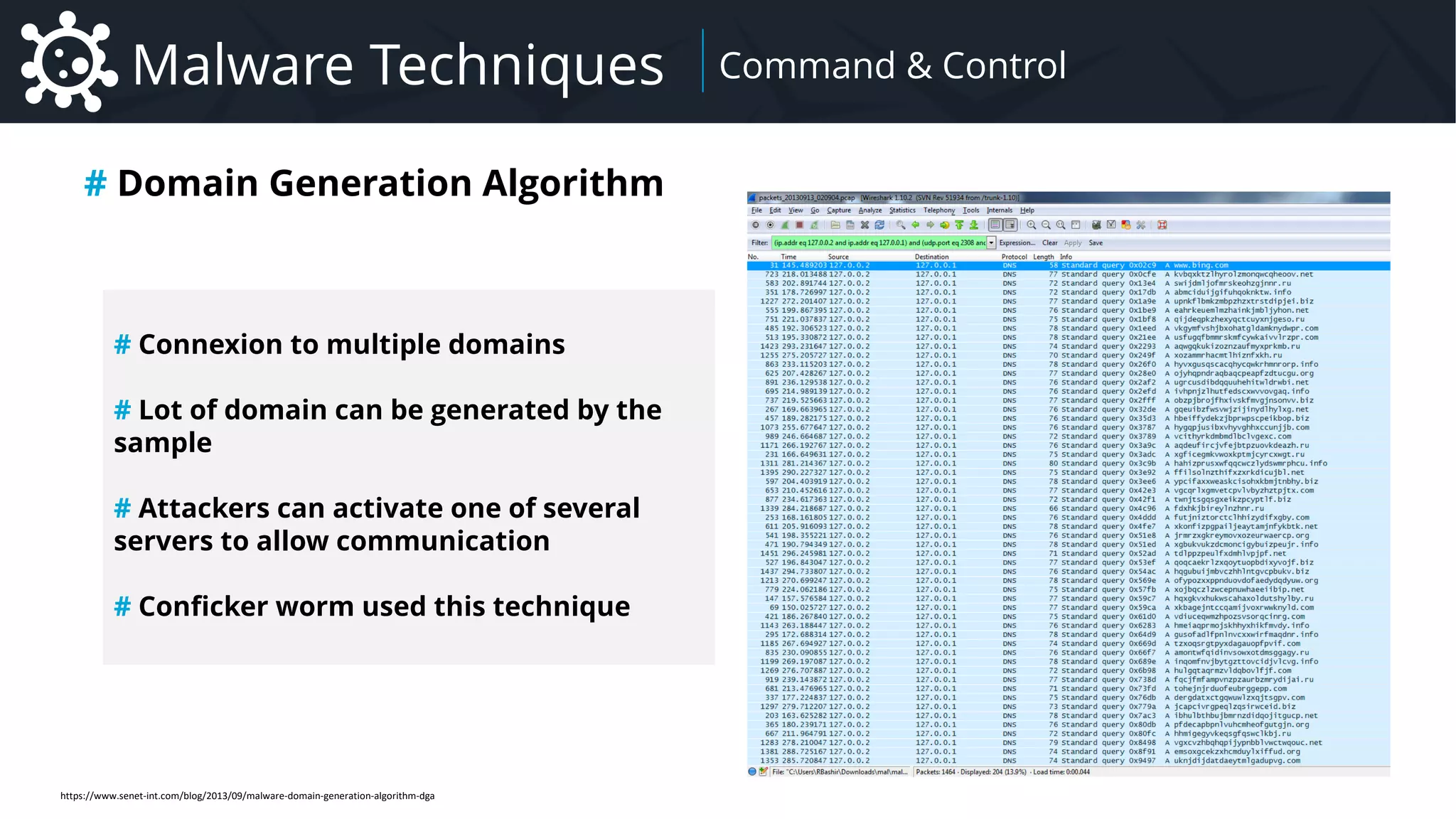
![Malware Payload Configuration
# PE (Portable Executable) Sections
Section Tables Add new section info
Section Address : 0x000FF12A
Size of section : N Bytes
Name of section : malconf
Section 1
DOS Segment
PE Header
Section 1
Section N
DOS Header
…
Custom Section
0x000FF12A
Explore PE Header and Sections (PE Bear)
JSON / CSV / Structures etc.
{
"cncaddr": [
"127.0.0.1",
"192.168.0.11",
"89.214.25.111",
"lamer.no-ip.org",
"lamer2.dyndns.org"
],
"startup": {
"enabled": true,
"name": "svchost.exe"
}
[...]
}
RAT Payload Configuration](https://image.slidesharecdn.com/malware-42-roccia-lesueur-180424062501/75/42-Malware-Understand-the-Threat-and-How-to-Respond-59-2048.jpg)