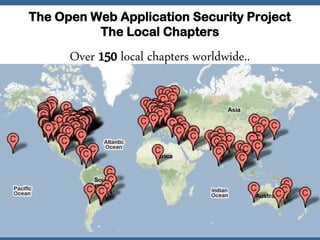
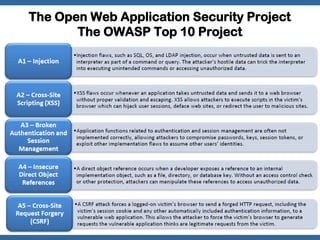
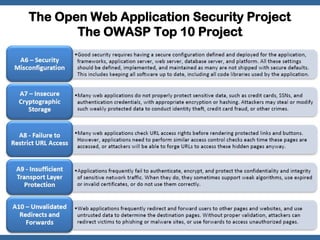
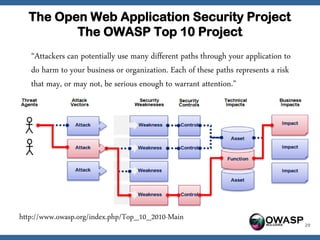
The document discusses an OWASP plan and meeting agenda. It introduces Georgi Geshev as the OWASP Bulgaria leader and provides an overview of OWASP including its mission to improve application security. The agenda covers introducing OWASP and discussing the OWASP Top 10 project, which lists the top 10 web application security risks. Attendees are encouraged to get involved with the local OWASP chapter.