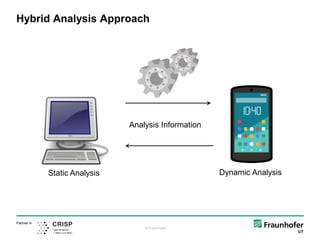
The document discusses the challenges and methods of analyzing sophisticated Android malware, emphasizing the limitations of both static and dynamic analysis. It introduces tools like CodeInspect and FuzzDroid for hybrid analysis, combining various techniques to improve detection capabilities. Conclusions highlight the necessity of aiding human analysts and the use of hybrid approaches to effectively combat malware threats.

















![© Fraunhofer
Partner in
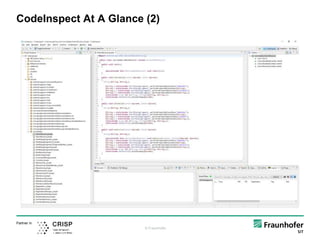
public void foo() {
byte[] $arrbyte;
java.io.FileOutputStream $FileOutputStream;
…
specialinvoke this.<android.app.Service: void onCreate()>();
$File = new java.io.File;
specialinvoke $File.<java.io.File: void <init>(java.lang.String)>("/sdcard/test.apk");
specialinvoke $FileOutputStream.<java.io.FileOutputStream: void <init>(java.io.File)>($File);
$arrbyte = newarray (byte)[1024];
$int = virtualinvoke $InputStream.<java.io.InputStream: int read(byte[])>($arrbyte);
…
The Jimple IR
Method Declaration
Variable Declarations
Implementation](https://image.slidesharecdn.com/investigatingmalware-161117095447/85/Dissecting-State-of-the-Art-Android-Malware-Using-Static-and-Dynamic-Analysis-23-320.jpg)












