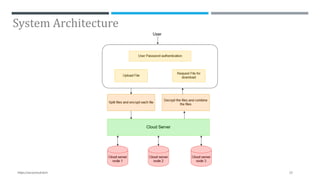
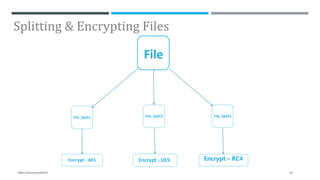
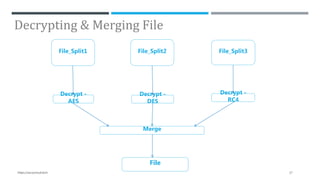
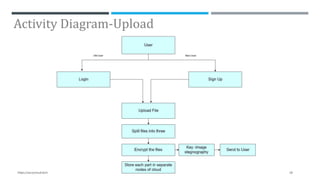
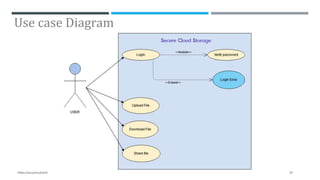
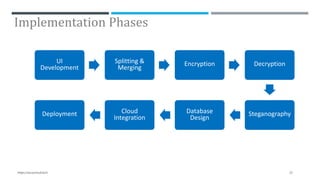
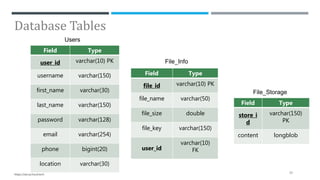
The document presents a project on secure file storage in the cloud using hybrid cryptography techniques, detailing the problem of data security in cloud computing and proposing a distributed, encrypted storage system that splits files into shards. It outlines existing literature, system architecture, implementation phases, and cryptographic algorithms used for file encryption and decryption. The project aims to enhance data integrity, confidentiality, and security while eliminating third-party access.