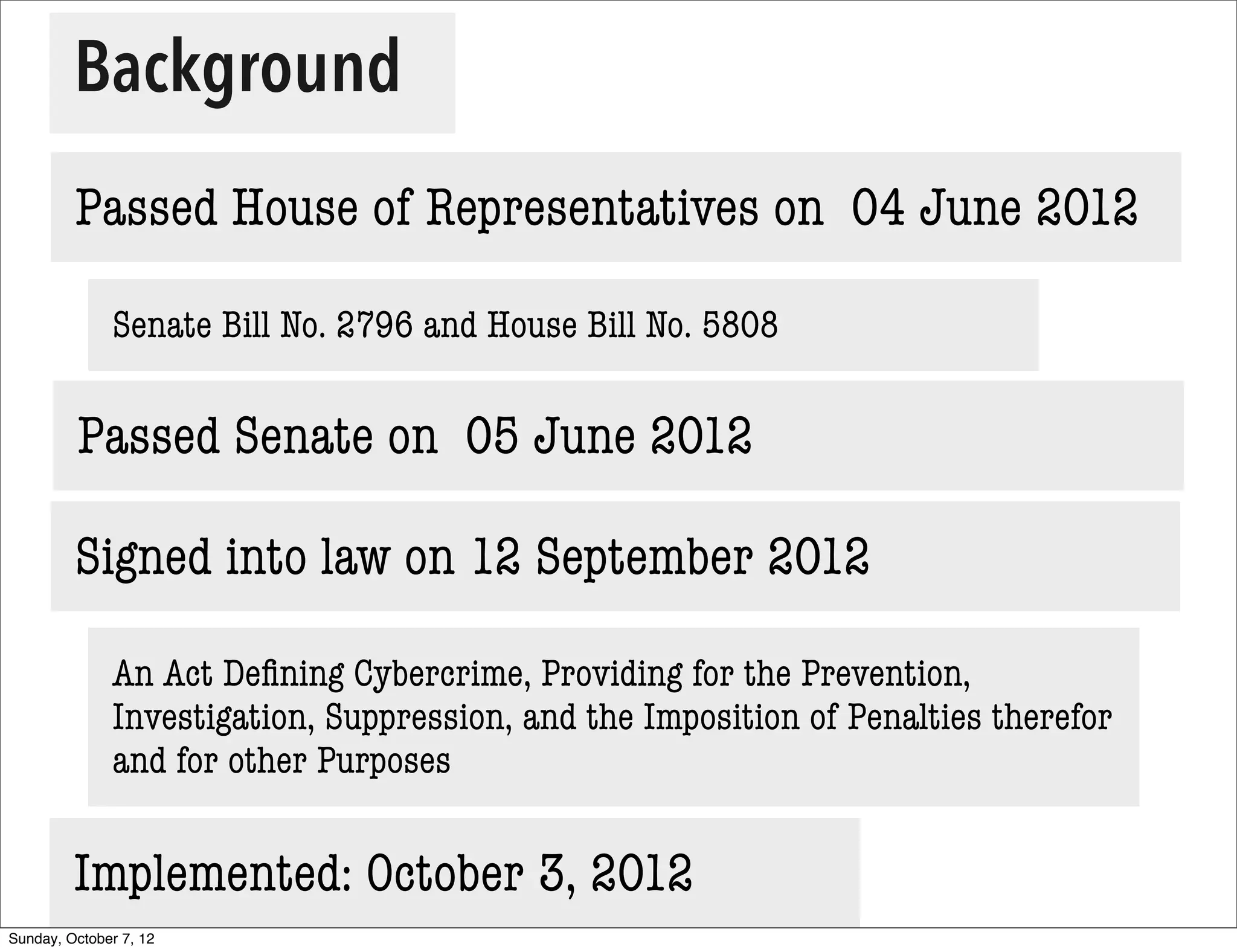
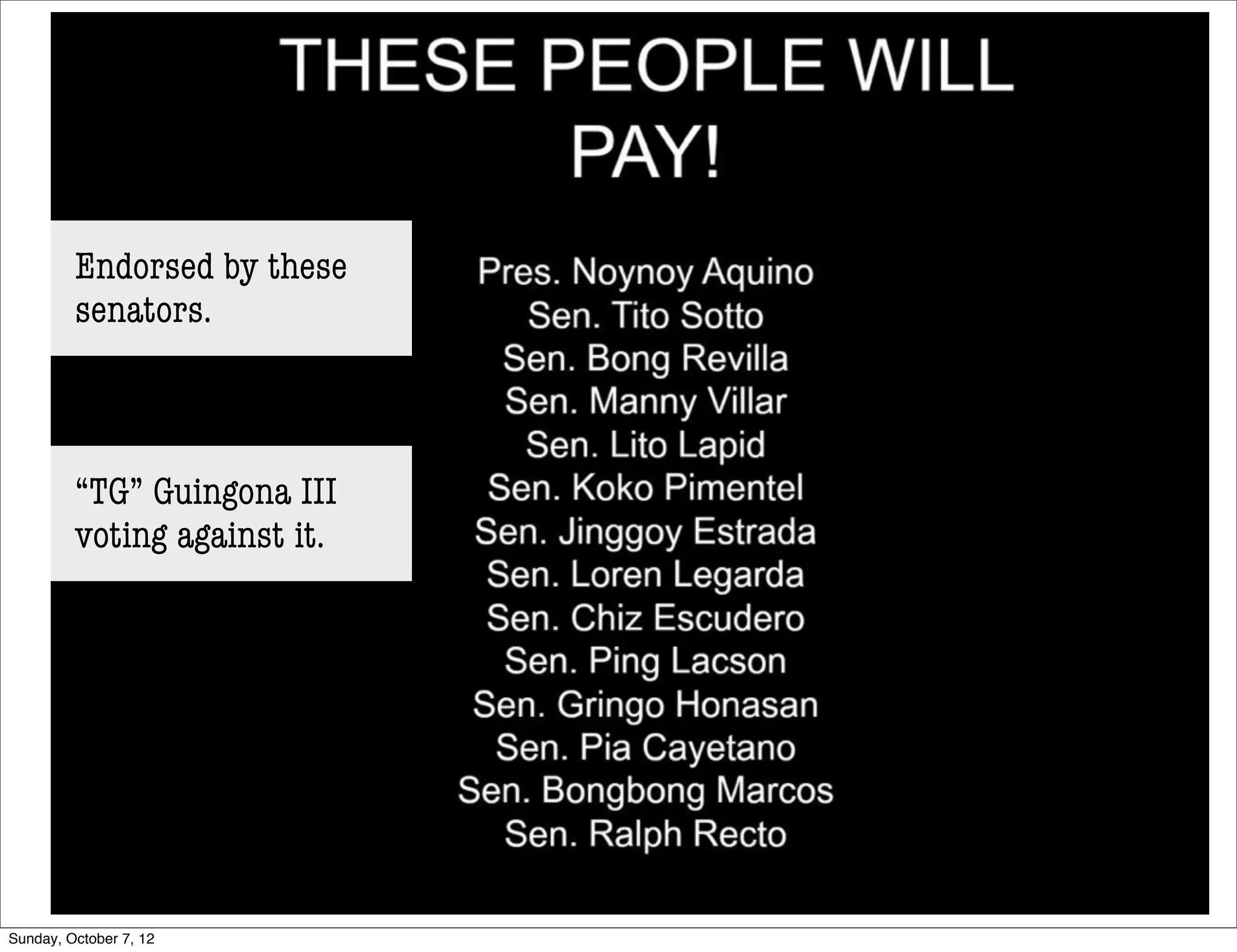
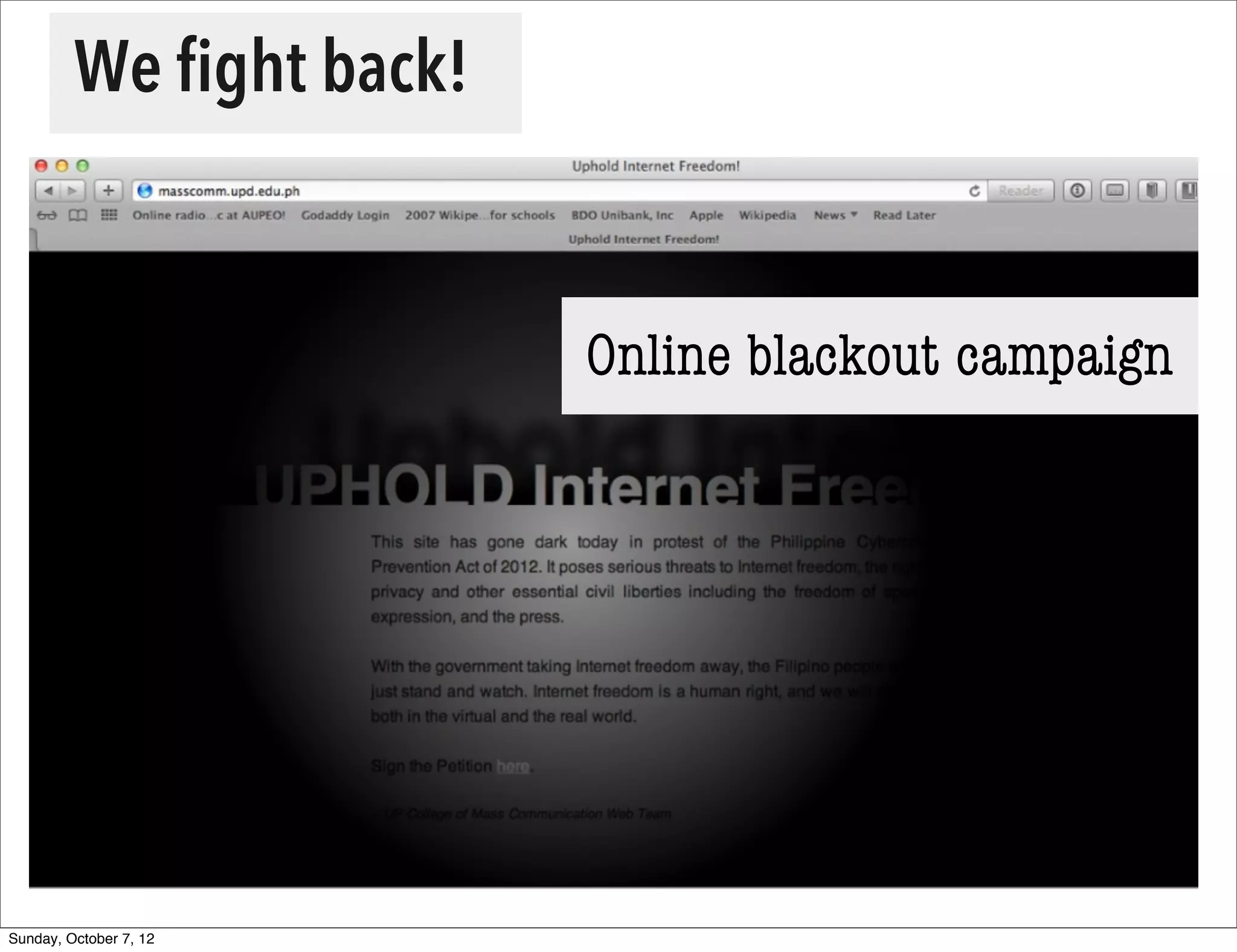
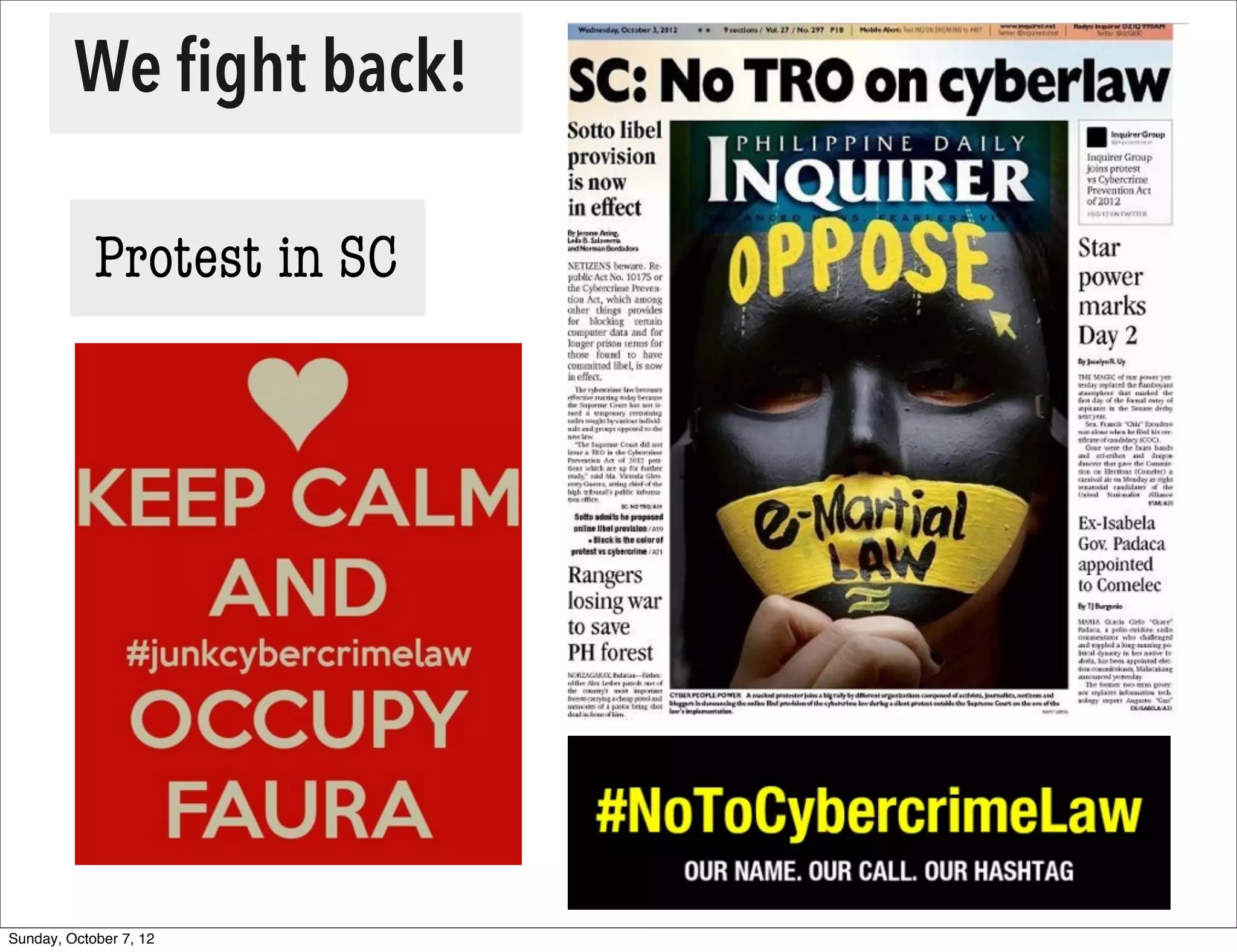
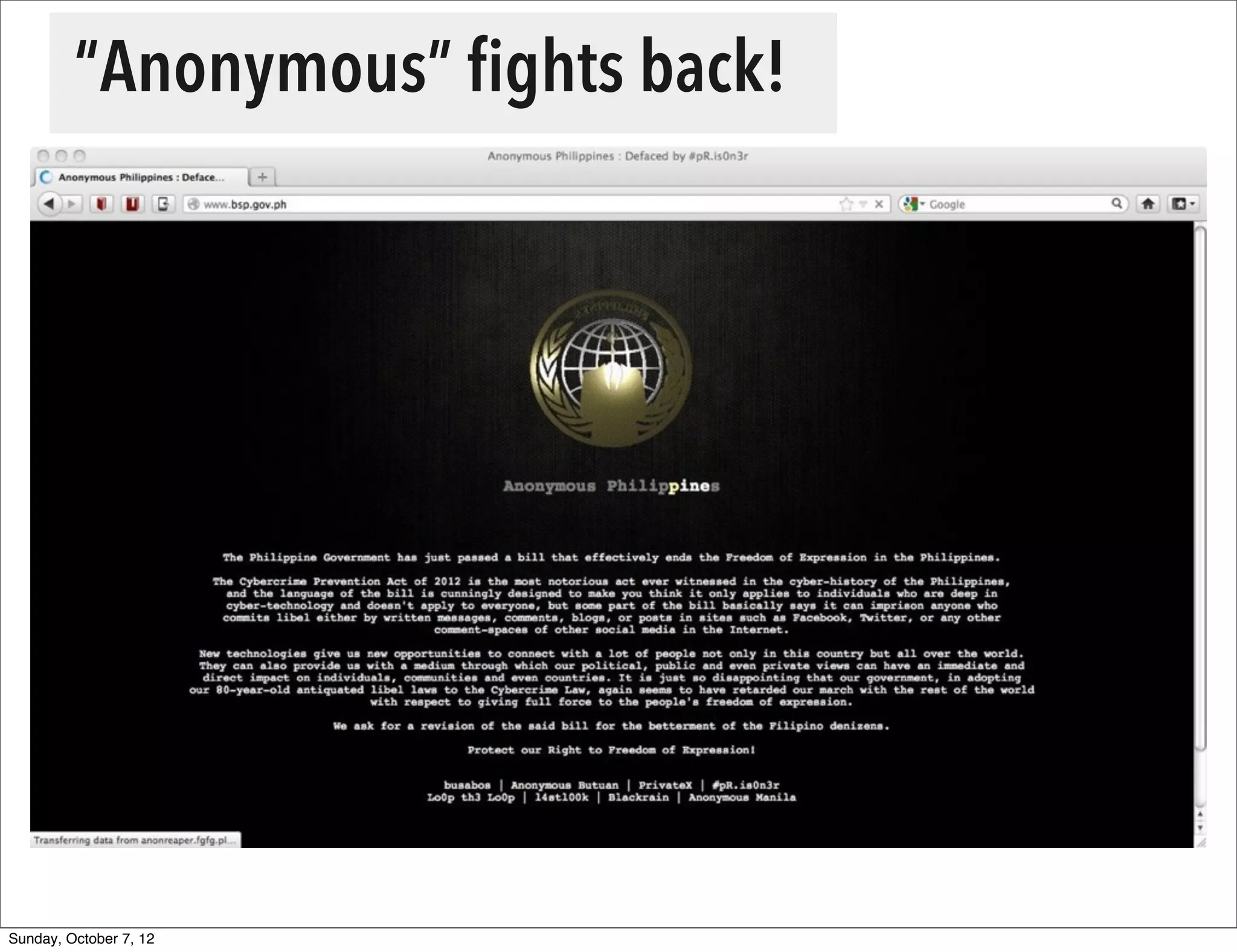
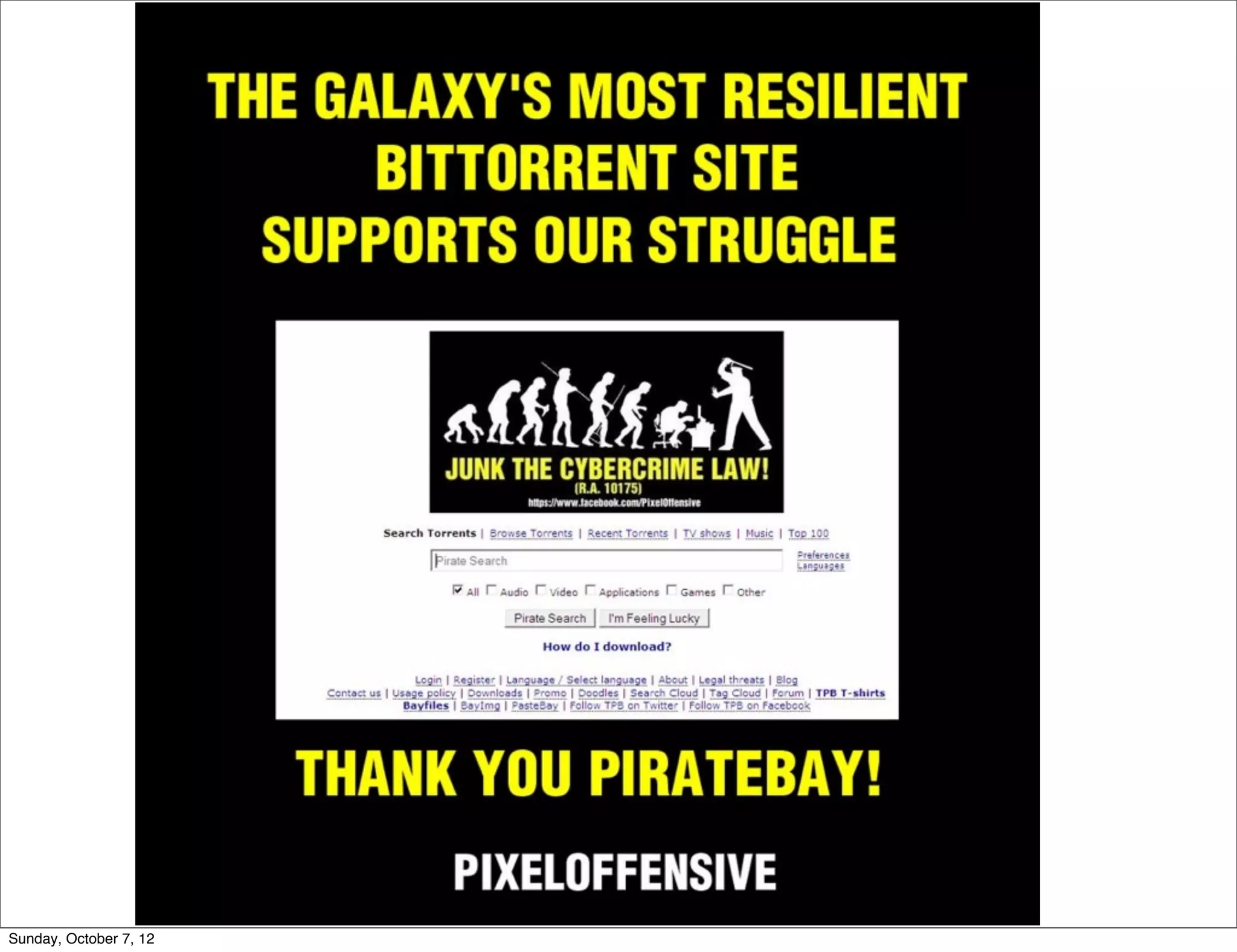
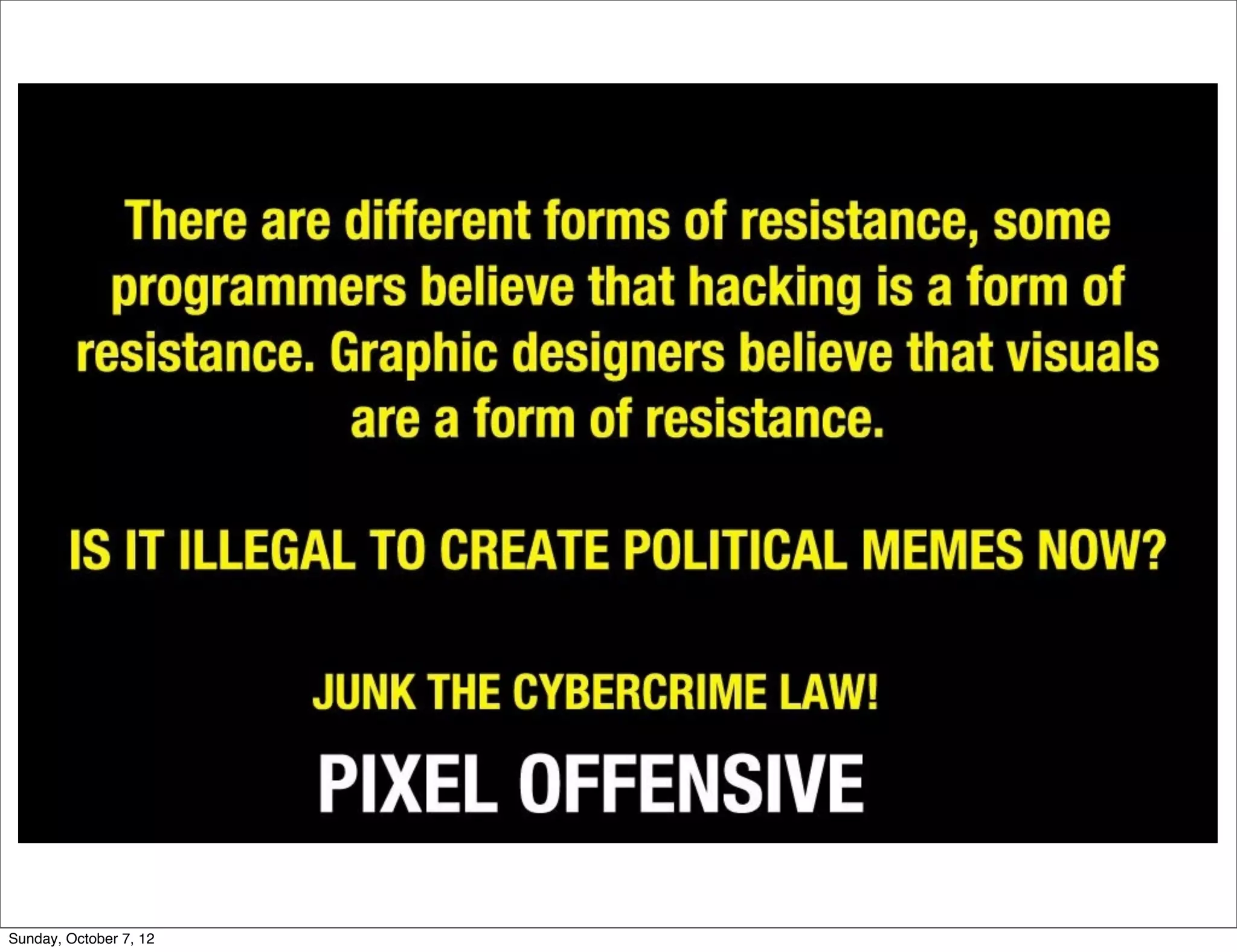
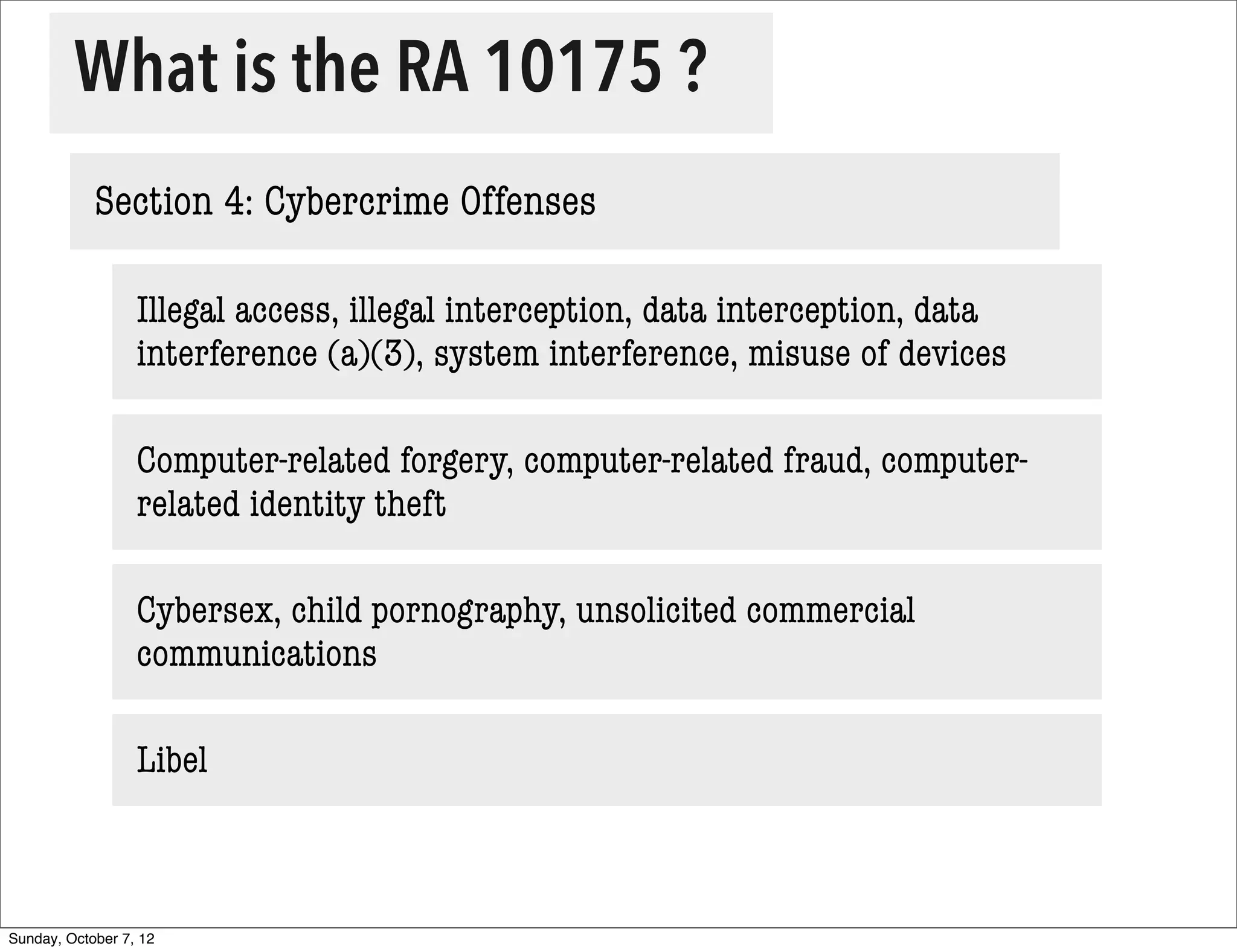
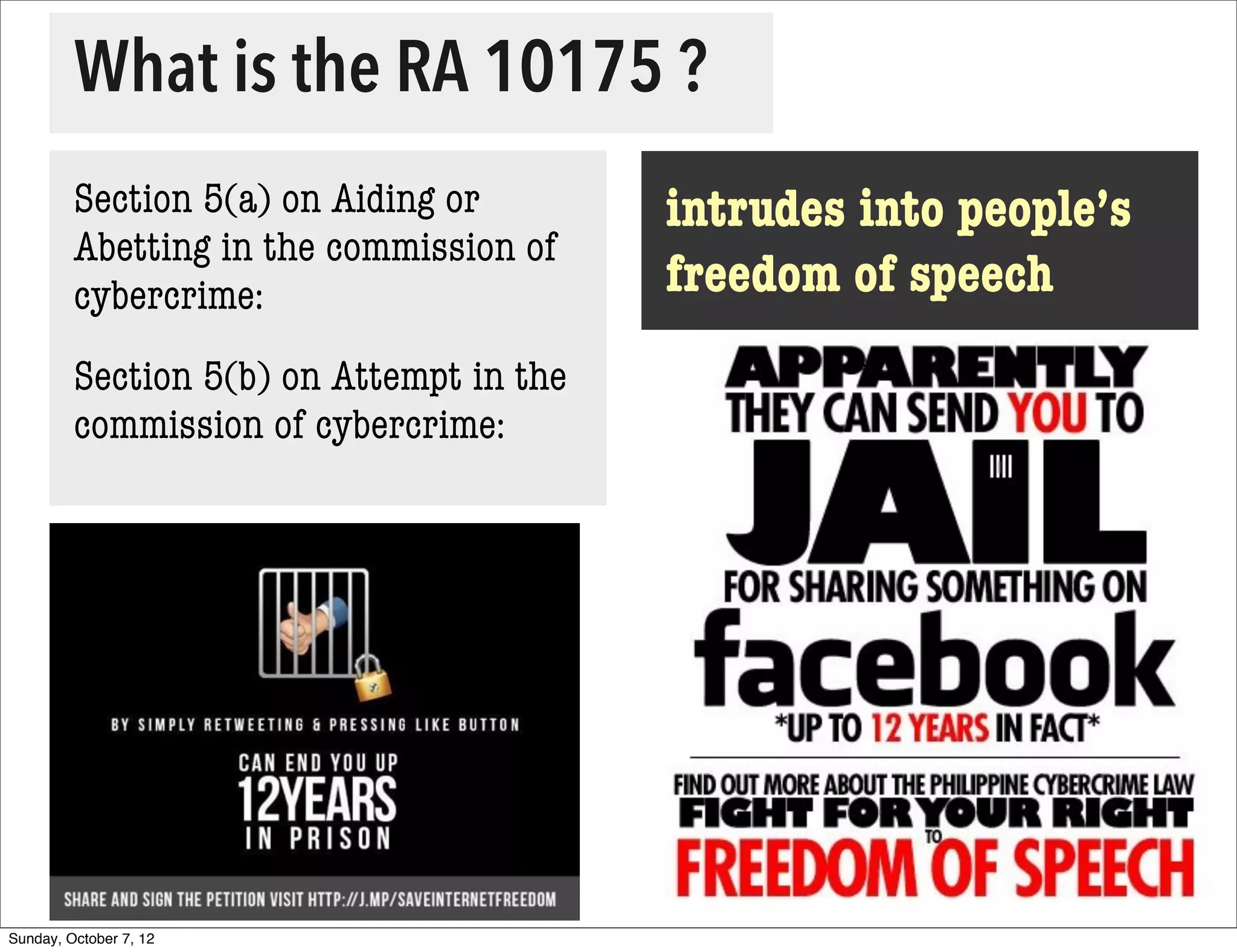
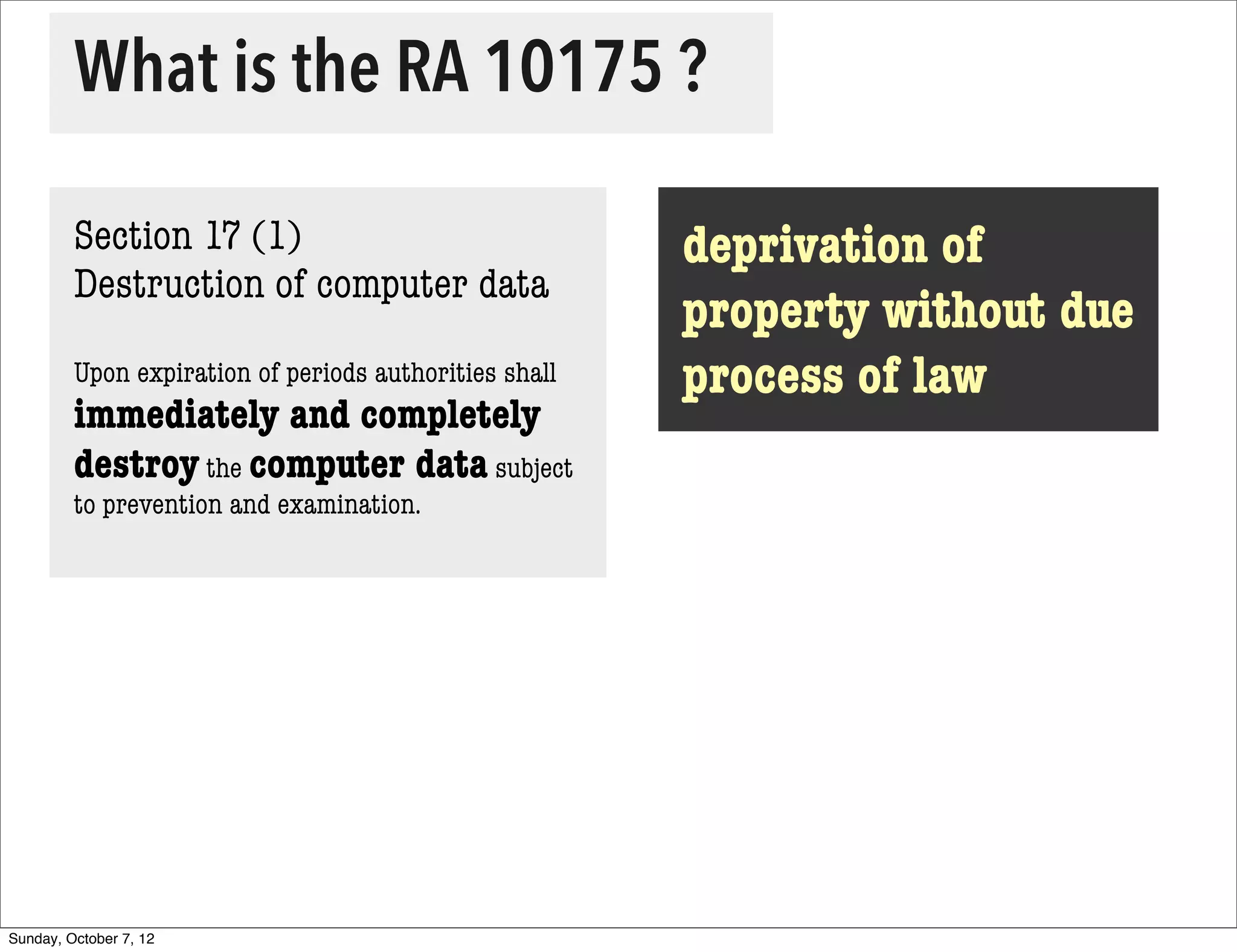
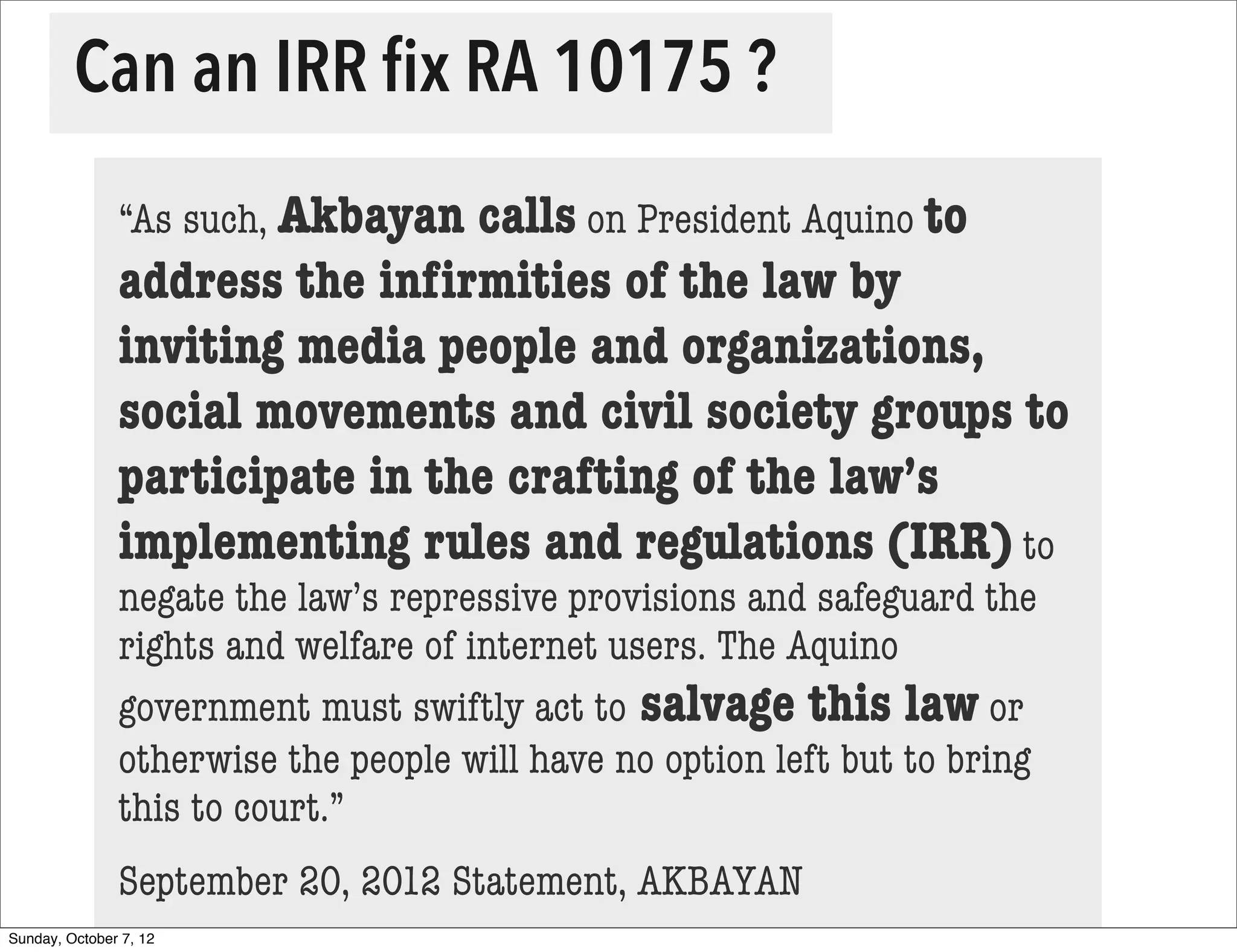
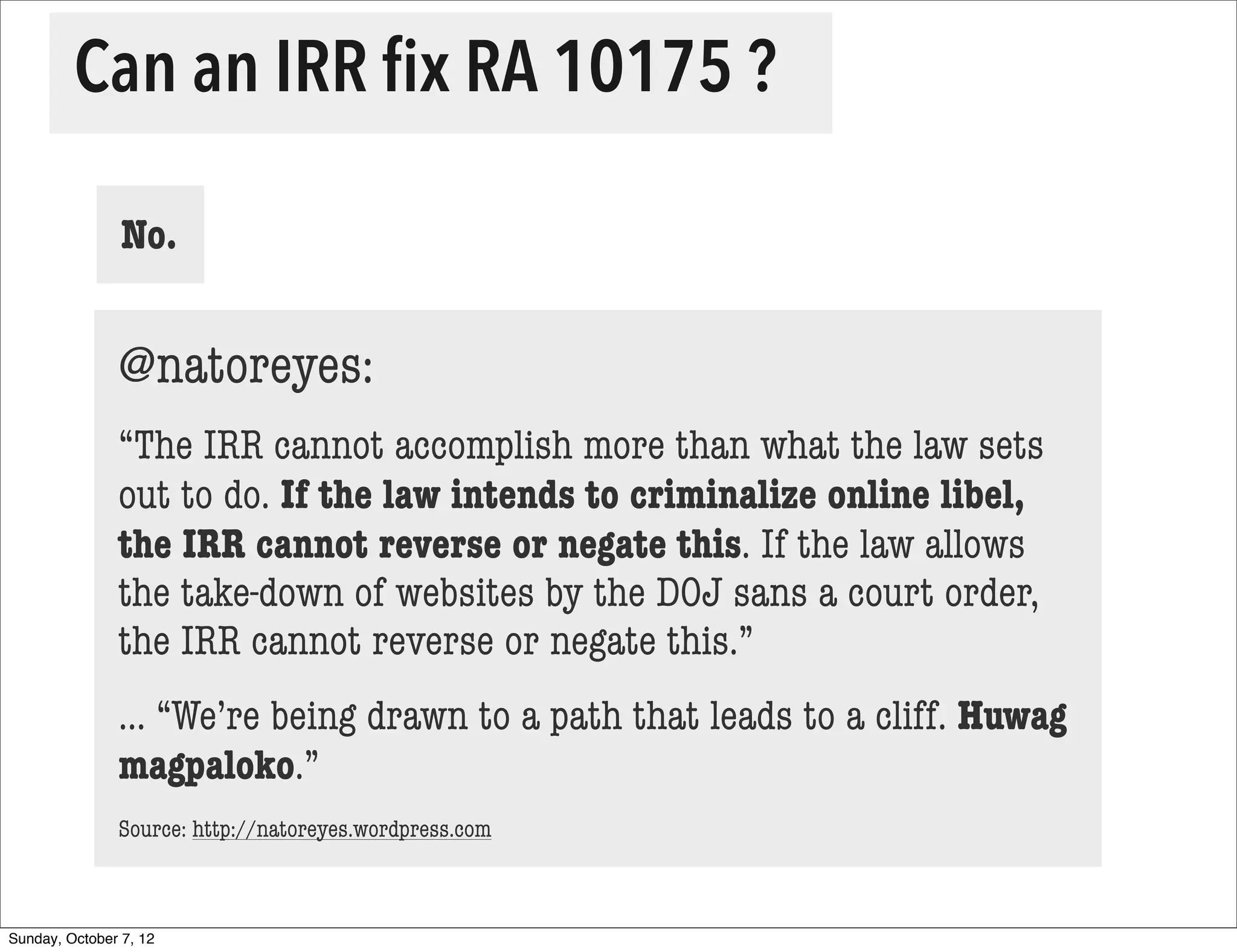
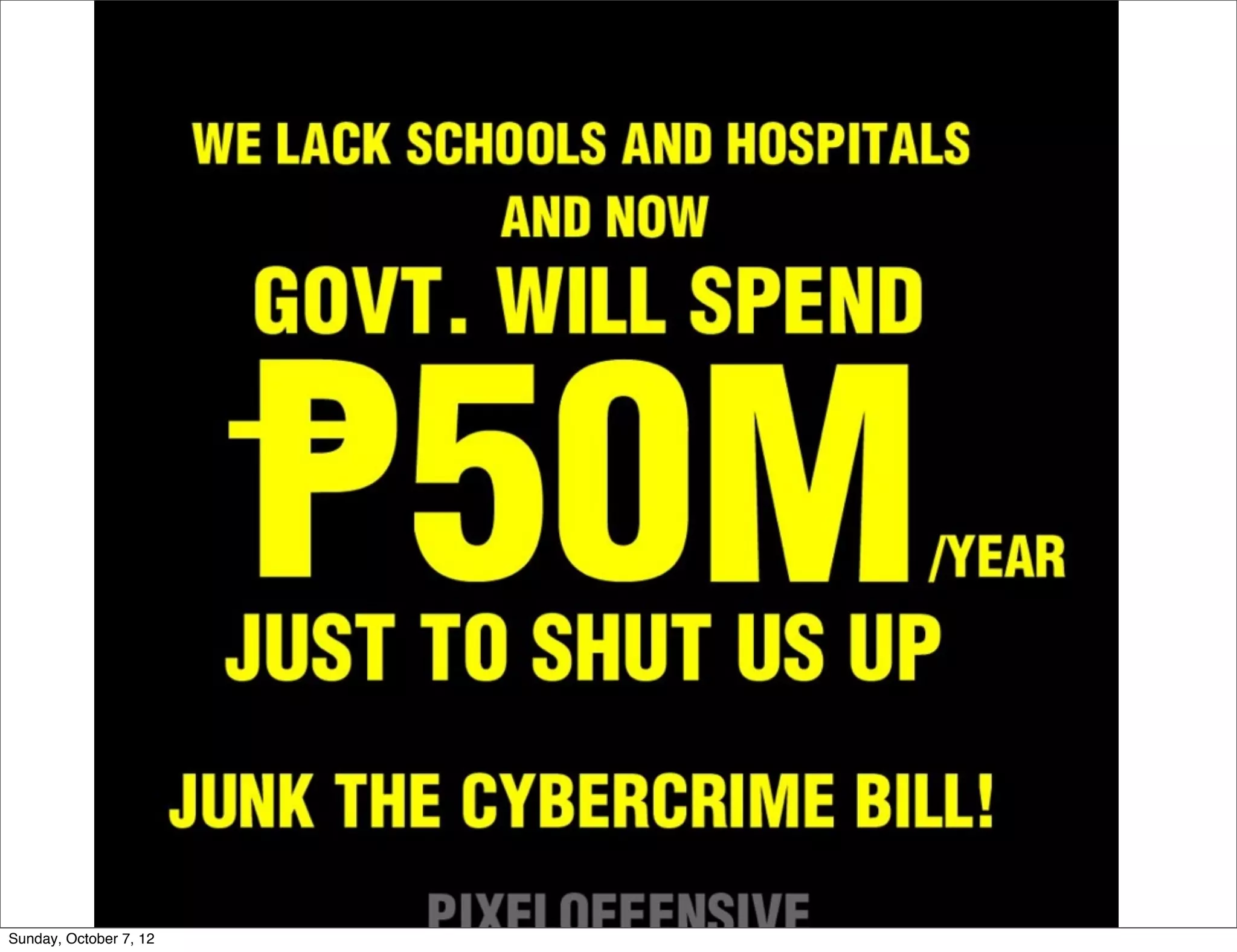
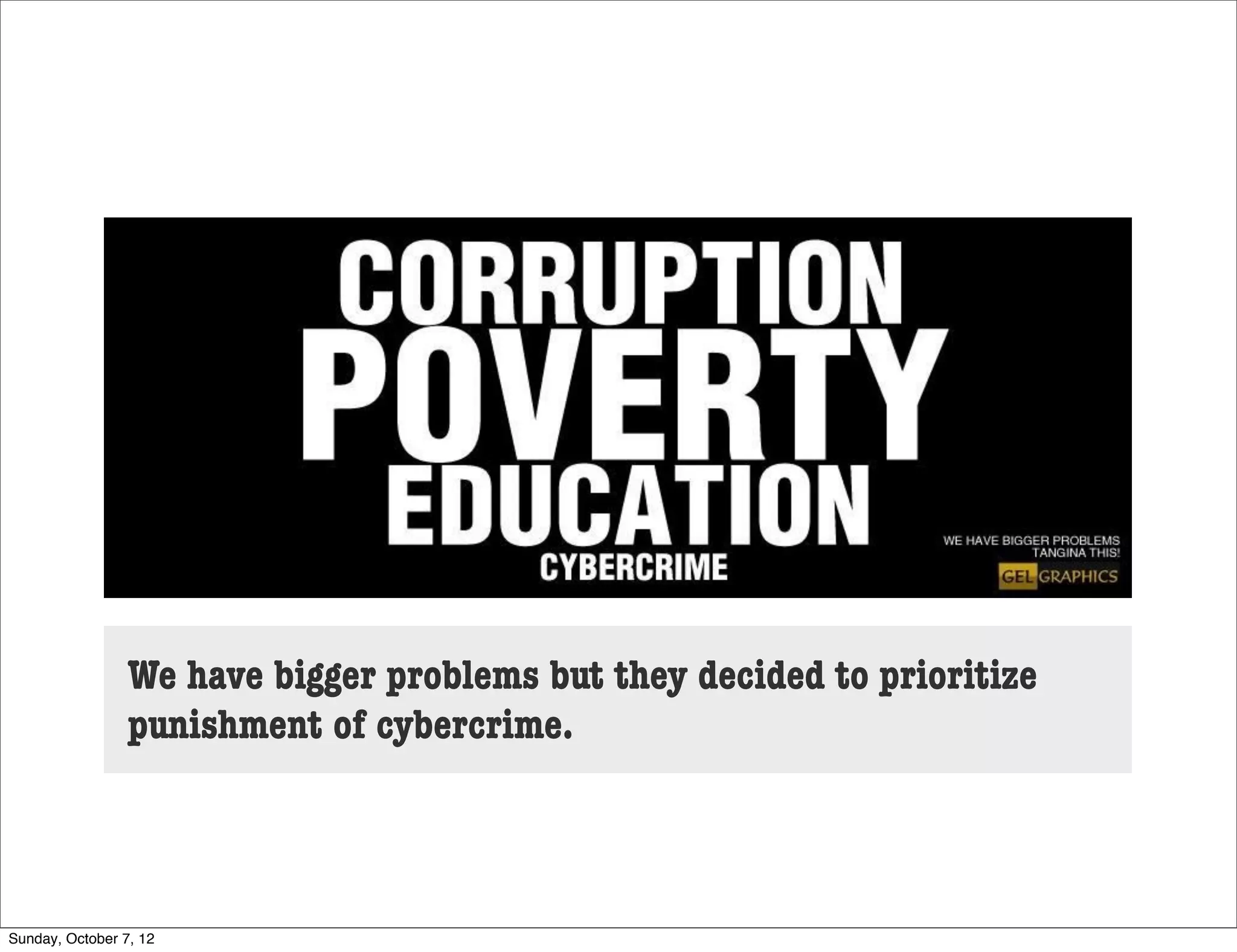
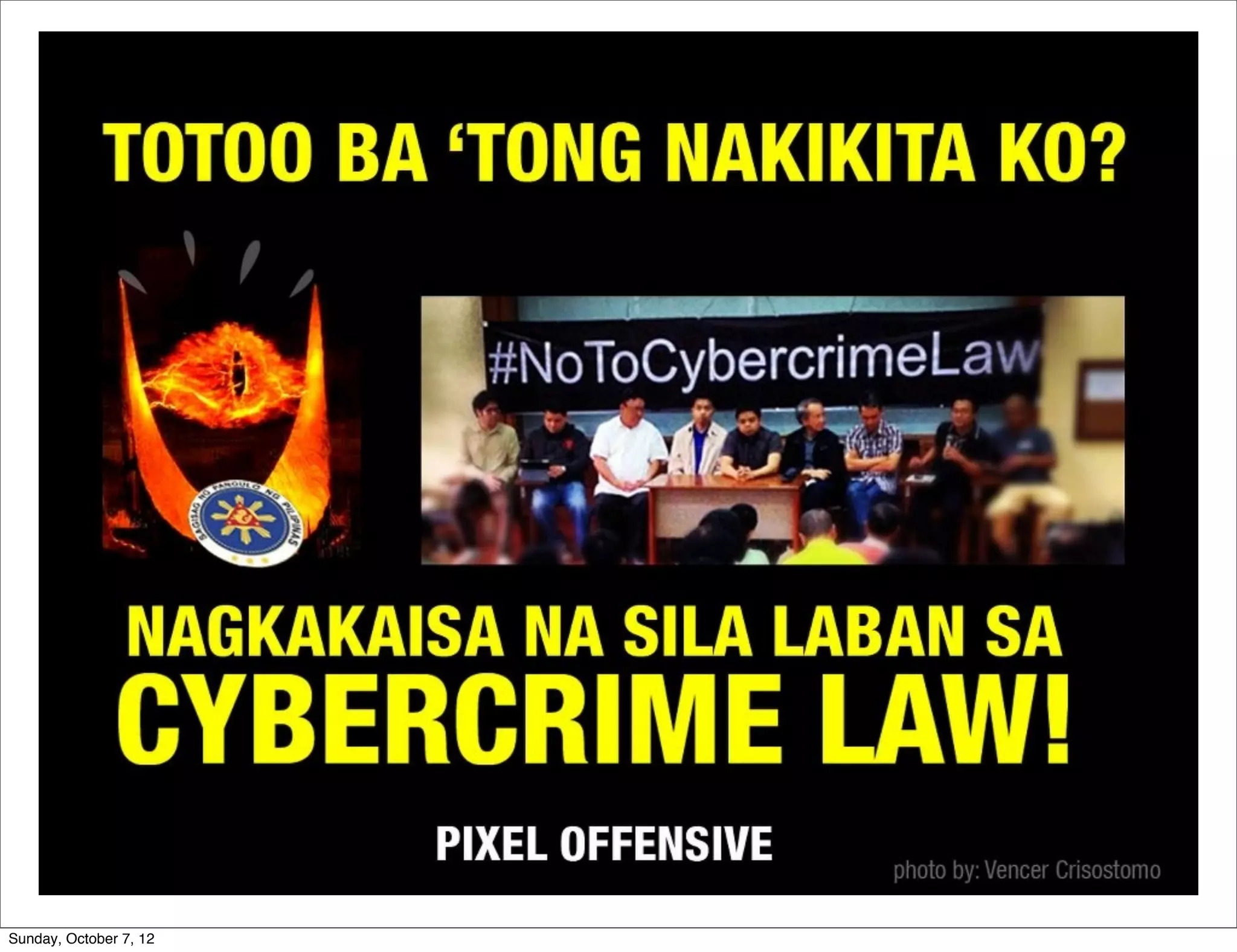
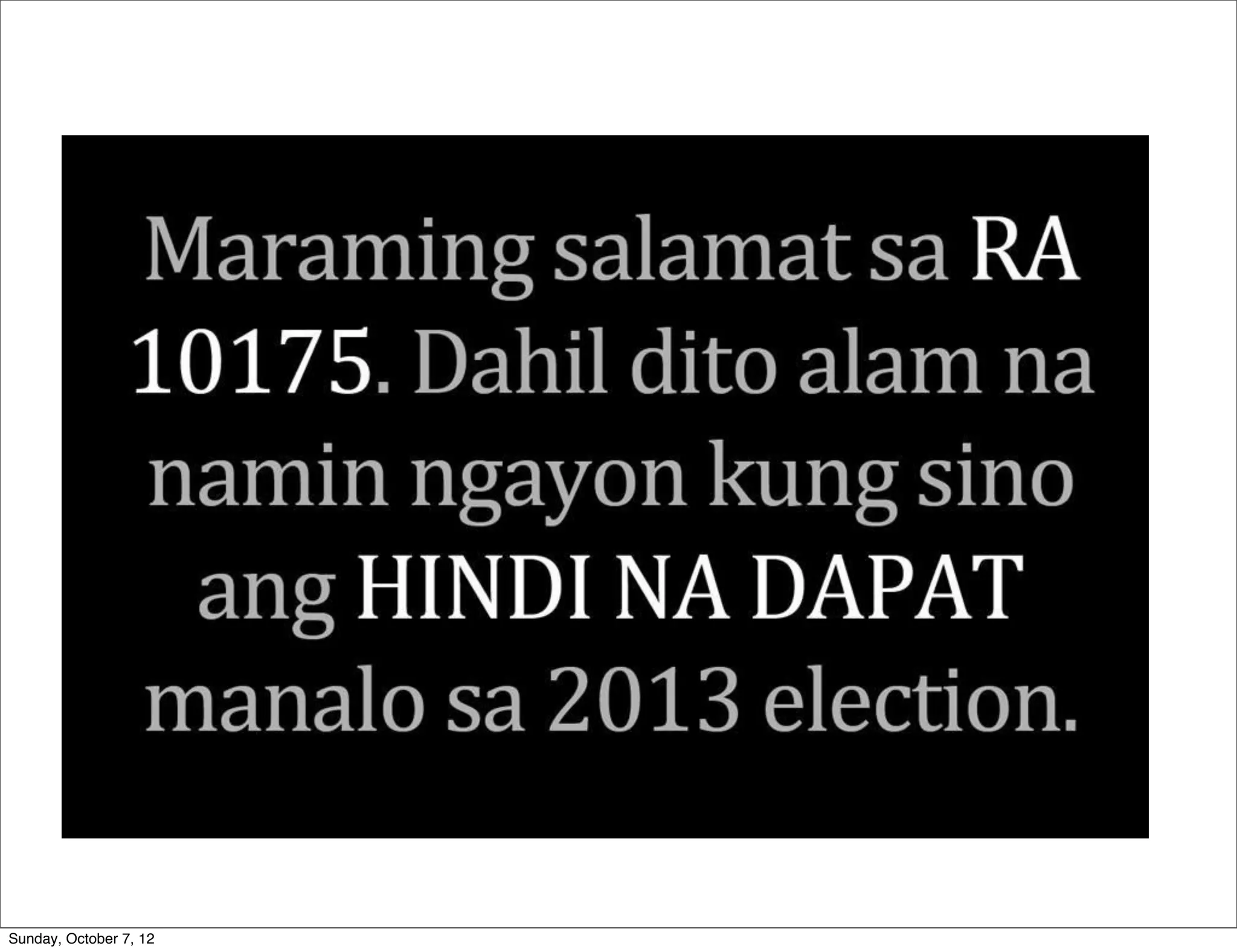
The document summarizes concerns about the Cybercrime Prevention Act of 2012 in the Philippines from the Computer Professionals' Union. It discusses how several provisions in the new law threaten freedom of speech and expression by criminalizing libel and allowing websites to be blocked without due process. It also notes how the law could negatively impact internet users and technology professionals by punishing normal computer use or repair work if they are misinterpreted as cybercrimes. Critics argue the issues cannot be addressed through an implementing regulation and call for challenging the law in court.