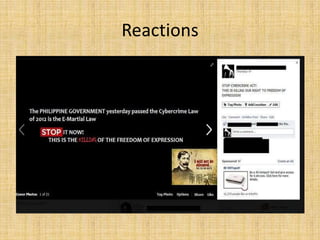
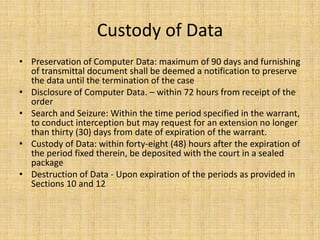
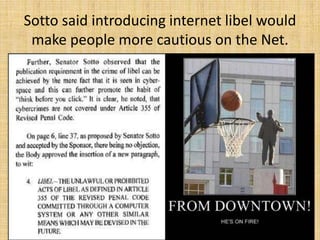
The document outlines Republic Act No. 10175, also known as the Cybercrime Prevention Act of 2012, which defines and penalizes cybercrimes such as illegal access, cybersex, and libel. It establishes the Cybercrime Investigation and Coordinating Center to investigate cybercrimes and allows law enforcement to collect traffic data with a court order. The law was controversial due to introducing internet libel as an offense and was temporarily blocked by the Supreme Court.