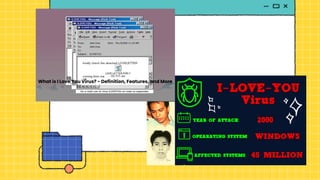
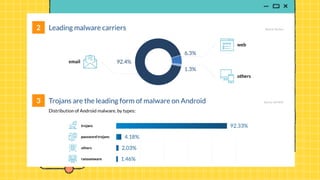
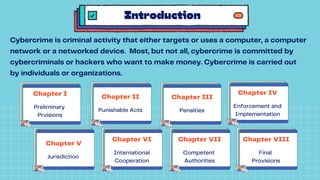
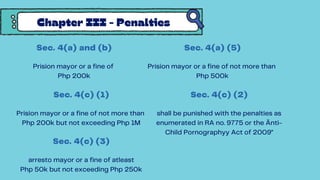
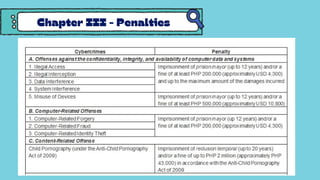
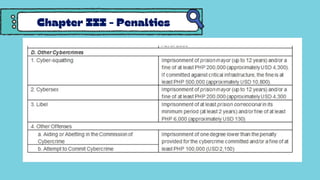
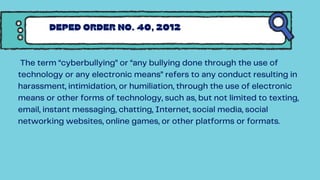
The document discusses the Cybercrime Prevention Act of 2012 in the Philippines. It begins with background on the "I LOVE YOU" computer virus in 2000 that prompted the first cybercrime law. It then summarizes key aspects of RA 10175, including punishable cybercrimes, penalties, enforcement authorities, and international cooperation provisions. Examples are given of types of cybercrimes prosecuted under the act such as identity theft, cyberbullying, and an online sexual exploitation case. The document provides an overview of the Philippine government's efforts to address cybercrime through laws and law enforcement agencies.