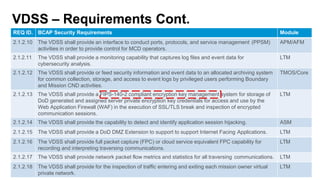
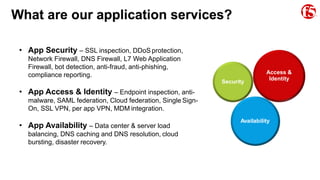
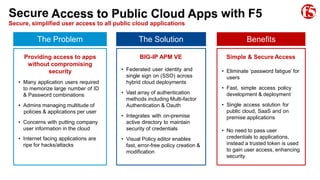
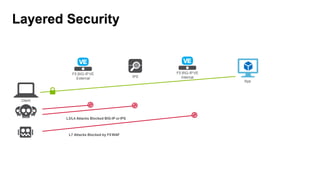
The document discusses F5 solutions for securing applications in Microsoft Azure. It includes details on F5 products like BIG-IP VE, ASM, AFM, and LTM that can provide capabilities like load balancing, application security, firewall, and traffic inspection for workloads running in Azure. The document also includes requirements for a VDSS and VDMS system for a DOD cloud environment and how different F5 modules map to those requirements.