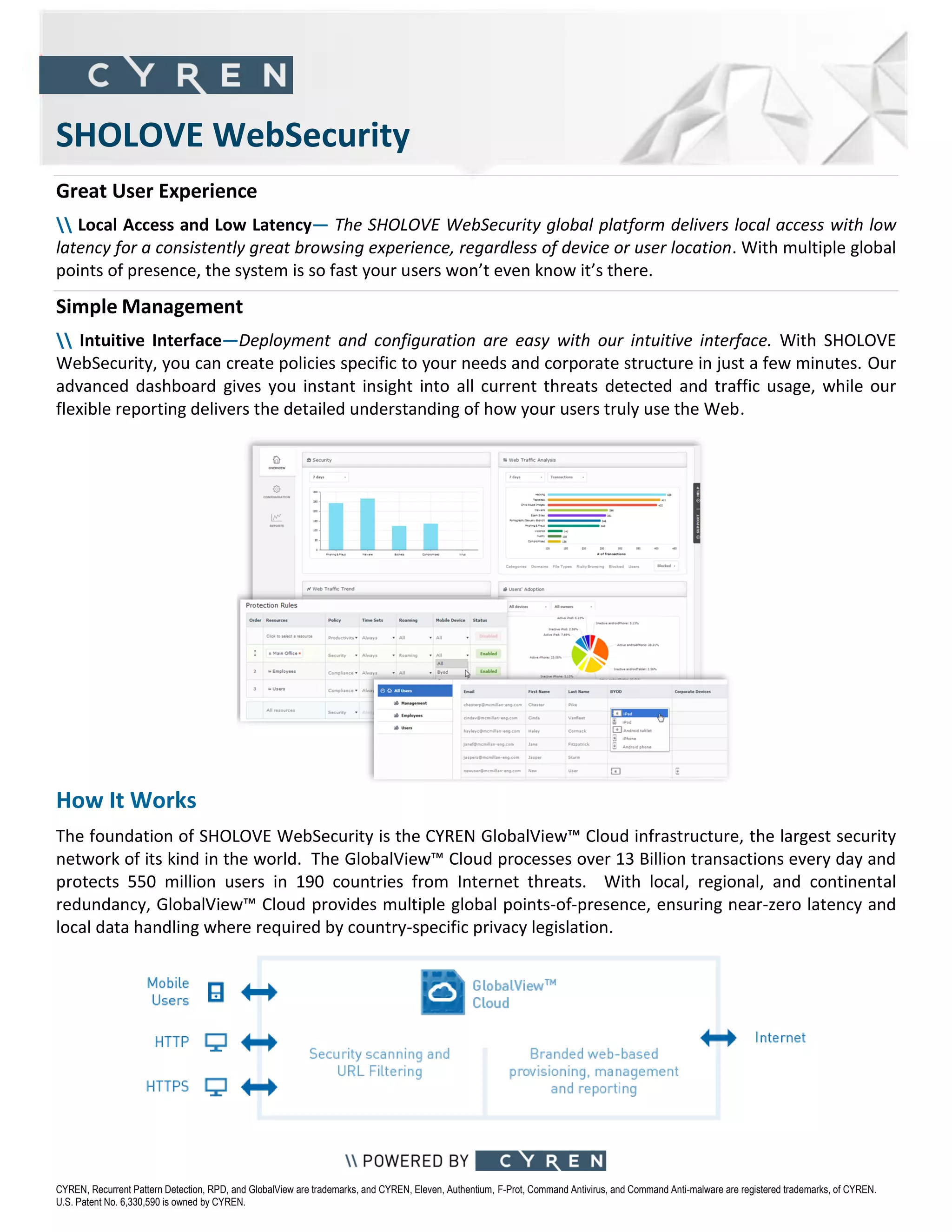
SHOLOVE WebSecurity is a cloud-based security solution that protects employees and enables compliance from threats across devices and locations. It uses the CYREN GlobalView Cloud infrastructure and its analysis of over 13 billion daily transactions to provide advanced protection from malware, phishing, and botnets. The solution offers mobile coverage, low latency experience, and simple management through an intuitive interface.