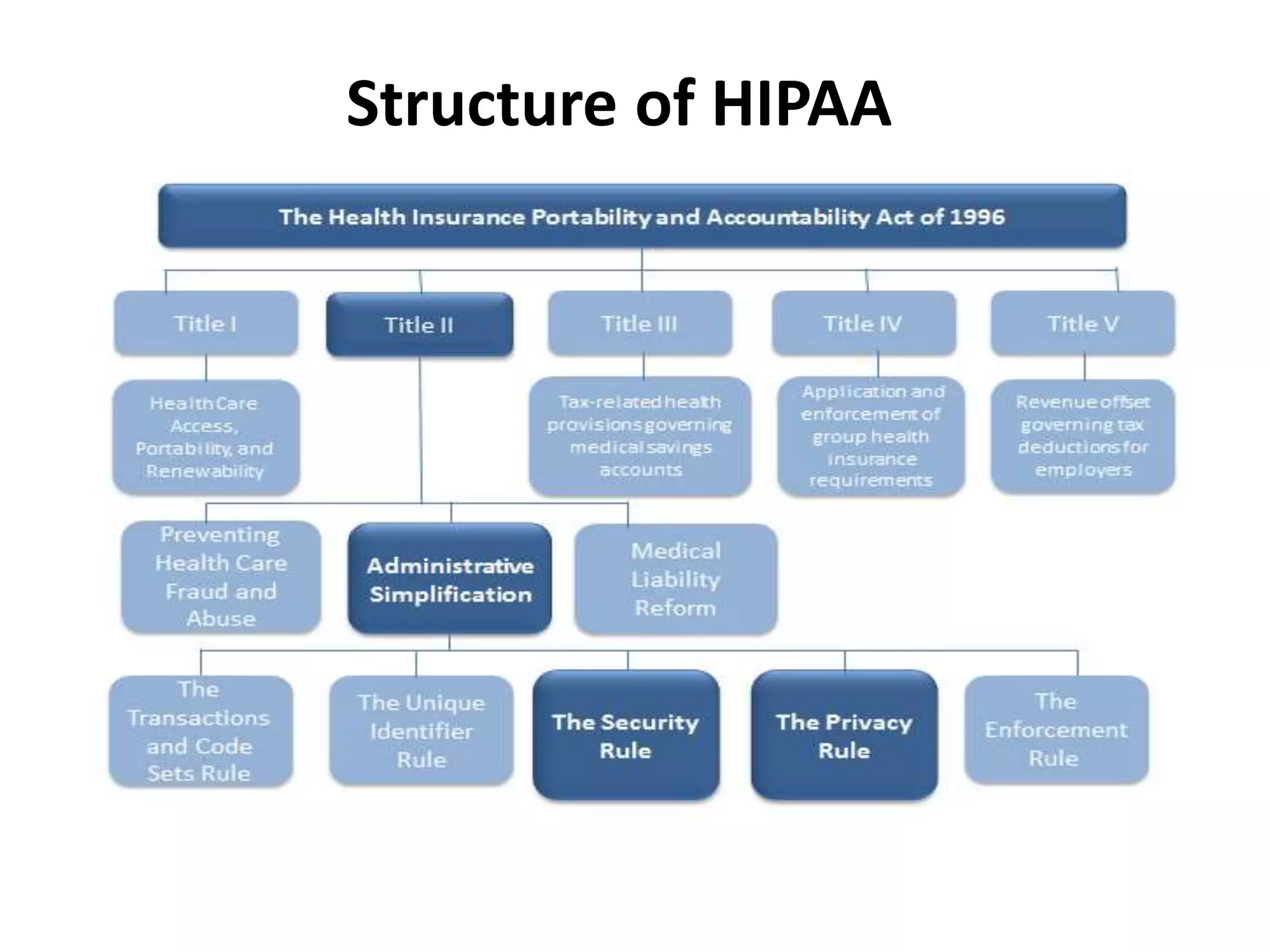
This document discusses the importance of HIPAA compliance for information security. It begins with an introduction of the author and agenda. It then explains what HIPAA is, why it was implemented, and who are covered entities and business associates. The three pillars of HIPAA compliance are described as the Privacy Rule, Security Rule, and Breach Notification Rule. Covered entities are defined as healthcare organizations that store, process or transmit personal health information. Business associates provide services to covered entities and must also comply with HIPAA. The document outlines key aspects of each HIPAA component and requirements for breach notification. It emphasizes the critical need for organizations to understand and follow HIPAA regulations to protect private health information and reduce liability