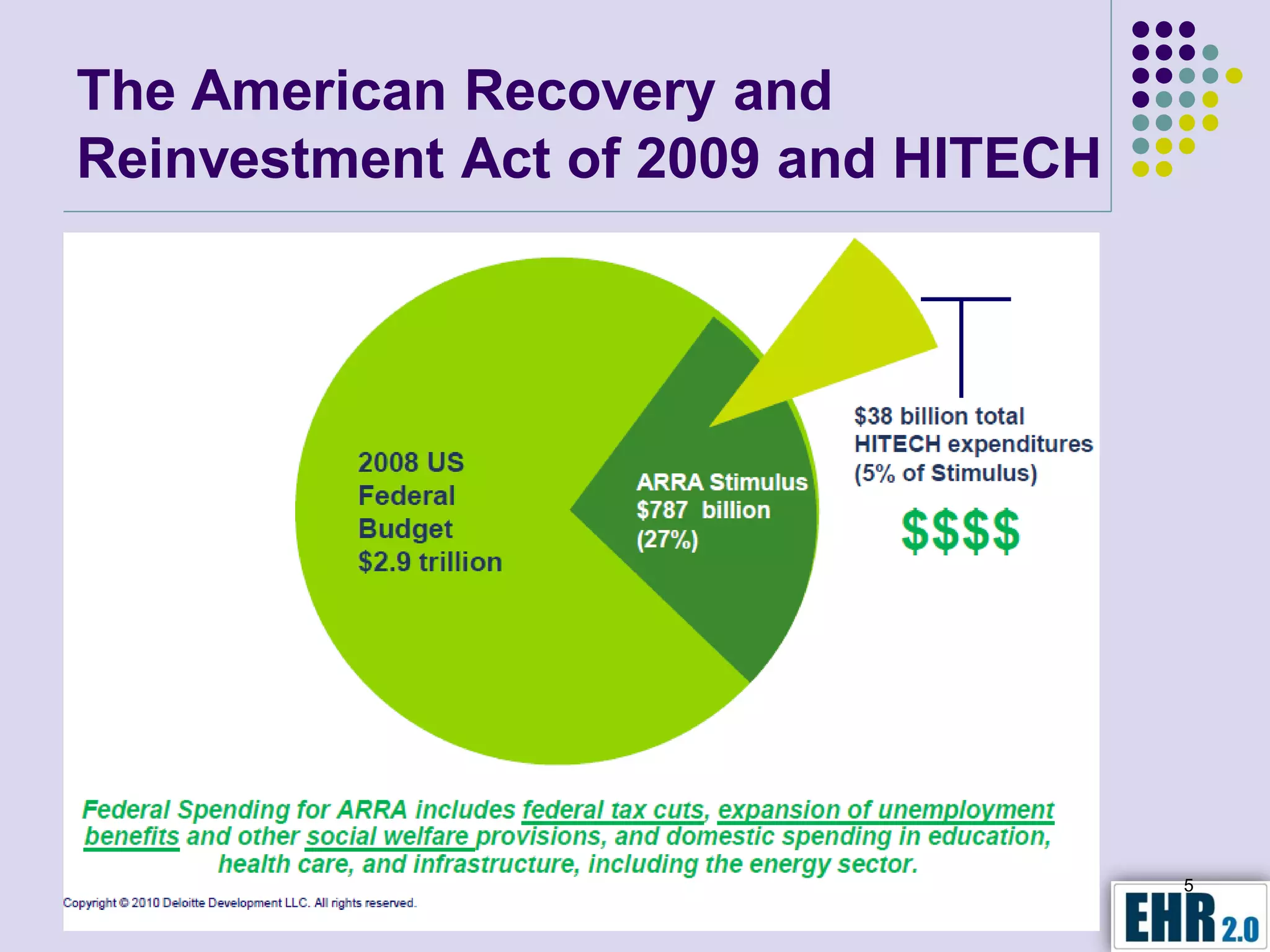
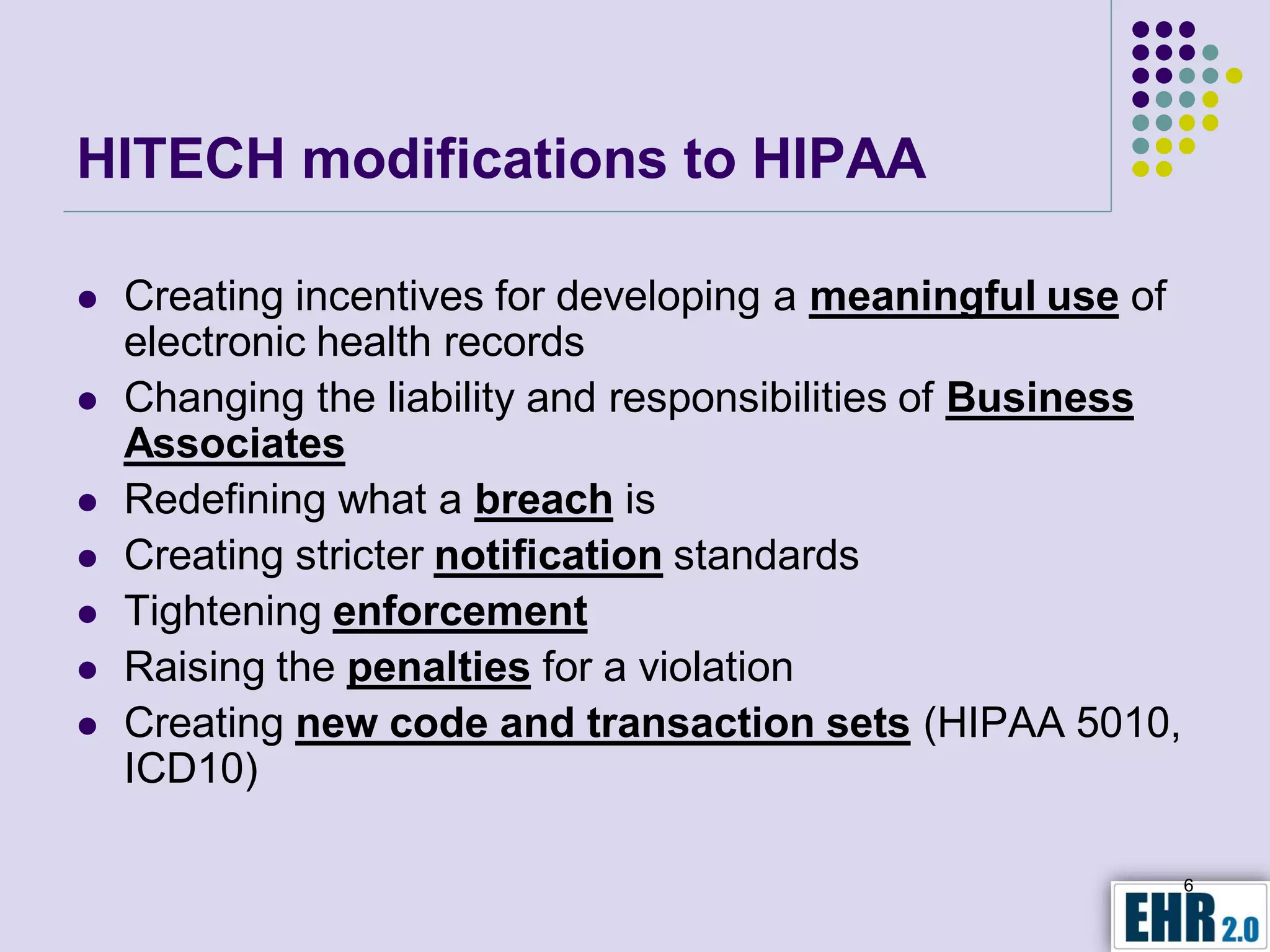
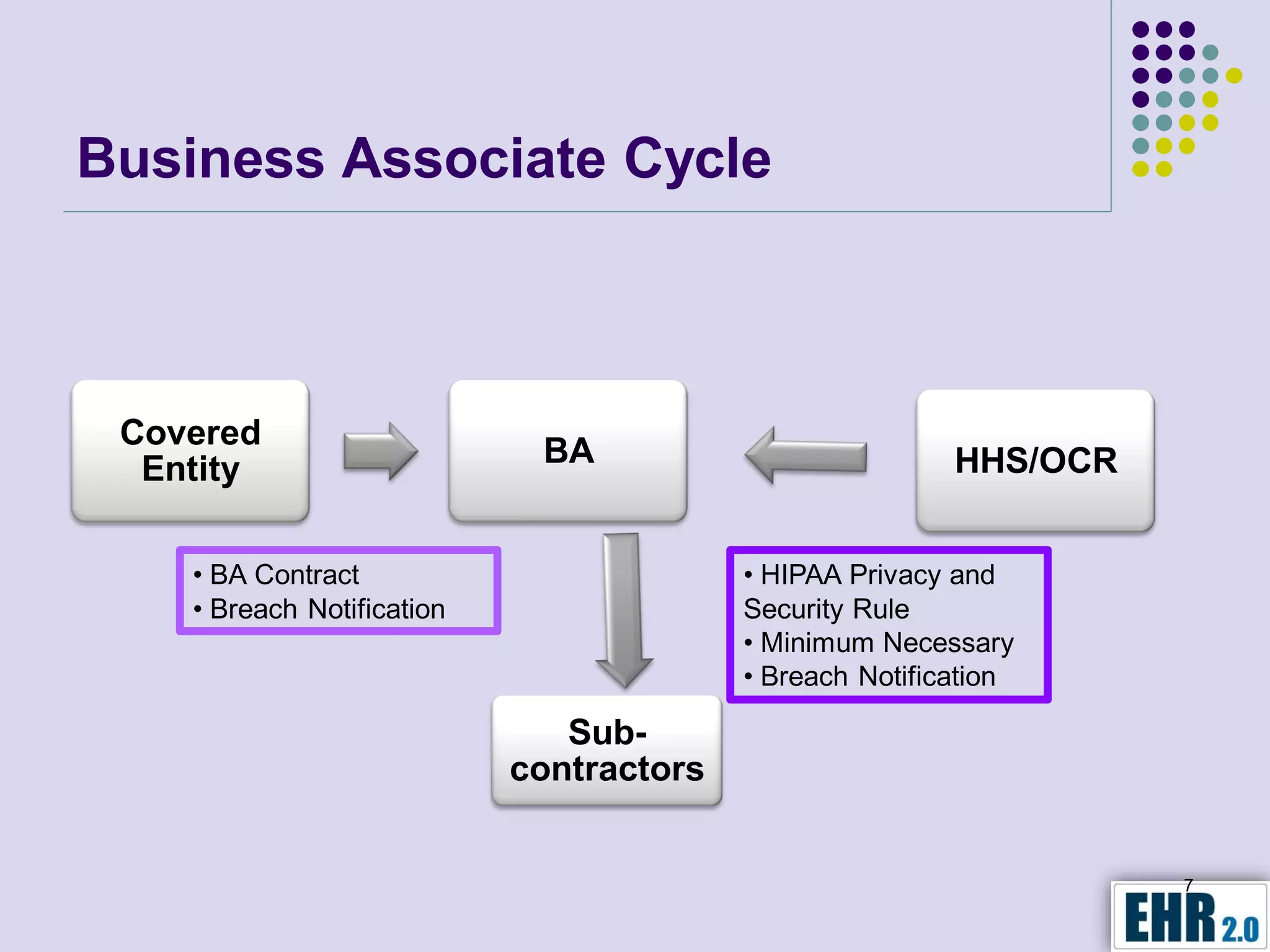
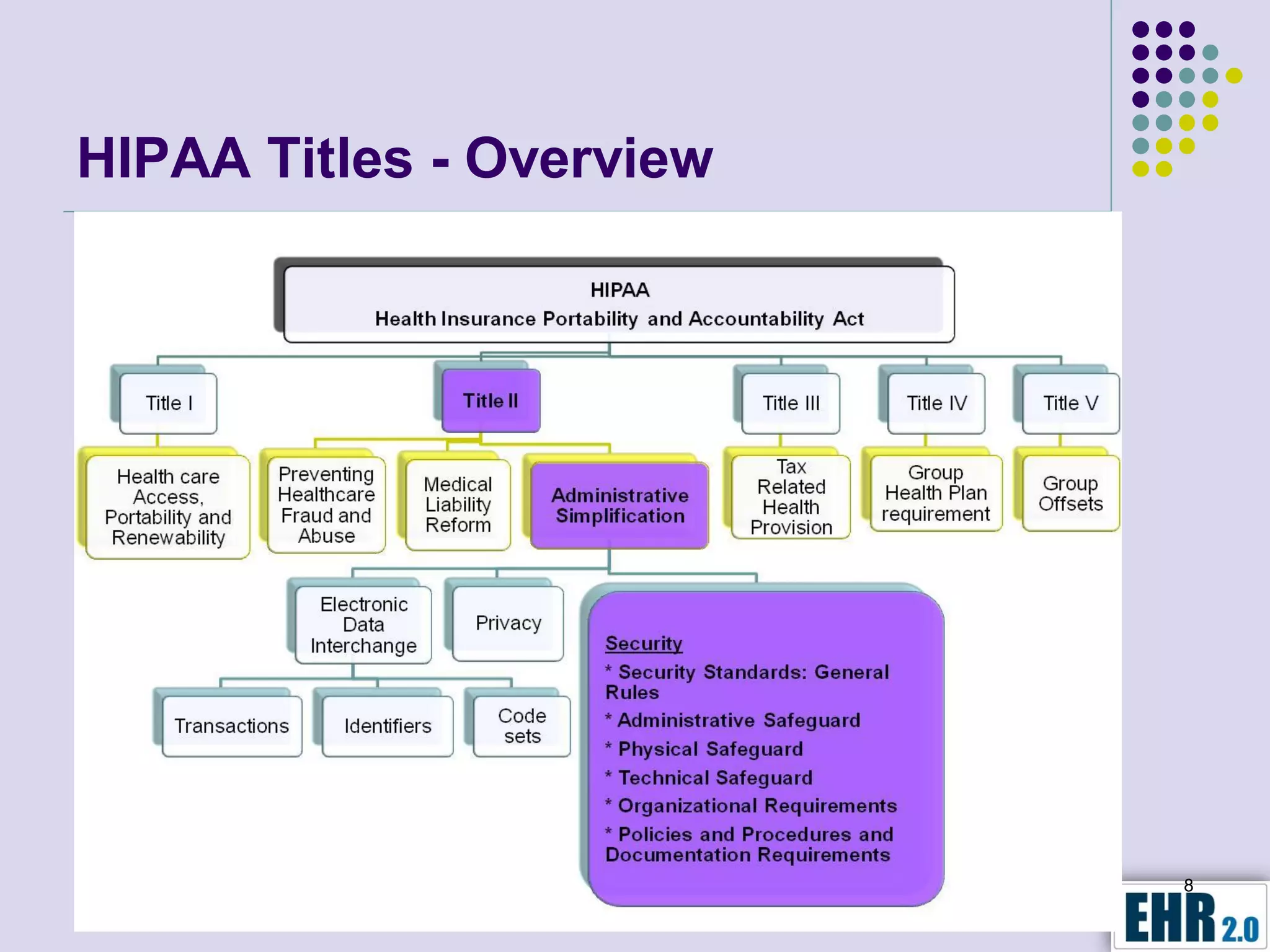
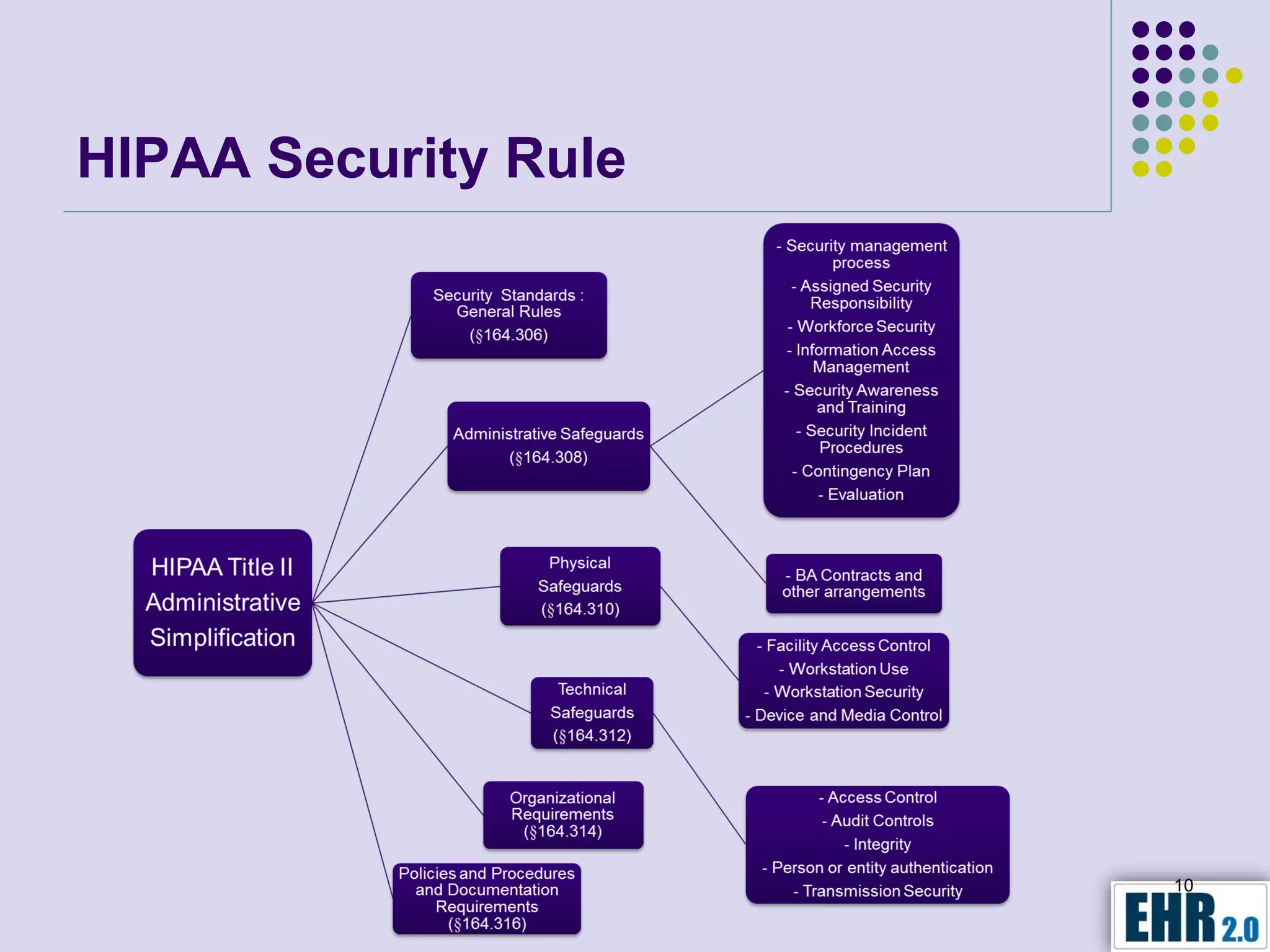
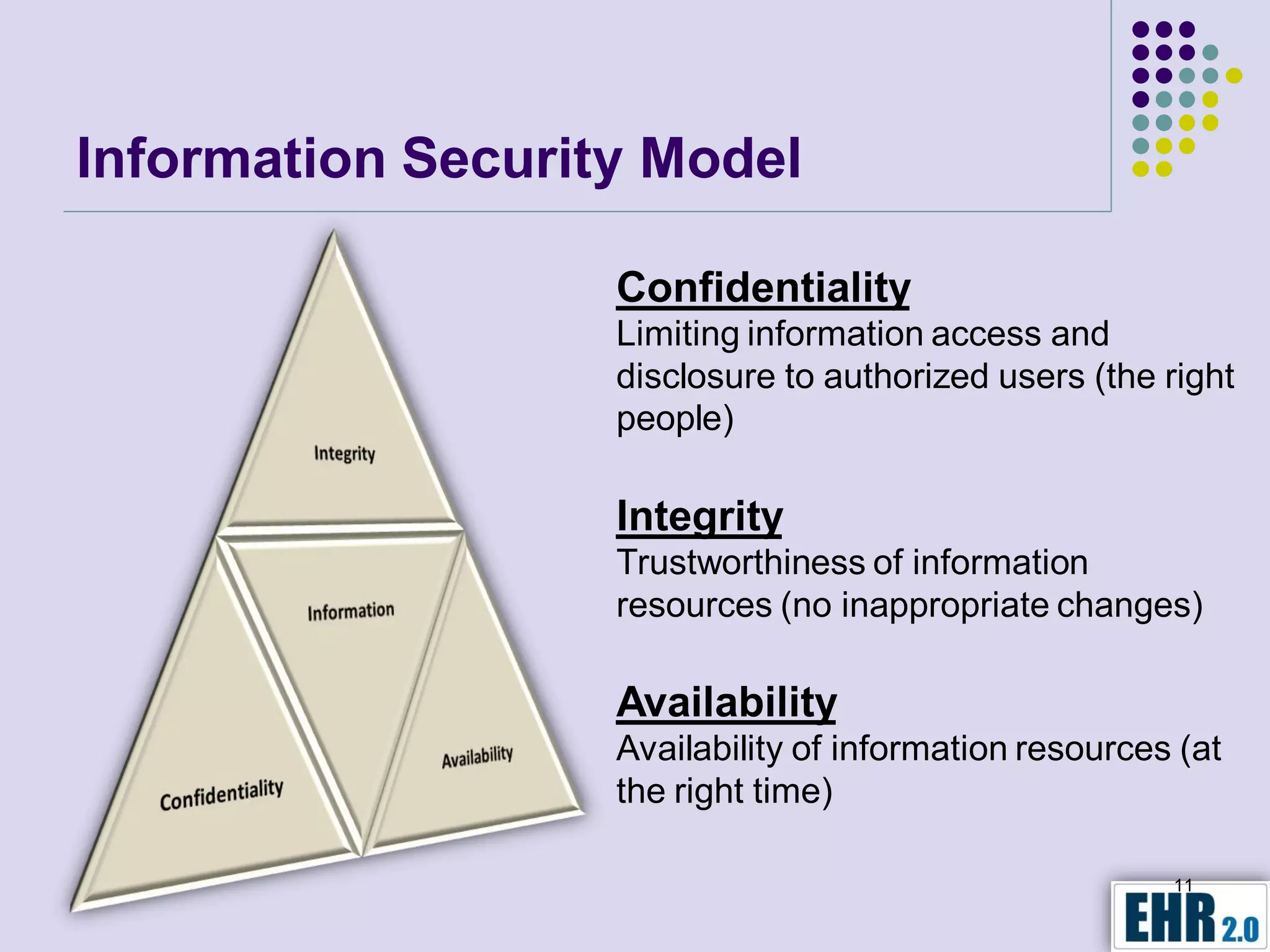
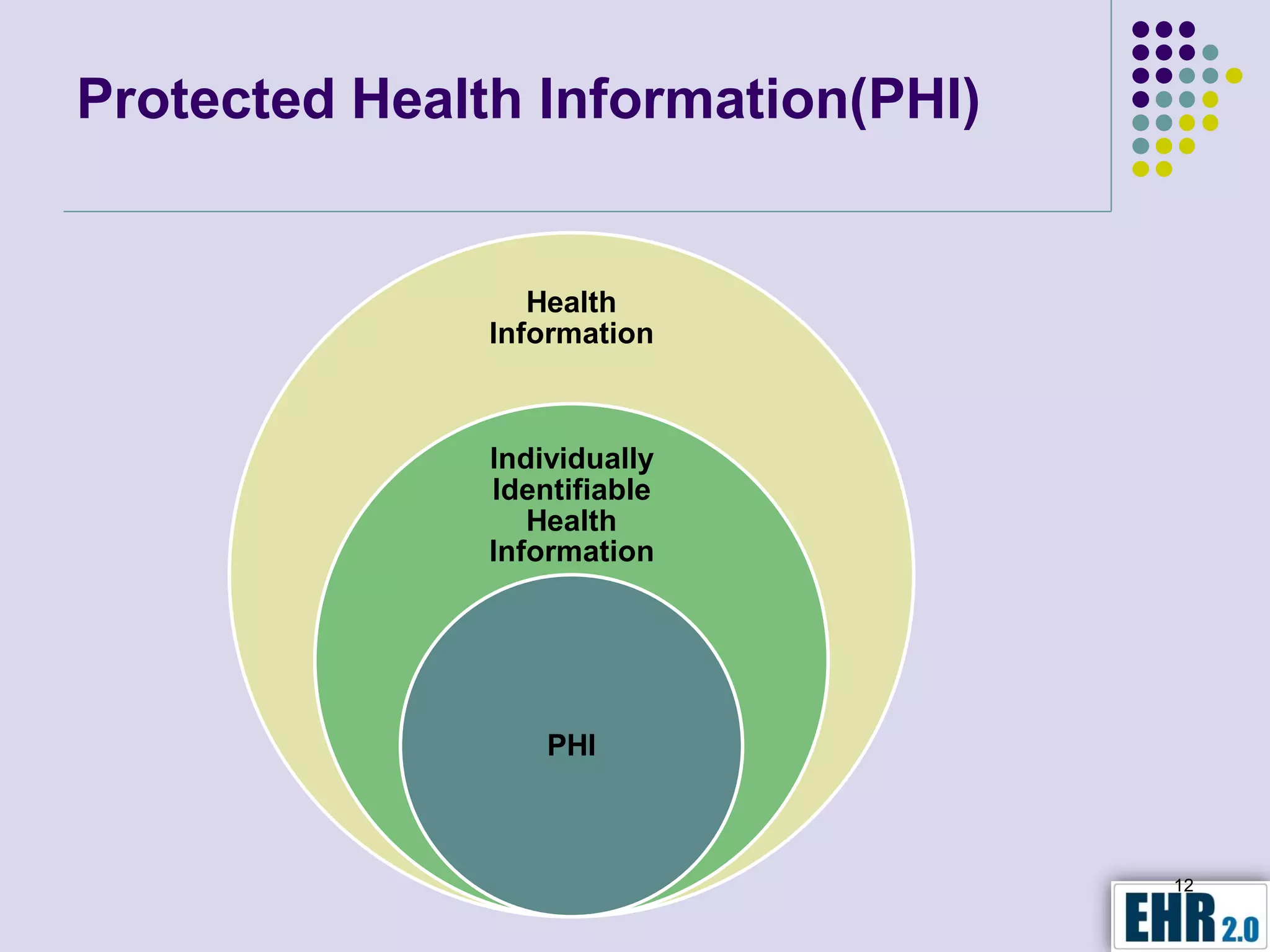
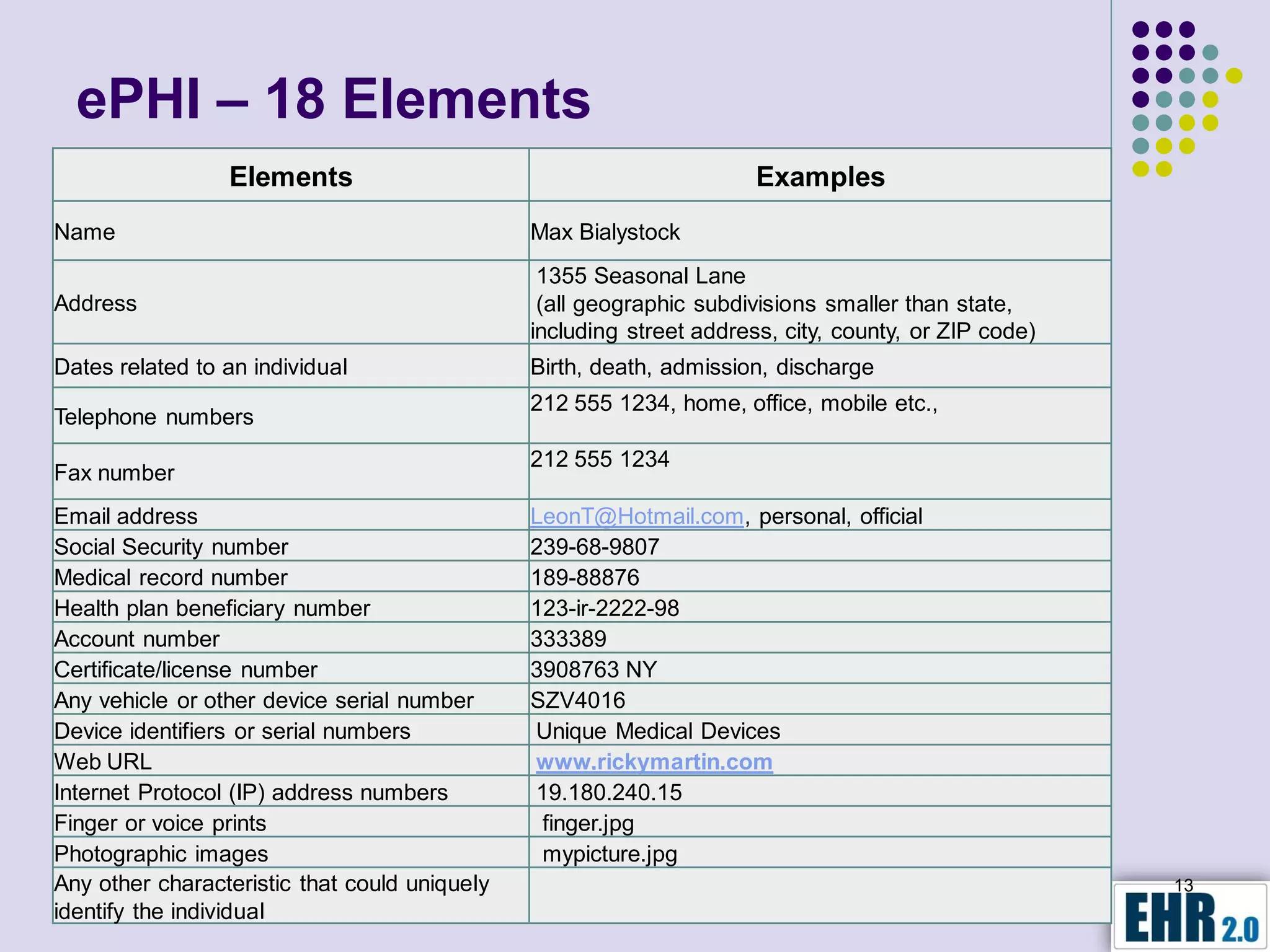
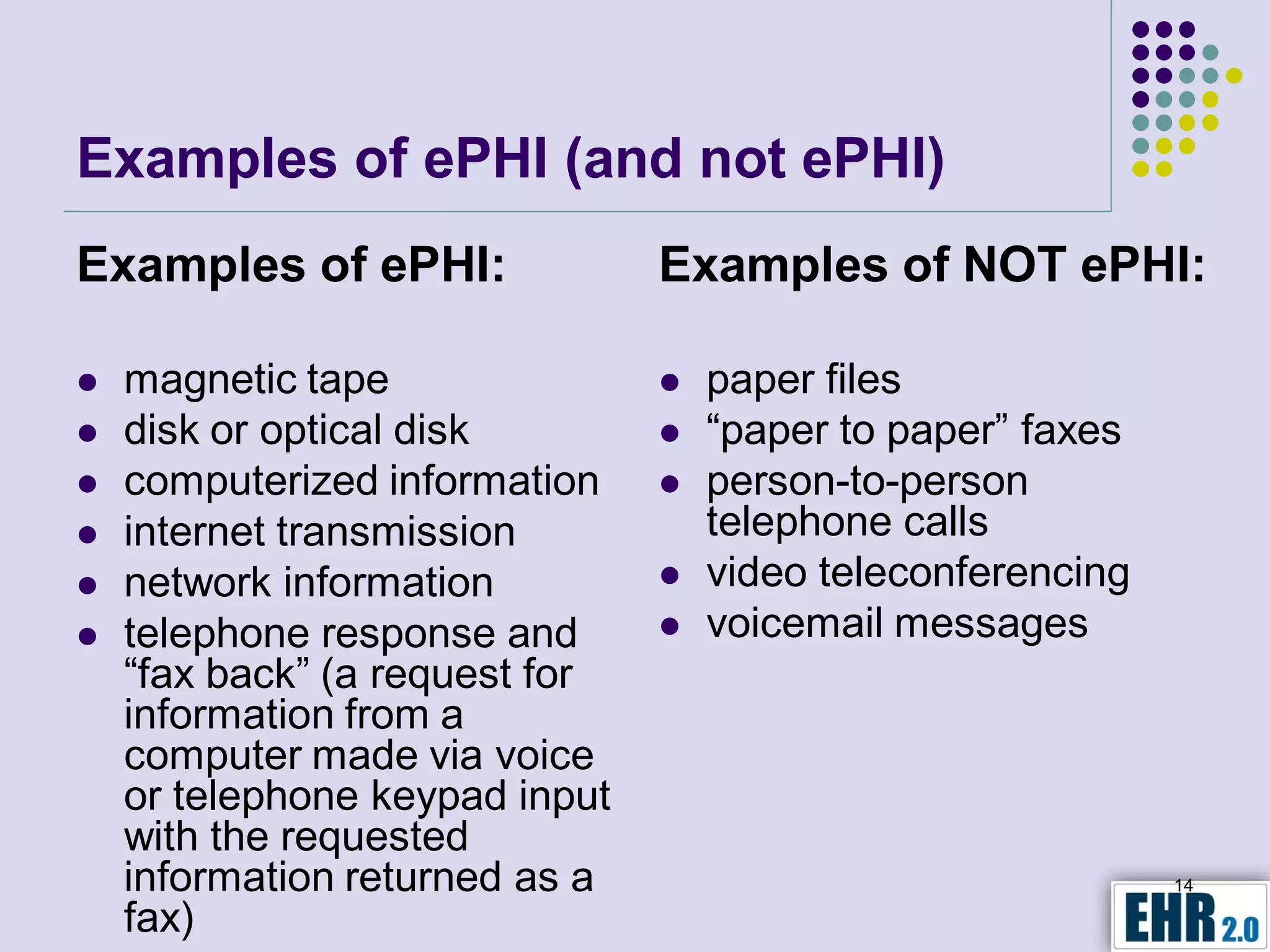
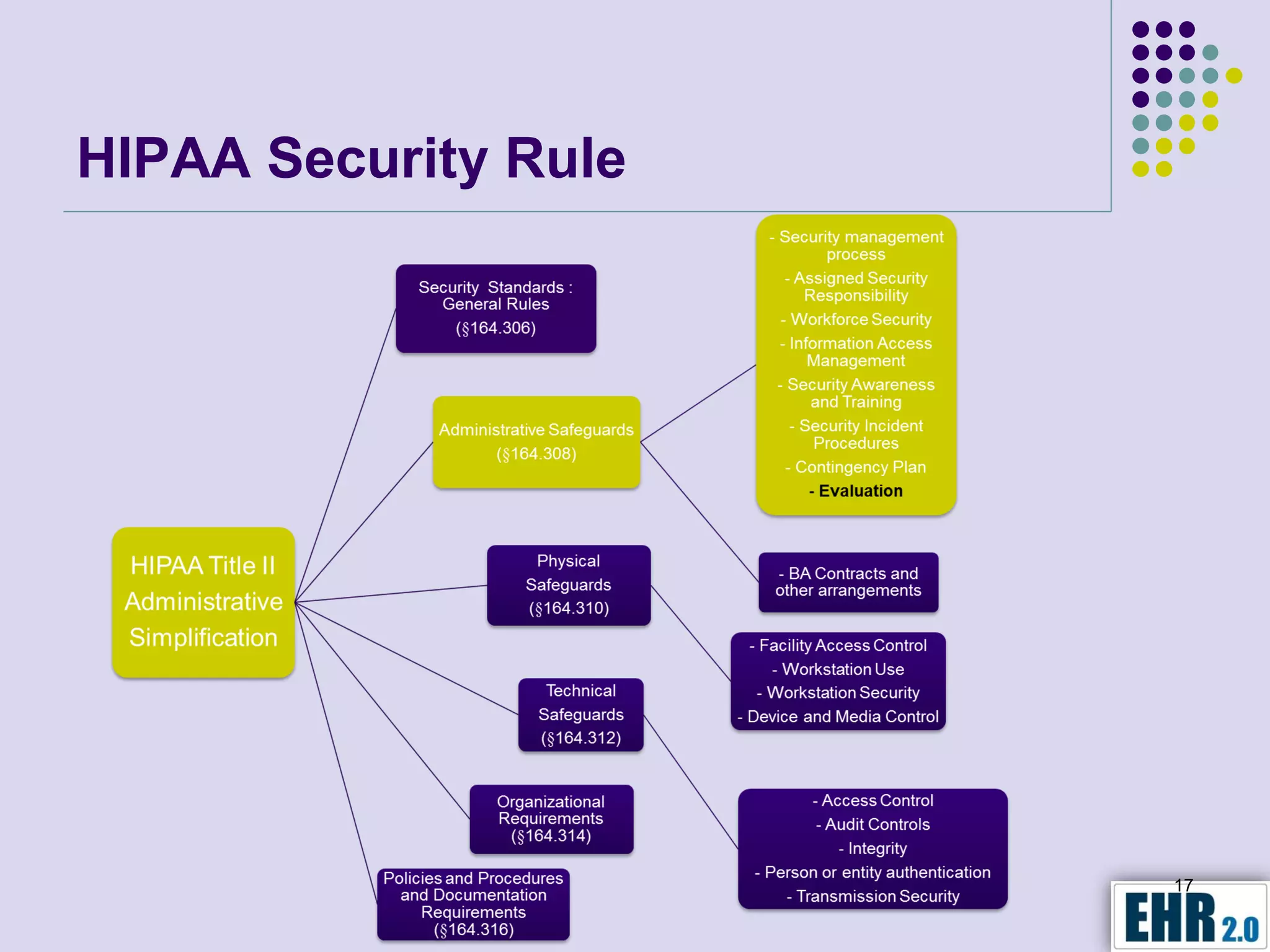
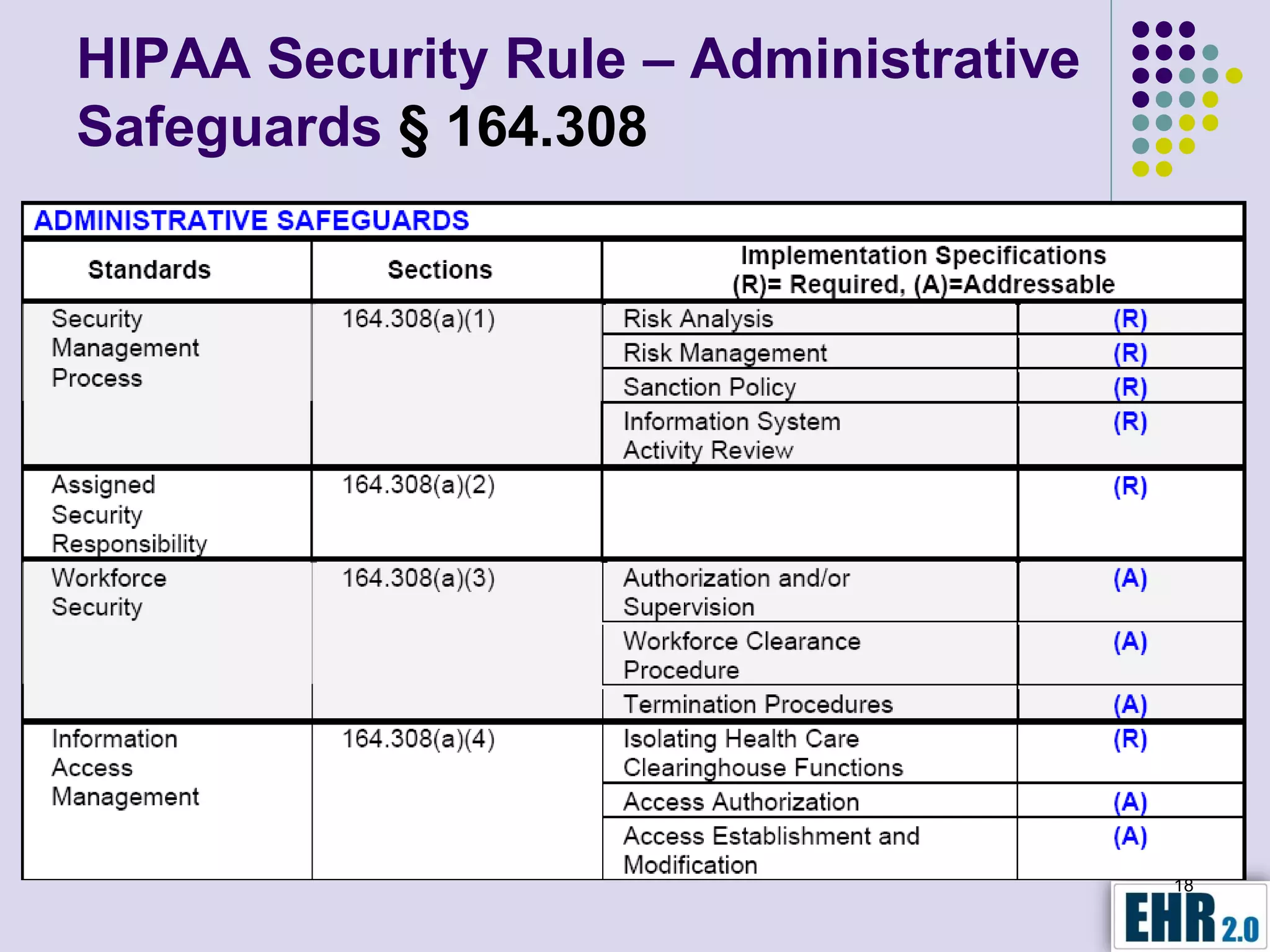
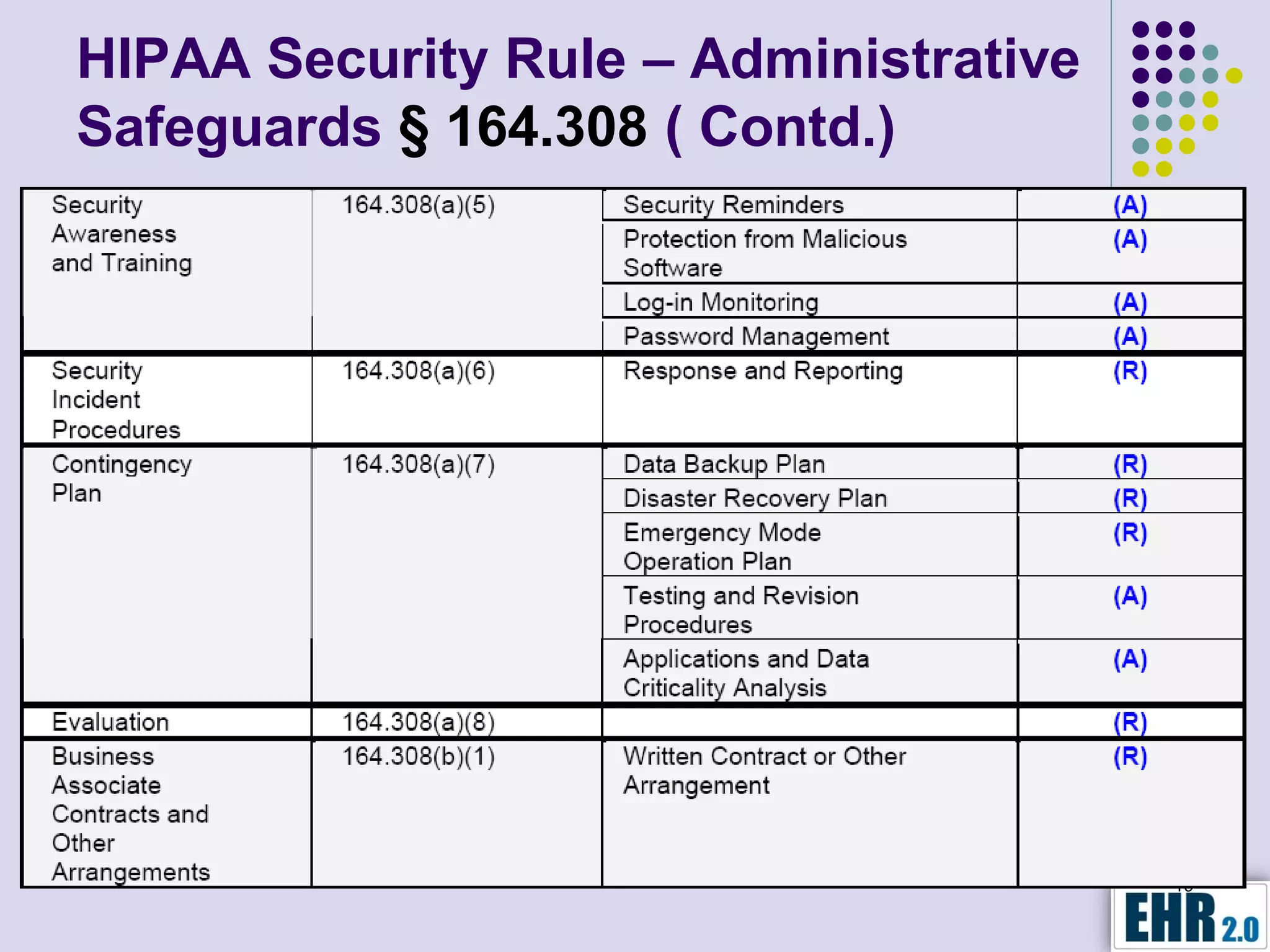
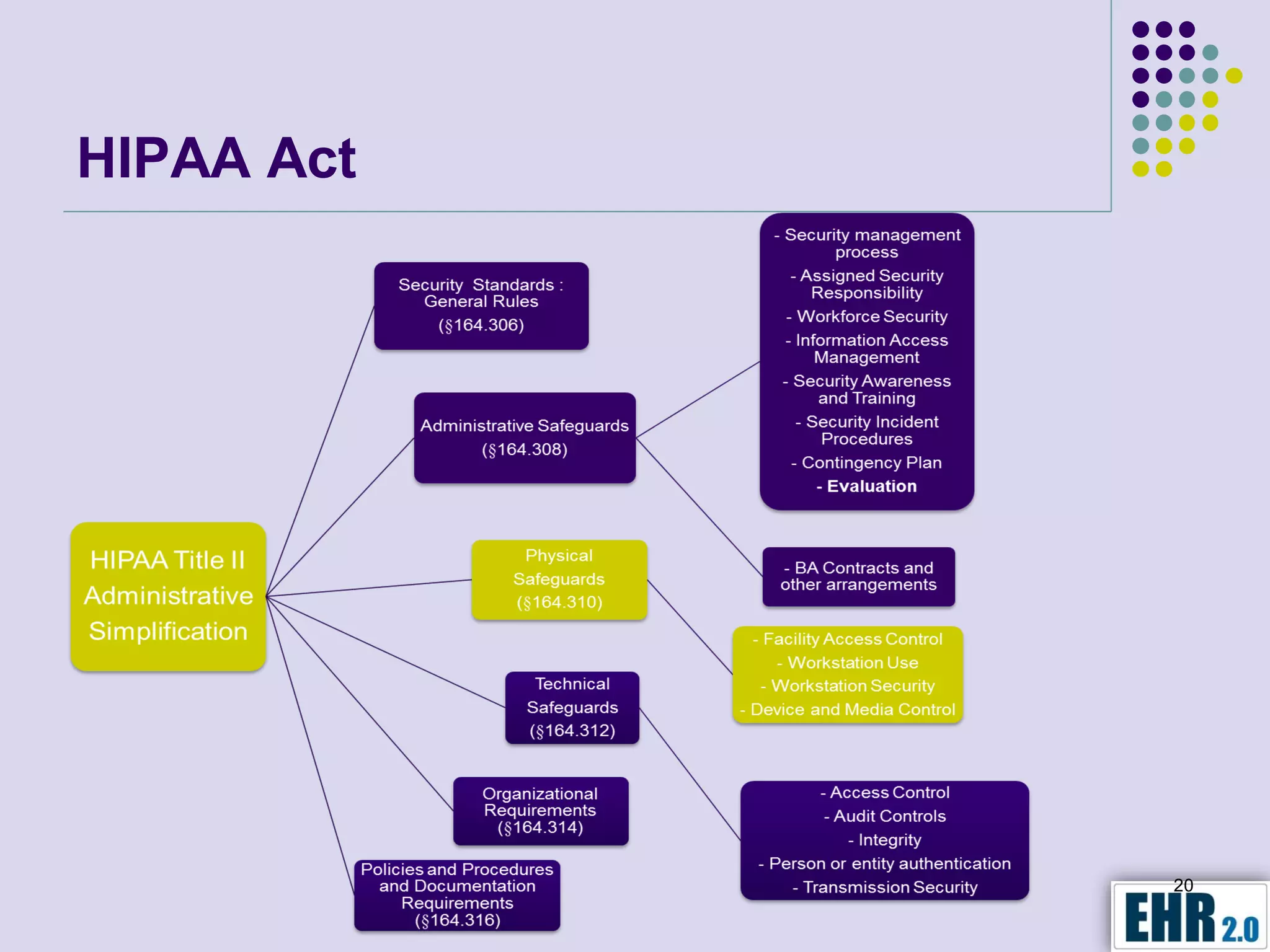
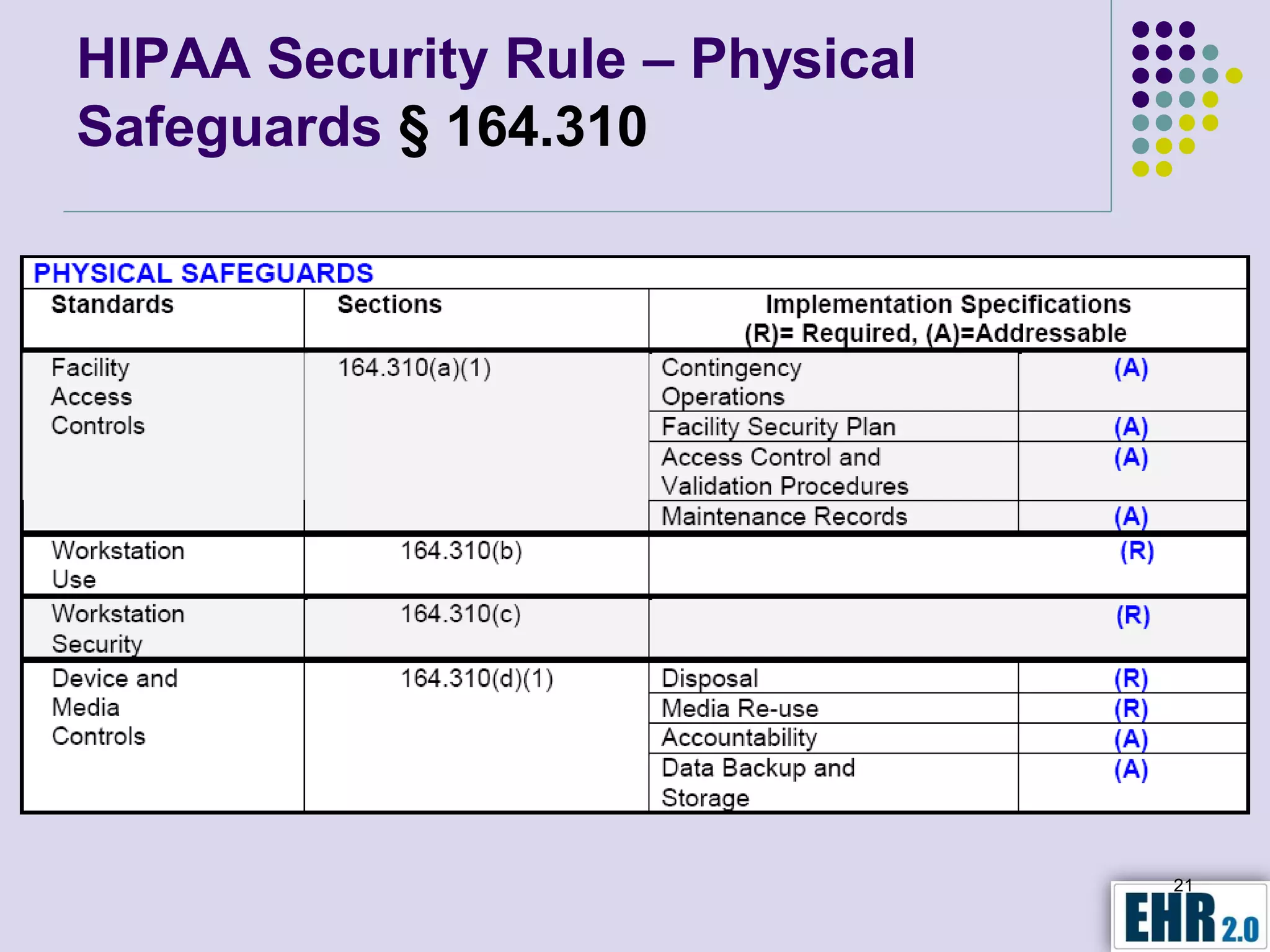
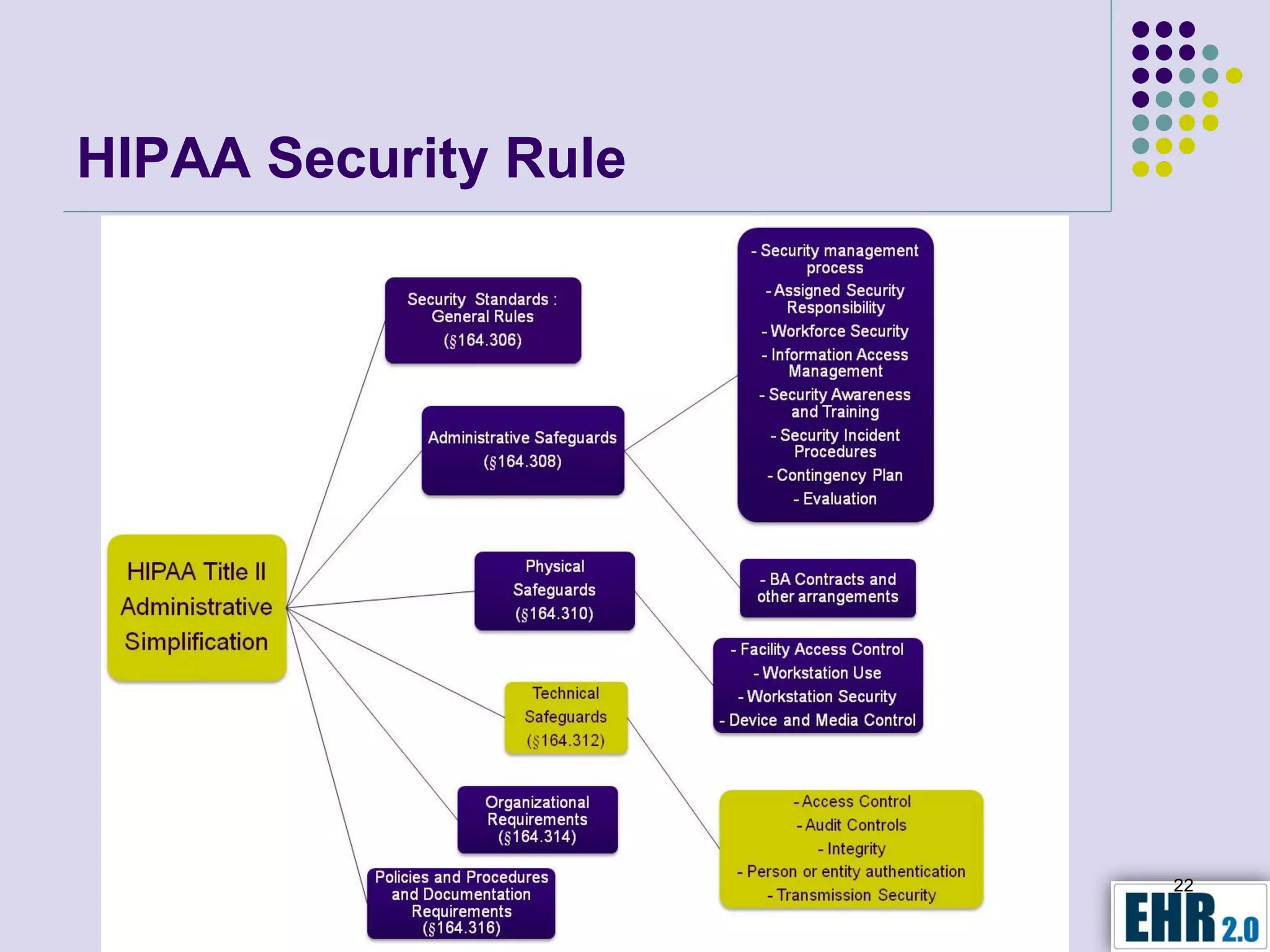
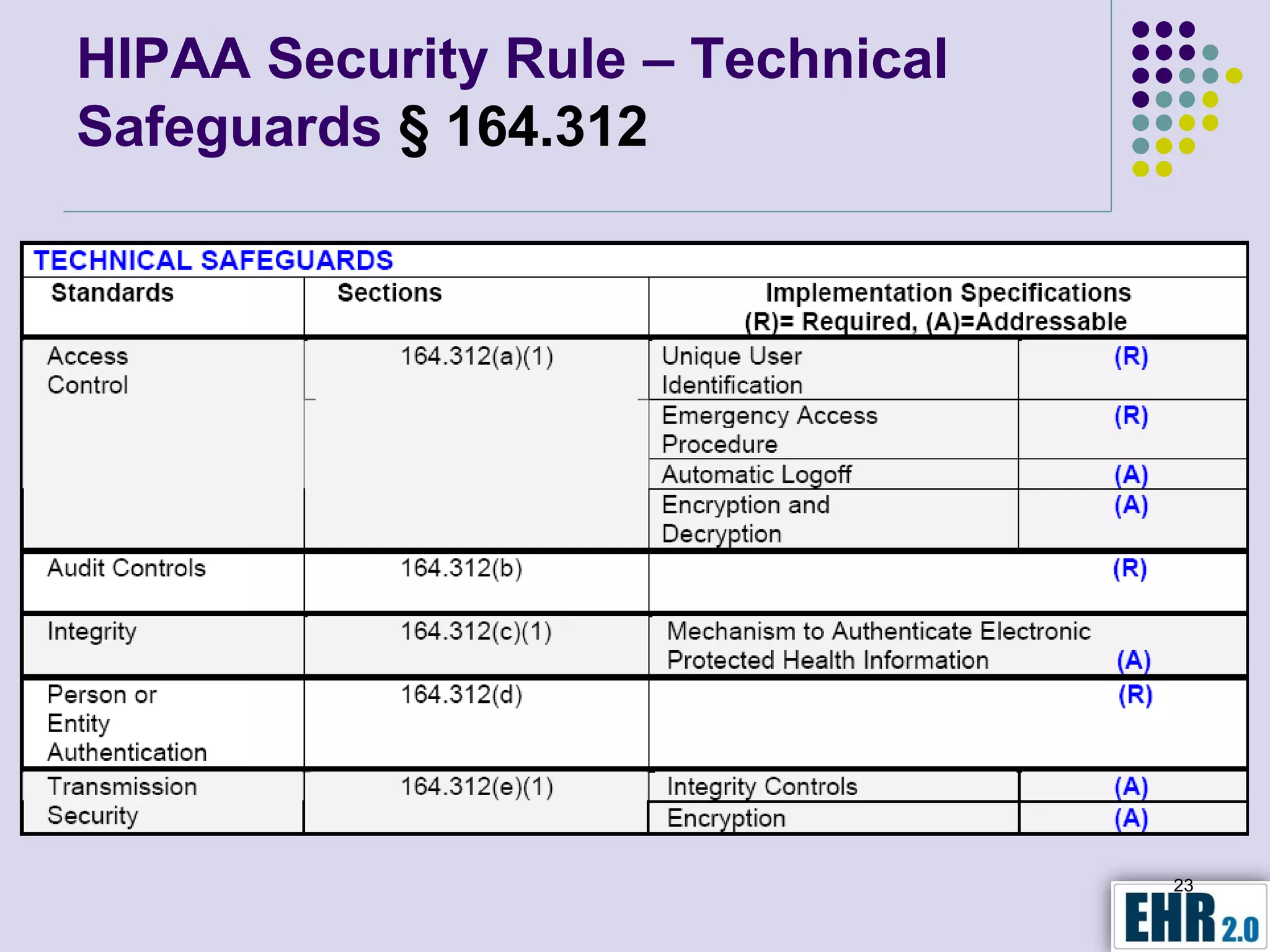
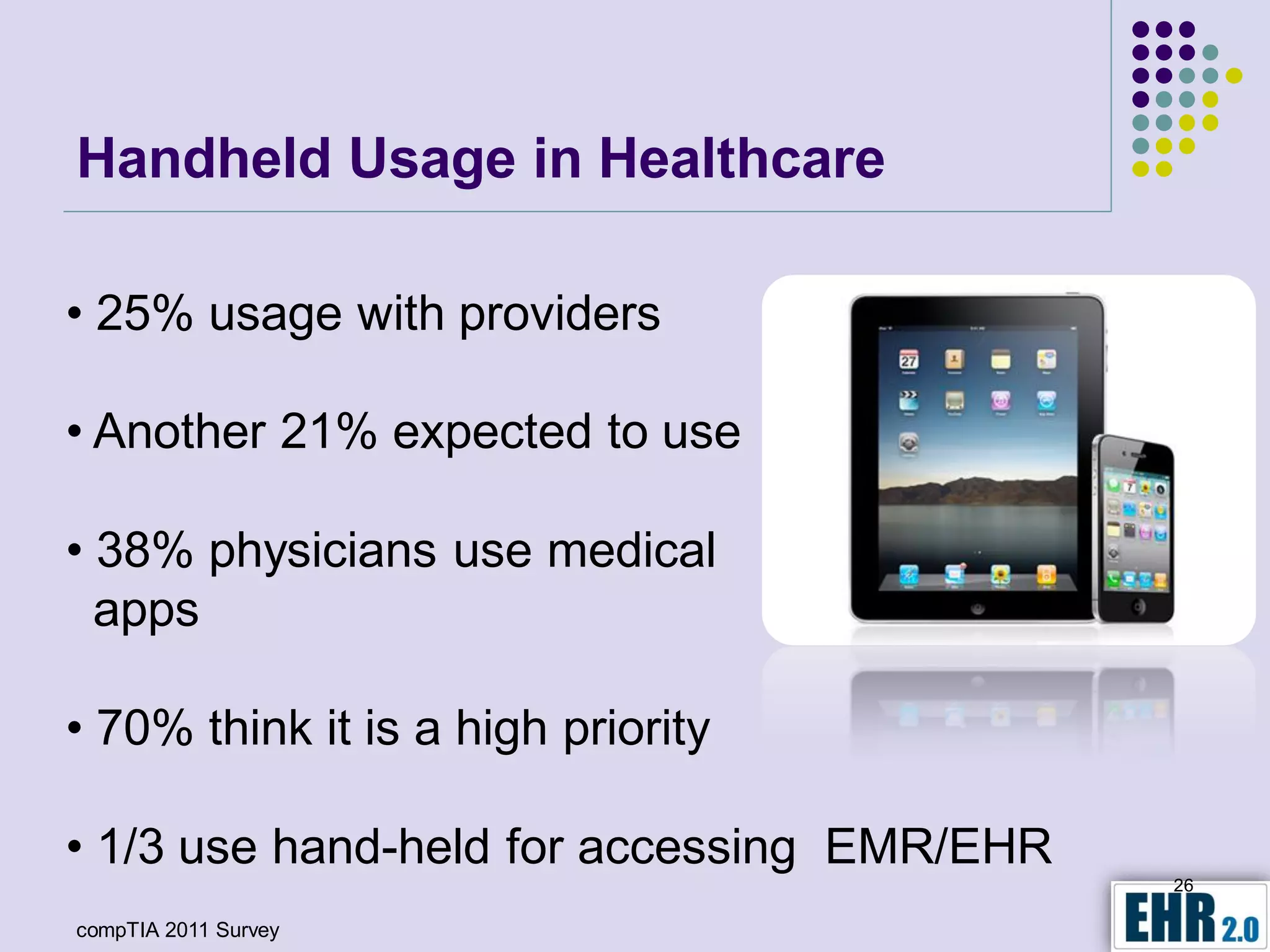
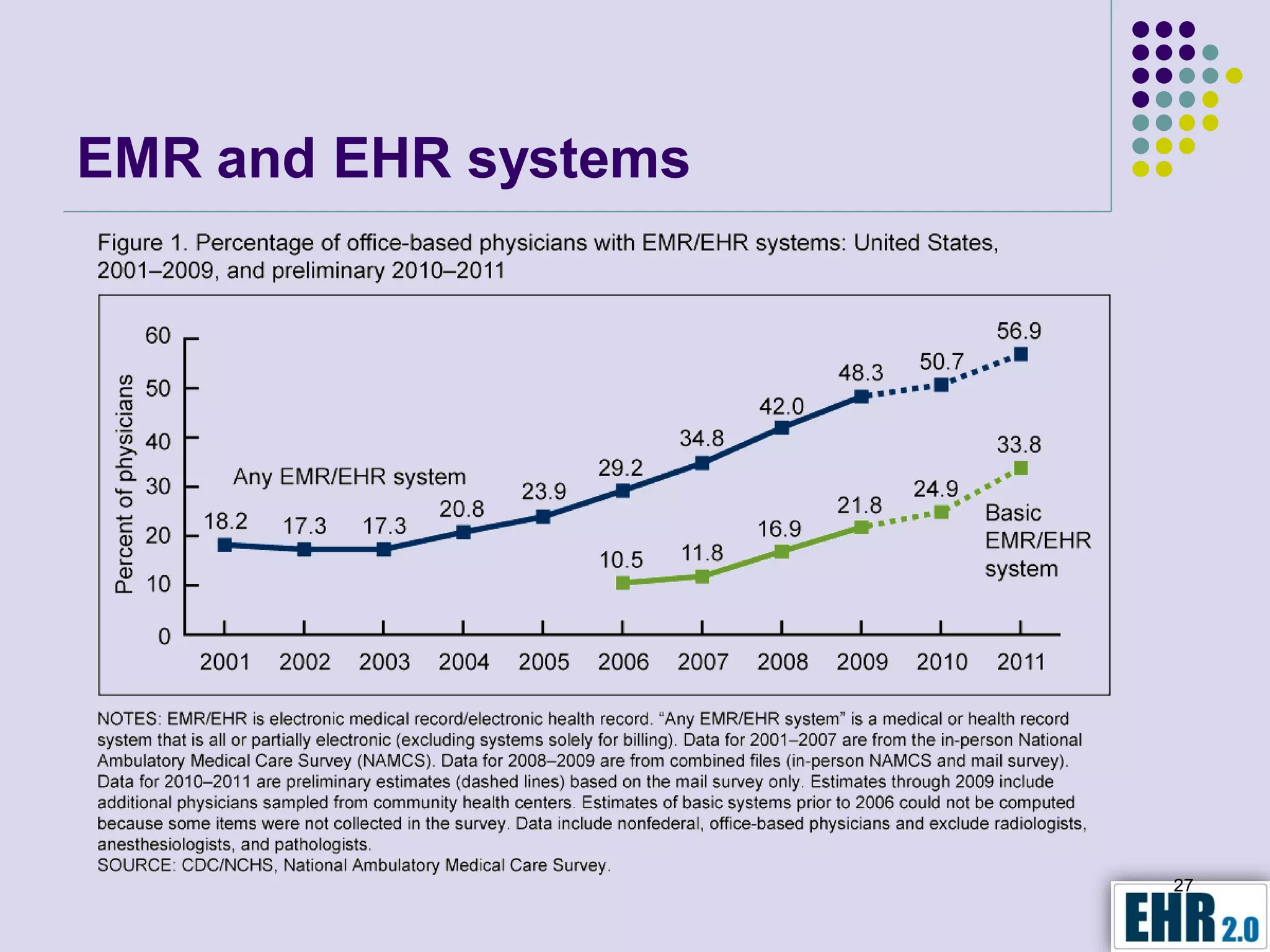
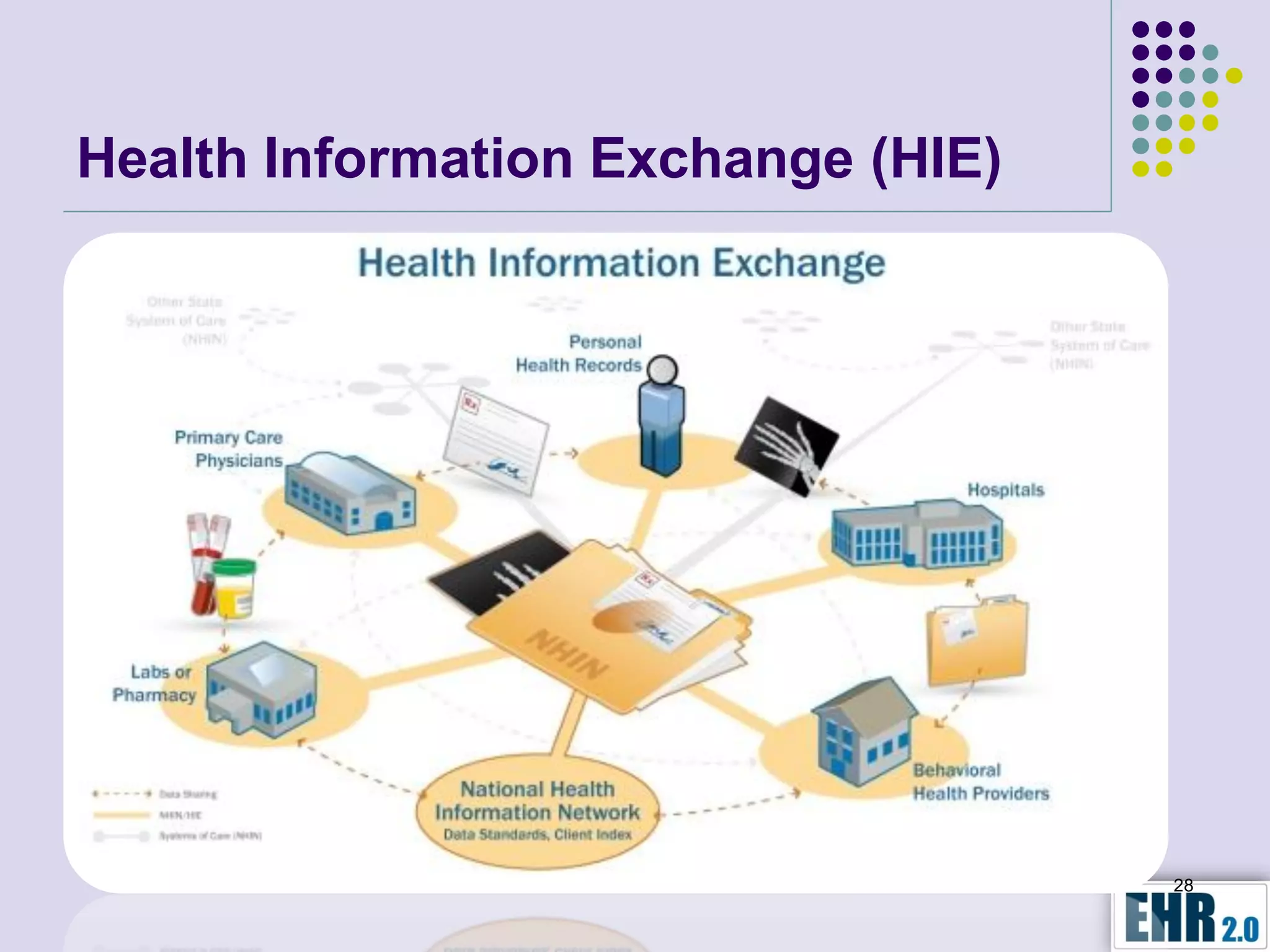
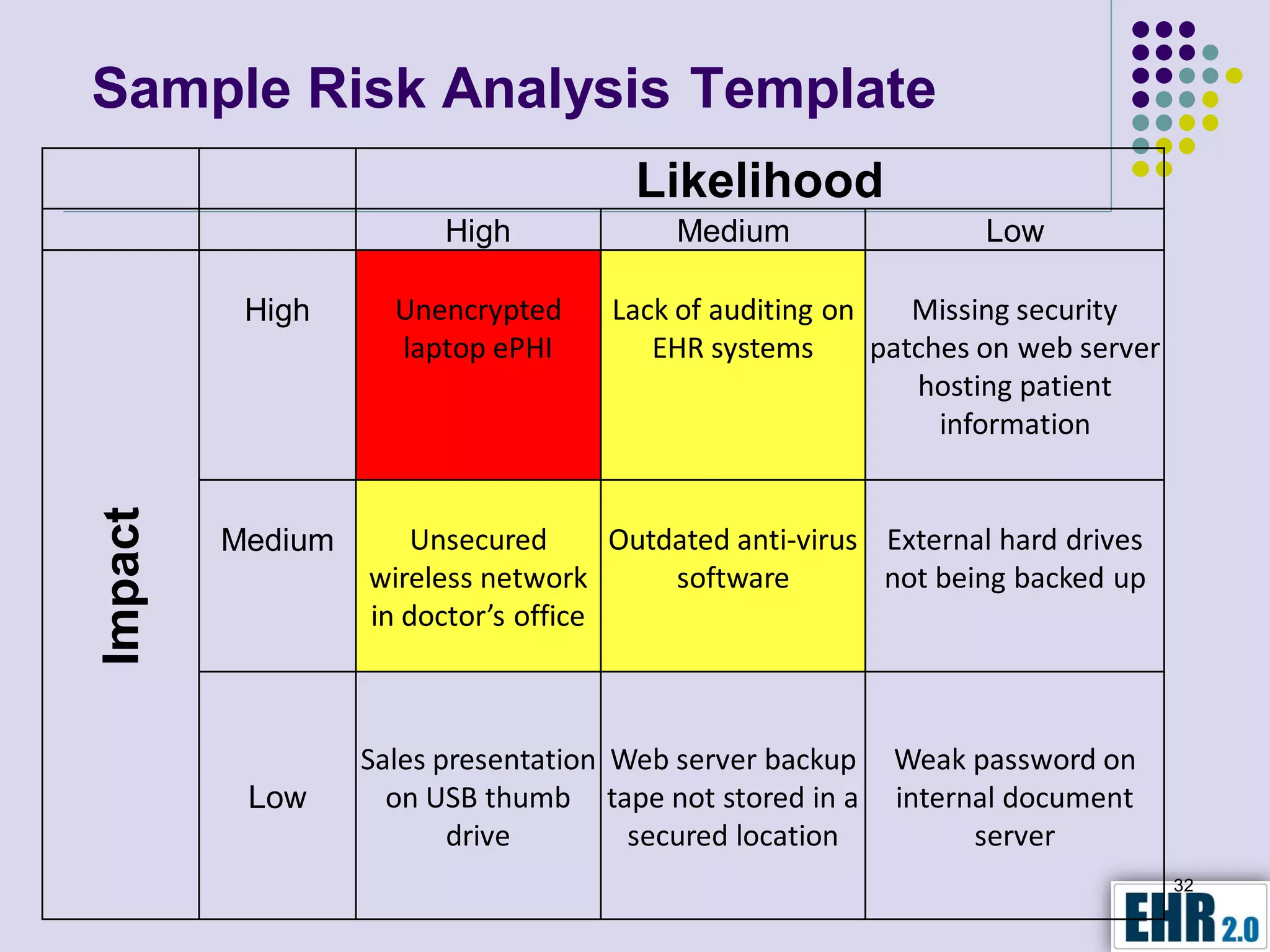
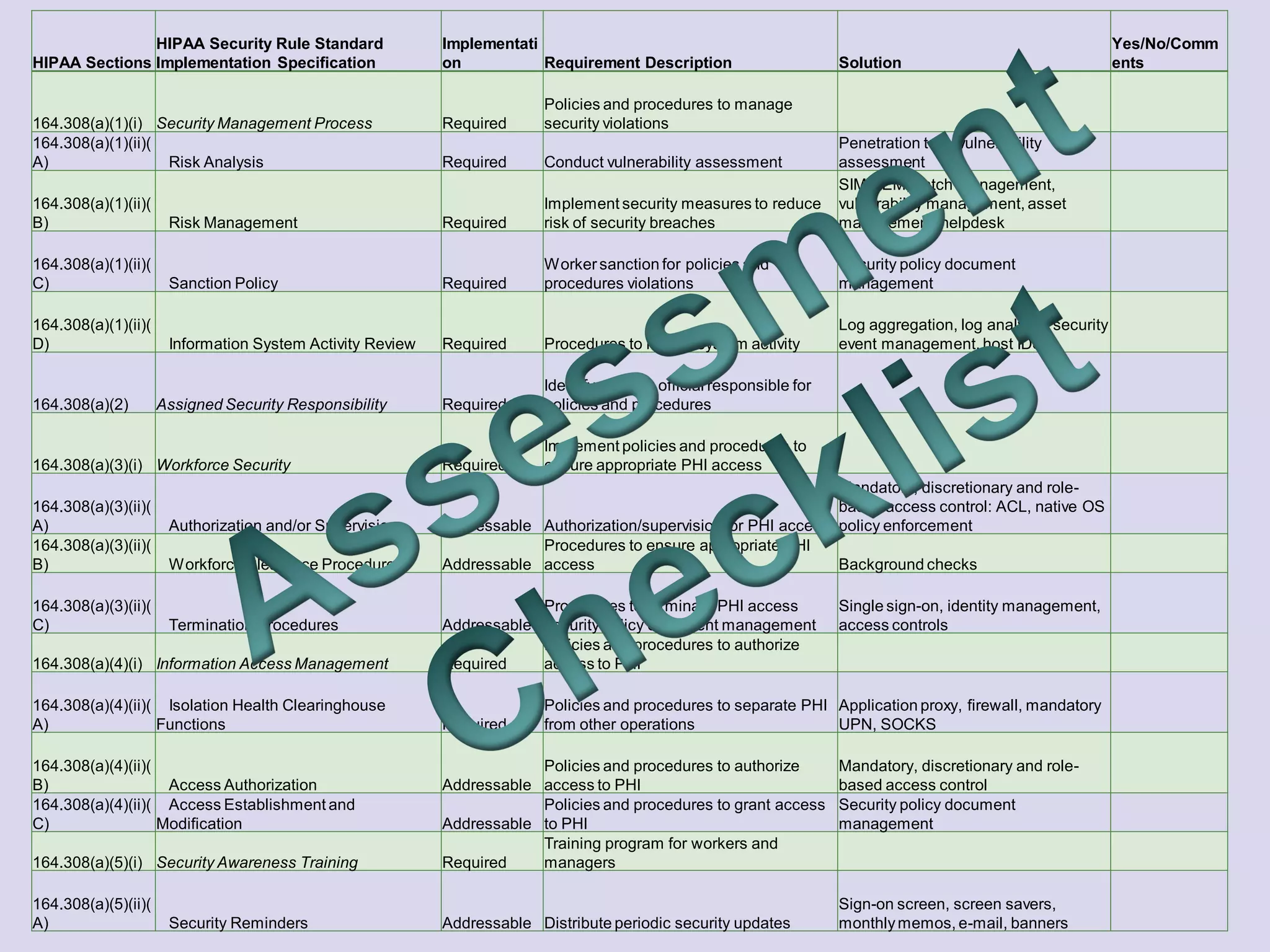
The document presents objectives for a HIPAA/HiTech security assessment webinar, aiming to educate healthcare organizations on compliance and security principles, safeguards, and assessment methodologies. It outlines key changes introduced by HiTech, such as stricter oversight and breach notifications, alongside essential HIPAA rules related to the protection of patient health information. Furthermore, the document emphasizes the importance of security standards and administrative, physical, and technical safeguards in maintaining the confidentiality and integrity of electronic protected health information.