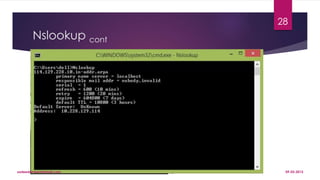
The document provides a comprehensive overview of network testing and debugging, covering TCP/IP concepts, configuration, and various troubleshooting methods. Key utilities for testing network connections such as ping, tracert/traceroute, ipconfig/ifconfig, and nslookup are discussed, along with different testing strategies like load, stress, and performance testing. It also emphasizes the importance of penetration testing for evaluating network security and includes basic tools for network troubleshooting.