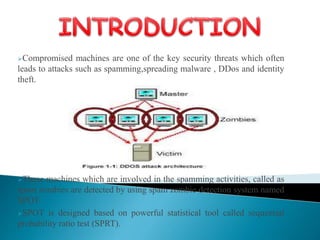
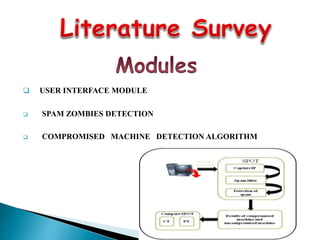
Compromised machines are often used to launch security attacks like spamming and distributing malware. This document describes SPOT, a system that detects these compromised machines, called spam zombies. SPOT uses sequential probability ratio testing (SPRT) to detect spam zombies in a network. It aims to identify compromised machines online and in real-time, with low false positive and false negative rates. The document outlines the hardware and software requirements for SPOT and provides diagrams illustrating the system design and components.






















![[1] Apache Spam Assassin project. http://spamassassin.apache.org/
[2] DBMS by McGraw-Hill International Edition
[3] F. Sanchez and Z. Duan, ” Understanding forgery properties of spam delivery
paths”, in Proceedings of 7th Annual Collaboration, Electronic Messaging, Anti-Abuse
and Spam Conference (CEAS), Redmond, WA, July 2010.
[4] Java by Cengage Learning
[5]Know your enemy: Tracking Botnets. http://www.honeynet.org/papers/bots.
[6]N. Ianelli and A. Hackworth “Botnets as a Vehicle for Online Crime” in Proc. of
First International Conference on Forensic Computer Science, 2006.
[7] Sequential Methods in Statistics. Chapman and Hall, 1986.
[8] Sequential Analysis. John Wiley & Sons, Inc, 1947
[9] Software Engineering by Precise Approach
[10] Software Testing Modeling by Boris Bezier
[11]UML: OOAD CONCEPTS- Gradybooch](https://image.slidesharecdn.com/0ca01142-b212-4310-8e57-2a424f684146-160401071135/85/spamzombieppt-26-320.jpg)
