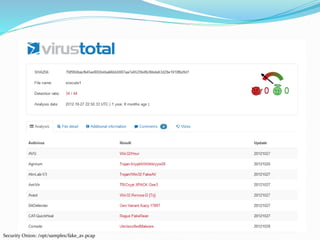
This document provides information about a presentation on network packet analysis and file carving techniques. The presenter is introduced as a security researcher and systems administrator with experience in networking and security consulting. An overview of the presentation outlines the assumed knowledge, tools that will be used including Wireshark and Network Miner, and the methodology of pattern matching, identifying conversations, exporting data, and drawing conclusions. Additional resources on sample packet captures and further reading are also referenced.