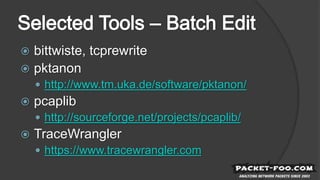
The document discusses the complexities of packet capture (pcap) and the challenges faced by network and security analysts in editing packets while removing sensitive information. It emphasizes the need for a balance between sanitizing data and preserving its usefulness for analysis, mentioning various tools for packet manipulation. Key issues include protocol dependencies, payload fragmentation, and the intricacies of modifying IP addresses and fully qualified domain names (FQDNs).