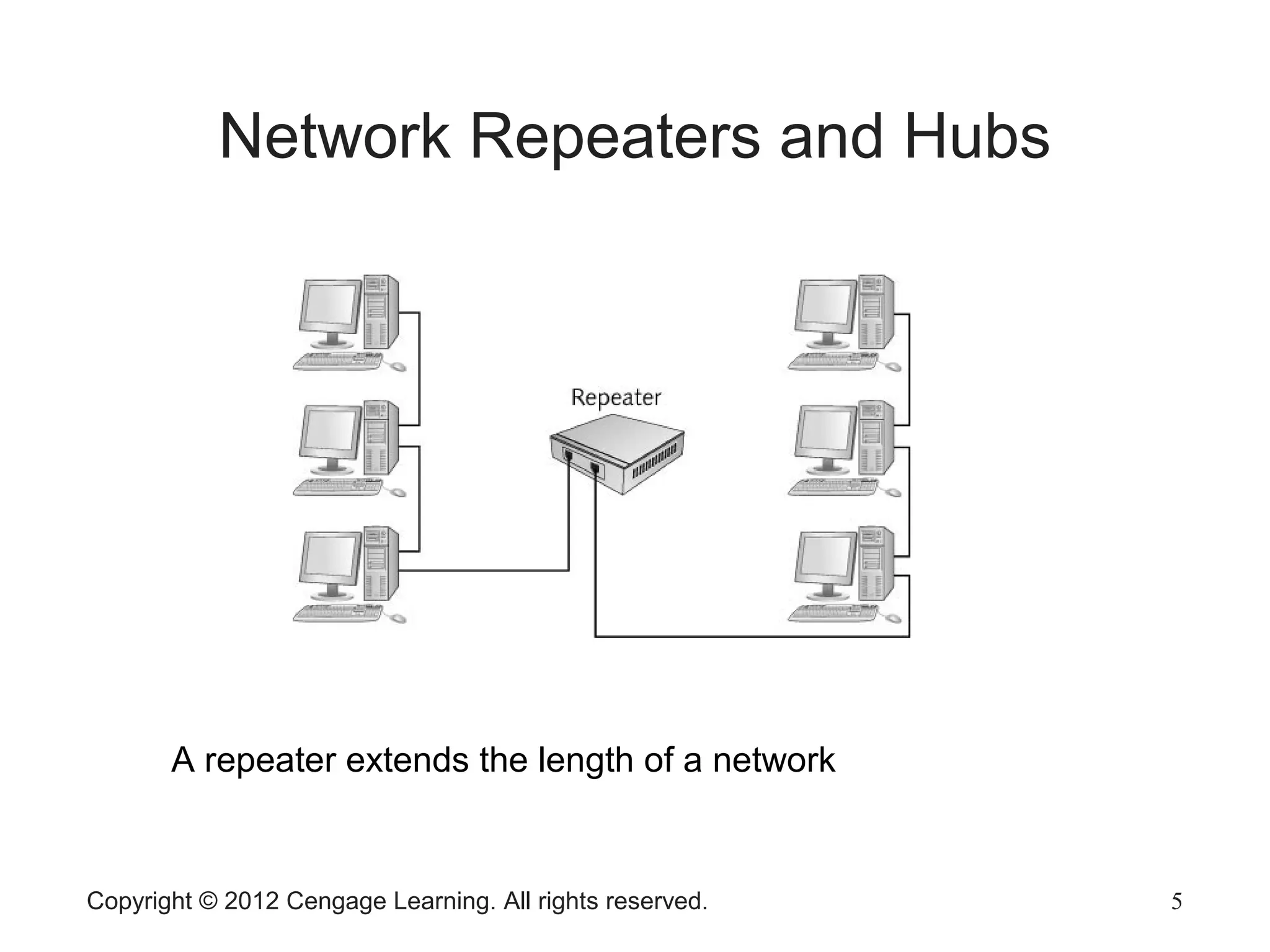
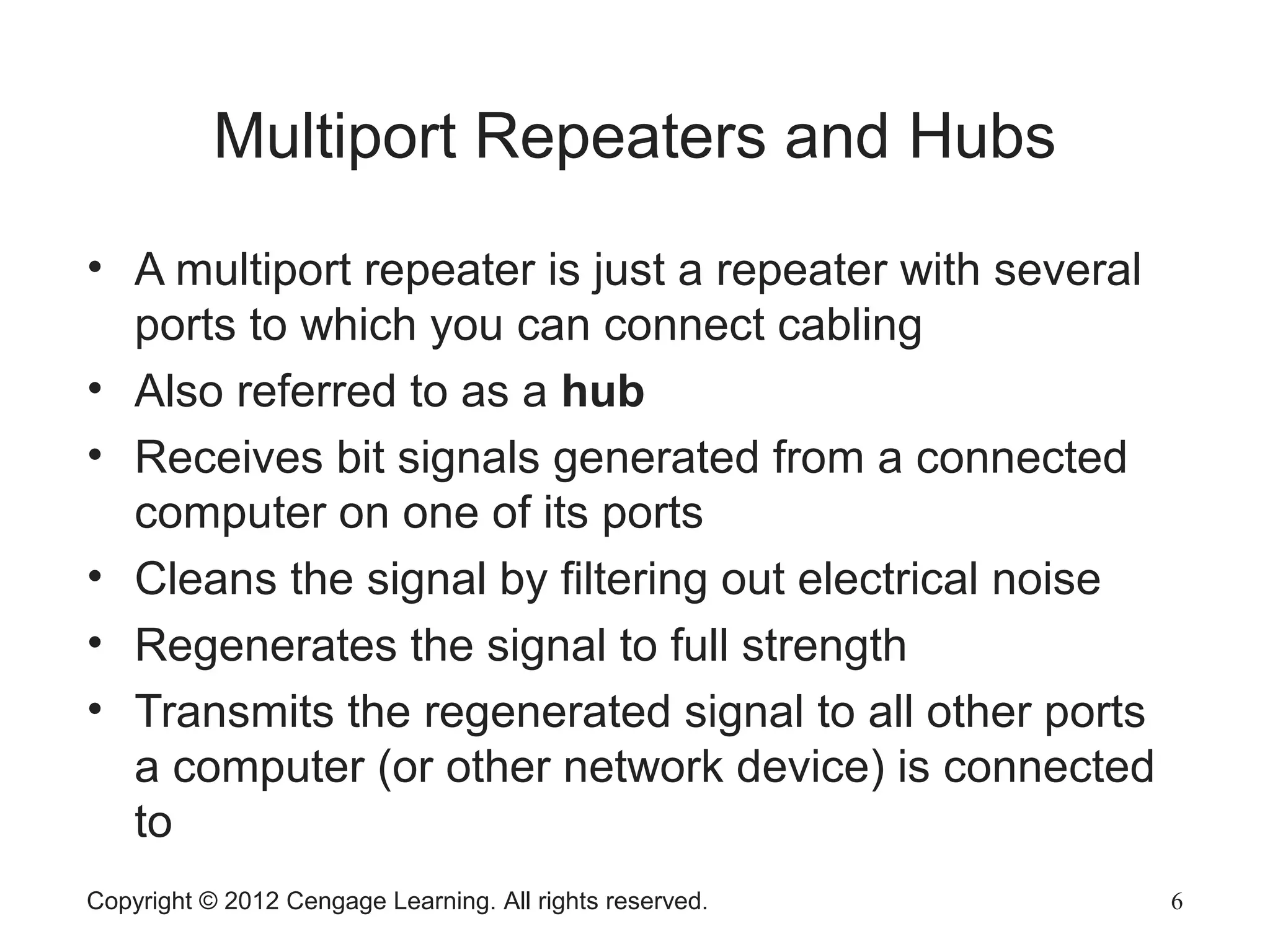
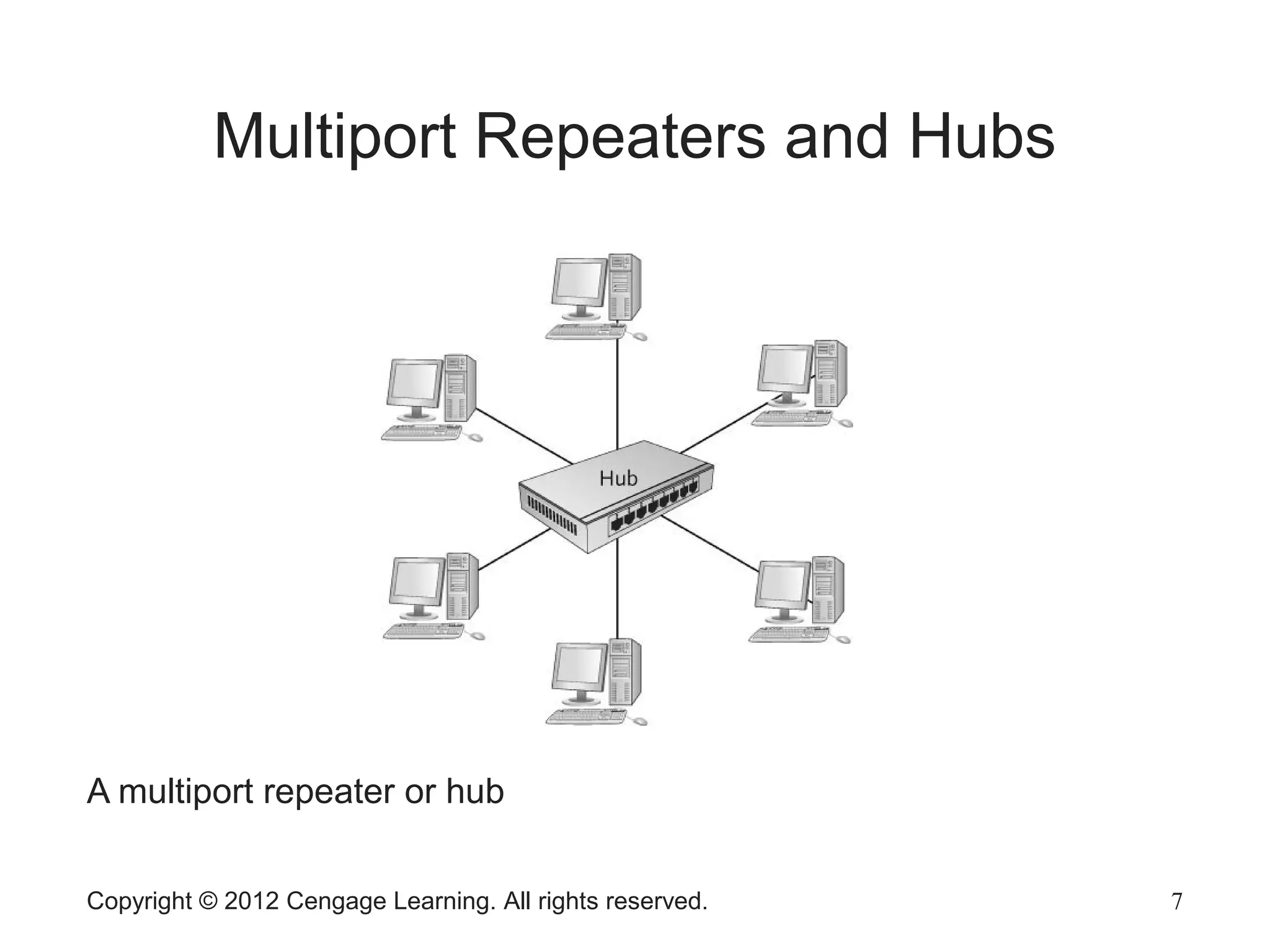
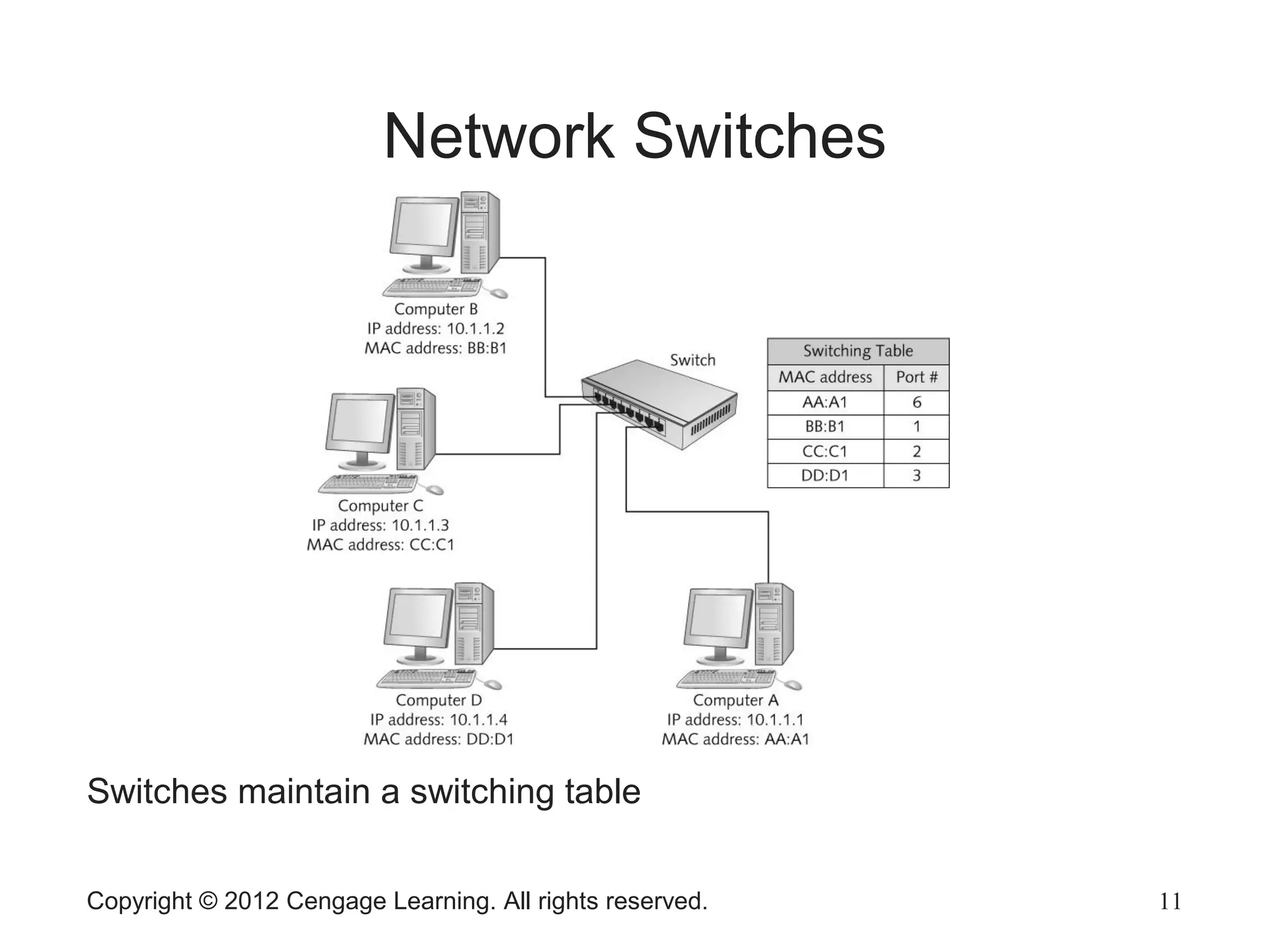
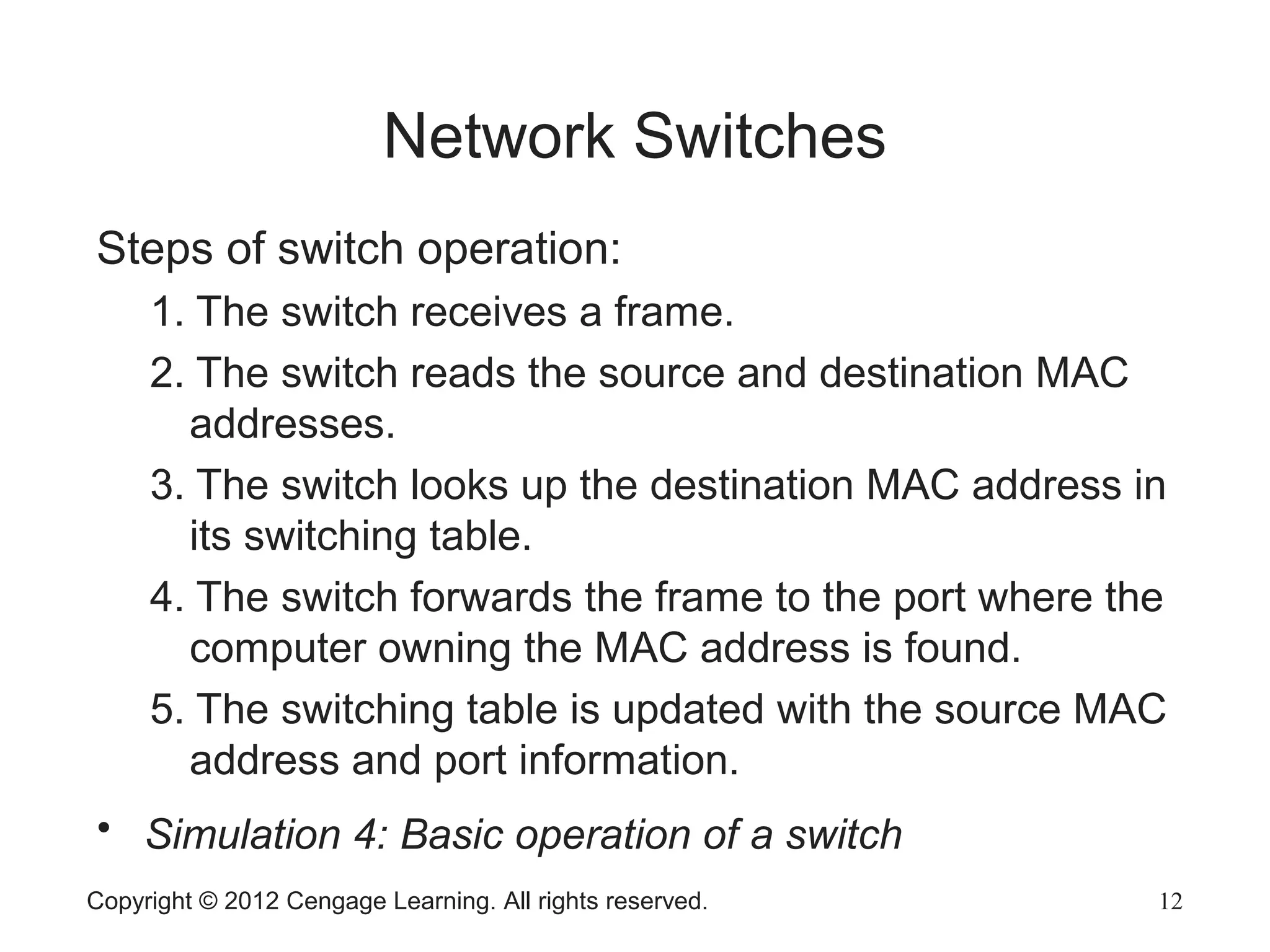
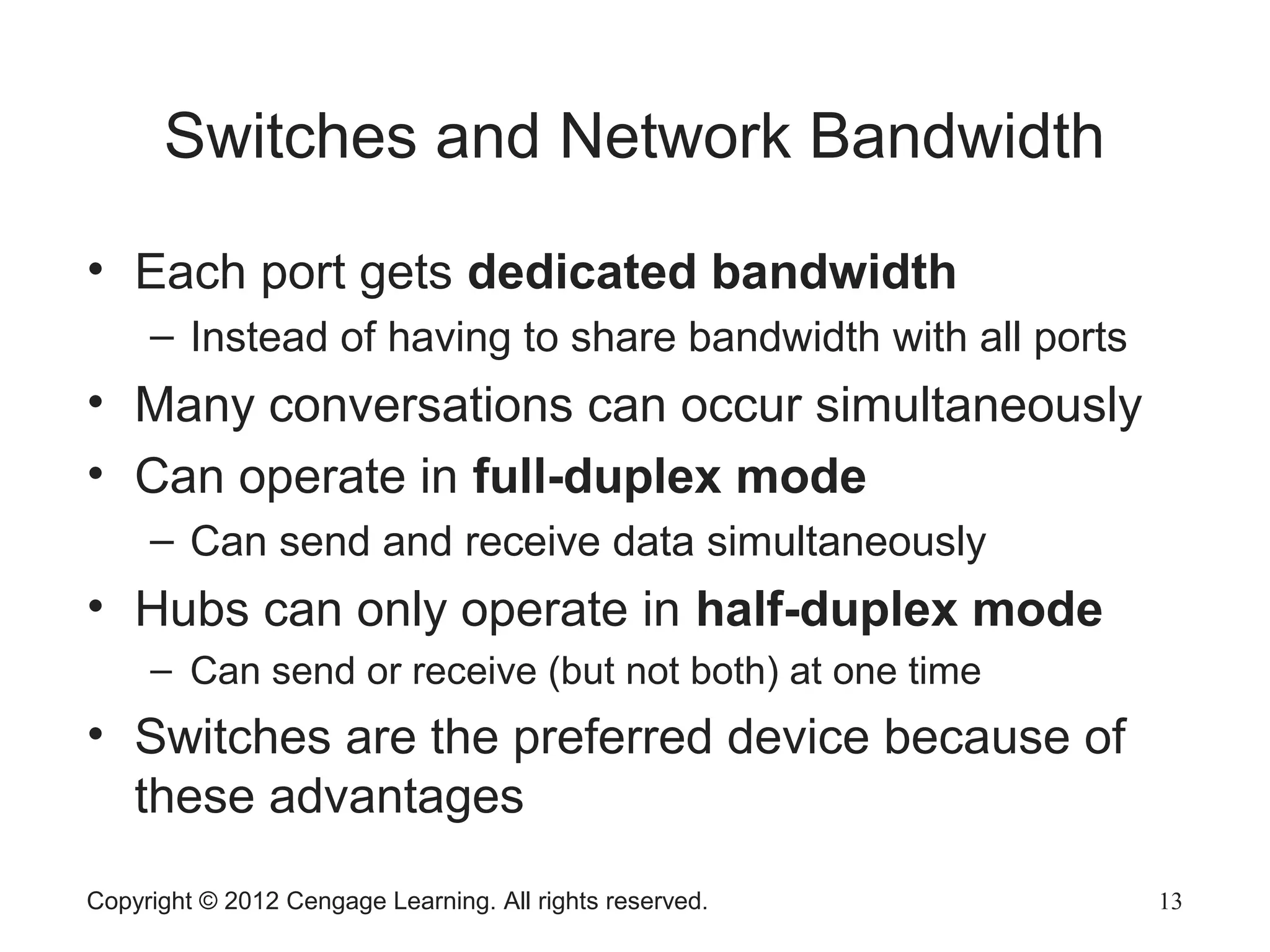
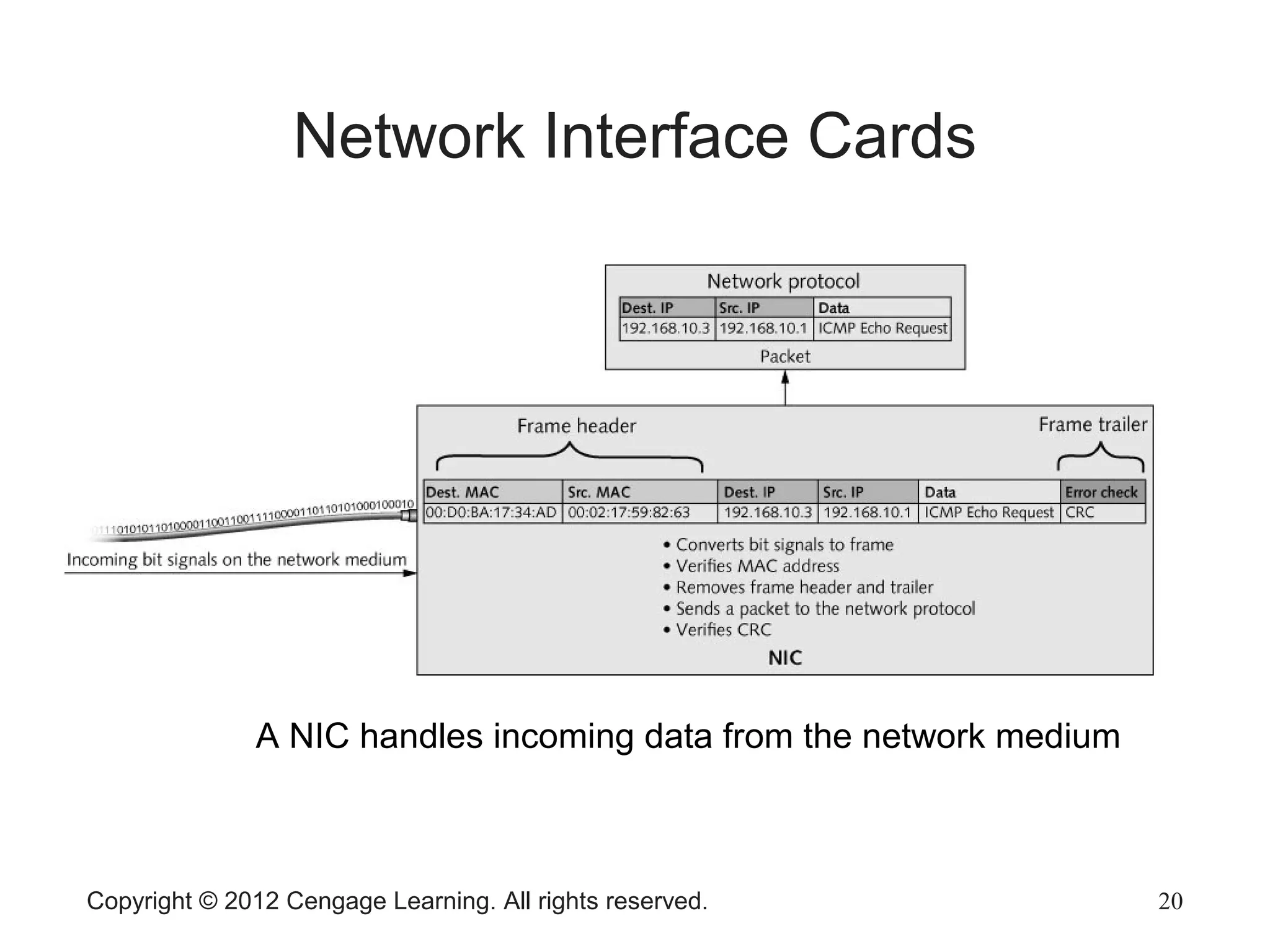
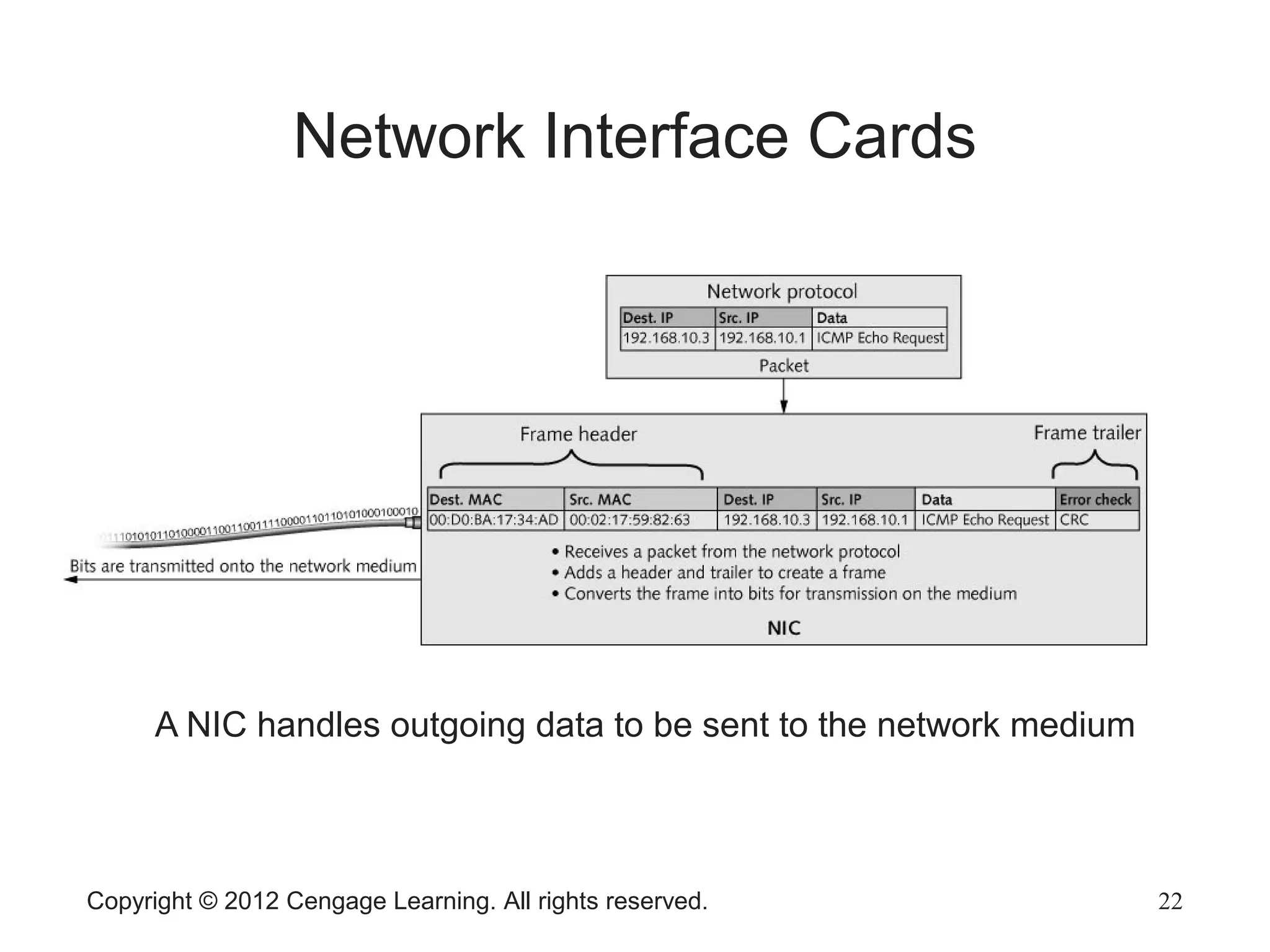
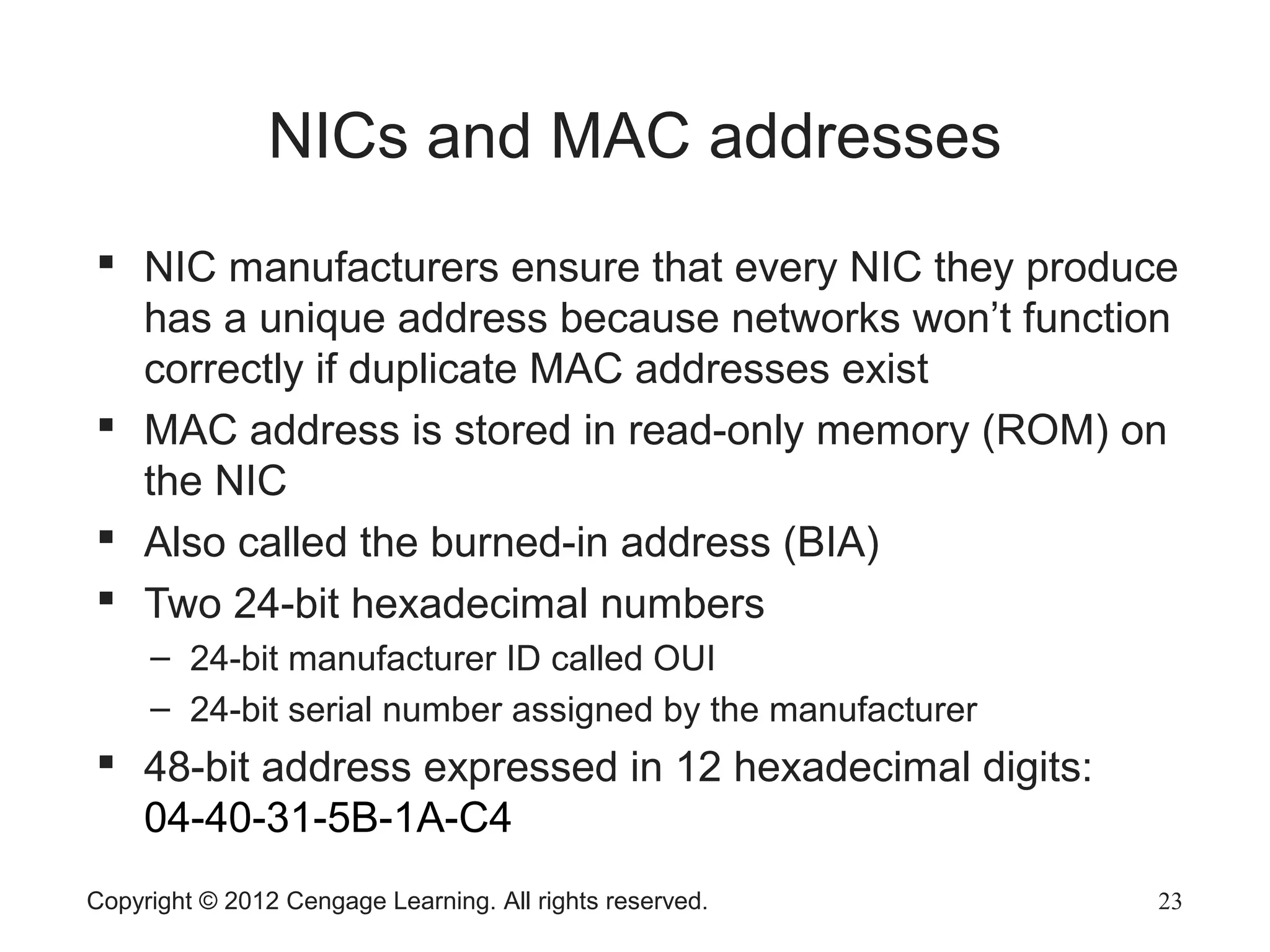
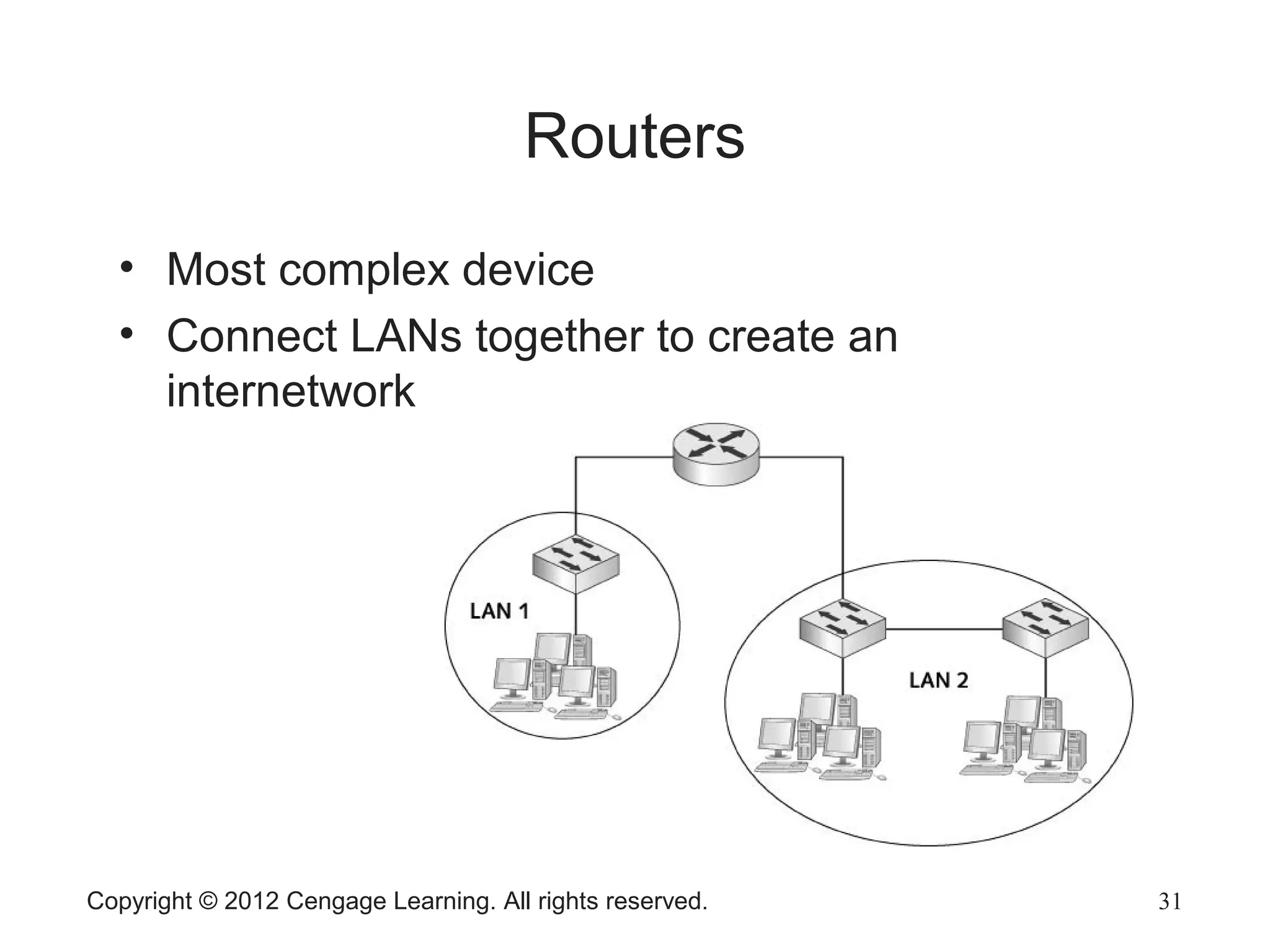
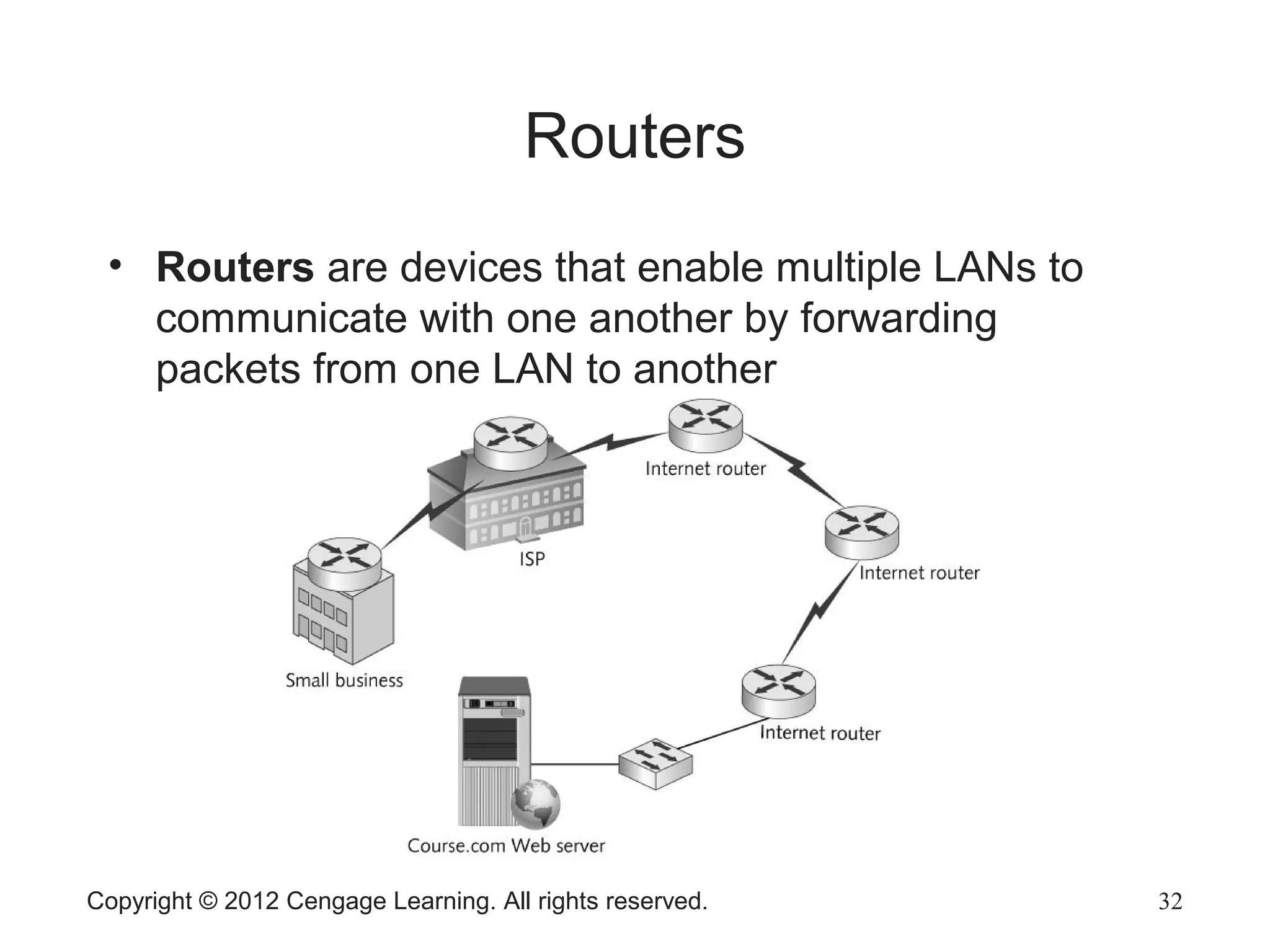
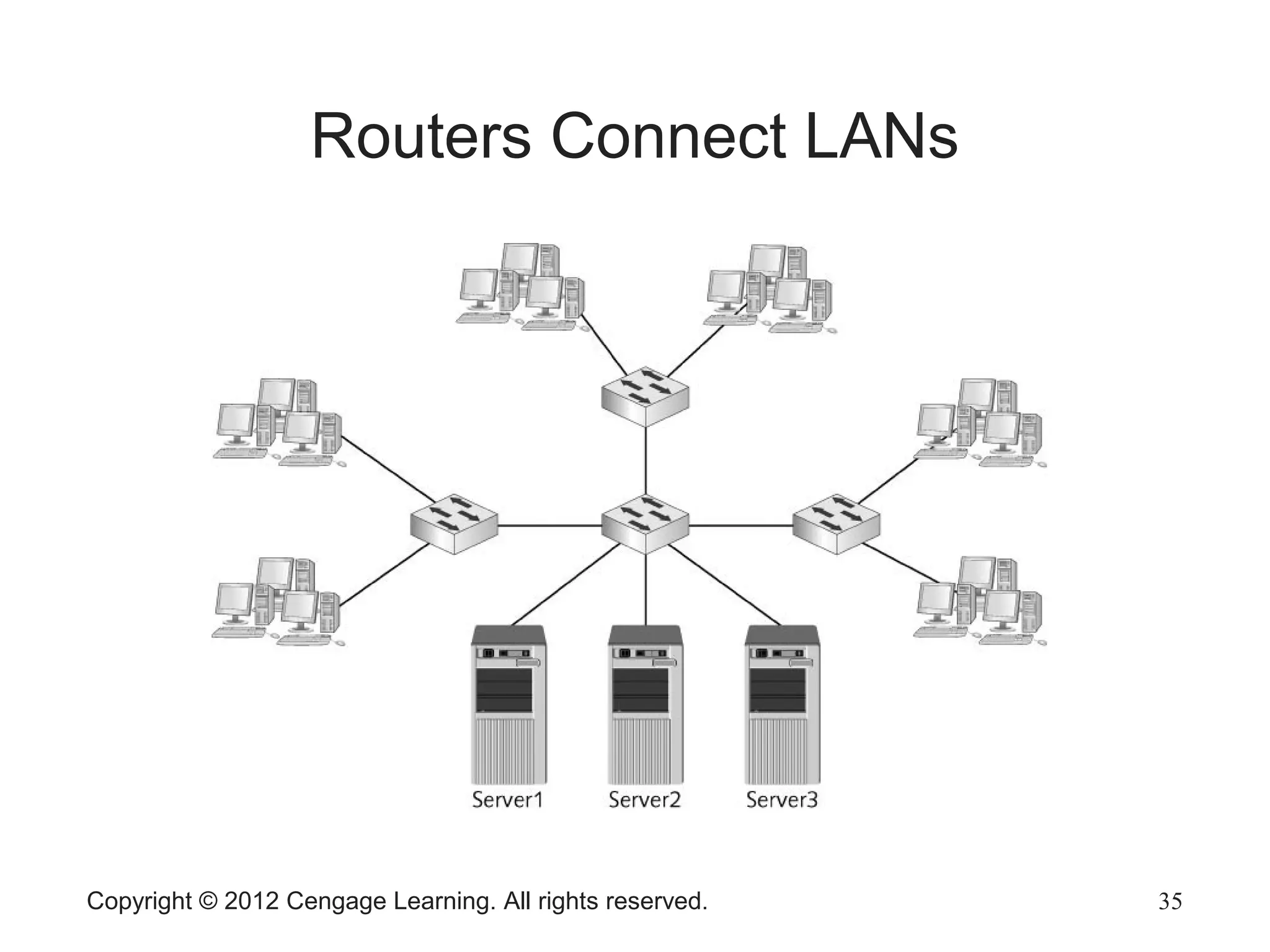
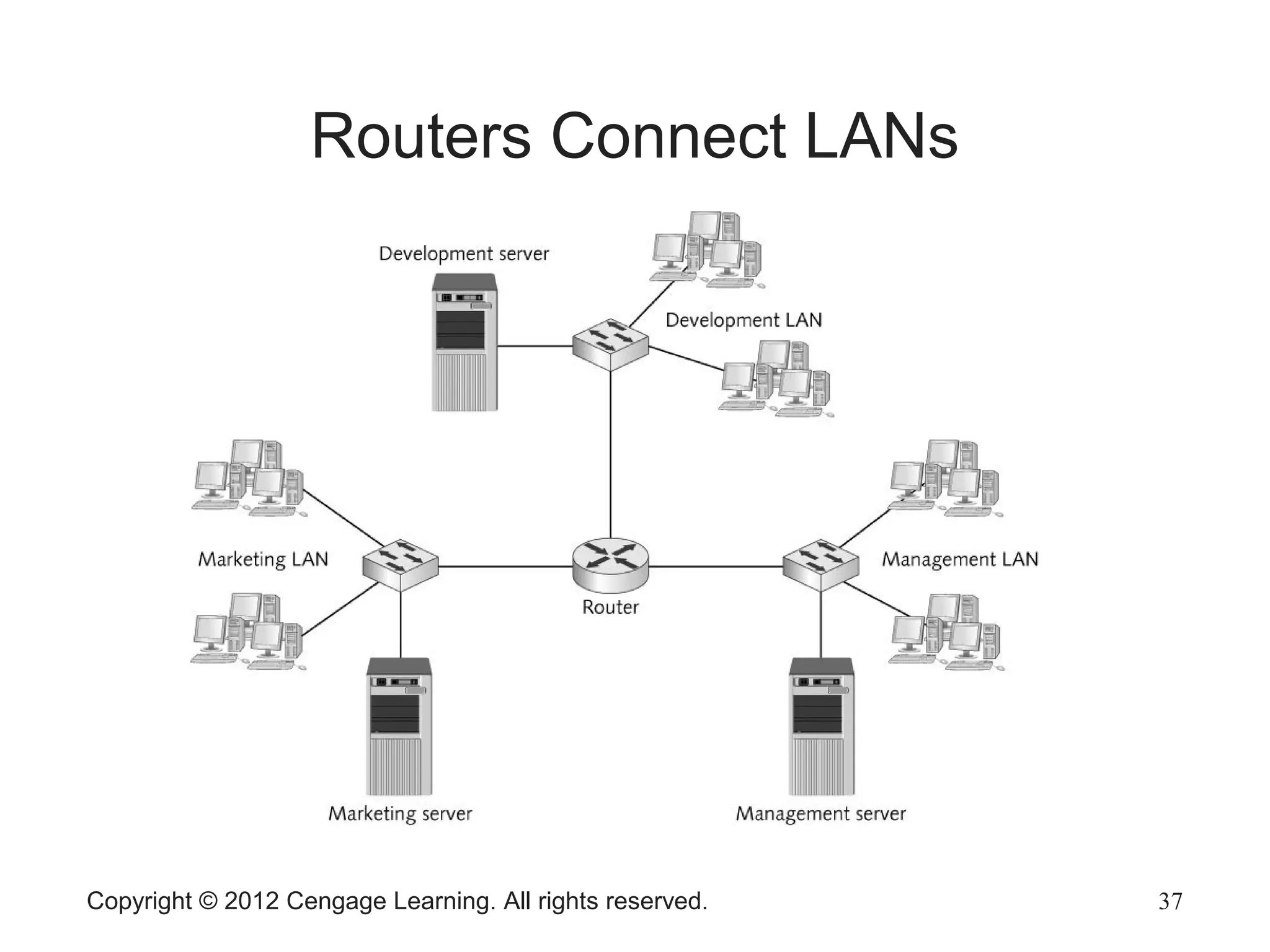
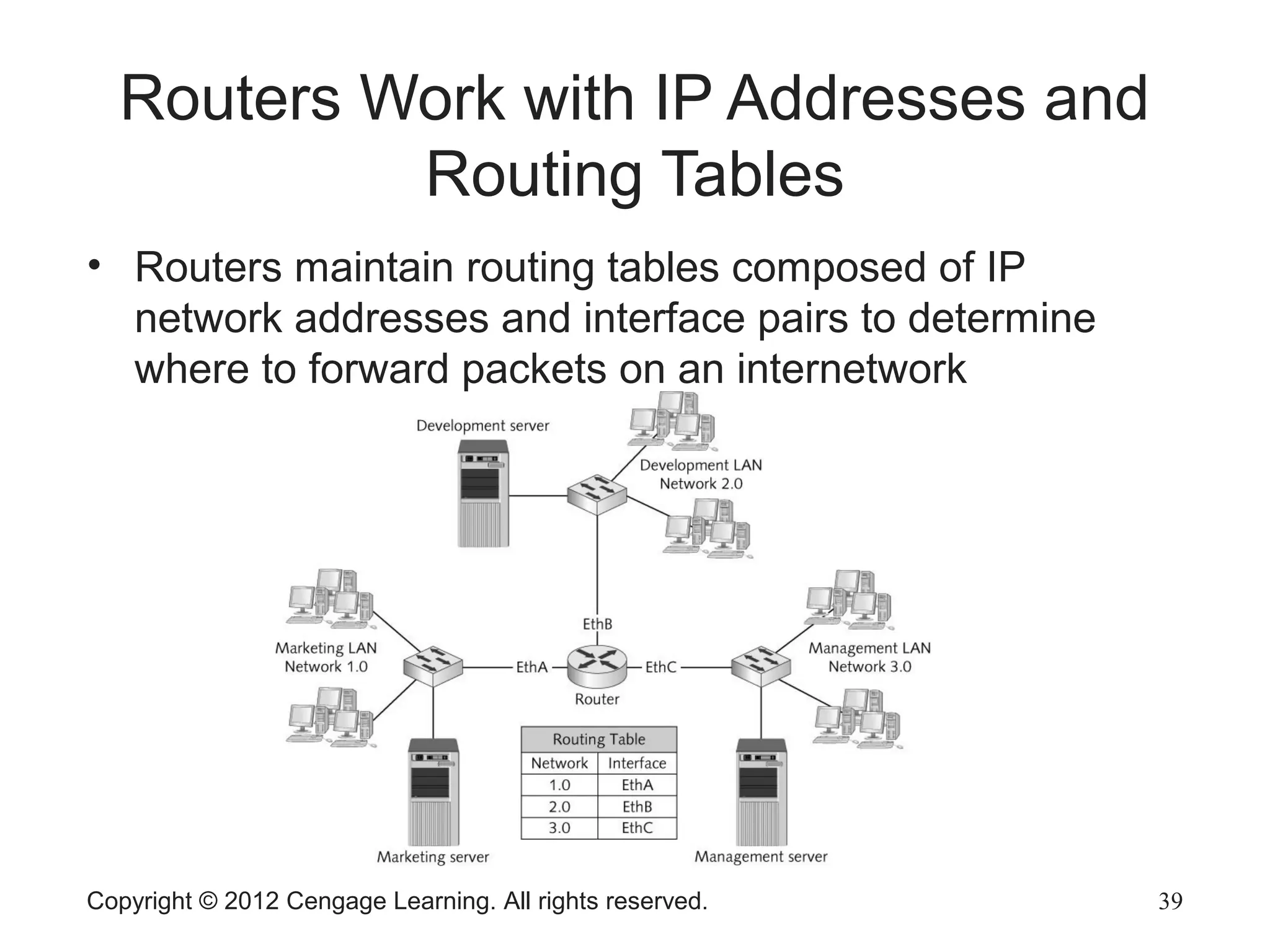
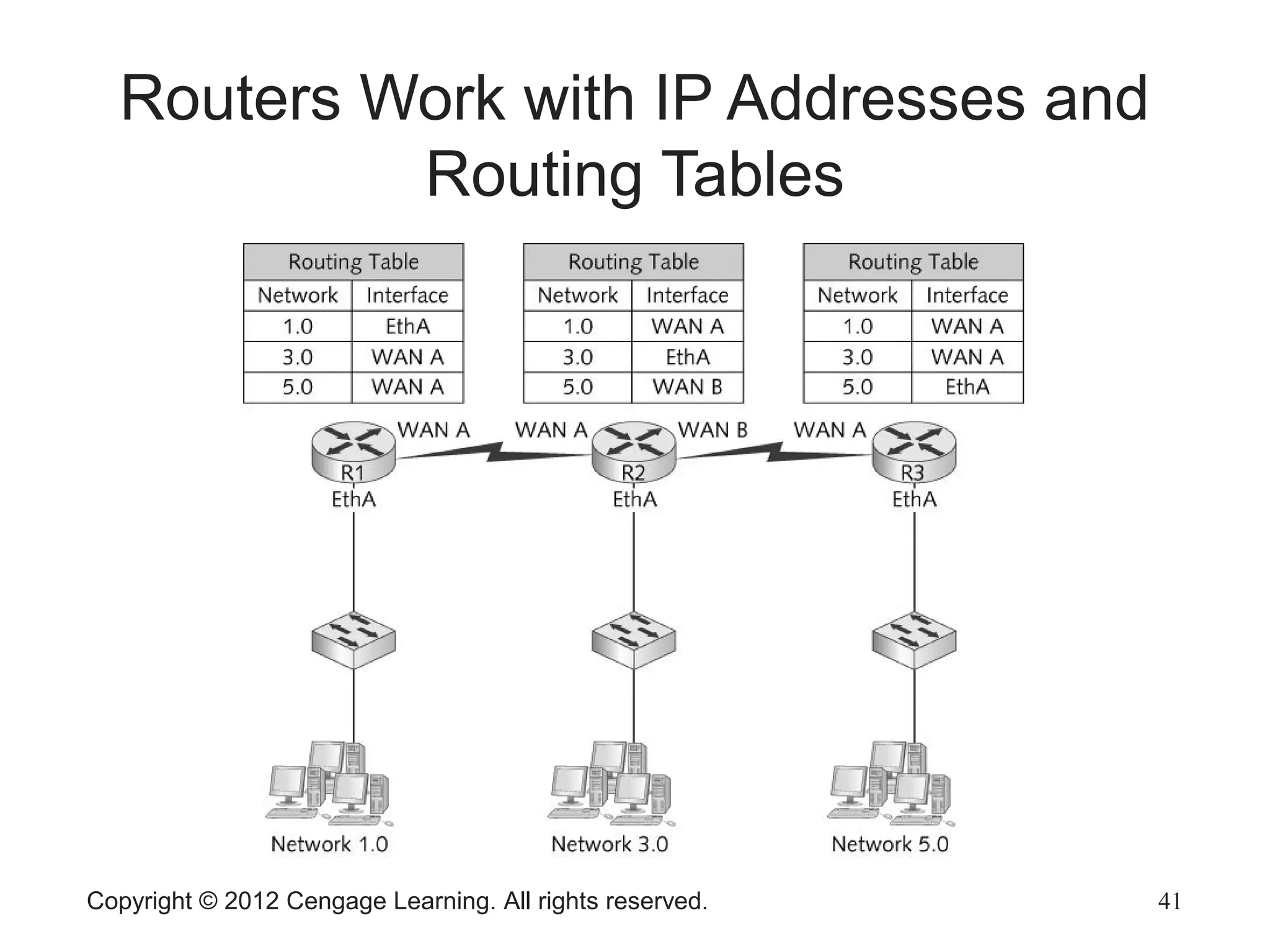
The document describes various network hardware components. It explains that repeaters and hubs receive and retransmit signals to extend network reach, while switches determine destination ports by reading addresses. Wireless access points function similarly to hubs to connect wireless devices. Network interface cards mediate the connection between computers and networks by assembling and transmitting signals. Routers connect local area networks and forward packets between networks using IP addresses and routing tables.