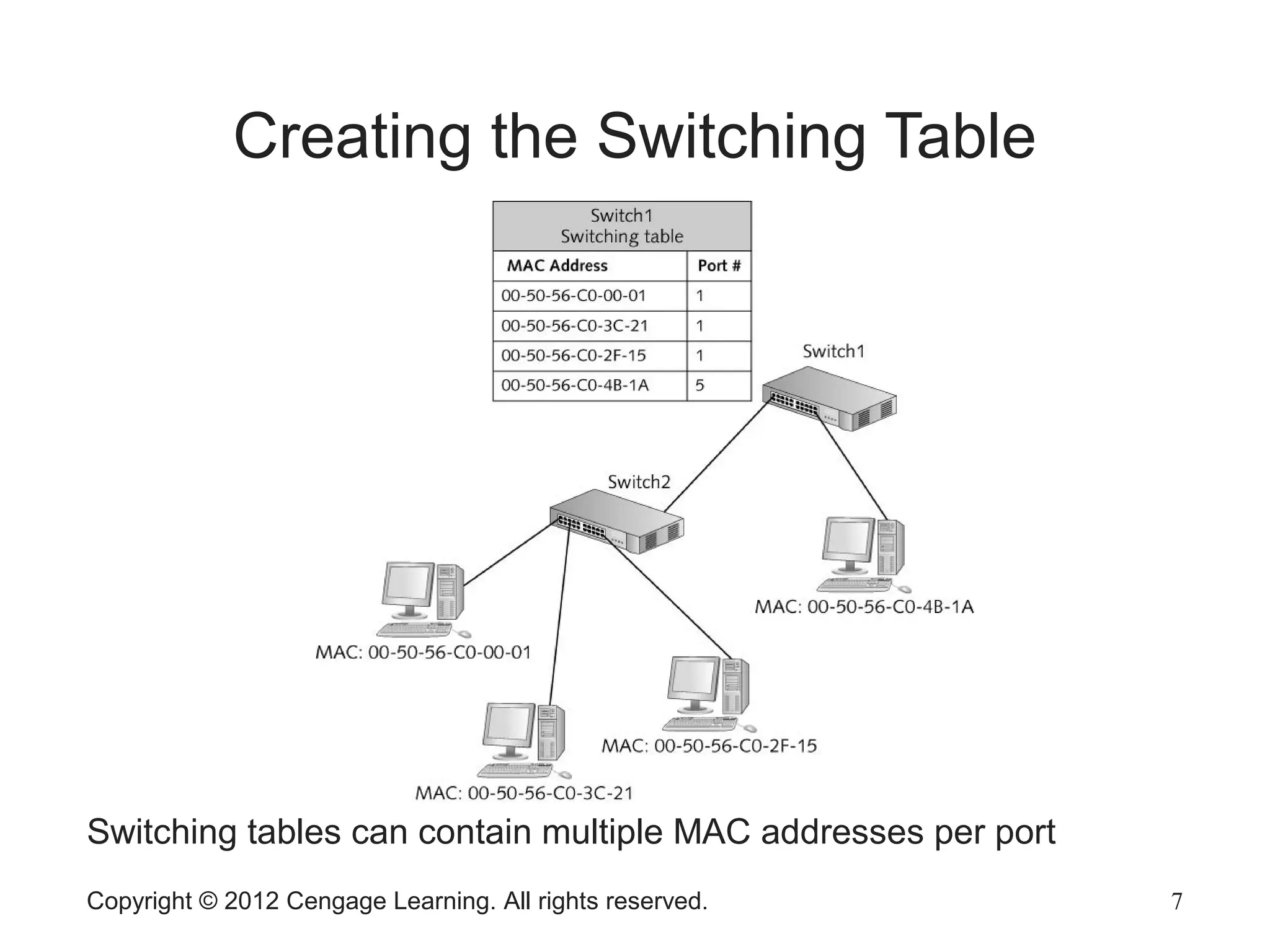
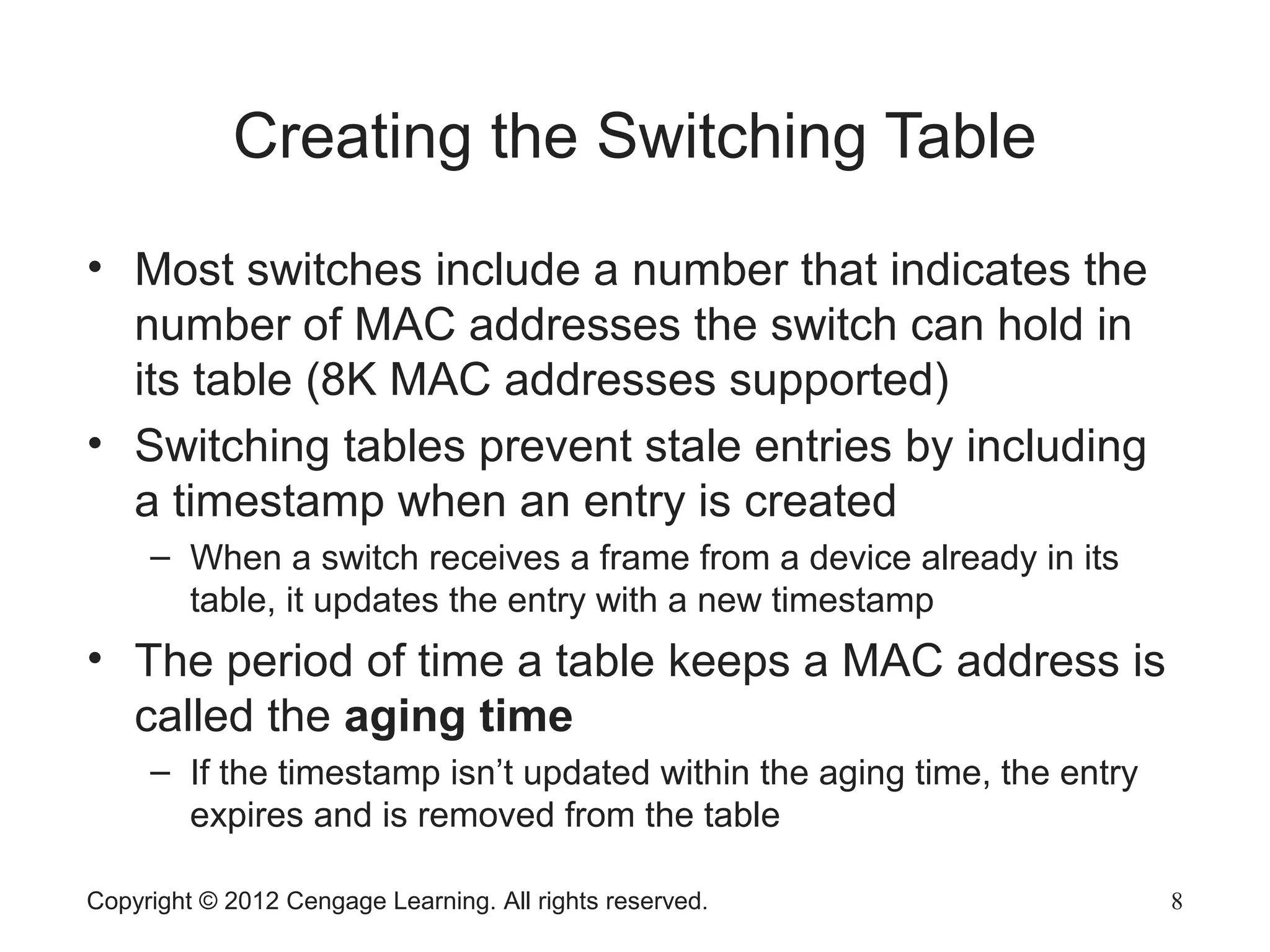
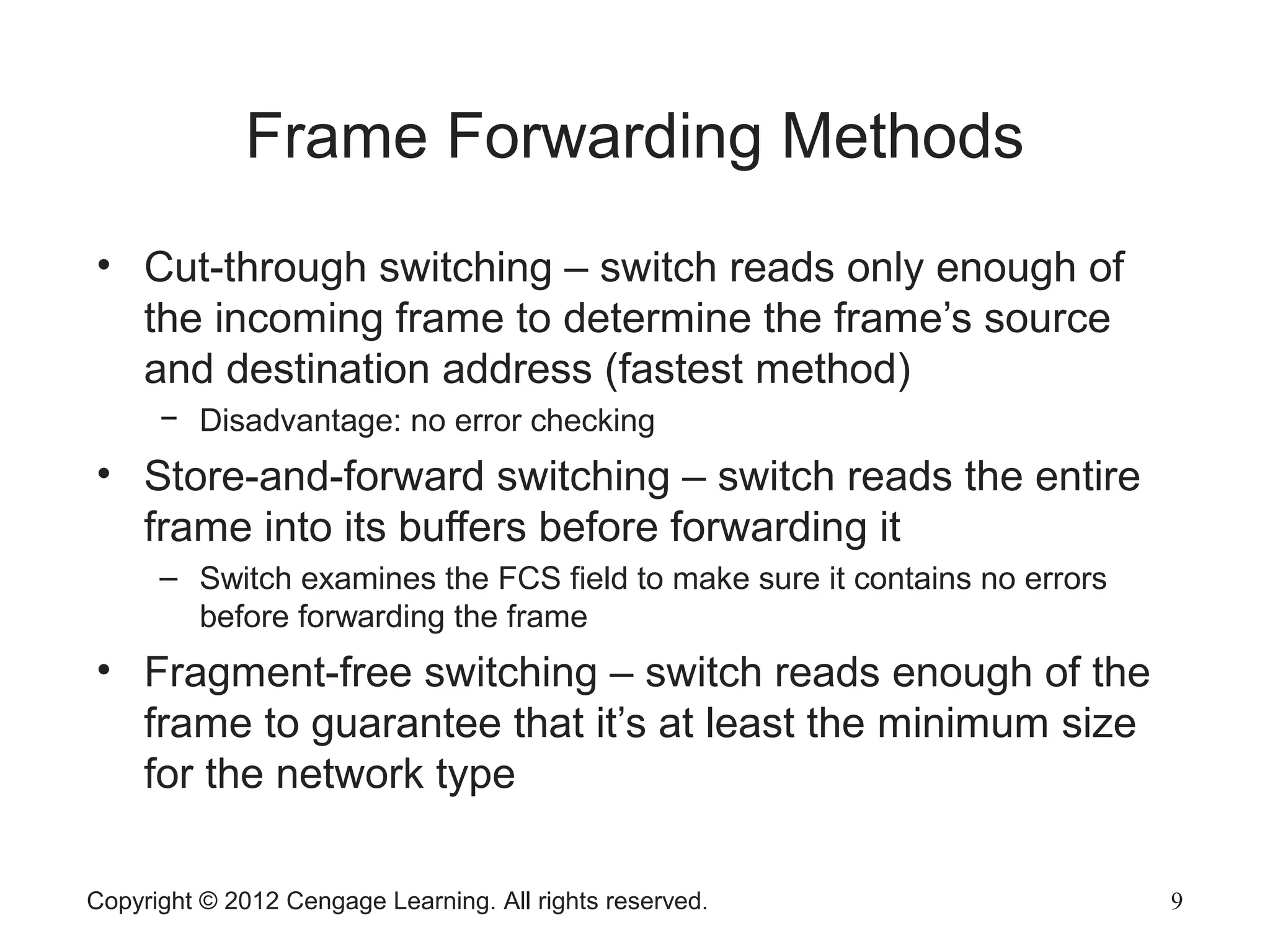
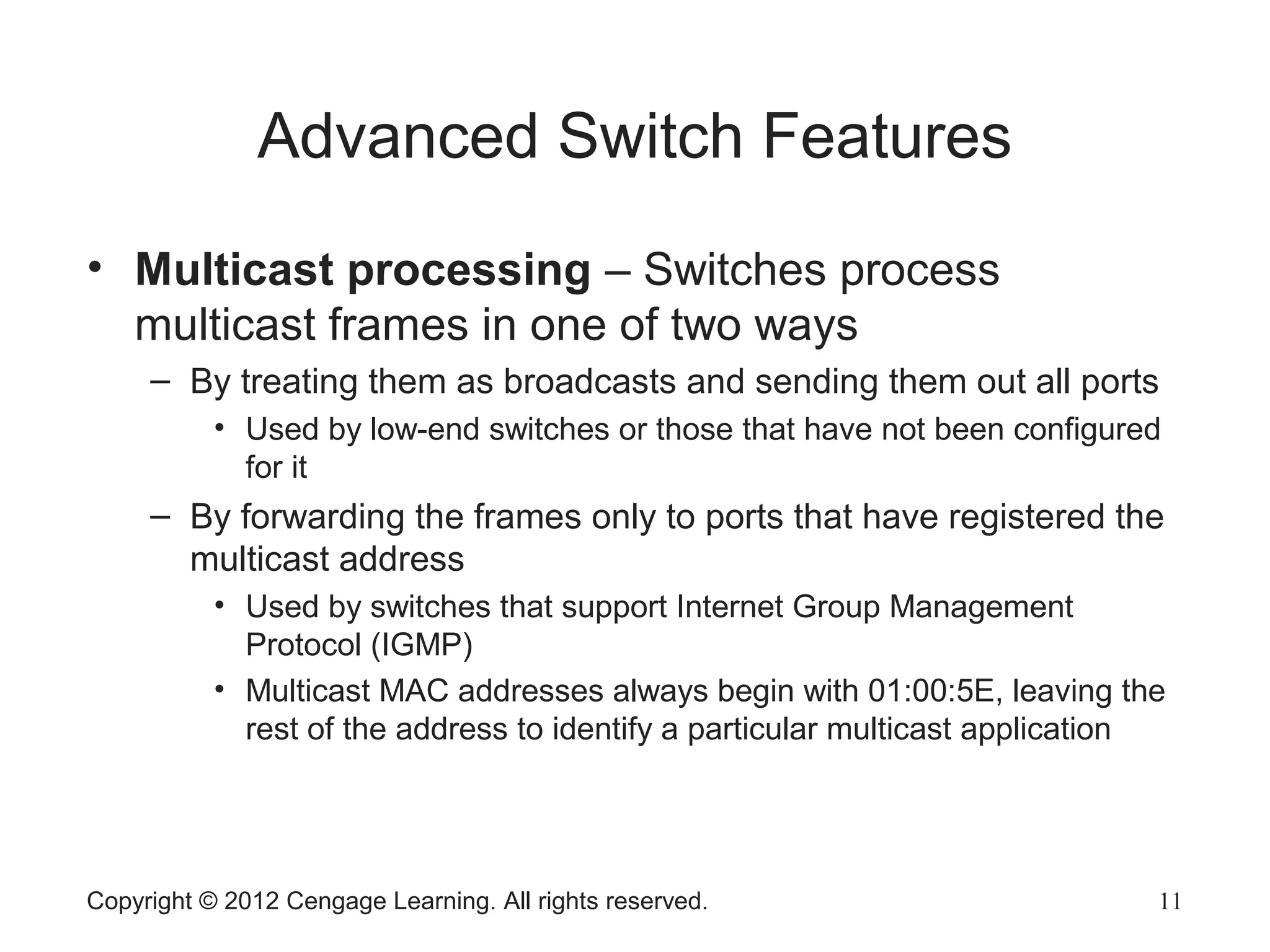
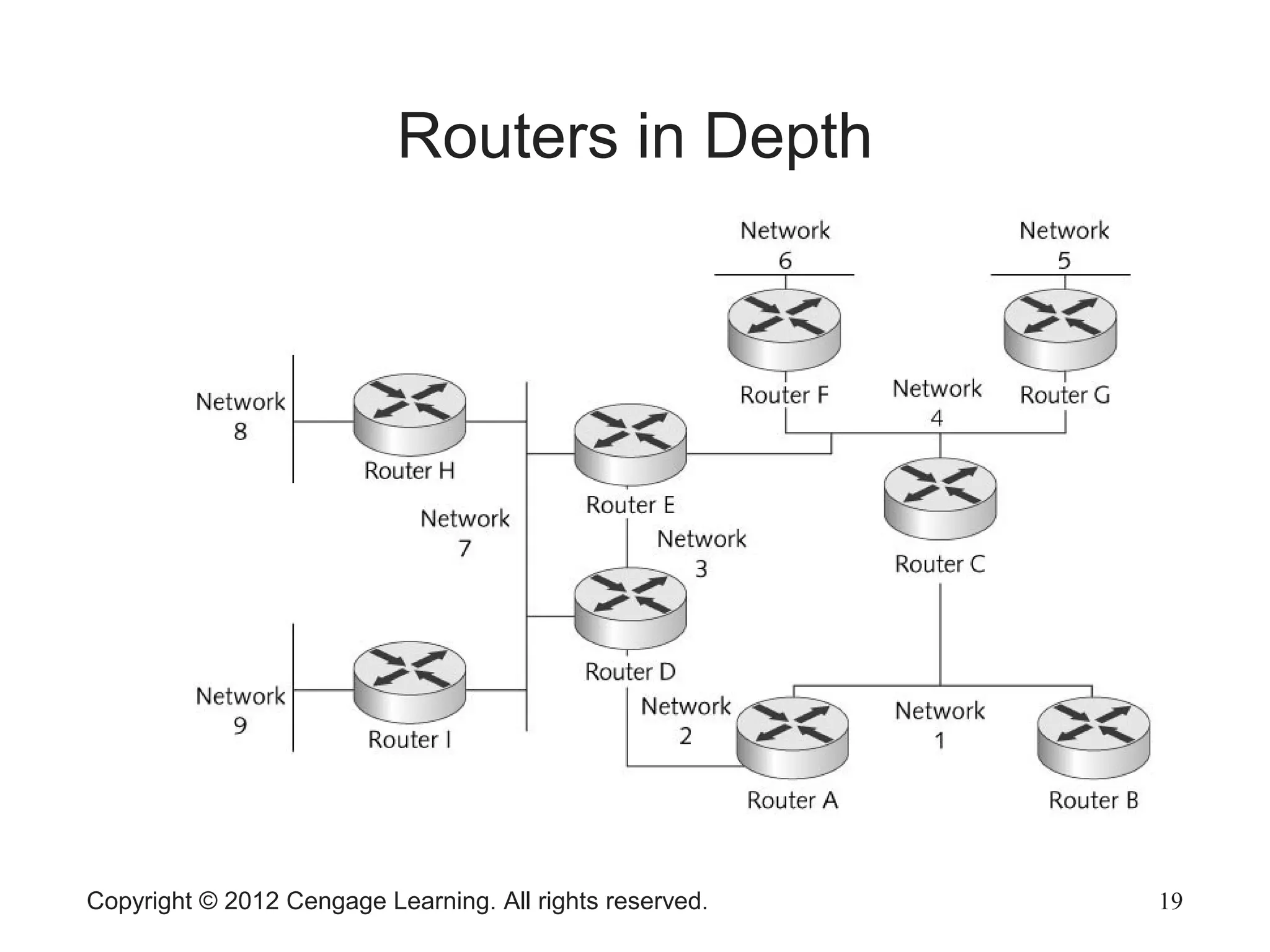
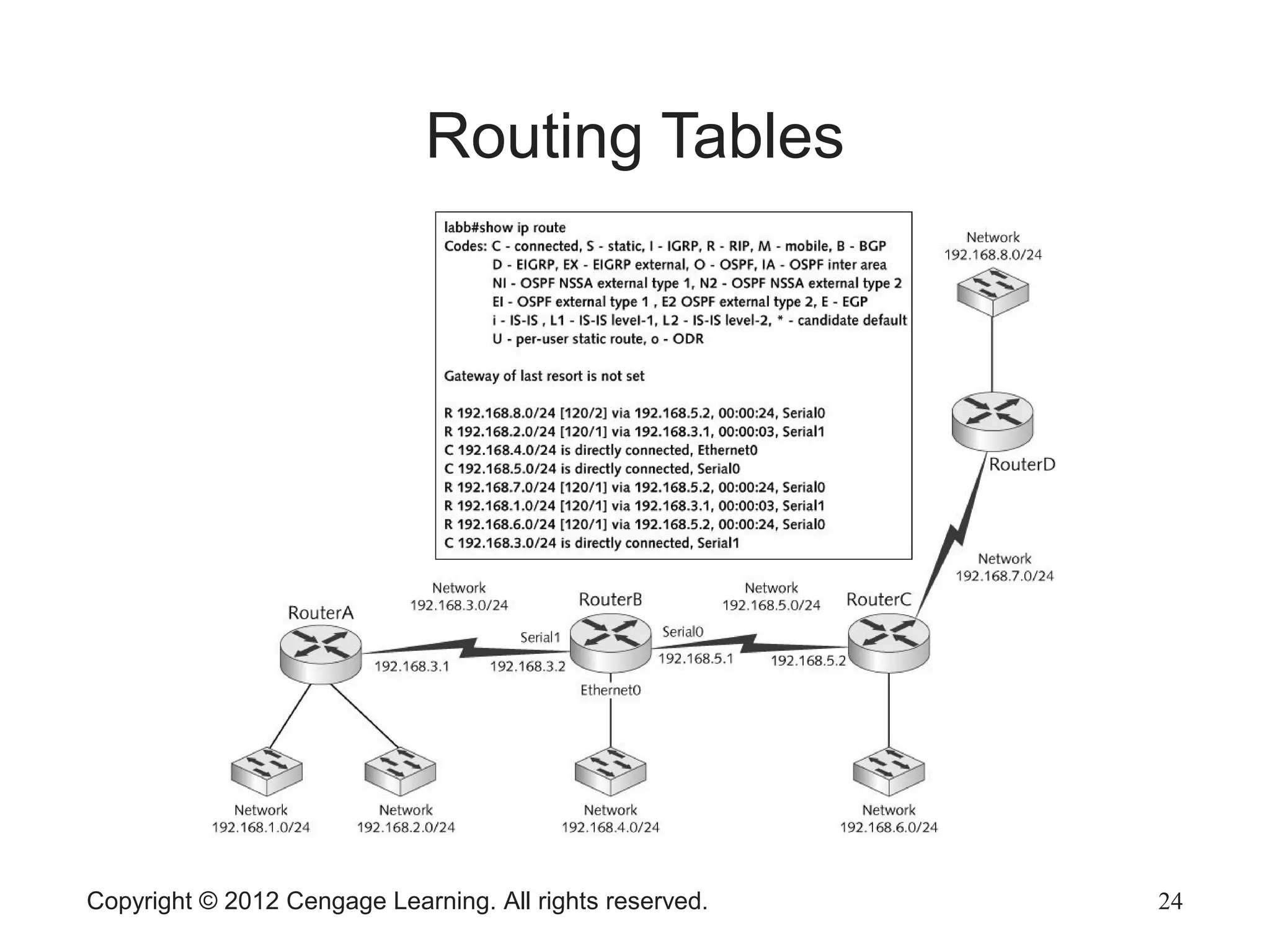
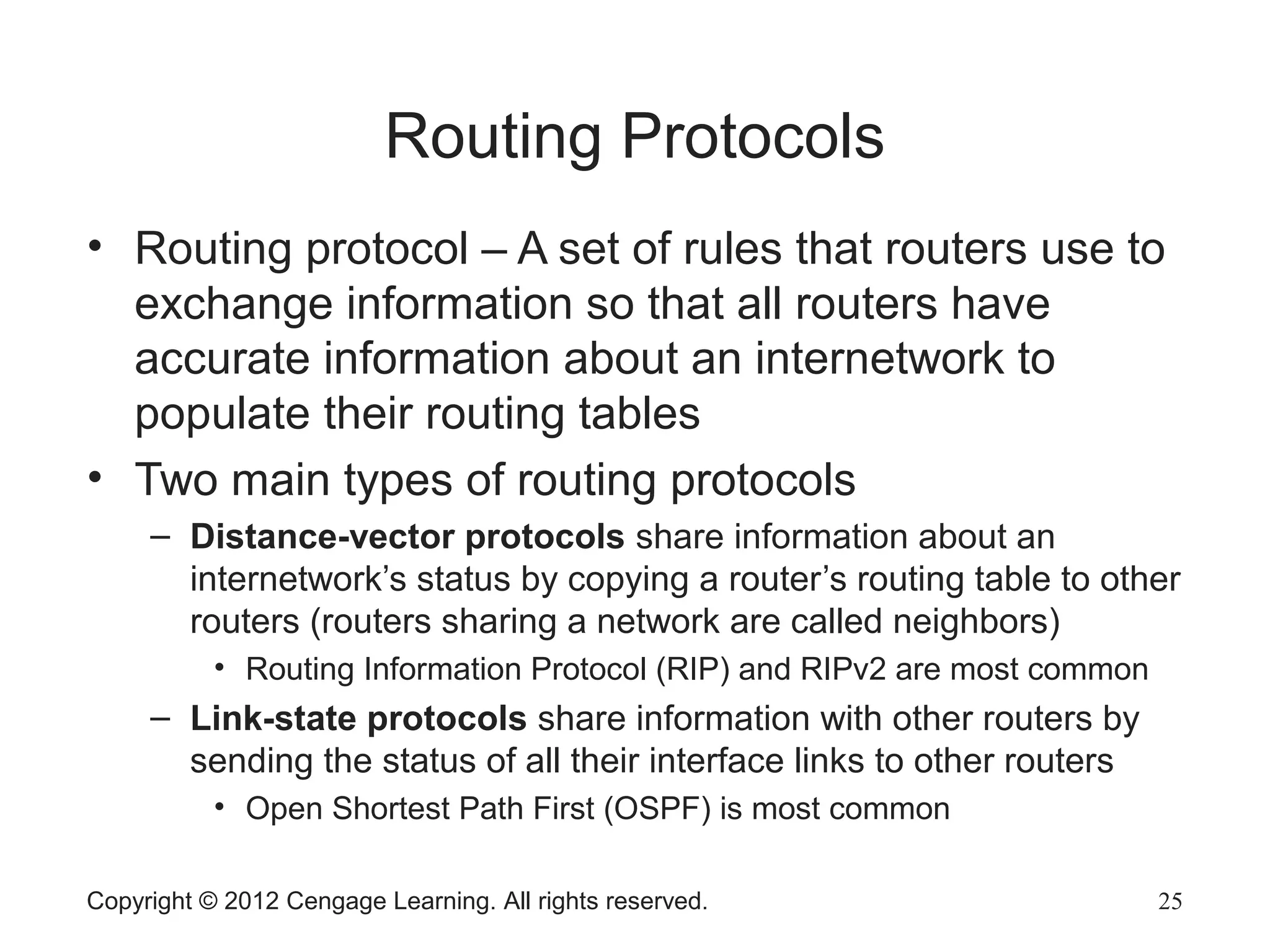
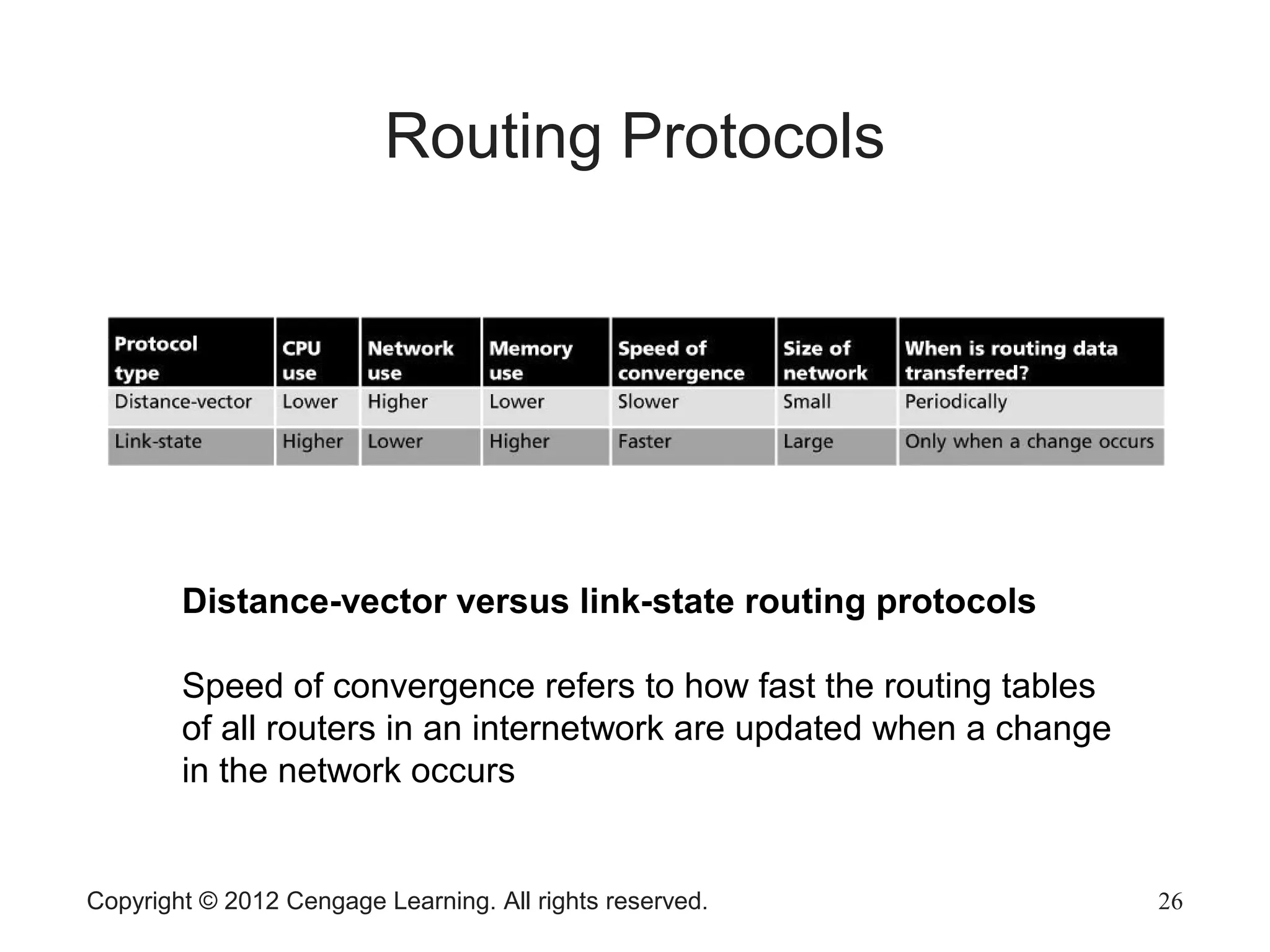
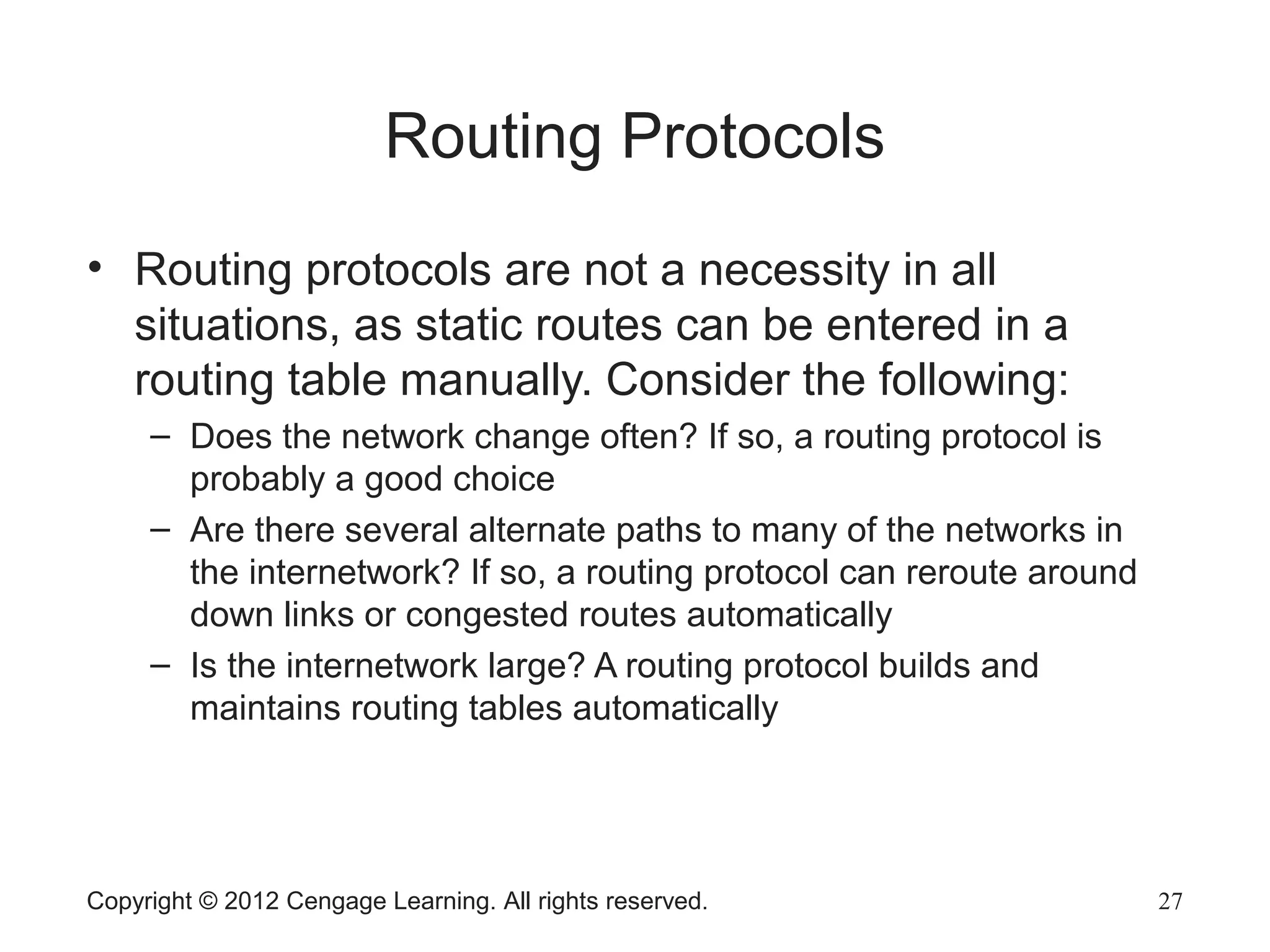
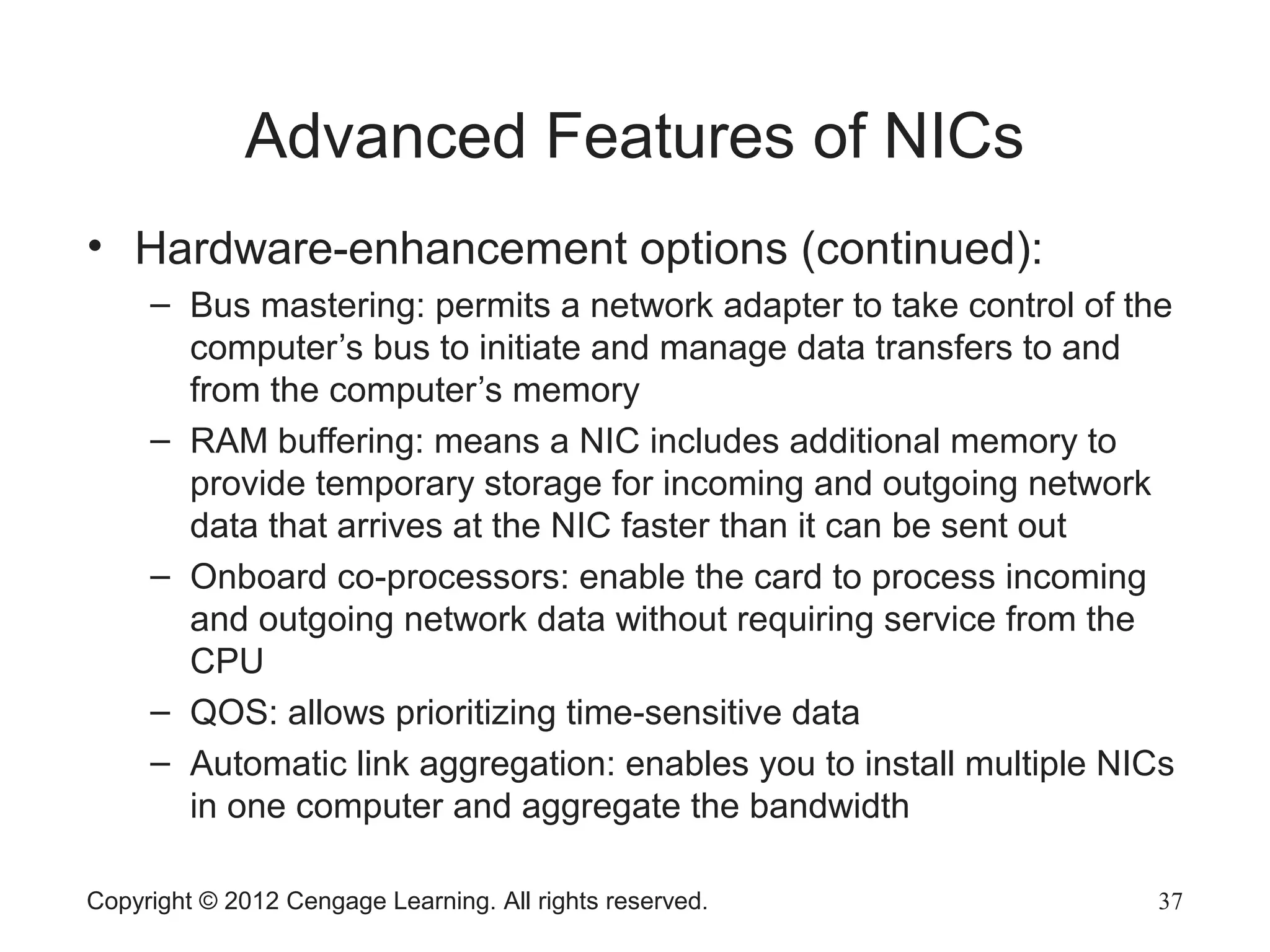
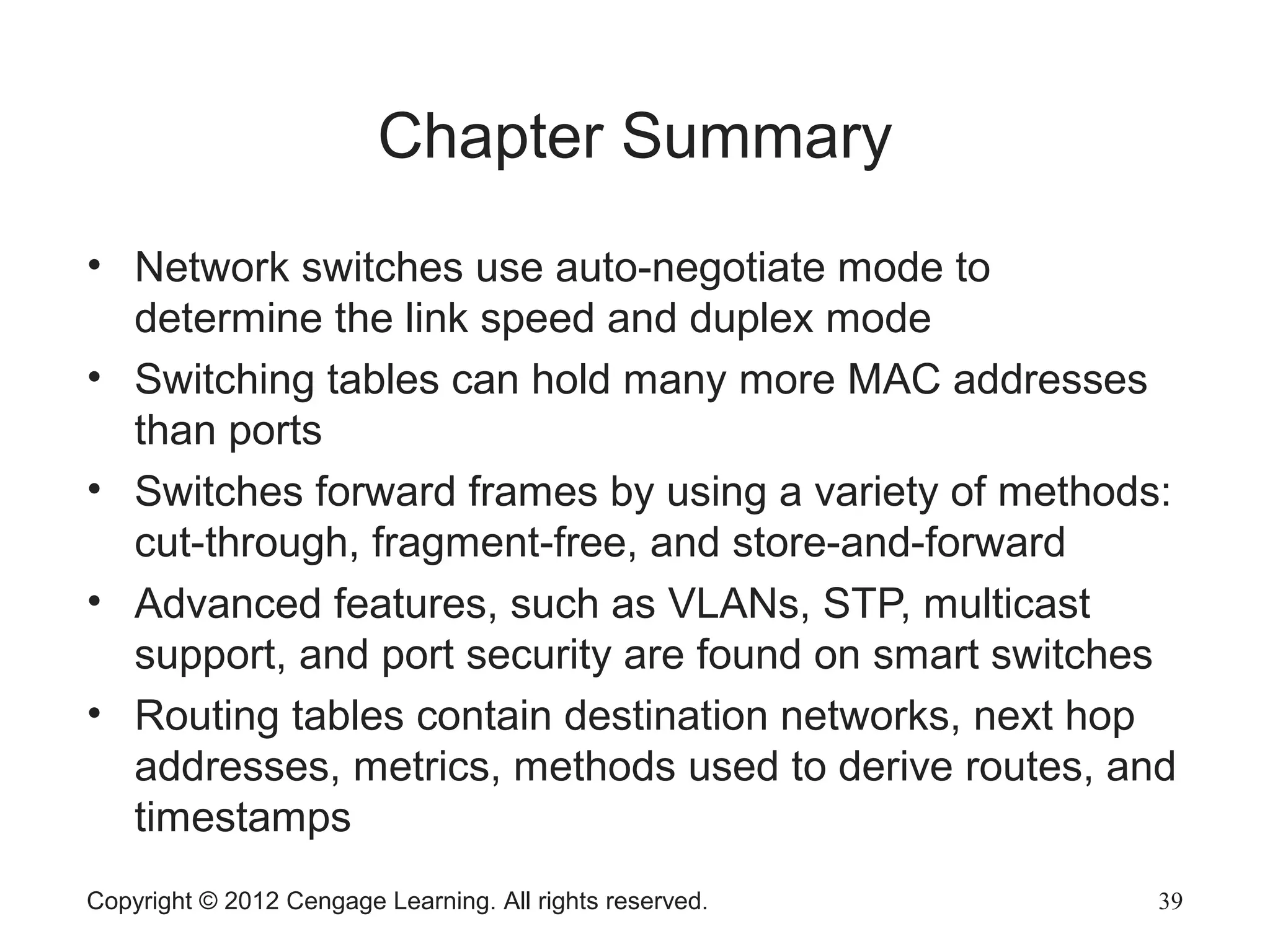
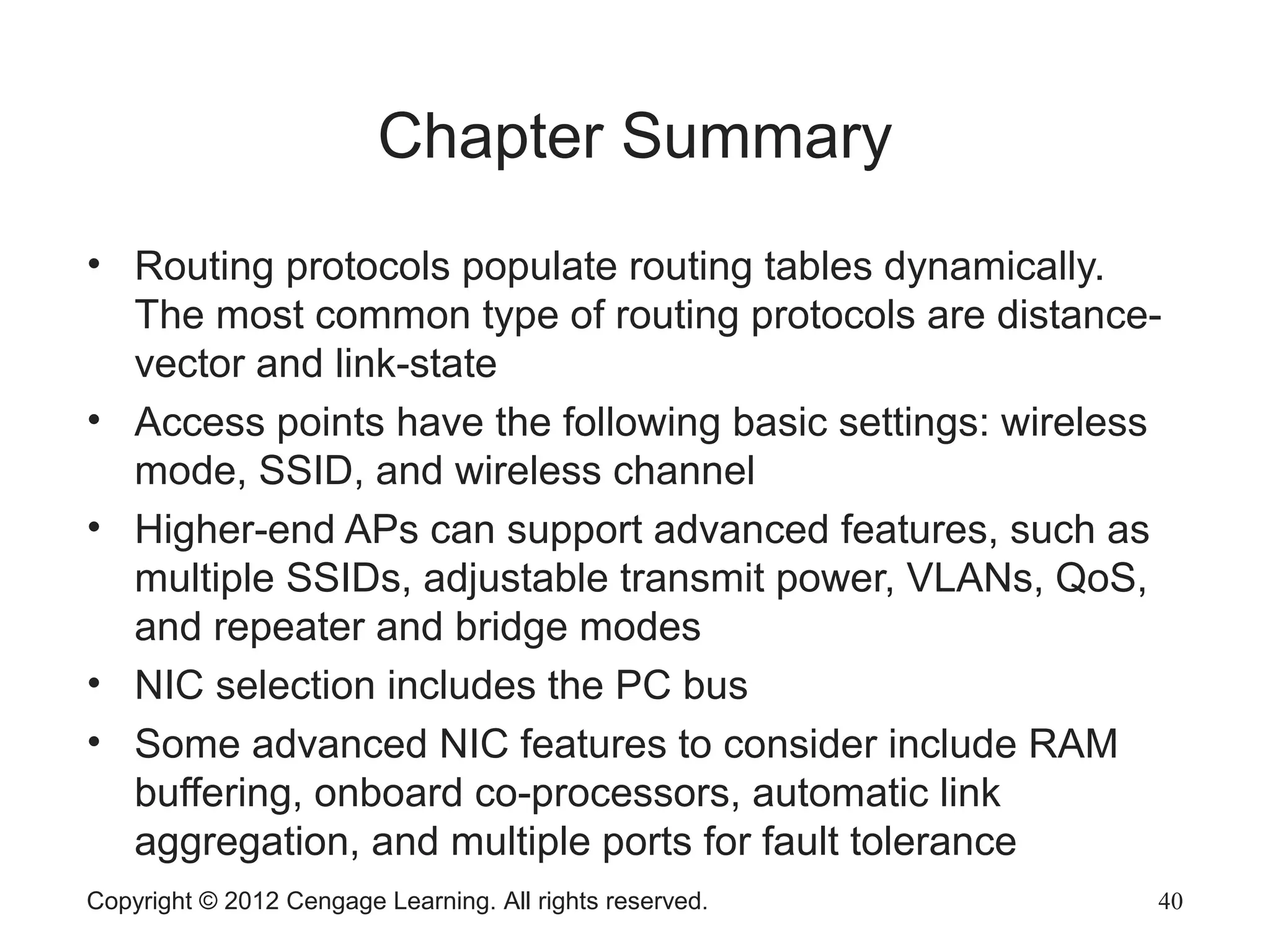
This chapter discusses network hardware in depth, including switches, routers, wireless access points, and network interface cards. It describes the operation and advanced features of switches, such as creating the switching table, frame forwarding methods, and features like VLANs and port security. For routers, it explains routing tables, routing protocols, and access control lists. It also covers wireless security options, advanced wireless settings, and bus and feature options for network interface cards.