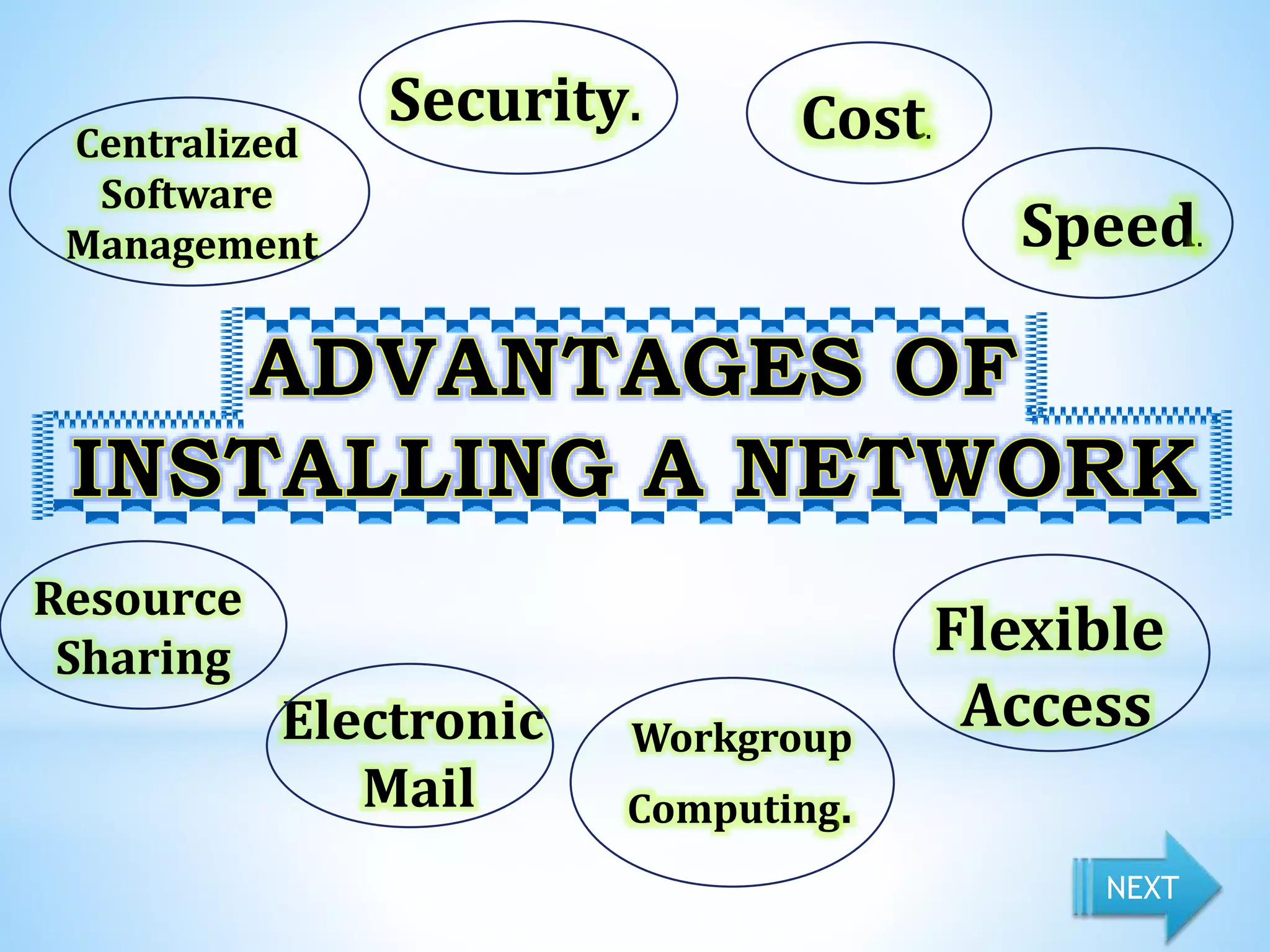
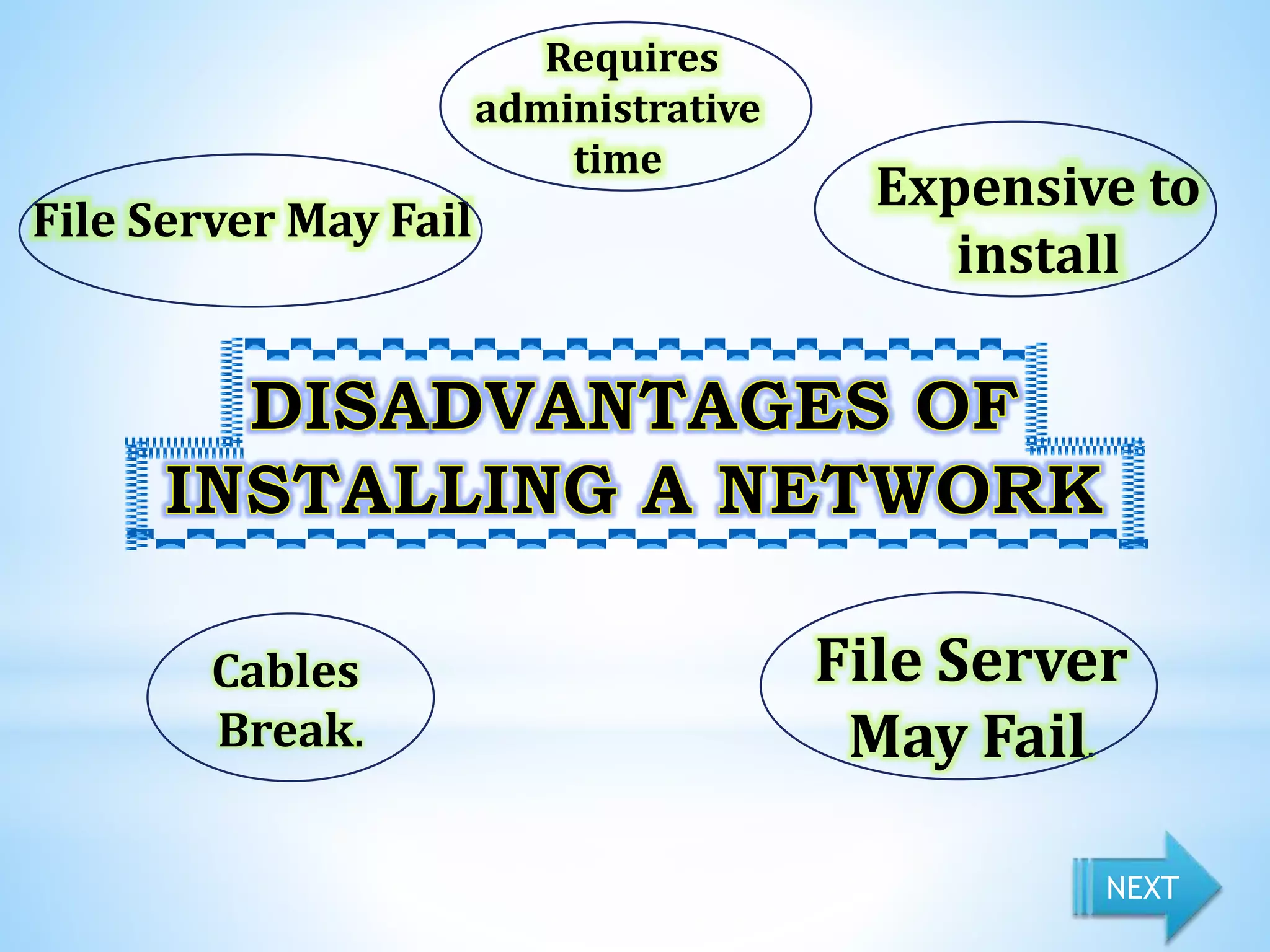
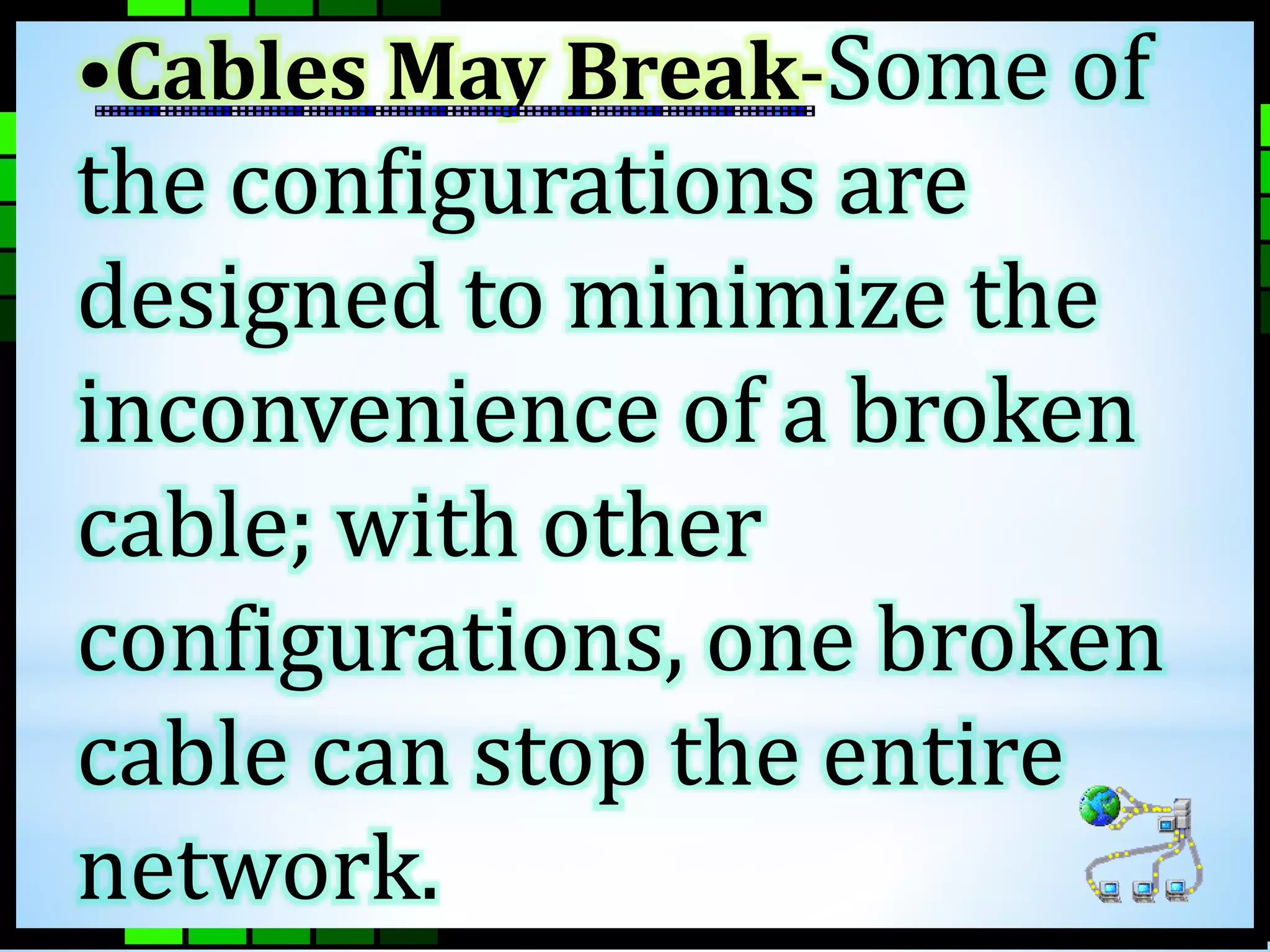
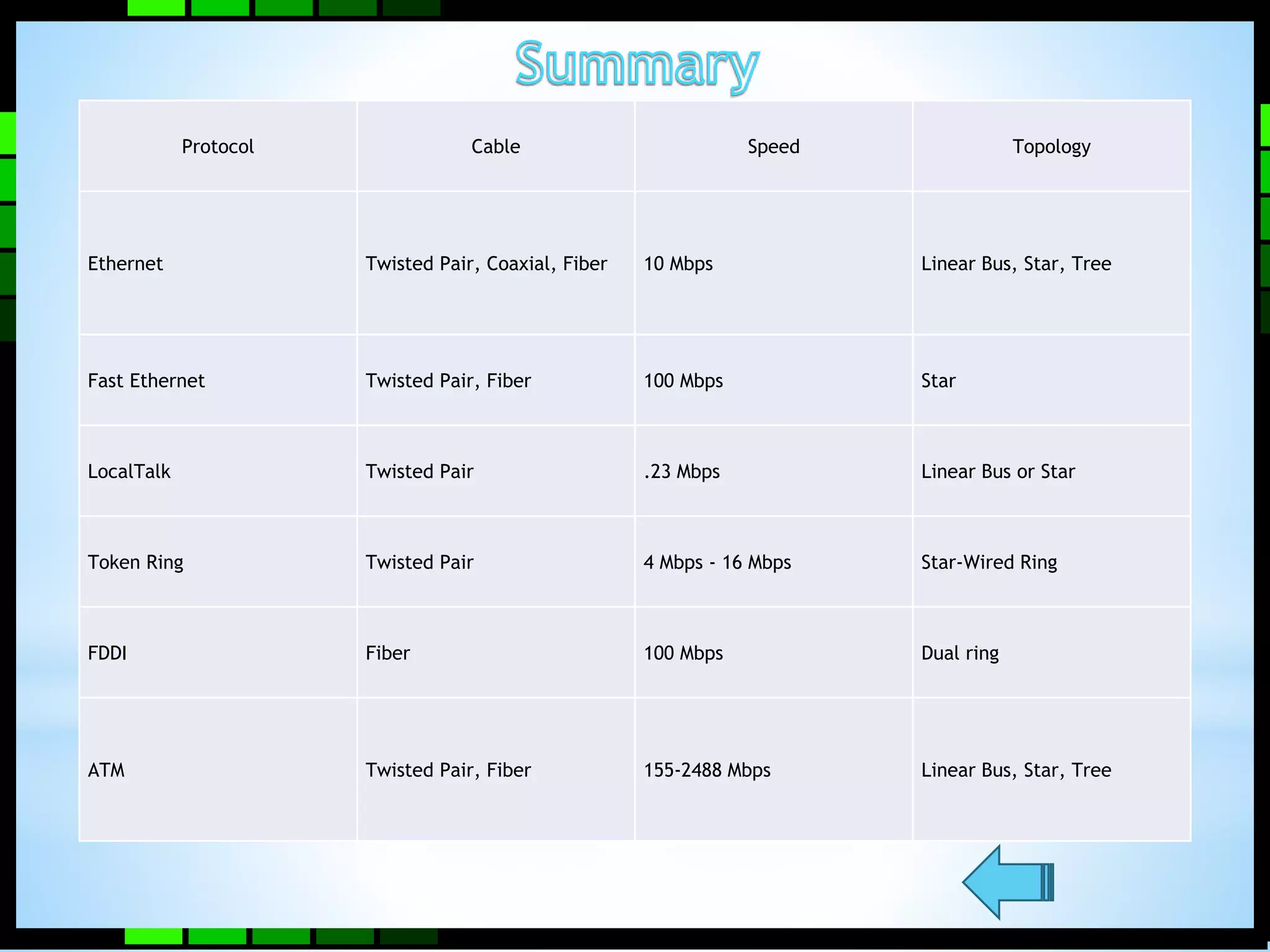
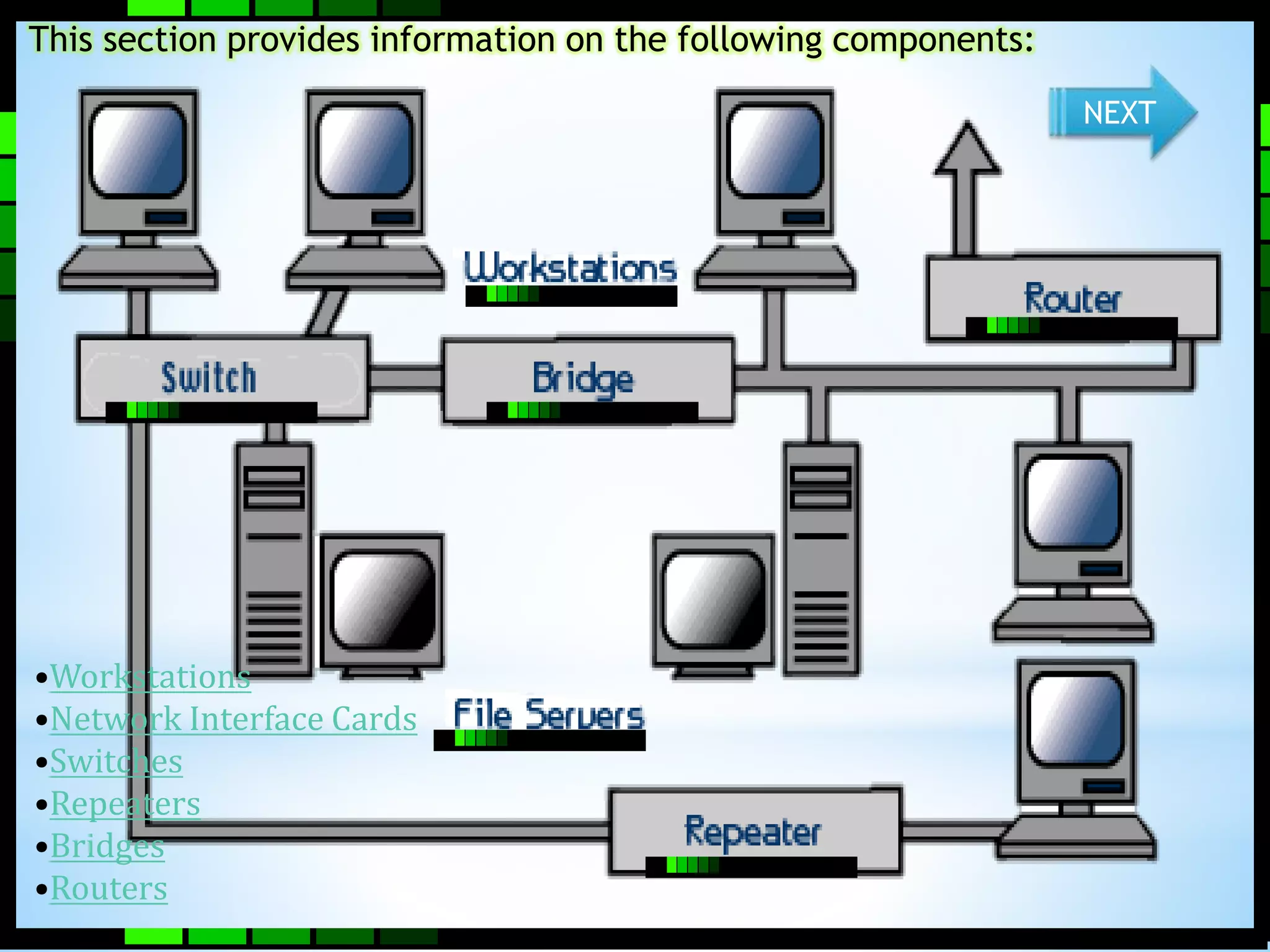
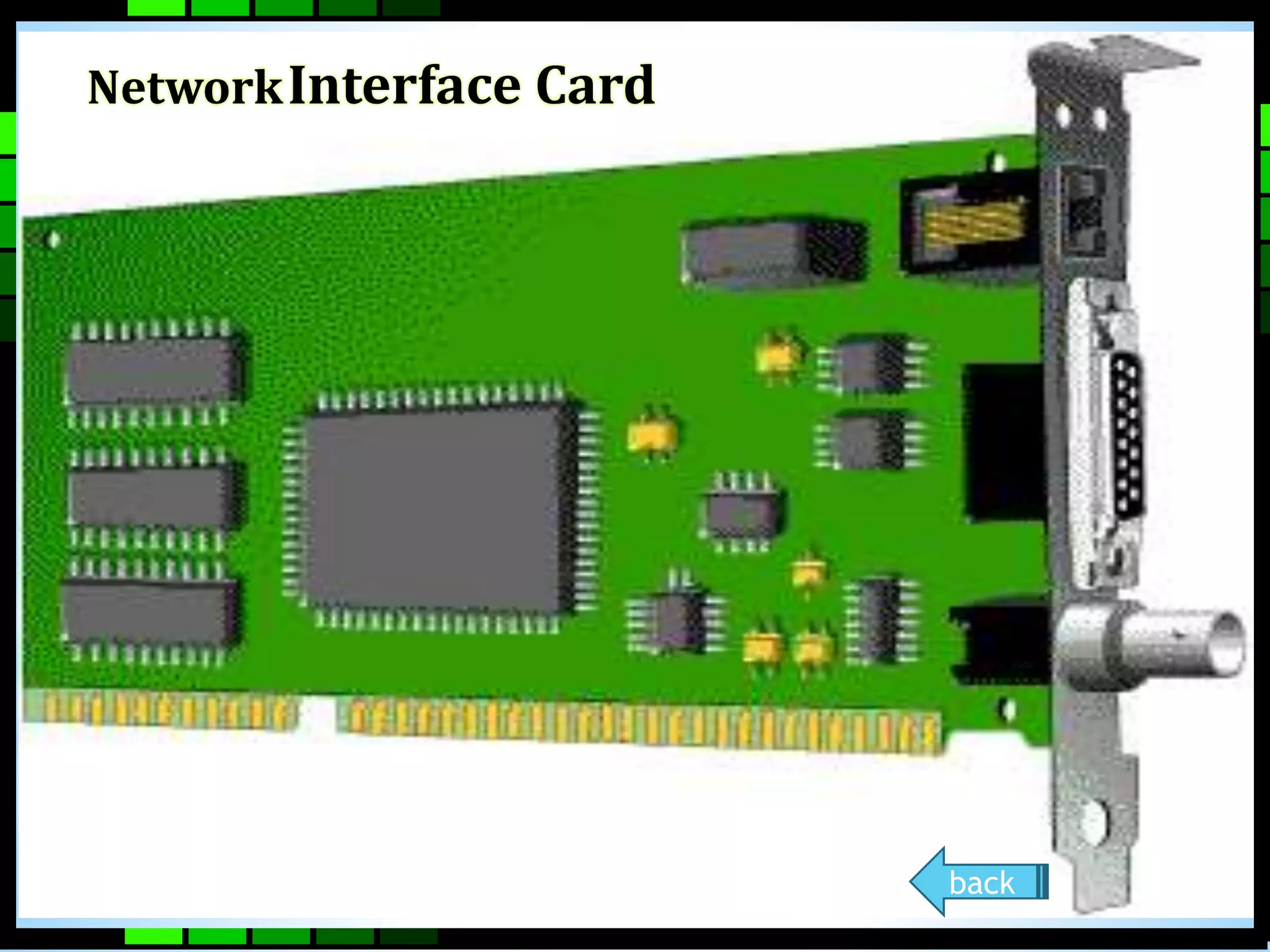
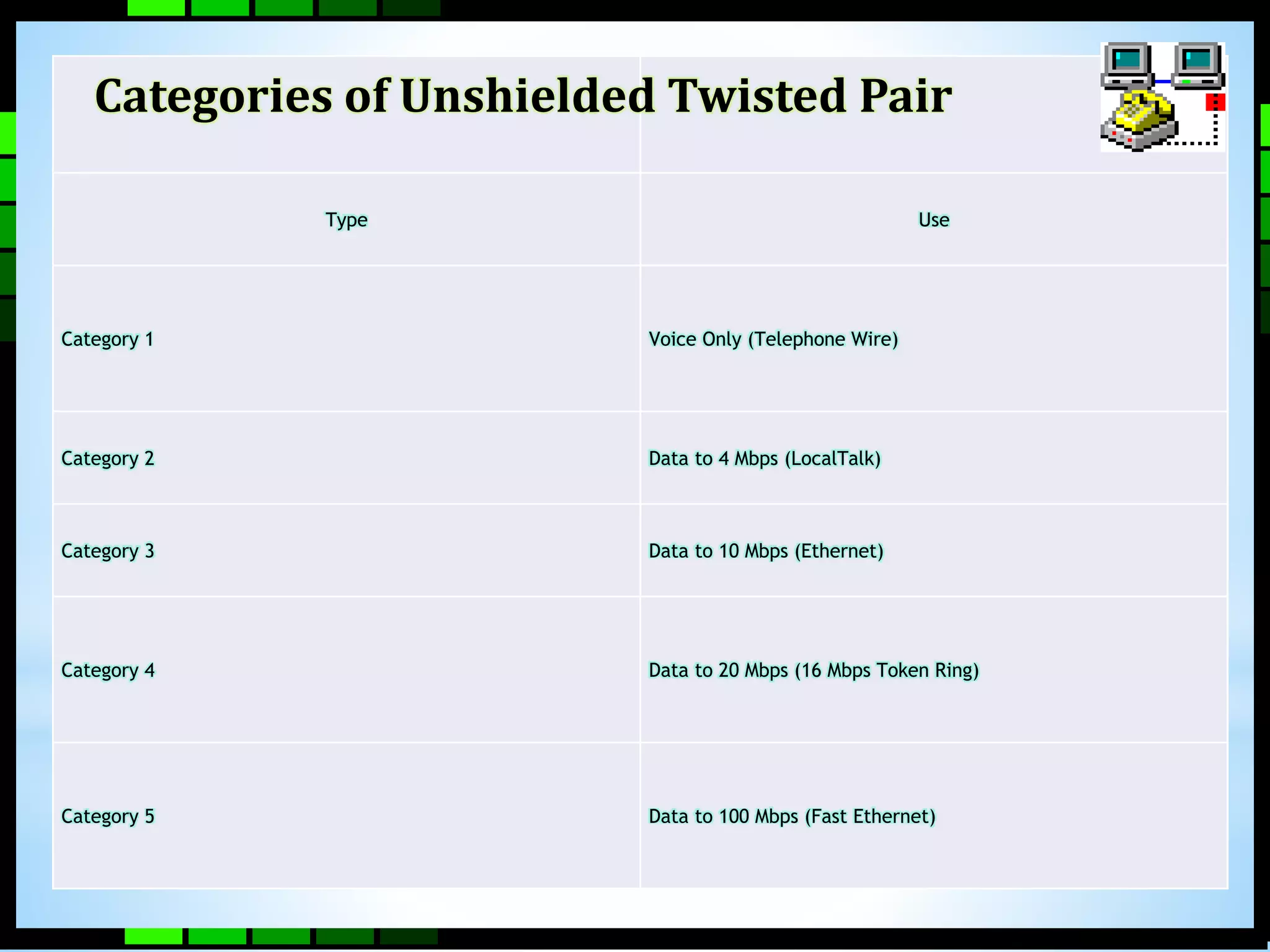
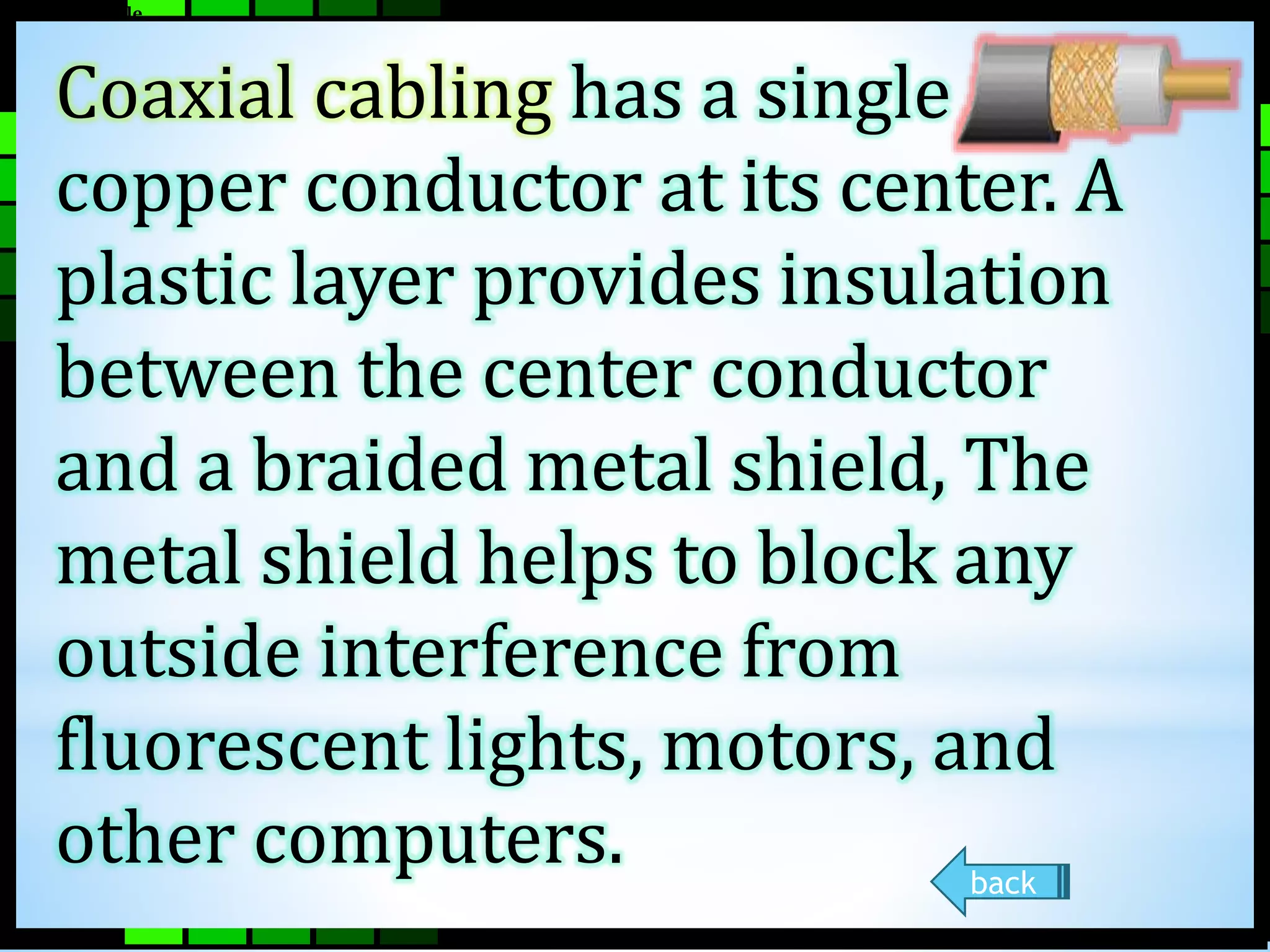
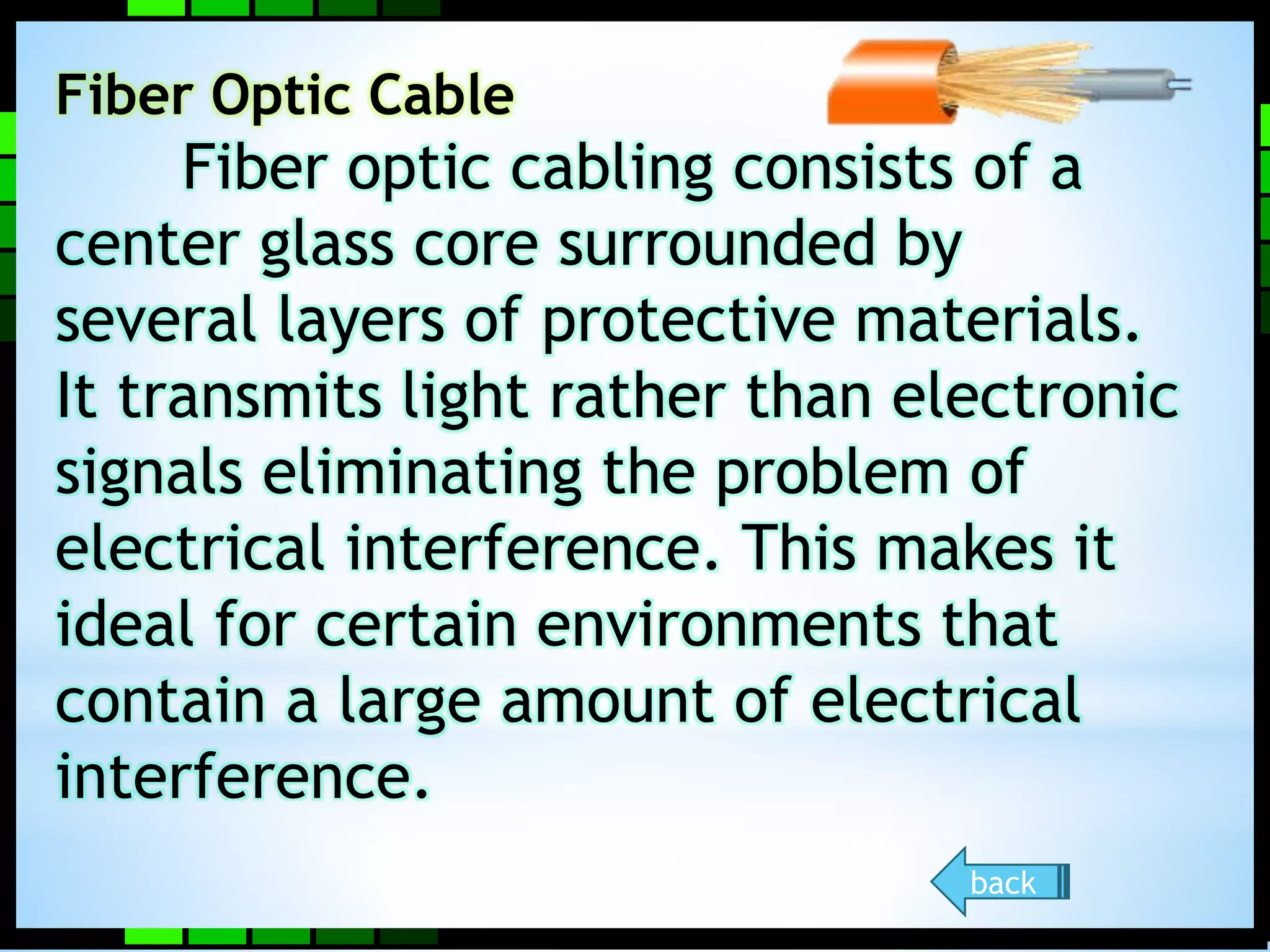
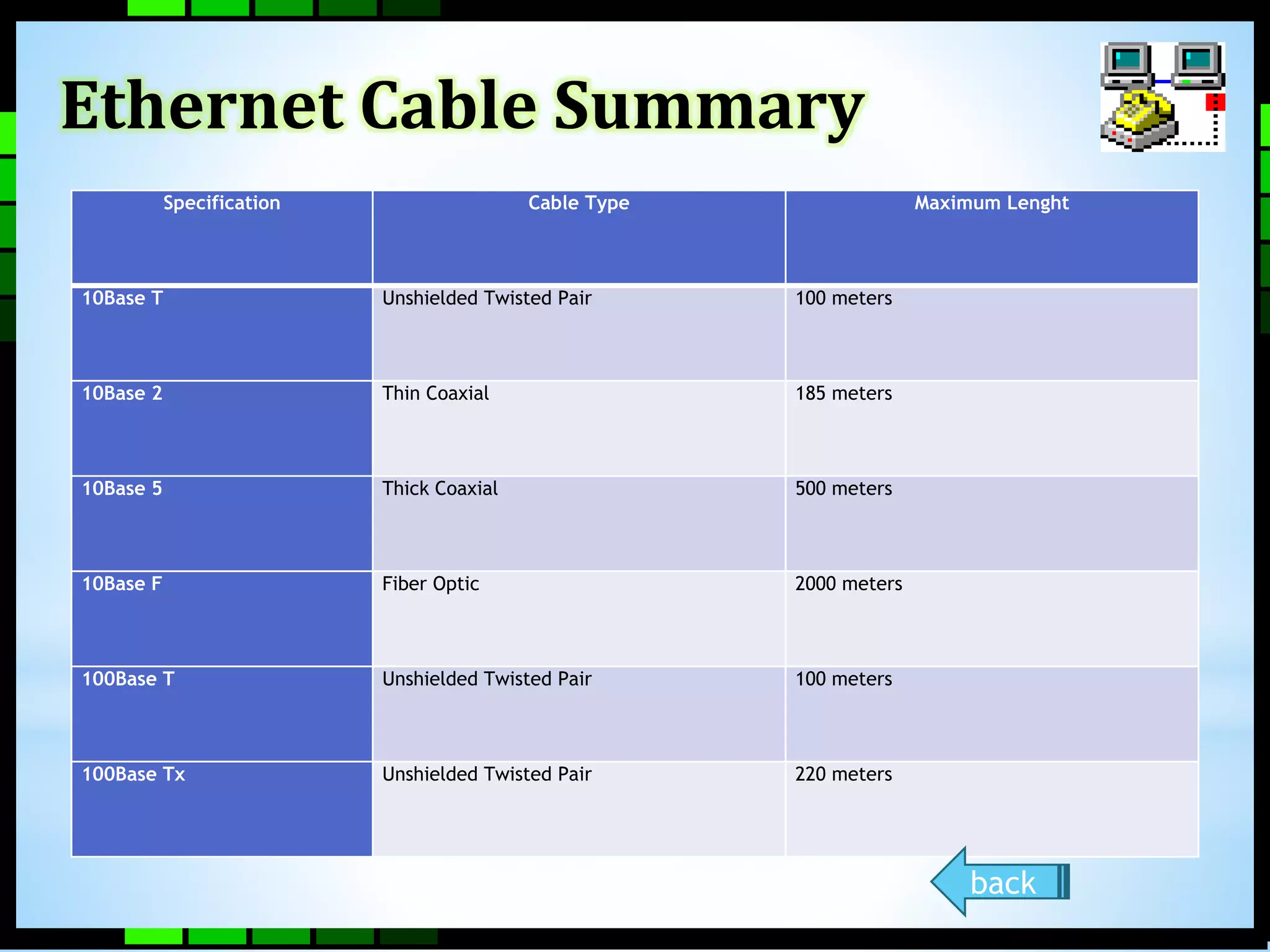
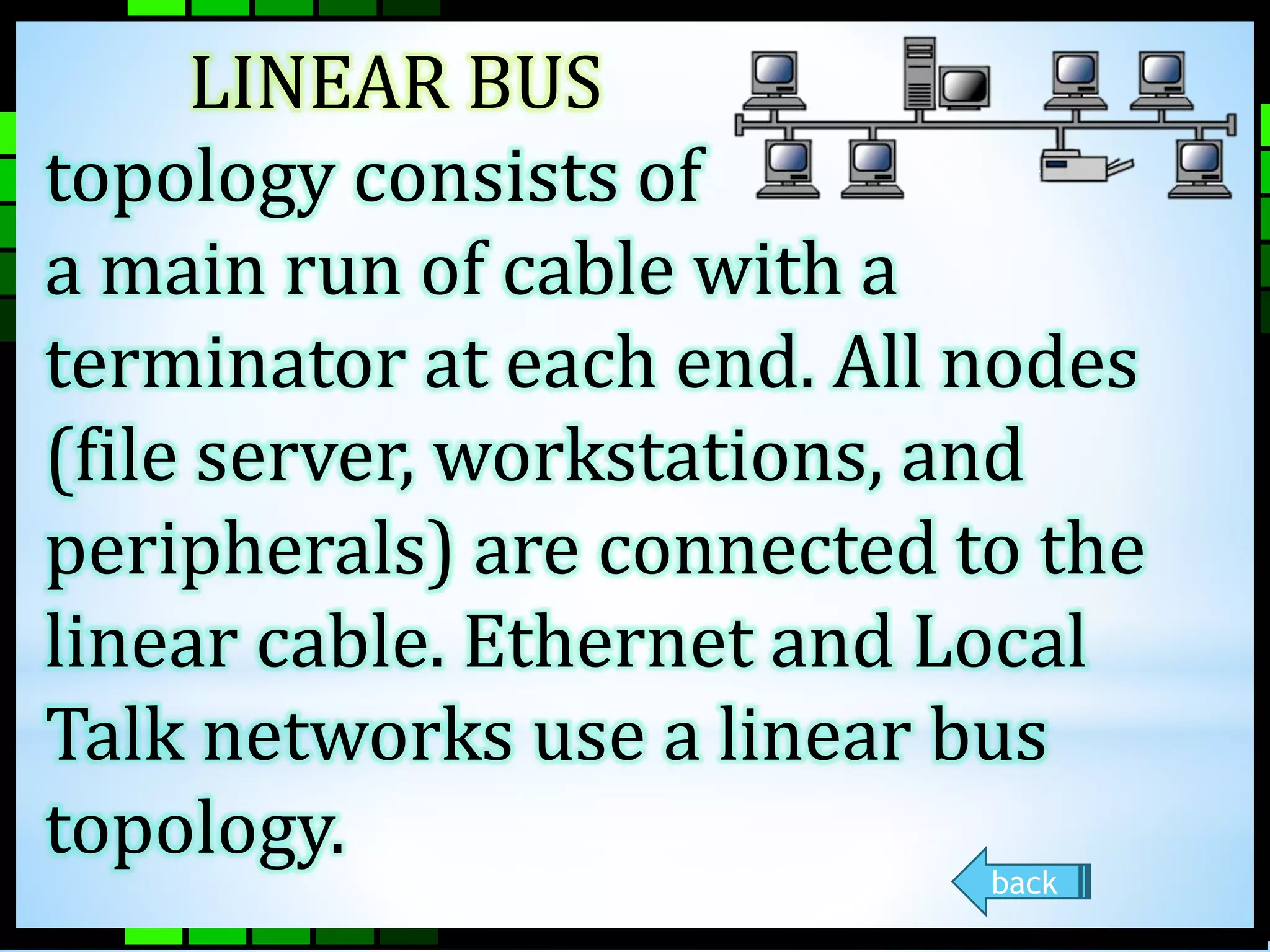
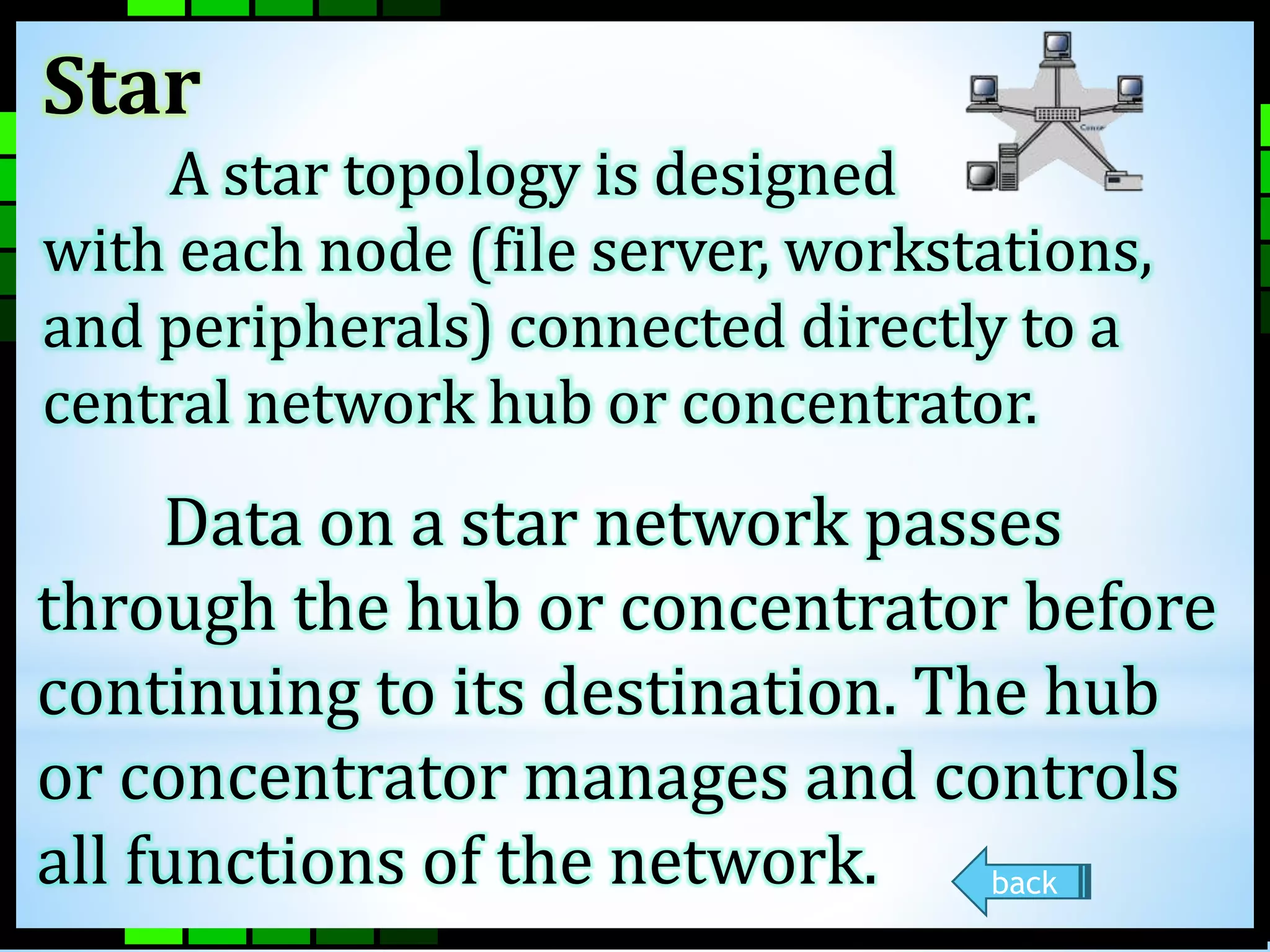
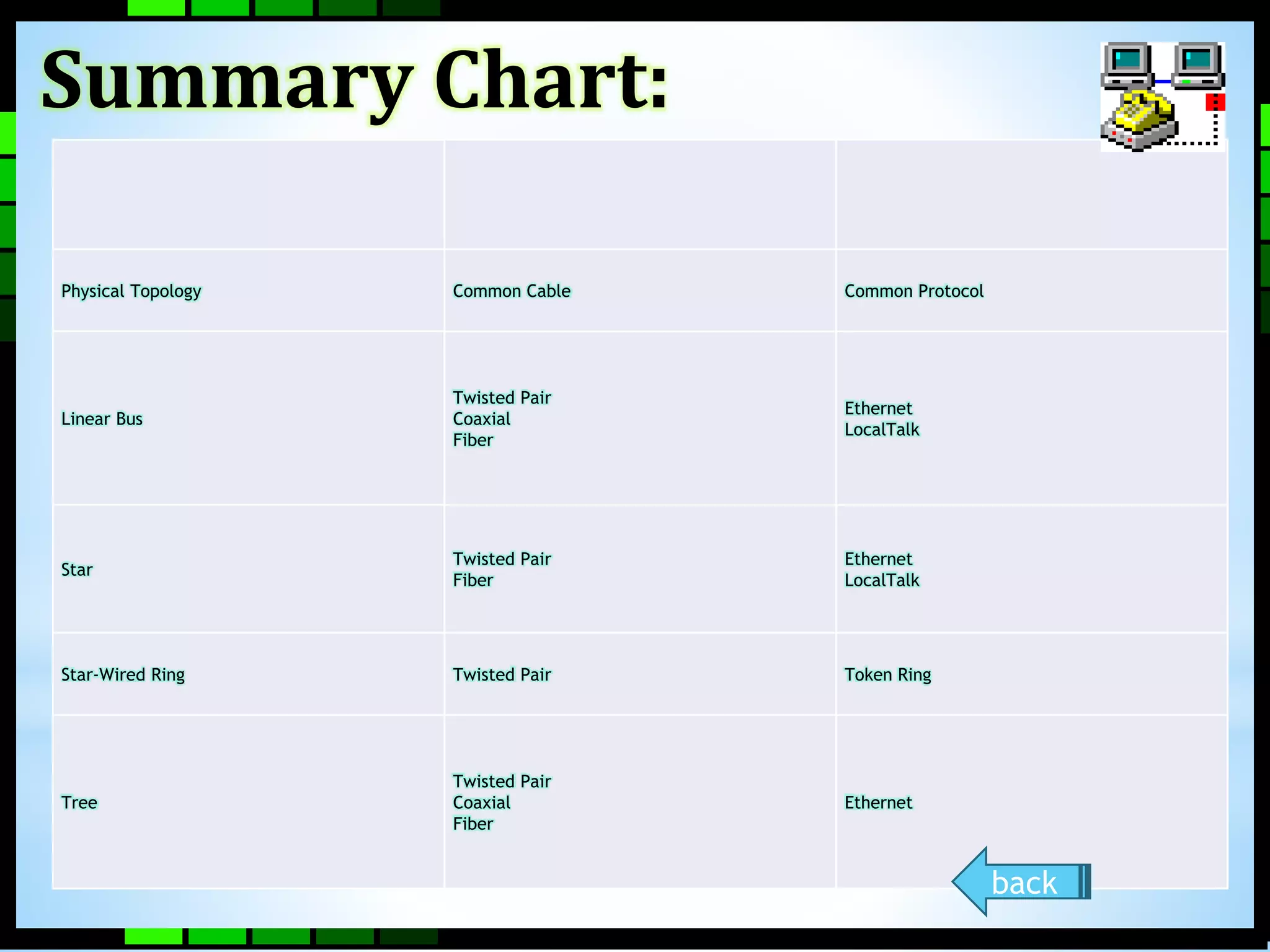
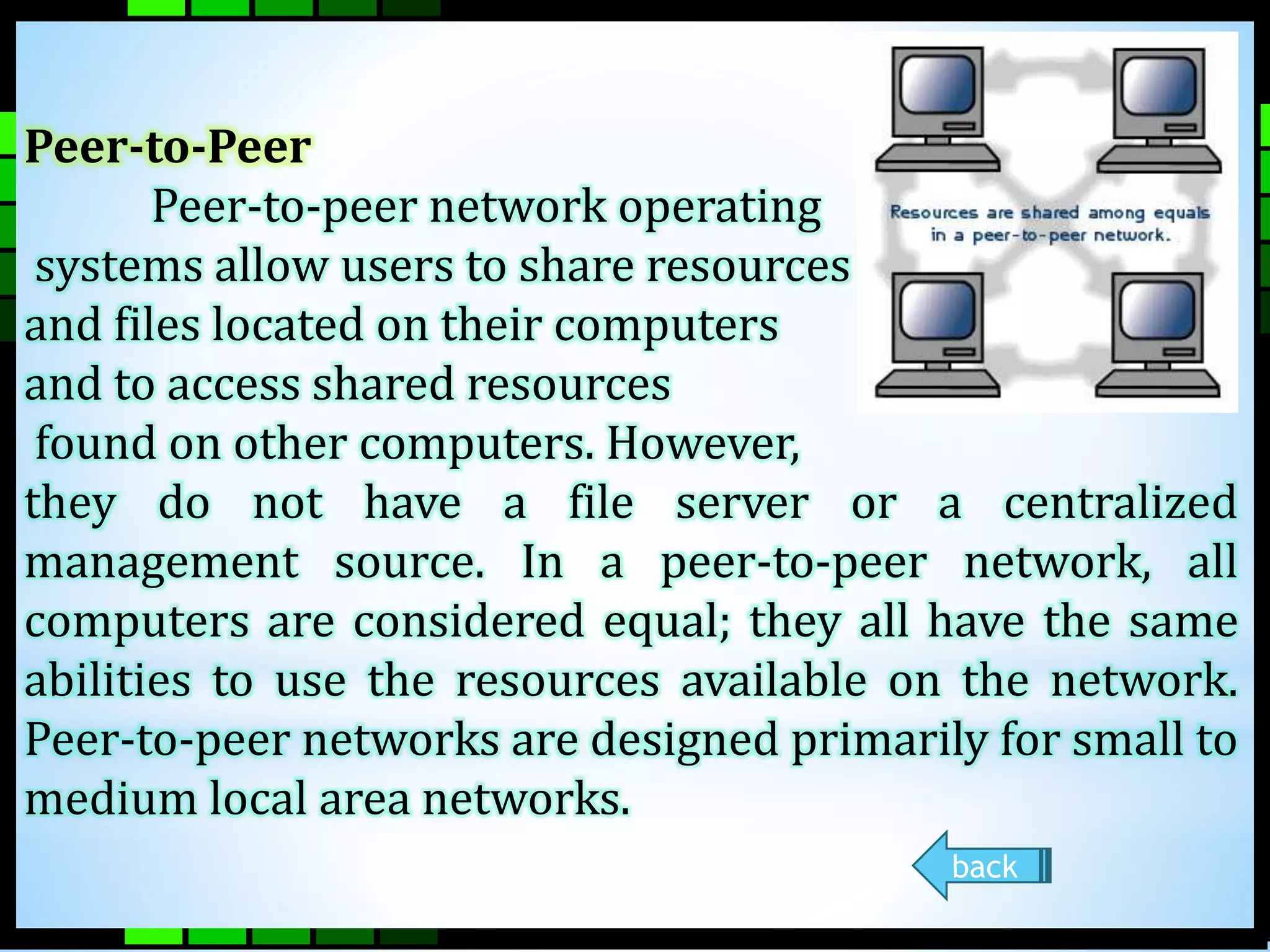
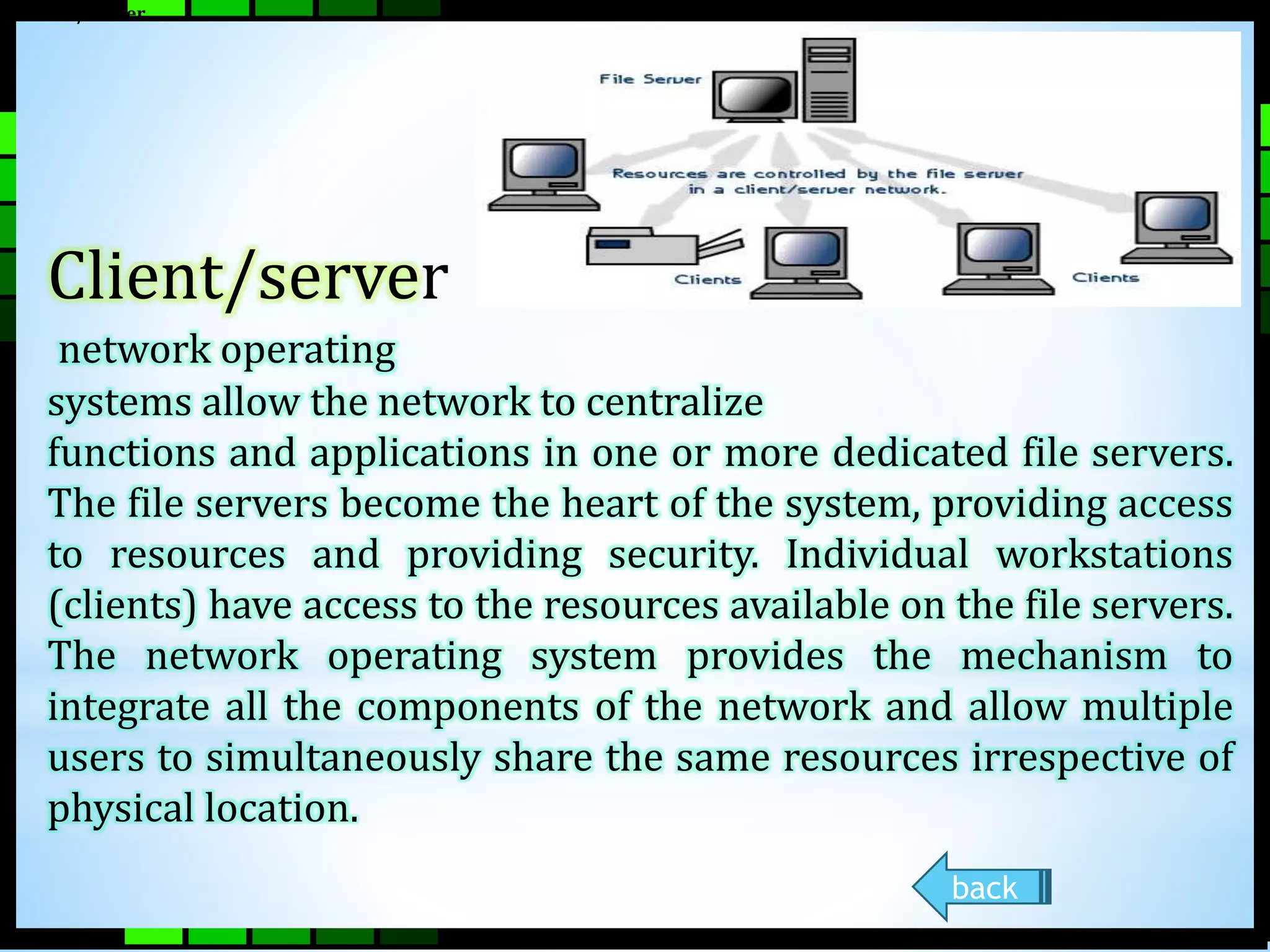
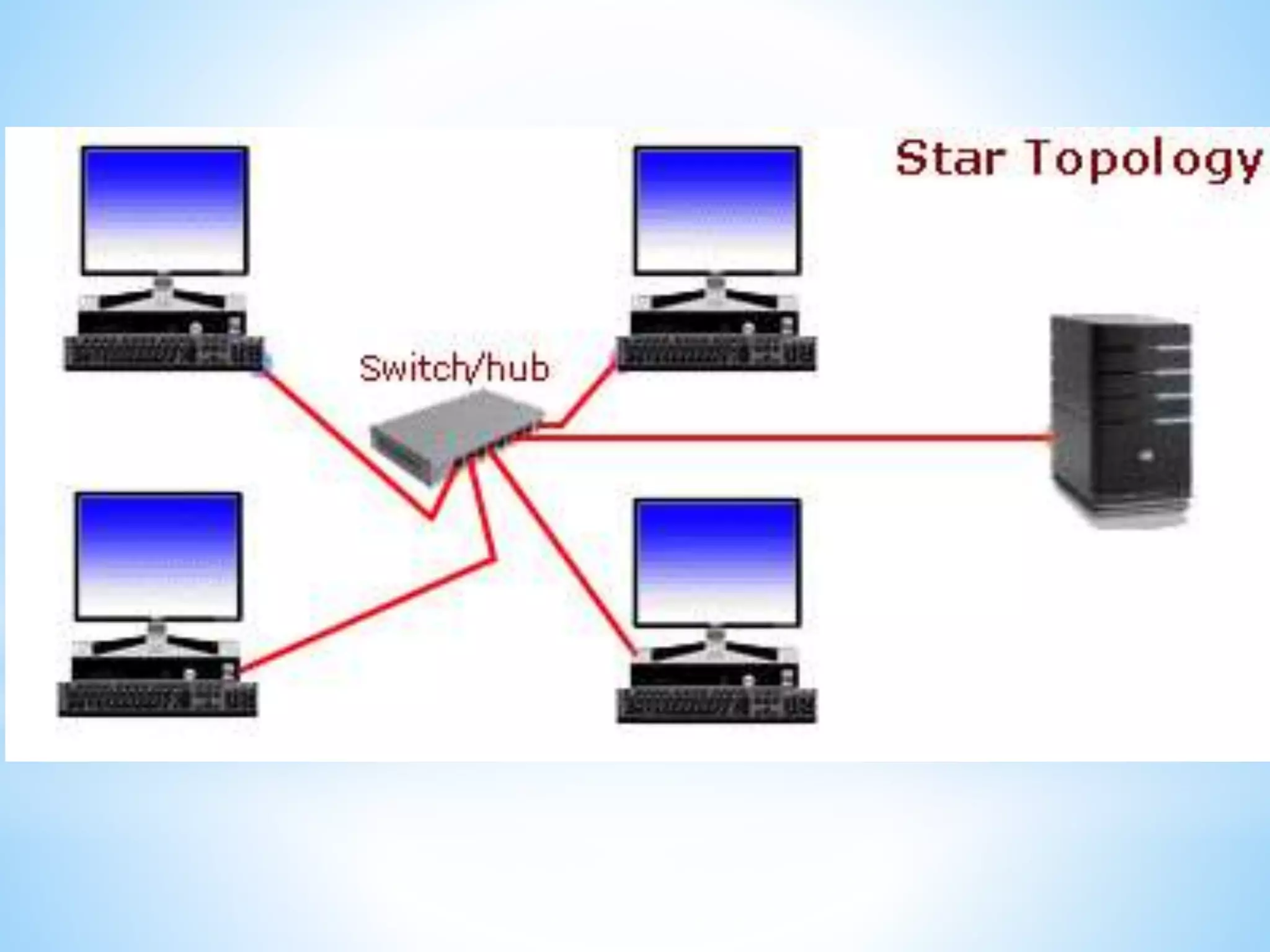
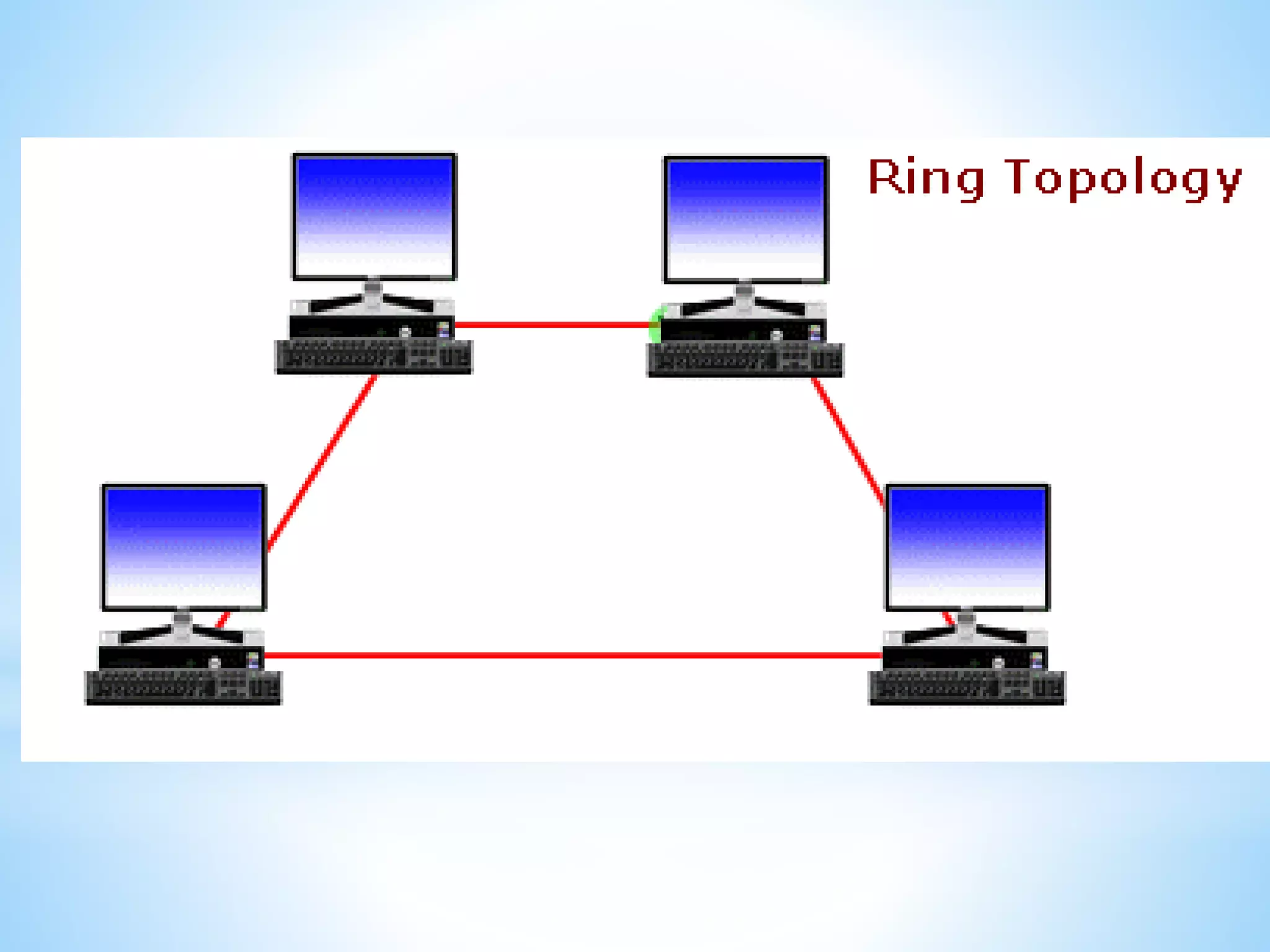
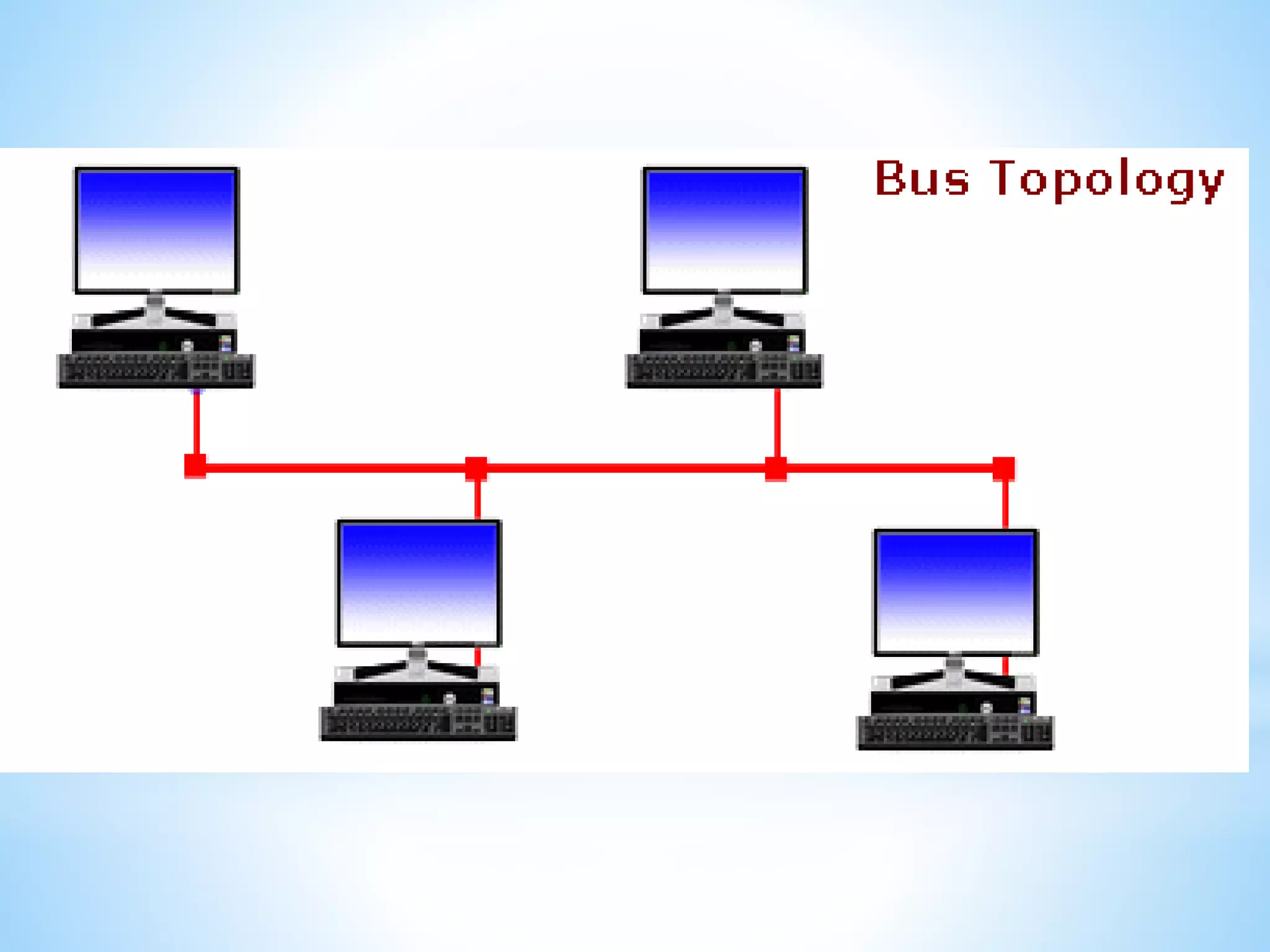
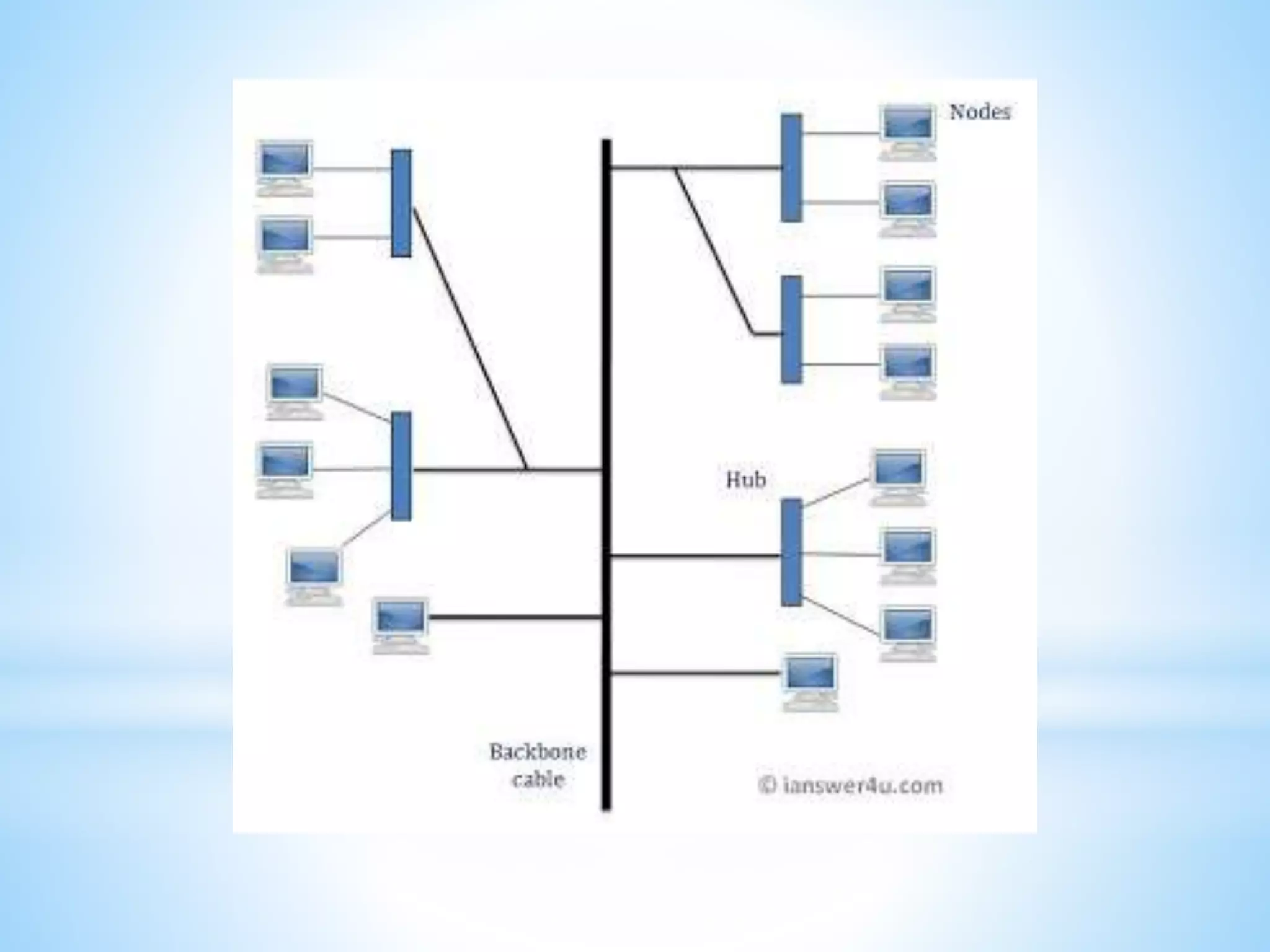
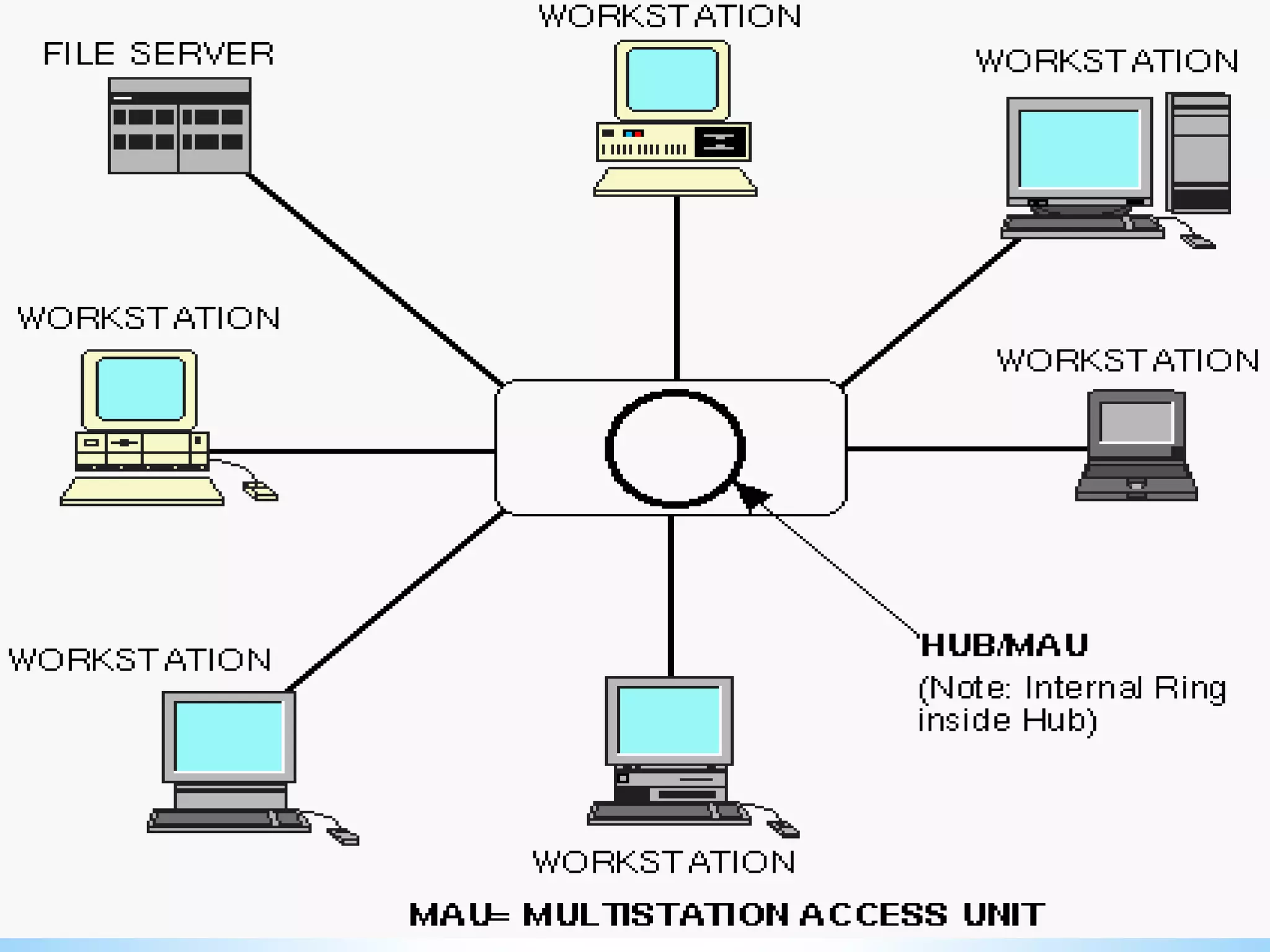
This document provides information on different types of computer networks including local area networks (LANs), metropolitan area networks (MANs), and wide area networks (WANs). It then discusses various networking components such as network interface cards, switches, bridges, routers, and different types of network cabling including unshielded twisted pair, coaxial, fiber optic, and wireless networking. The document also provides specifications for Ethernet cable types and their maximum lengths.