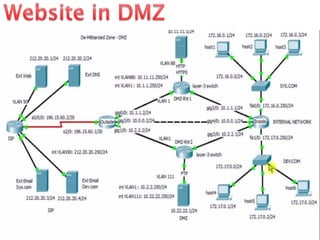
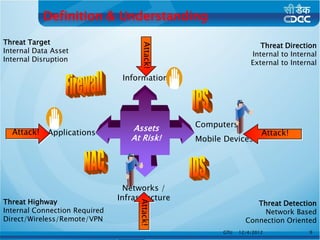
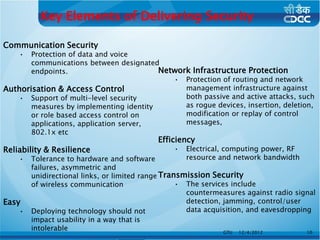
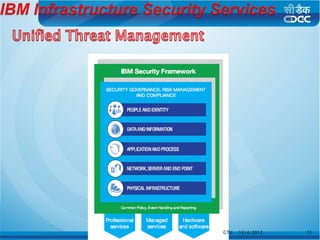
This document is a thesis prepared by Bhadreshsinh Gohil, a 3rd semester student at Gujarat Technological University. It is guided by three officials from the NPSF Group at C-DAC Pune. The thesis proposes a framework to streamline the process of releasing new websites and web portals to the public internet. It discusses some challenges with the current process and proposes a web-enabled framework using technologies like PHP, Java and databases. The framework would delegate tasks to stakeholders and support different user roles for activities like implementing security policies.