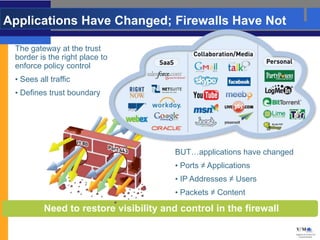
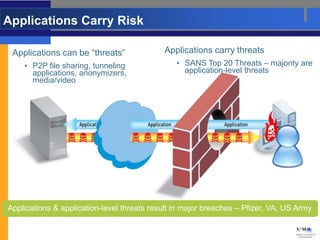
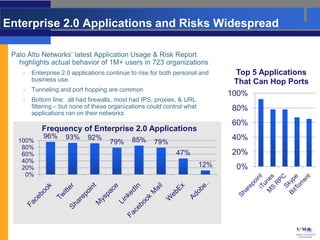
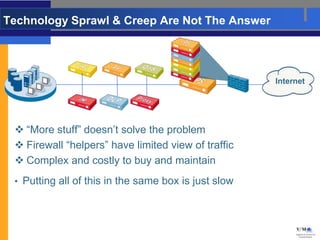
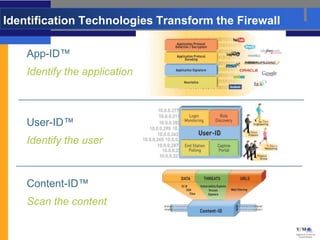
- Palo Alto Networks builds next-generation firewalls that can identify over 1,100 applications regardless of port or protocol, restoring visibility and control to the firewall.
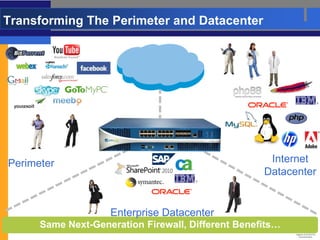
- Traditional firewalls cannot control applications effectively as applications change but firewalls have not. Next-generation firewalls from Palo Alto Networks address this by identifying applications, users, and scanning content.
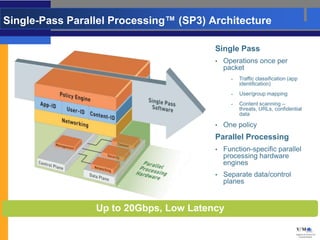
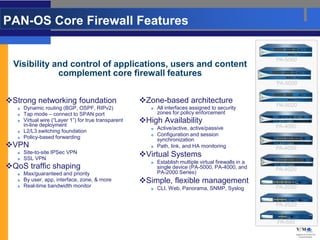
- These firewalls provide comprehensive visibility and policy control over application access and functionality with high-performance processing capabilities.