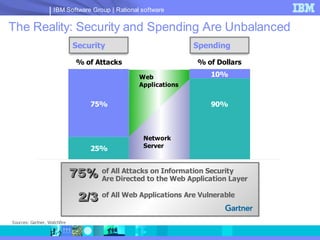
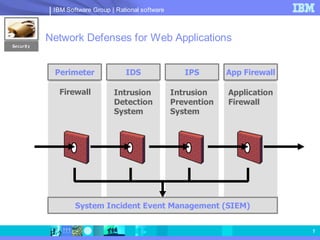
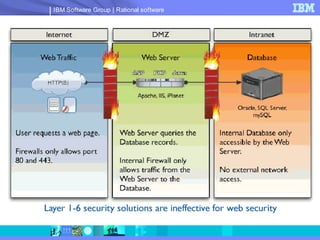
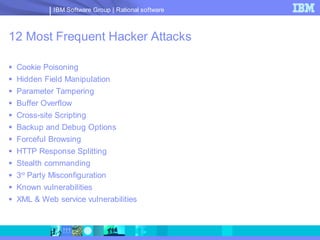
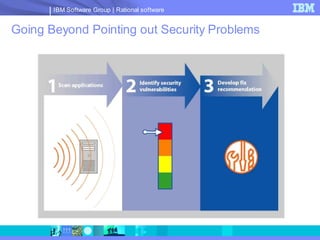
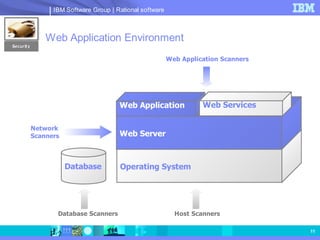
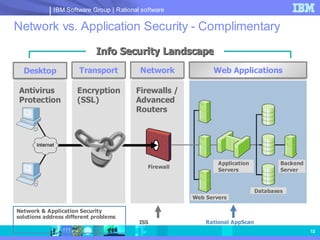
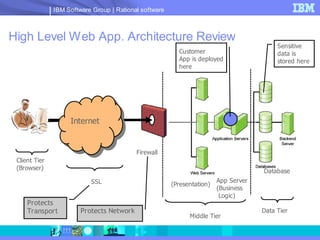
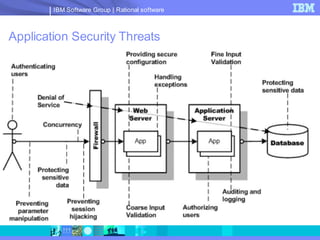
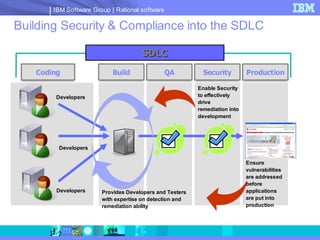
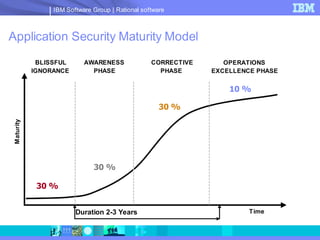
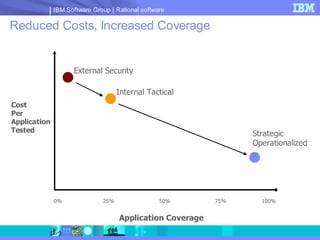
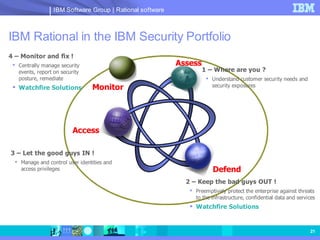
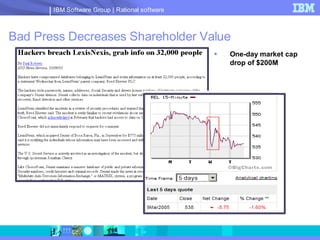
The document discusses web application security and securing the software development lifecycle. It notes that web applications are the top target of hackers, with many sites being vulnerable. It emphasizes that network defenses like firewalls are not enough, and that application security needs to be addressed throughout development. The document promotes IBM Rational products for automating security testing of web applications across the entire development lifecycle.