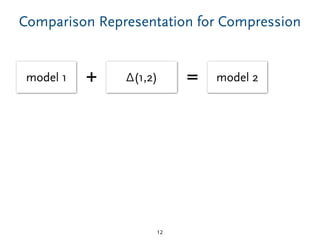
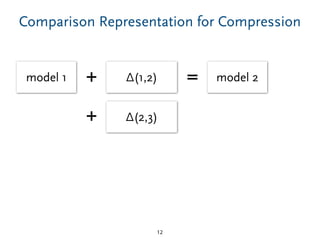
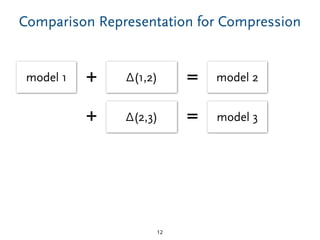
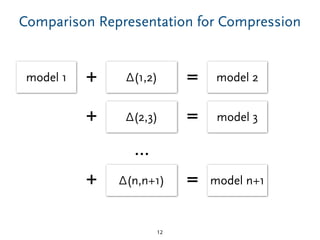
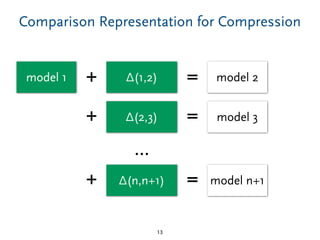
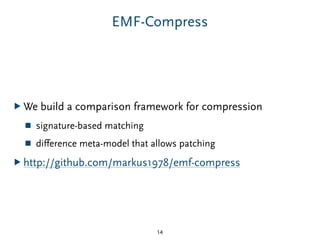
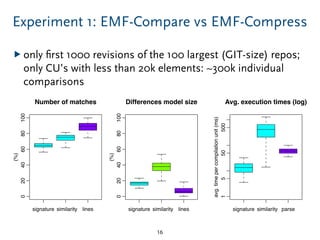
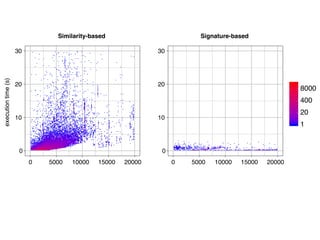
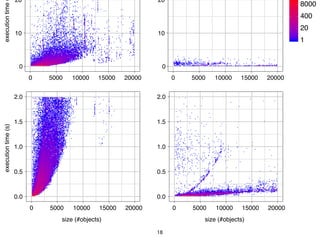
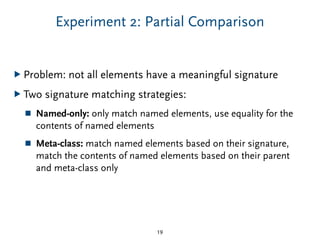
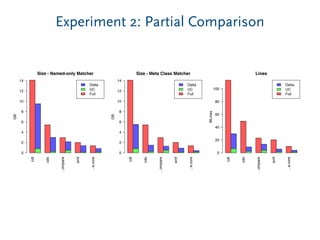
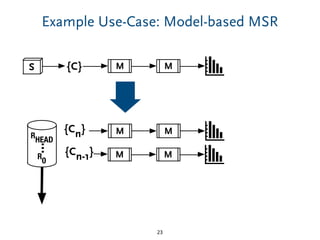
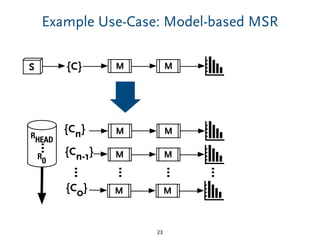
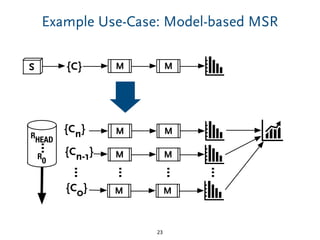
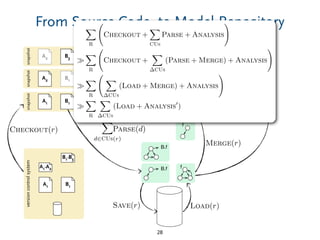
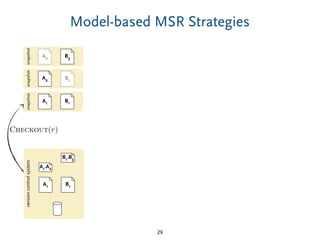
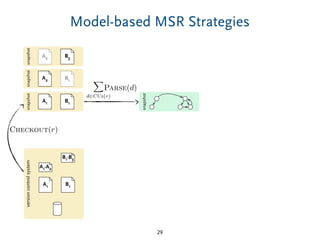
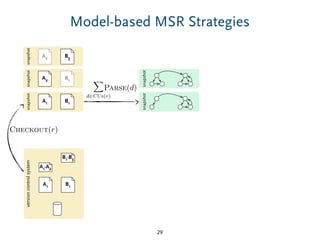
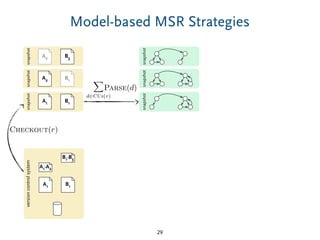
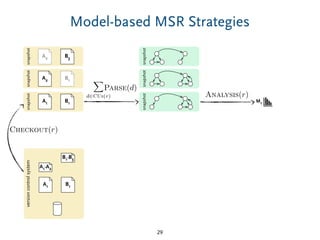
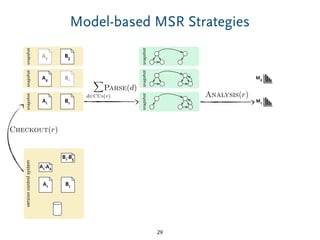
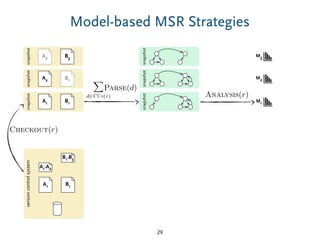
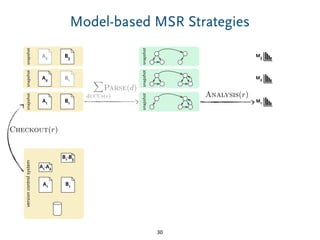
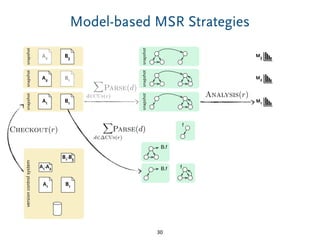
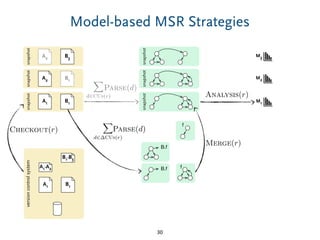
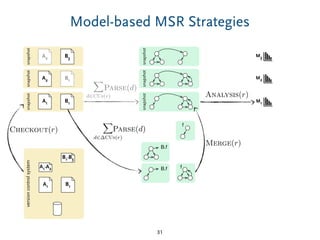
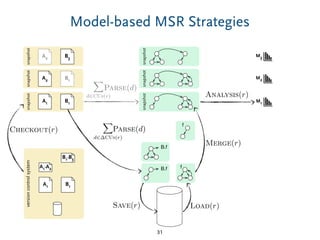
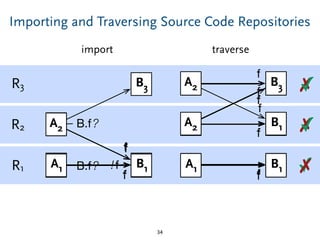
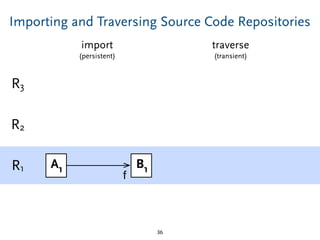
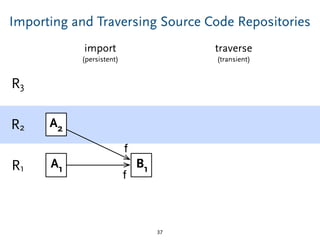
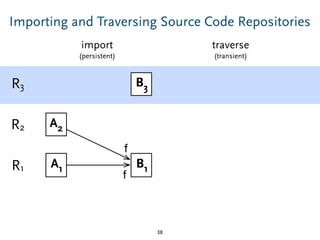
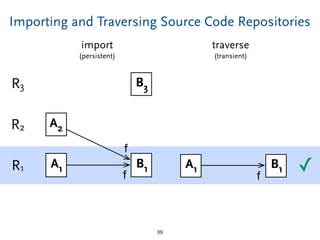
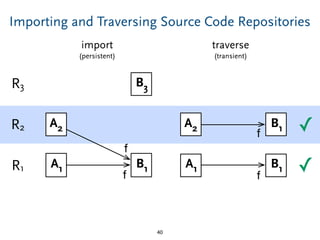
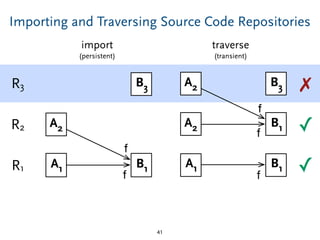
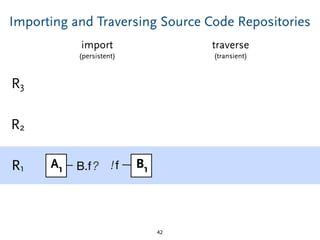
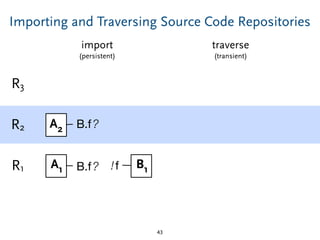
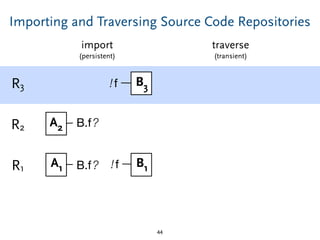
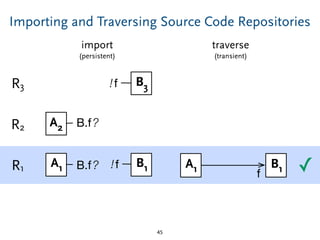
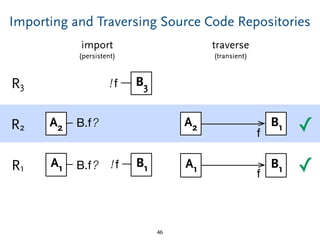
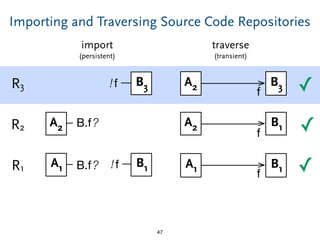
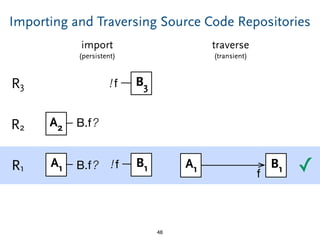
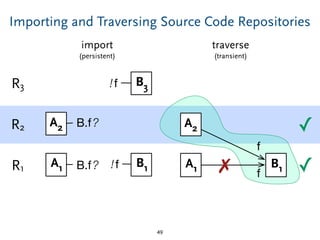
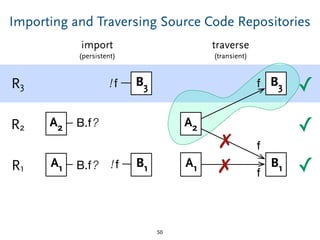
The document discusses model comparison approaches for delta-compression. It describes comparing models at the element level by matching elements between models and identifying differences. It also discusses representation of differences for compression purposes and experiments comparing EMF Compare and EMF Compress on reverse engineered models from Git repositories.




![Comparison Time
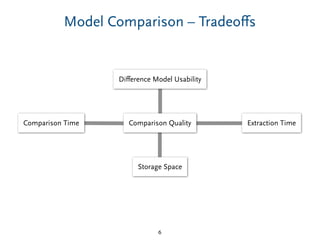
Difference Model Usability
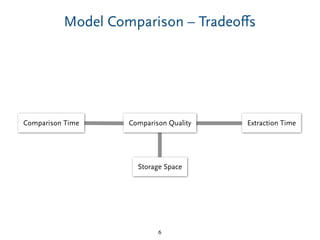
Extraction Time
Storage Space
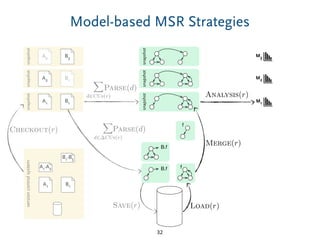
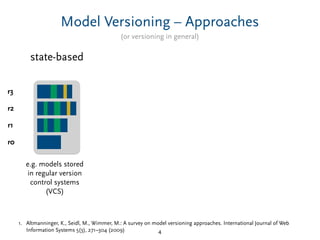
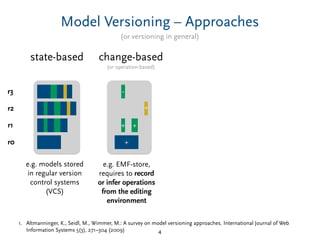
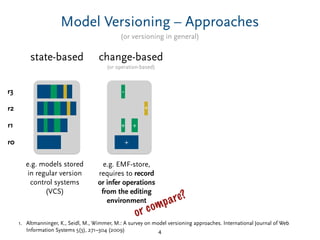
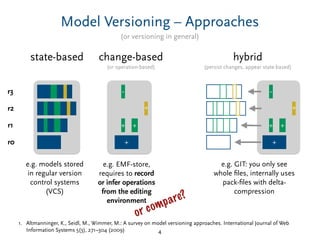
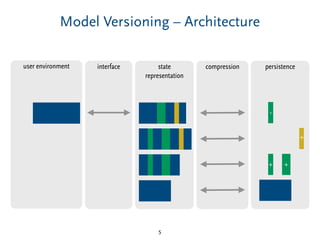
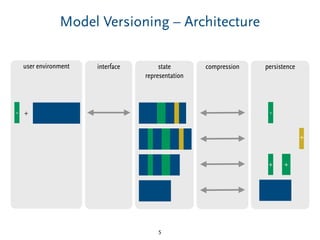
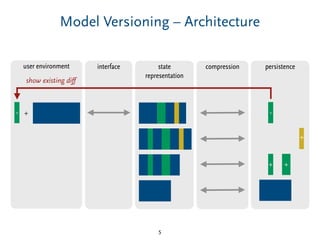
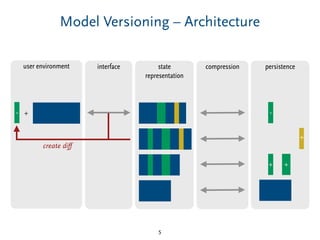
Delta-Compression – Tradeoffs
7
Comparison Quality
priority for showing diffs to users [model comparison]
priority for using diffs in persistence [compression]](https://image.slidesharecdn.com/bigmde-compression-161216090308/85/Model-Comparison-for-Delta-Compression-17-320.jpg)
![Model Matching
9
model 1
model 2
matches differences
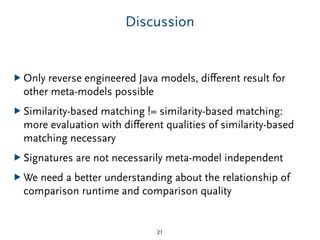
▶ Matching determines the quality of the comparison
▶ Different strategies to matching model elements
■ signatures: just meta-class, [name, parameter types], parent
■ similarity: lots of different criteria and heuristics
cheap
expensive](https://image.slidesharecdn.com/bigmde-compression-161216090308/85/Model-Comparison-for-Delta-Compression-19-320.jpg)