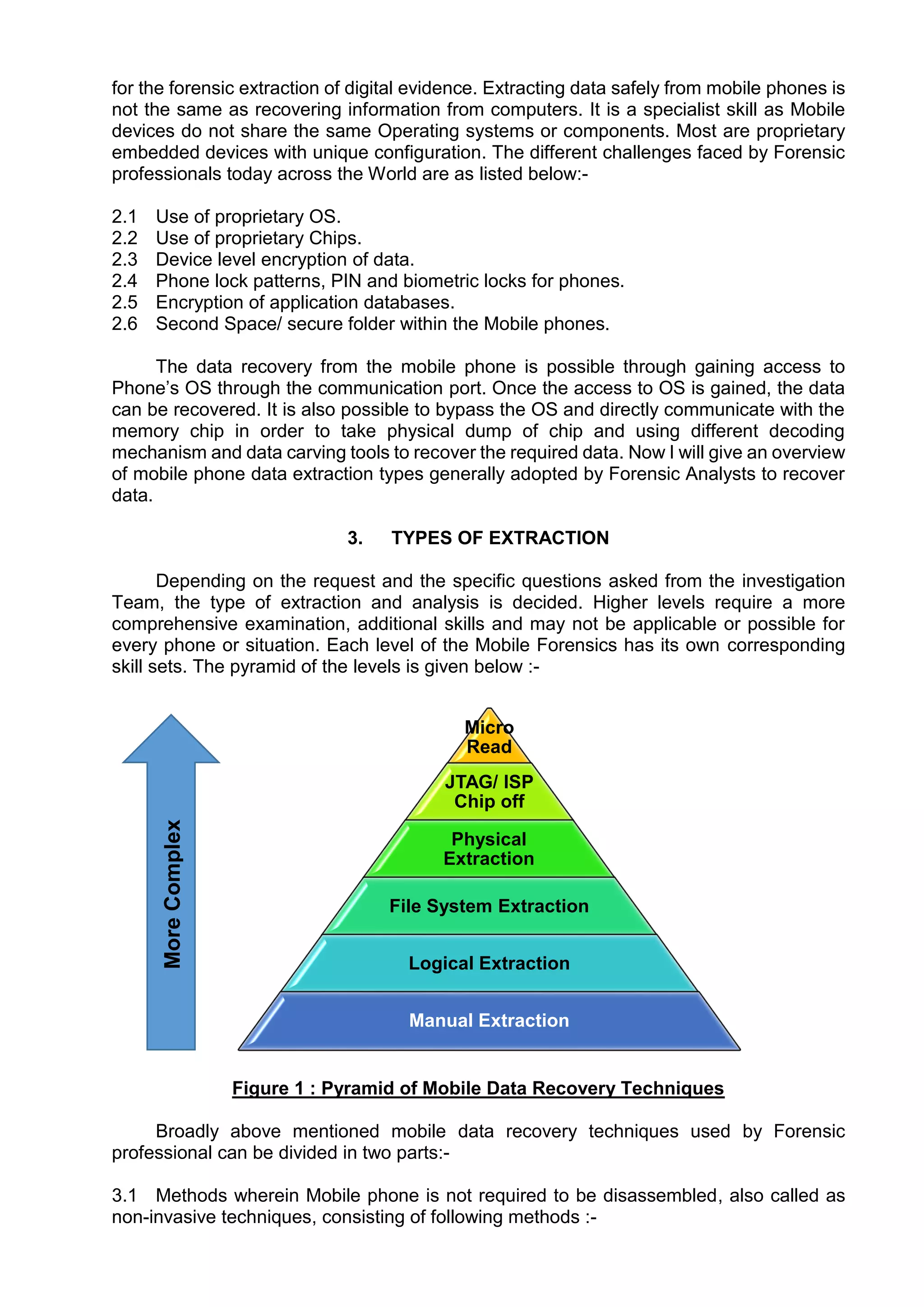
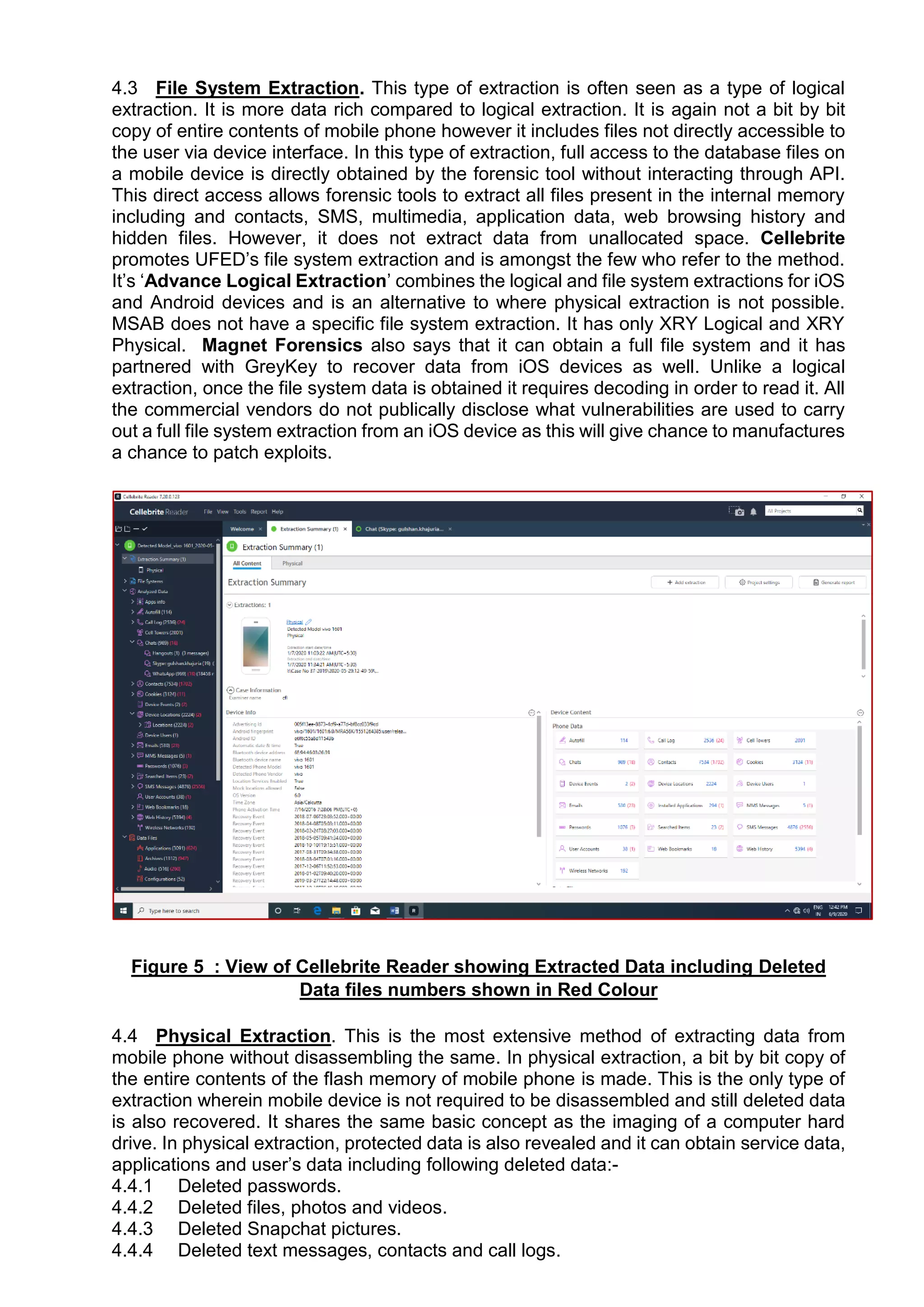
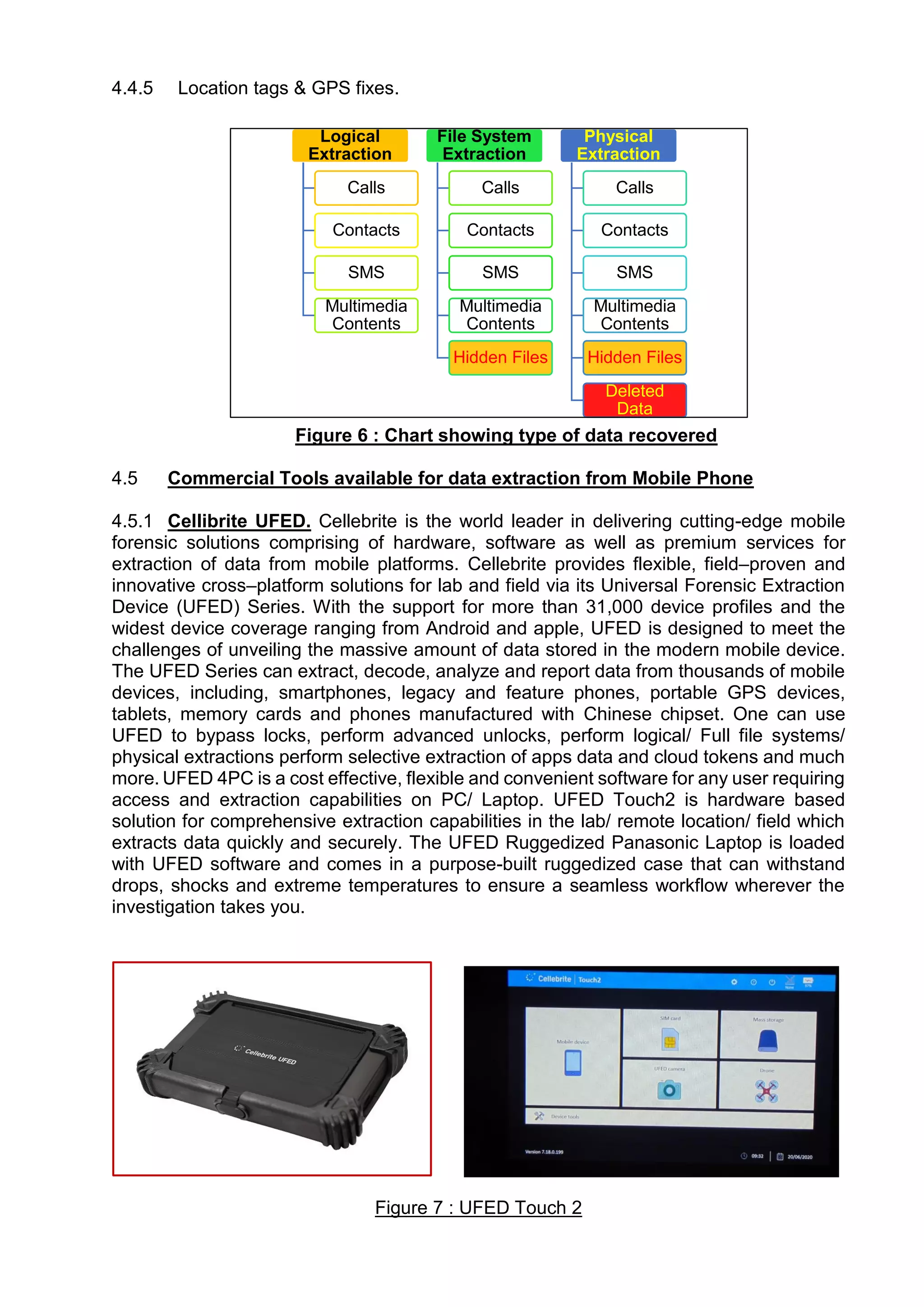
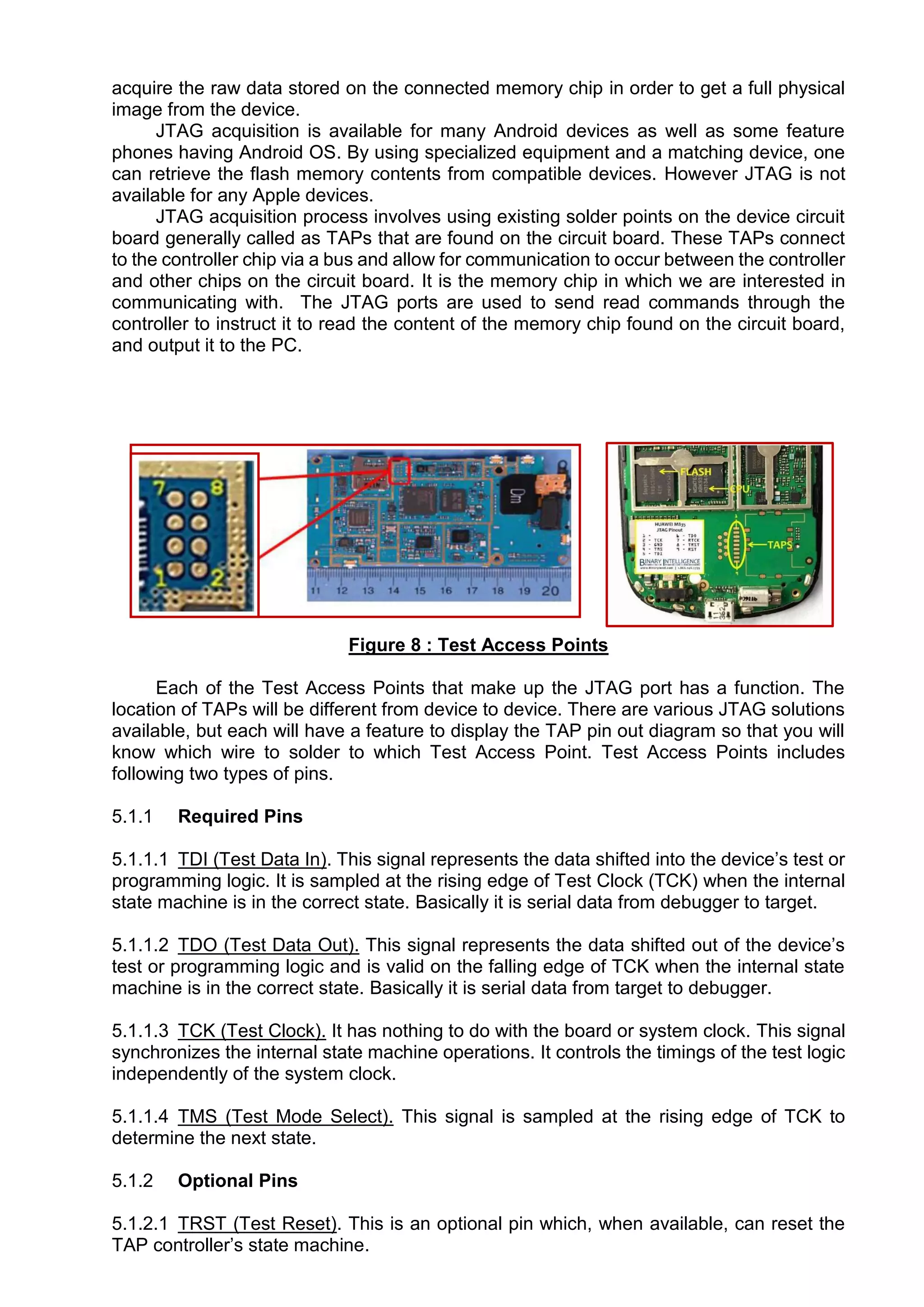
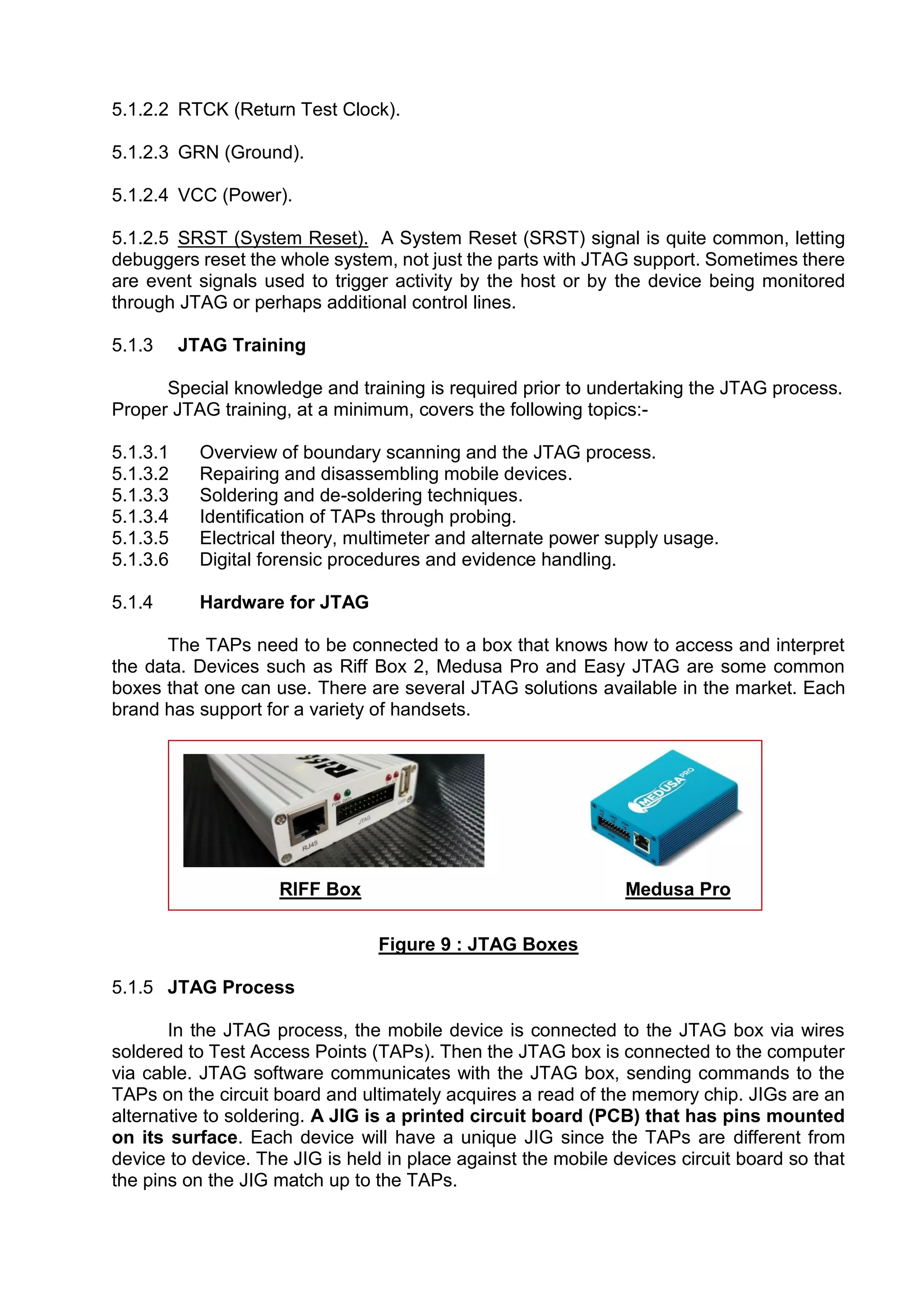
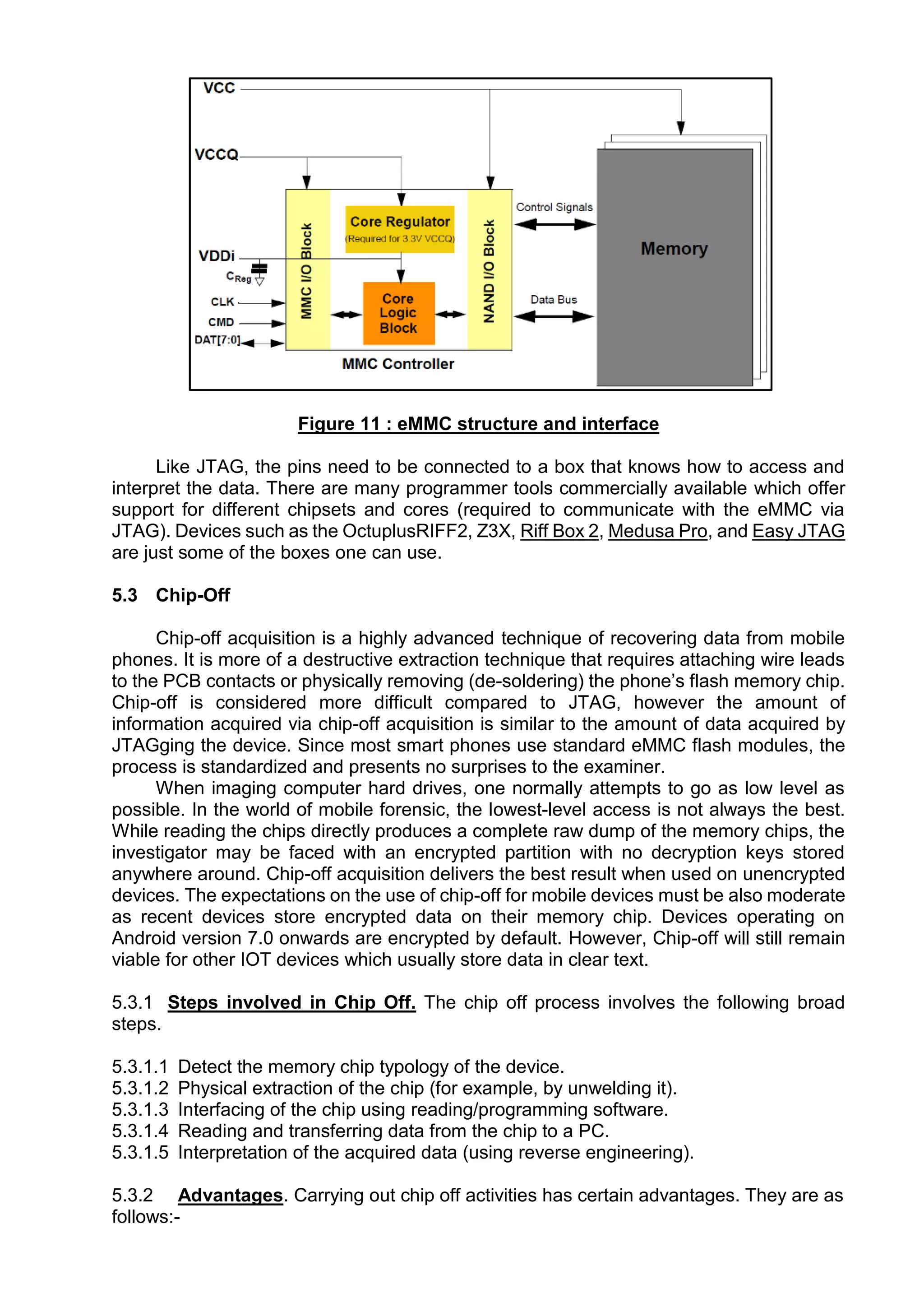
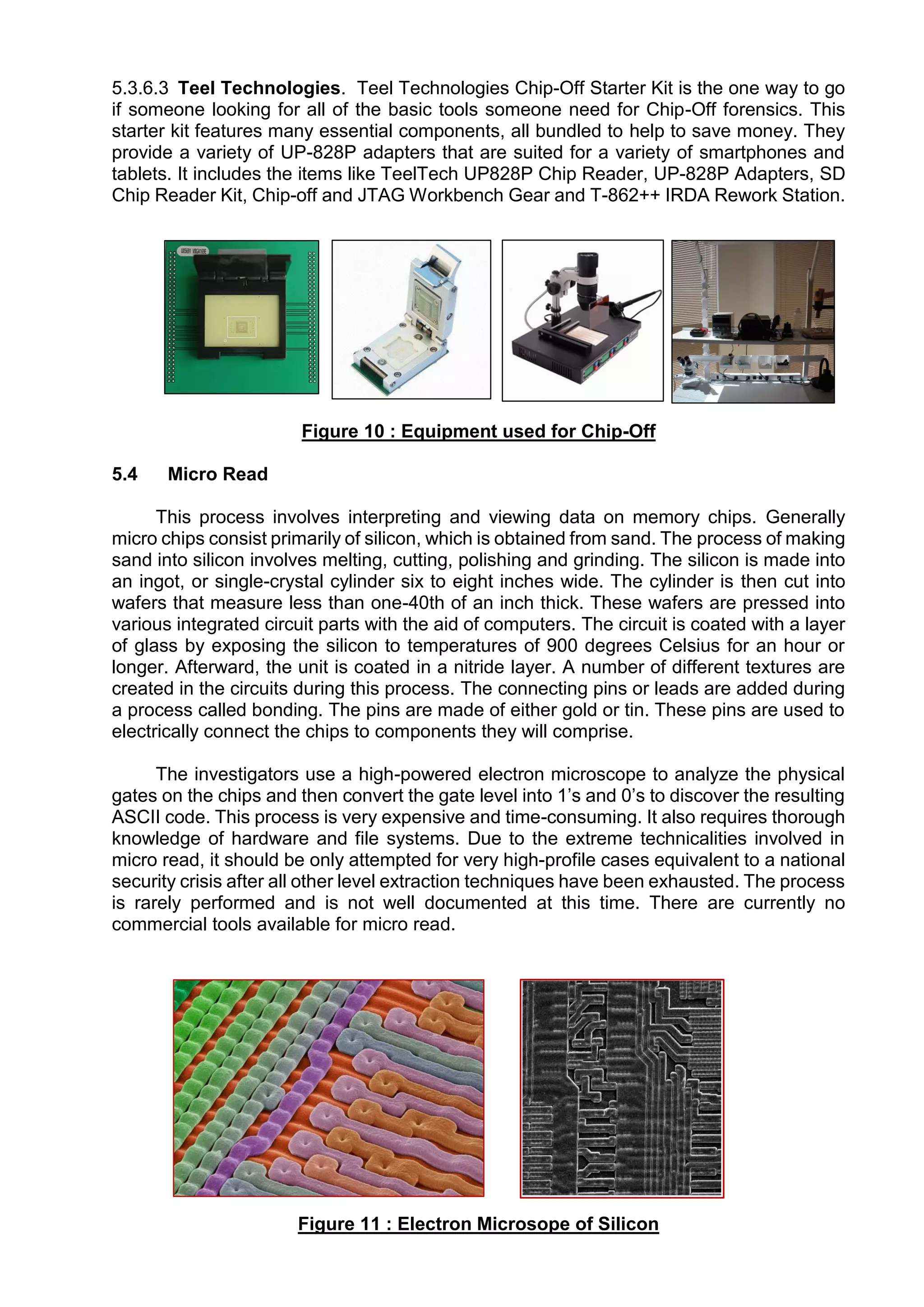
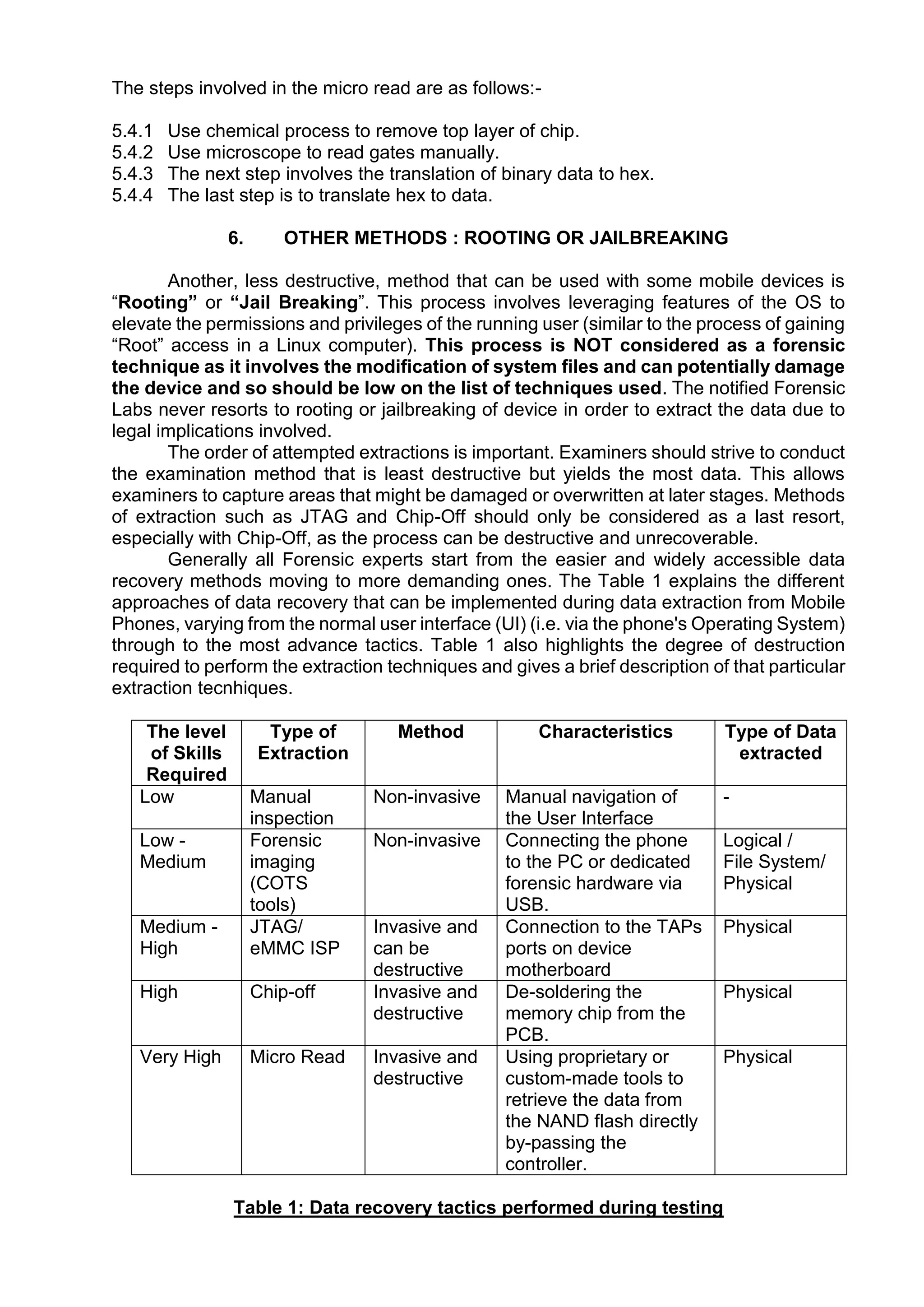
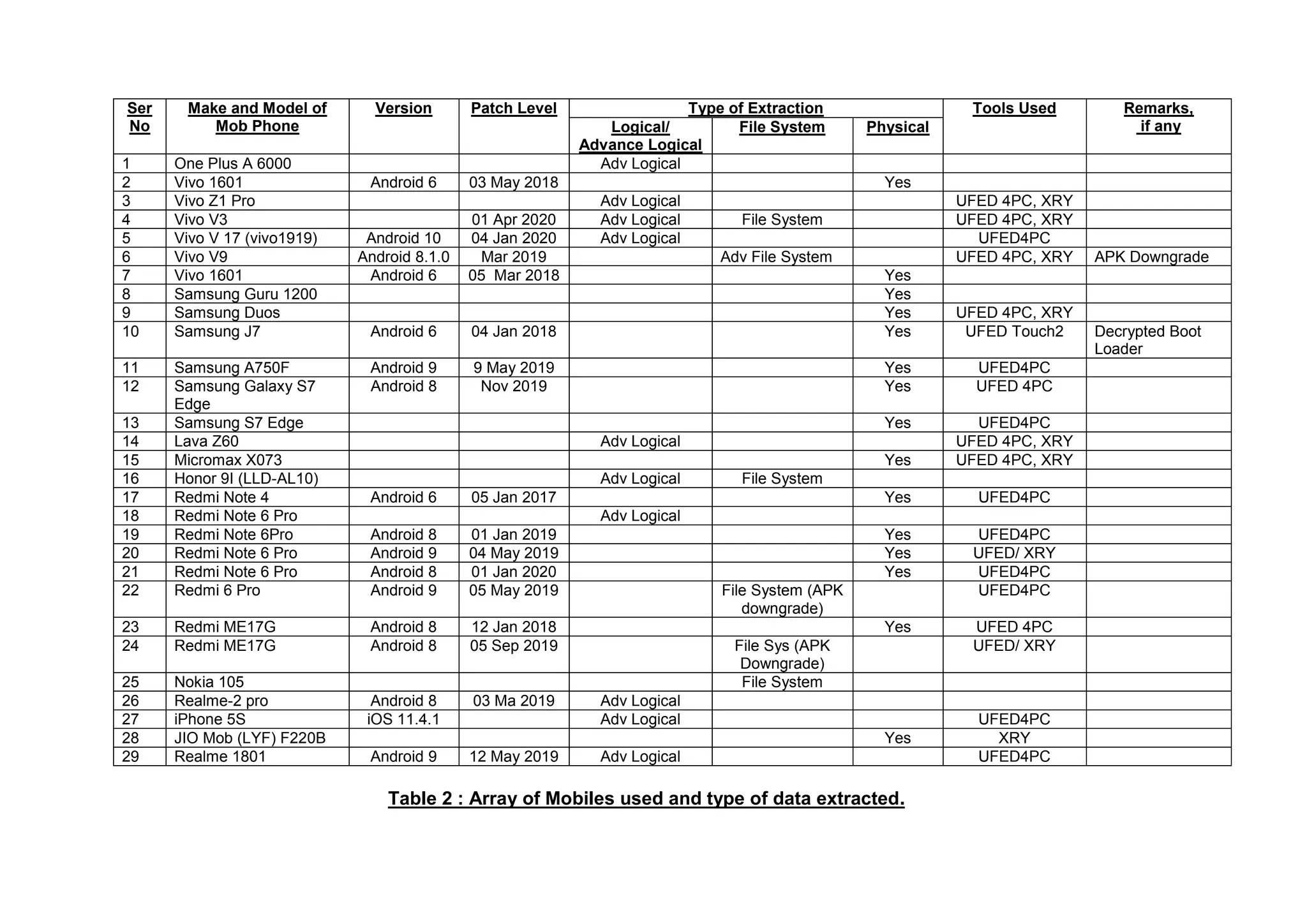
This document provides an overview of various techniques for extracting data from mobile phones for forensic investigations. It discusses challenges such as proprietary operating systems and encryption. Methods described include manual extraction by viewing the screen, logical extraction of accessible data through APIs, file system extraction of hidden files, and physical extraction making a bit-by-bit copy of memory. More advanced techniques require disassembling the phone, such as JTAG which communicates through test access ports to read memory. Commercial tools are available to perform different levels of extraction.