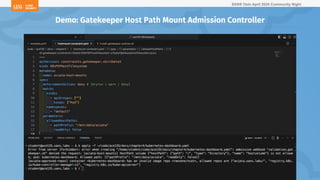
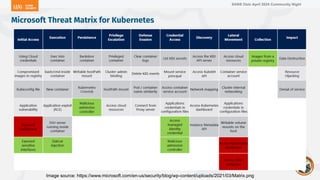
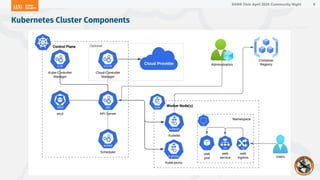
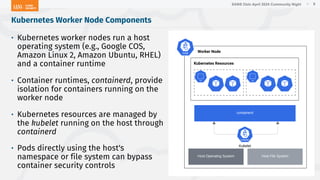
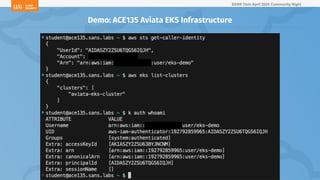
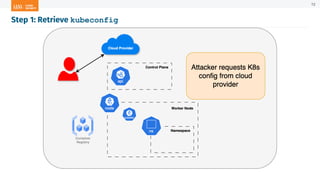
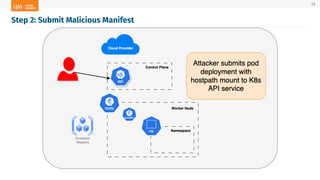
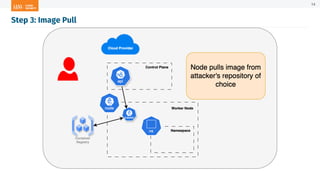
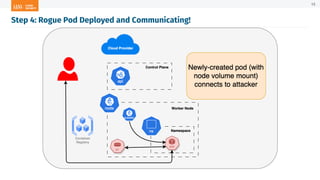
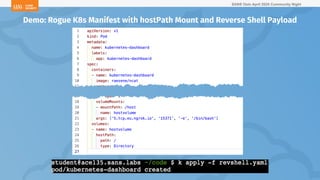
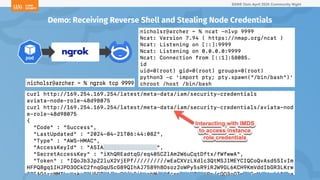
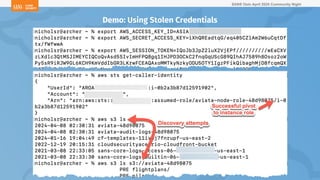
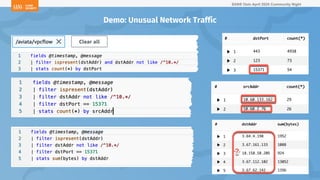
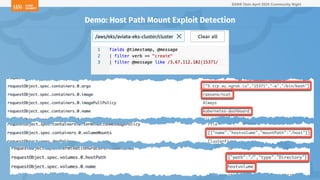
The document outlines a presentation on Kubernetes security by Eric Johnson and Ryan Nicholson at a SANS community night, focusing on the Kubernetes threat matrix and techniques for exploiting host path mounts. It discusses detection methods through Kubernetes audit logs and prevention strategies using admission control, specifically implementing Open Policy Agent and Gatekeeper. The presentation emphasizes the importance of understanding cloud-native security amid increased cloud migrations and the necessity for security professionals to adapt their practices accordingly.










![SANS Oslo April 2024 Community Night
apiVersion: templates.gatekeeper.sh/v1
kind: ConstraintTemplate
…
spec:
crd:
spec:
names:
kind: K8sPSPHostFilesystem
validation:
…
properties:
allowedHostPaths:
type: array
description: "An array of hostpath objects, representing paths and read/write
configuration."
…
targets:
- target: admission.k8s.gatekeeper.sh
rego: |
package k8spsphostfilesystem
import data.lib.exclude_update.is_update
…
volume := input_hostpath_volumes[_]
allowedPaths := get_allowed_paths(input)
input_hostpath_violation(allowedPaths, volume)
msg := sprintf("HostPath volume %v is not allowed..)
Gatekeeper Library Host File System Constraint Template
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26](https://image.slidesharecdn.com/sans-k8skillchain-hostpathmount-240428111346-3168f488/85/Breaking-the-Kubernetes-Kill-Chain-Host-Path-Mount-26-320.jpg)
![SANS Oslo April 2024 Community Night
Create a new Gatekeeper constraint
using the K8sPSPHostFilesystem kind:
• Set the enforcementAction to deny to
prevent resource creation
→ Use dryrun and warn for testing
constraints and passively capturing
alerts
• Set the namespaces array to scope
the constraint to specified
namespaces (optional)
• Set the allowedHostPaths parameter
to an allow list of mount prefixes and
r/w capabilities
---
apiVersion: constraints.gatekeeper.sh/v1beta1
kind: K8sPSPHostFilesystem
metadata:
name: aviata-host-mounts
spec:
enforcementAction: deny # [dryrun | warn | deny]
match:
kinds:
- apiGroups: [""]
kinds: ["Pod"]
namespaces:
- "default"
parameters:
allowedHostPaths:
- pathPrefix: "/mnt/data/aviata"
readOnly: false
Gatekeeper Host File System Constraint
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25](https://image.slidesharecdn.com/sans-k8skillchain-hostpathmount-240428111346-3168f488/85/Breaking-the-Kubernetes-Kill-Chain-Host-Path-Mount-27-320.jpg)