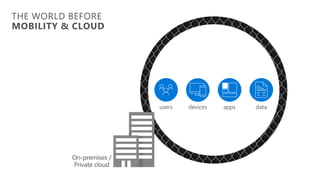
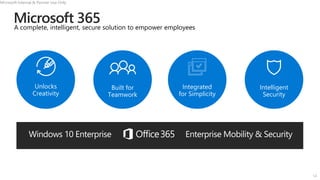
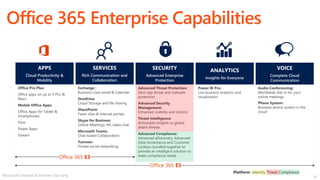
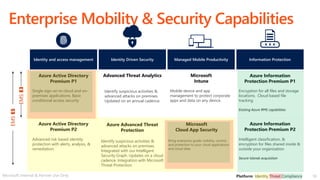
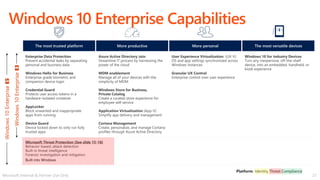
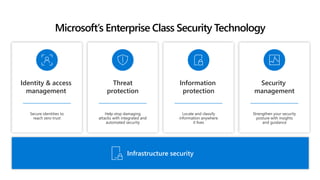
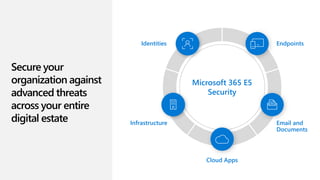
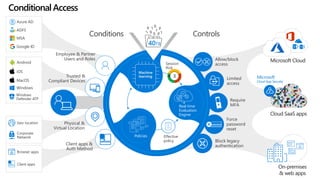
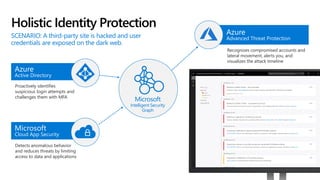
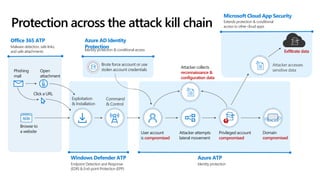
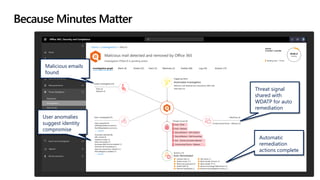
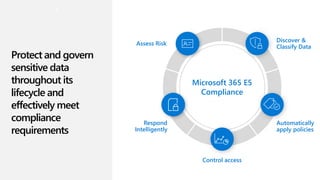
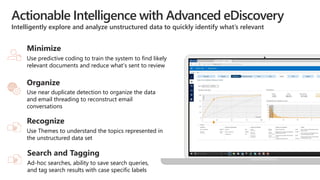
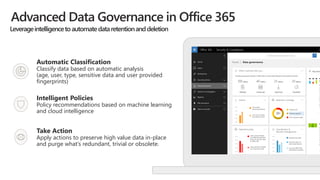
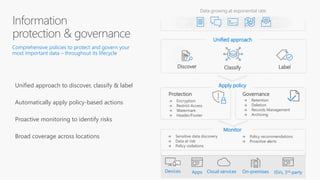
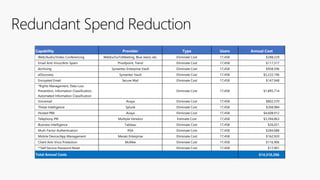
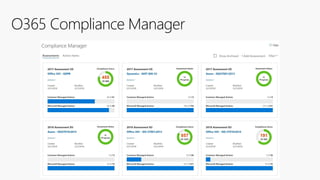
This document discusses migrating to Microsoft 365 from on-premises systems and third-party cloud services. It highlights how Microsoft 365 can help reduce redundant spending by consolidating capabilities in a single platform. It also outlines potential productivity and security benefits like reduced downtime, lower compliance costs, and decreased risk of data breaches. The document argues that organizations should move to Microsoft 365 now rather than later to realize cloud economics benefits and simplify operations.