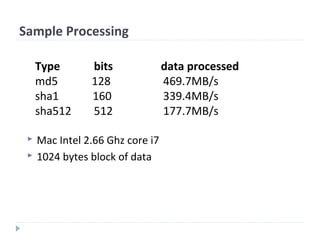
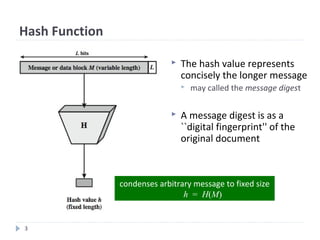
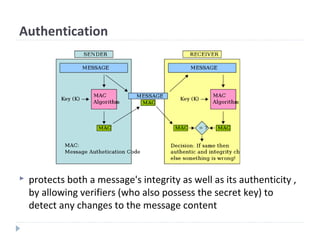
The document discusses cryptographic hash functions, including an overview of their usage, properties, structures, attacks, and the need for a new secure hash standard. Hash functions take an arbitrary-length message and condense it to a fixed length digest. They are used for applications like file integrity verification, password storage, and digital signatures. Key properties include producing fixed length outputs, being preimage resistant (one-way), and collision resistant. Common hash functions like MD5 and SHA-1 have been broken or shown to be vulnerable to attacks. This highlights the need for a new secure hash standard with stronger security.


























![Hash Algorithm Design – MD5
16 steps
Constructed from sine function
X[k] = M [q*16+k] (32 bit)](https://image.slidesharecdn.com/zxuv6hitszkhgalrxqqv-signature-36f32e70ca4a33ced055e07ae5cf71cddac8f7fec70112c9f9e169a5a2016f84-poli-160425162036/85/Hash-crypto-31-320.jpg)
![The ith 32-bit word in matrix T, constructed from the sine function
M [q*16+k] = the kth 32-bit word from the qth 512-bit block of the msg
Single step](https://image.slidesharecdn.com/zxuv6hitszkhgalrxqqv-signature-36f32e70ca4a33ced055e07ae5cf71cddac8f7fec70112c9f9e169a5a2016f84-poli-160425162036/85/Hash-crypto-32-320.jpg)