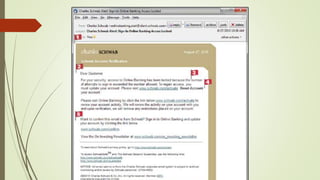
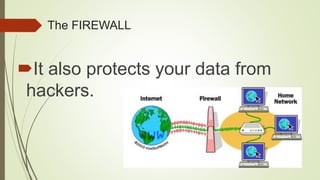
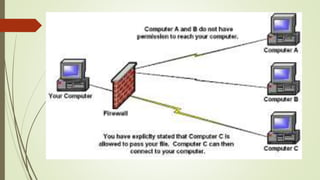
This document discusses internet safety, ethics, and netiquette. It defines phishing scams and how to avoid them, describes acceptable use policies (AUP) and their six key elements, and outlines the core rules of netiquette. Phishing involves deceiving users into providing private information through fraudulent emails or websites. An AUP defines constraints for network access and privacy expectations. Netiquette refers to polite and ethical online communication behavior. The core rules include treating others with respect, avoiding offensive content, knowing different community standards, and sharing knowledge to help others while maintaining privacy and control over flame wars.