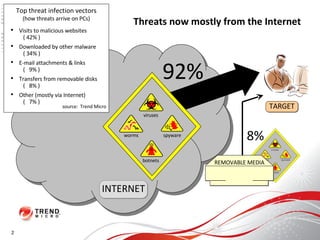
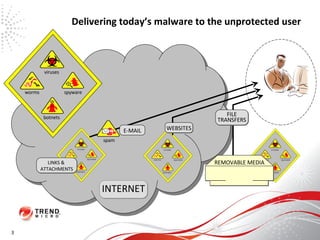
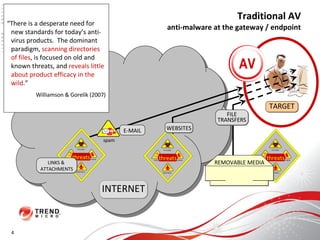
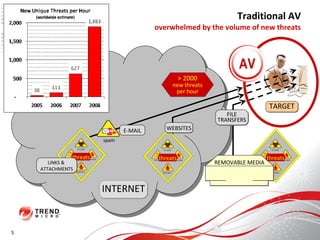
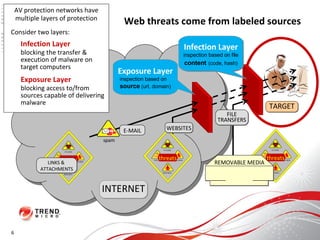
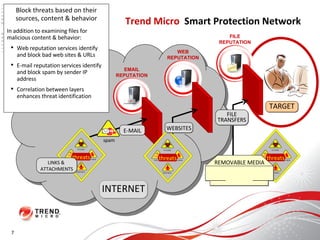
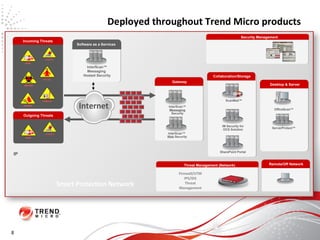
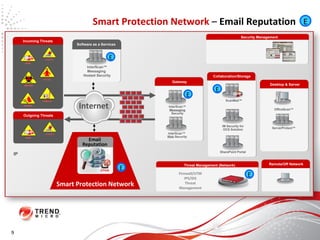
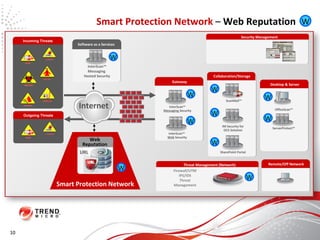
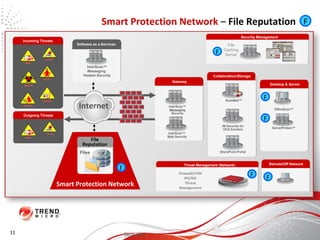
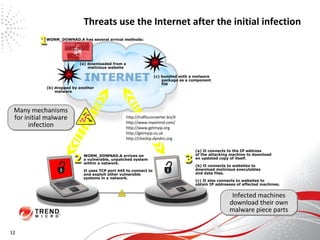
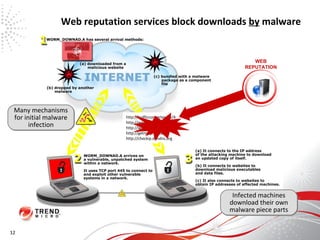
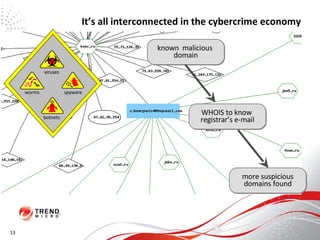
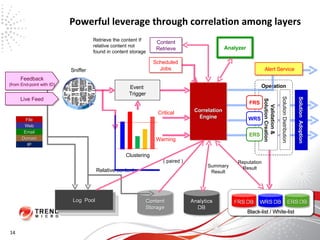
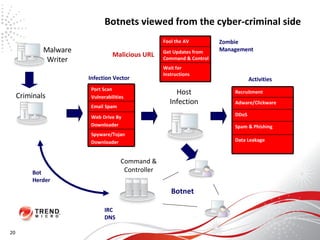
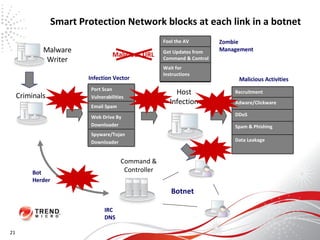
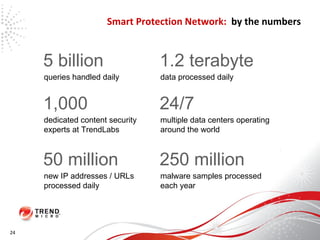
The document discusses how the threat landscape for IT security has radically shifted, presenting new challenges. It describes how information now largely comes from outside organizations rather than within, how cybercrime has evolved from opportunistic theft to organized crime for profit, and how protection has changed from deploying threat information locally to querying cloud databases. It then outlines how the Trend Micro Smart Protection Network uses multiple layers of inspection and correlation across email, web and file sources to identify and block threats throughout an organization's systems and networks.